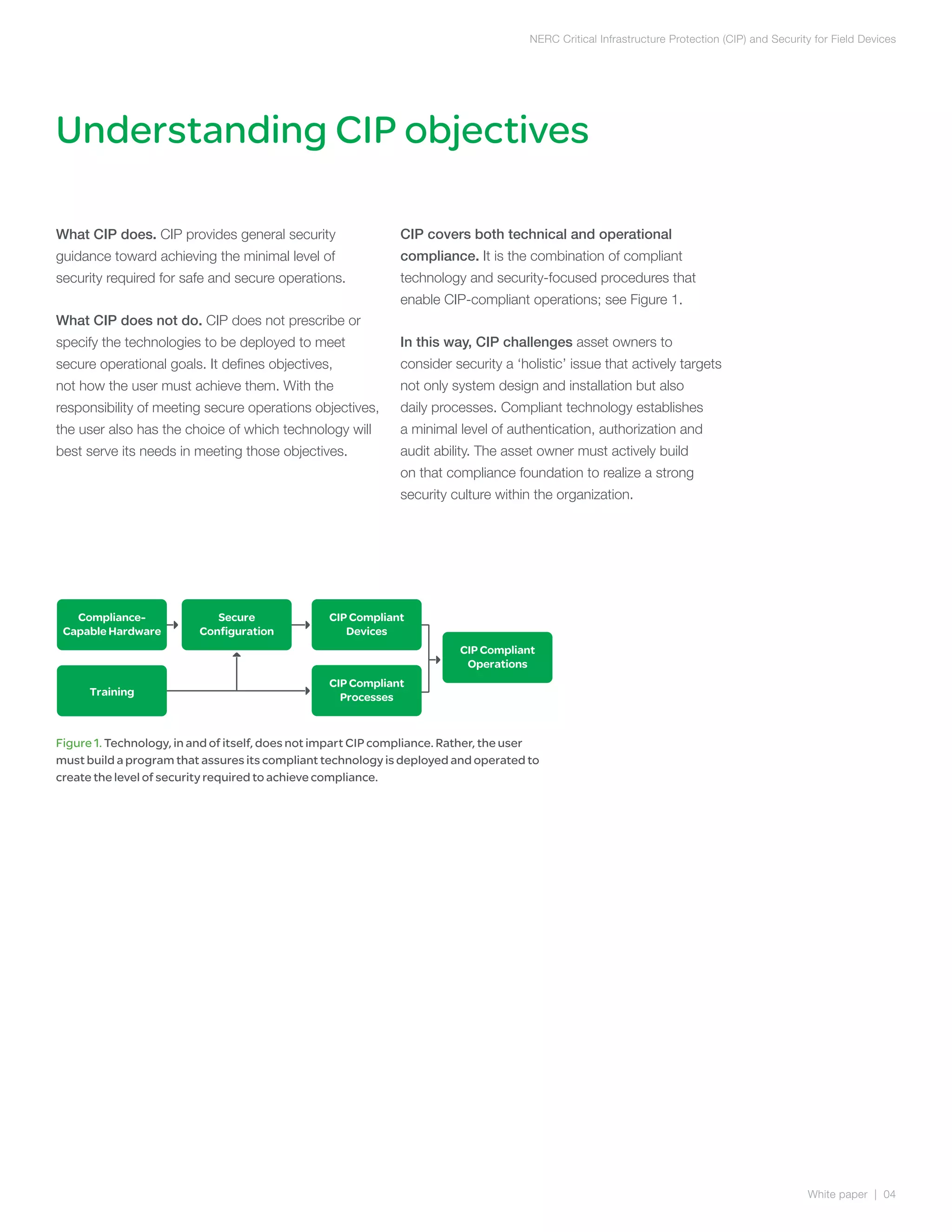
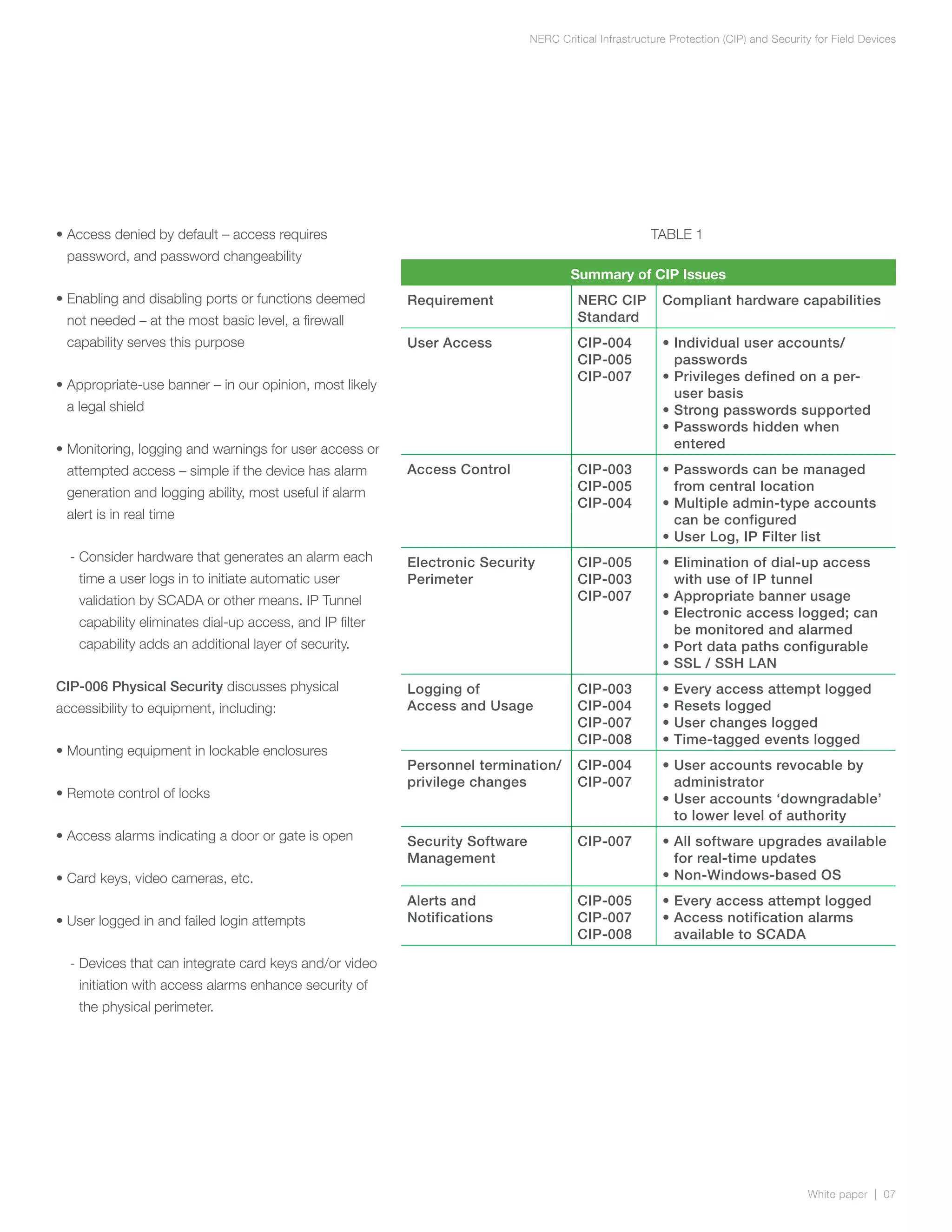
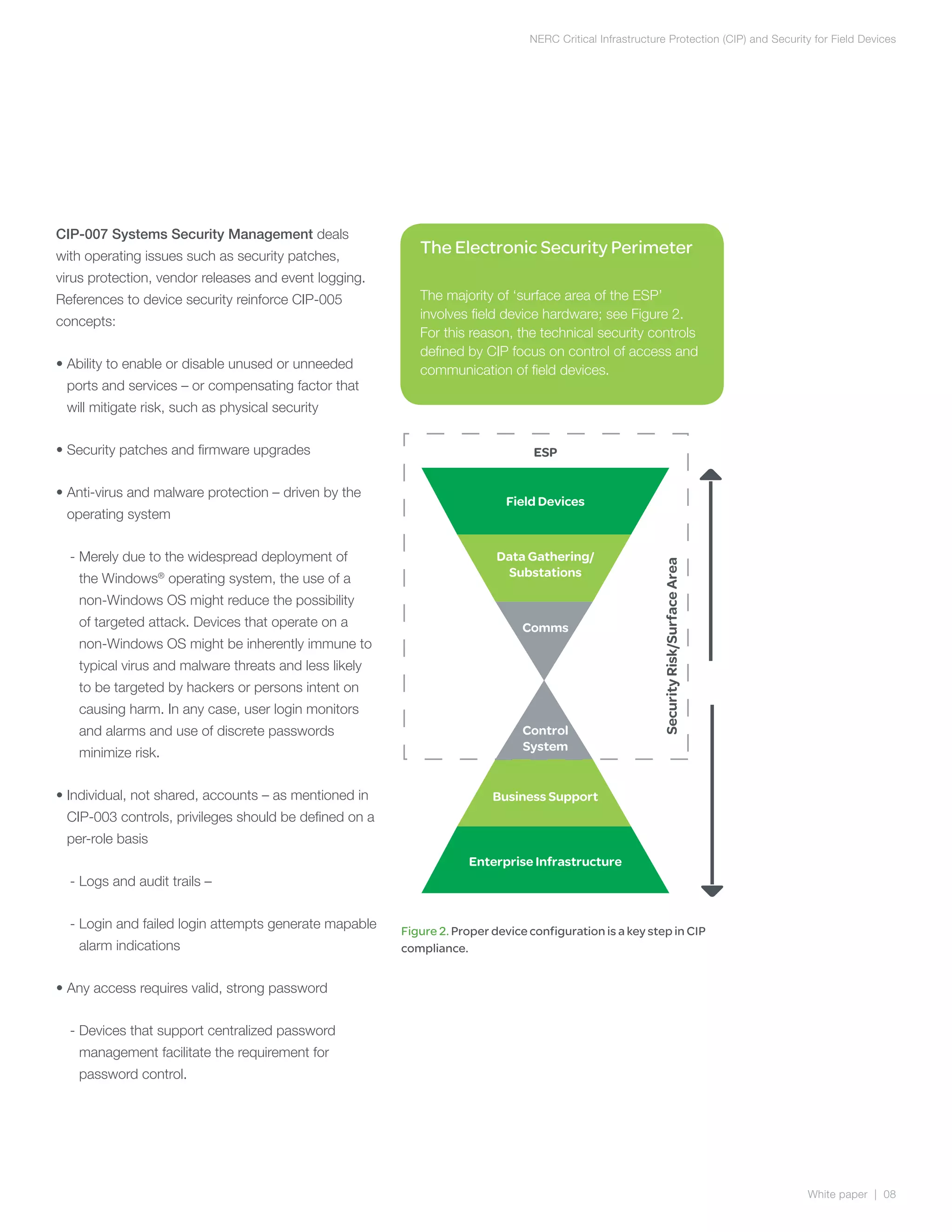
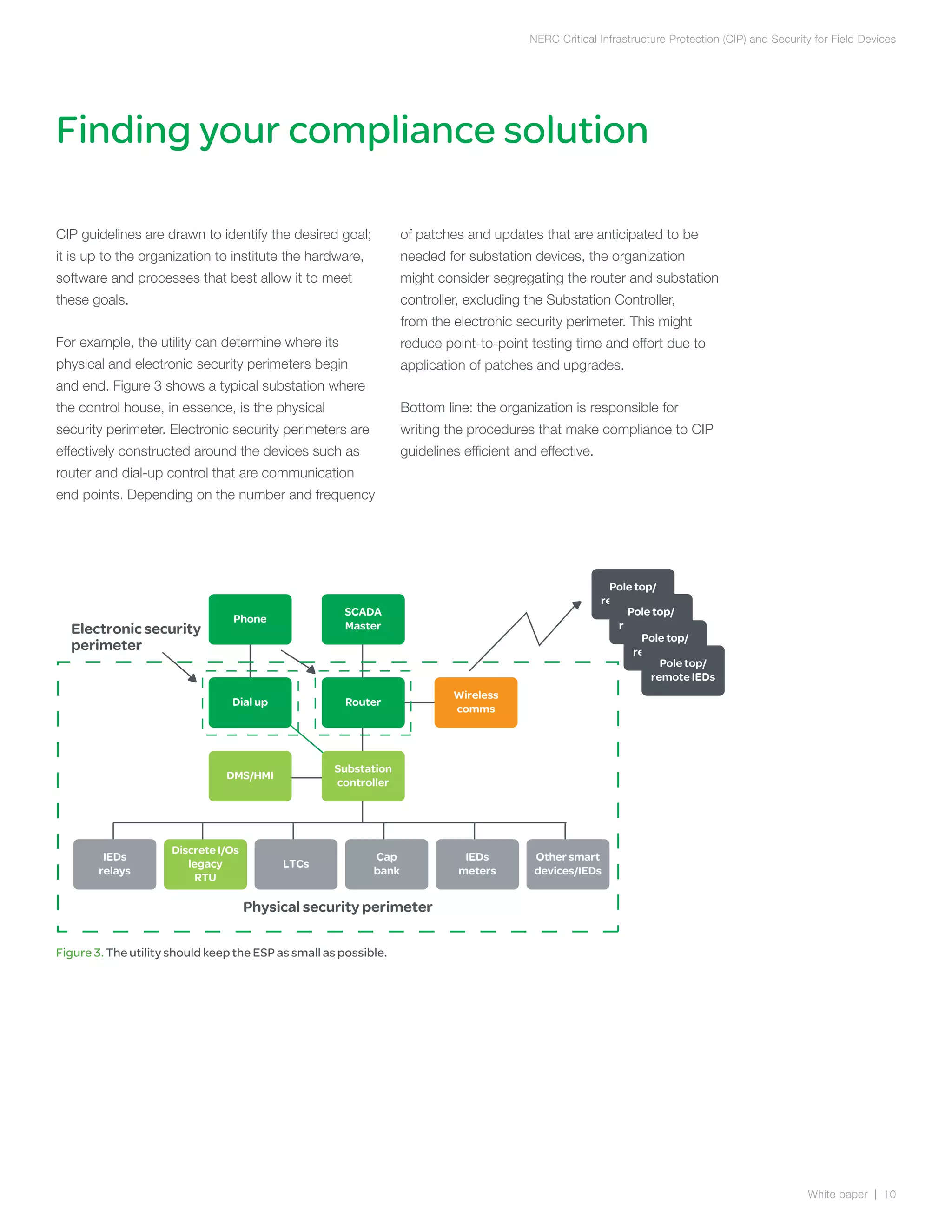
The document discusses NERC CIP guidelines for securing critical infrastructure devices in the electric grid. It provides an overview of the six main CIP guidelines regarding personnel authorization, training, security of the electronic perimeter, physical security, operations security, and incident reporting. The document emphasizes that compliance requires both compliant technologies and security-focused procedures. It also outlines key security principles like least privilege and role-based access controls. Overall, the summary provides a high-level view of the document's coverage of NERC CIP compliance objectives and guidelines.