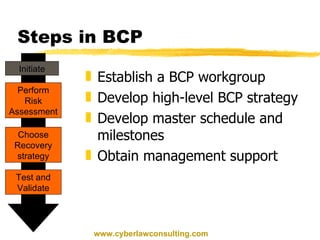
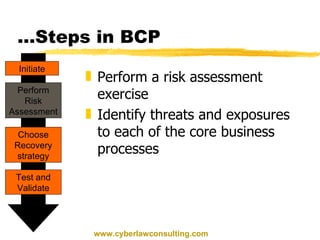
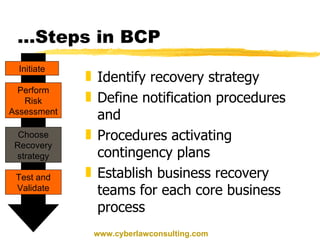
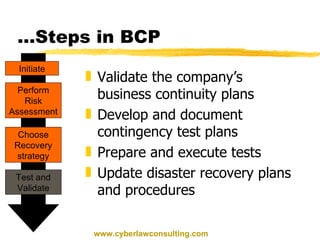
This document discusses disaster recovery and business continuity planning. It defines business continuity planning (BCP) and disaster recovery planning (DRP) as processes for improving an organization's ability to continue operations during adverse events. The key aspects covered include identifying threats, developing recovery teams, creating emergency and backup plans, selecting alternative processing sites, testing plans, and maintaining plans over time. Regular auditing of BCP/DRP is also recommended to ensure plans remain adequate as business needs change.
![Disaster Recovery And Business Continuity Adv. Prashant Mali [BSc.(Phy.), MSc.(Comp. Sci.),CNA, LLB ] Cyber Law ,Cyber Security & IPR Expert www.cyberlawconsulting.com](https://image.slidesharecdn.com/whatisbusinesscontinuityplanning-bcp-111014020038-phpapp01/75/What-is-business-continuity-planning-bcp-1-2048.jpg)






























































![Any Questions? Thank You Contact: prashant . [email_address] cyberlawconsulting @gmail.com Cell: (91)(9821763157) www.cyberlawconsulting.com](https://image.slidesharecdn.com/whatisbusinesscontinuityplanning-bcp-111014020038-phpapp01/85/What-is-business-continuity-planning-bcp-79-320.jpg)