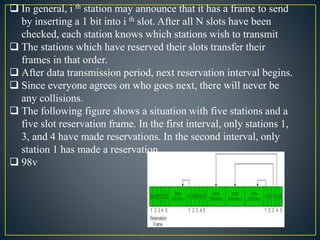
The document discusses various random access protocols for wireless networks, including ALOHA, CSMA, and controlled access protocols. It provides details on pure and slotted ALOHA, different CSMA access modes like 1-persistent and p-persistent, and controlled access methods like reservation, polling, and token passing. Key aspects like throughput calculations and performance metrics like delay and throughput are covered for different protocols.