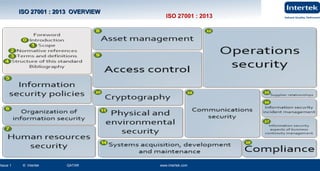
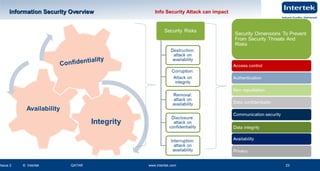
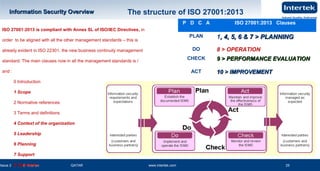
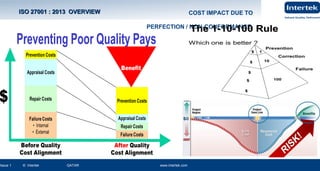
This document is a presentation on information security and business continuity. It covers topics such as ISO 27001 on information security, risk management, laws relating to information security in Qatar, and examples of product recalls due to incidents. The presentation provides an overview of ISO 27001, including its structure following the PDCA model and the roles of internal and external interested parties. It also discusses why information needs protection due to threats and vulnerabilities, and the principles of information security management systems.