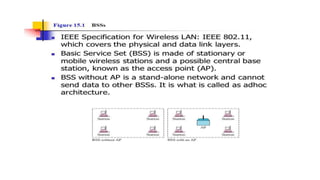
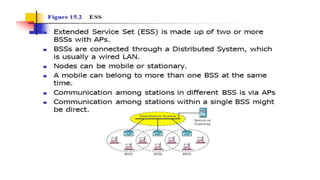
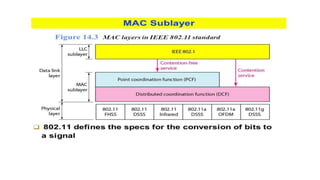
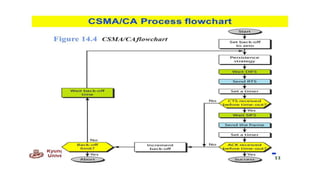
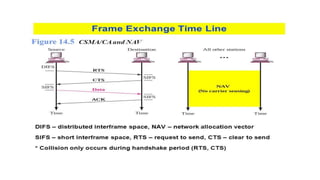
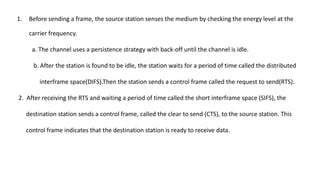
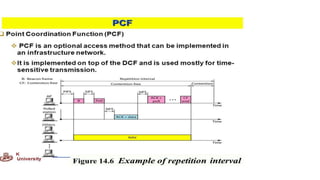
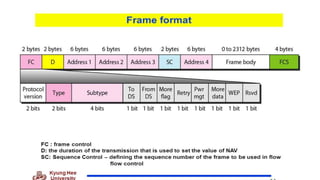
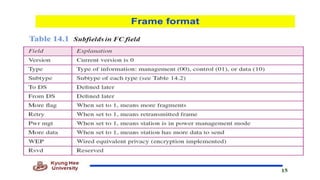
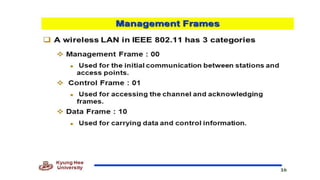
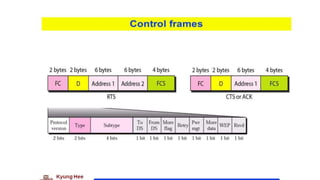
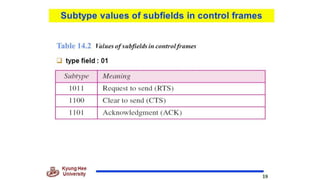
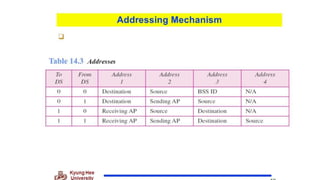
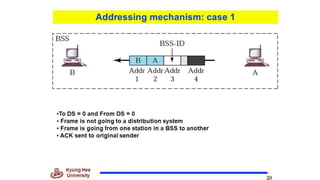
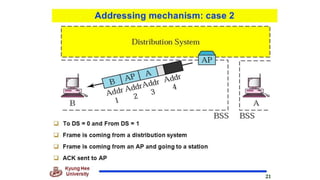
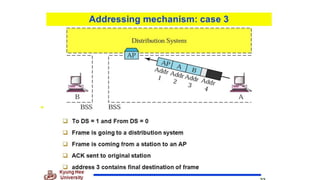
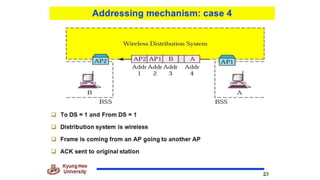
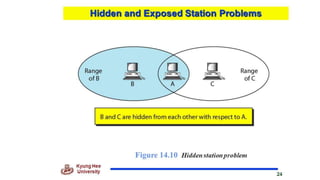
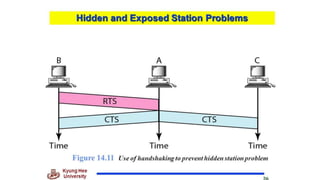
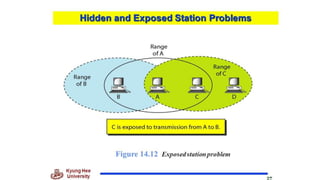
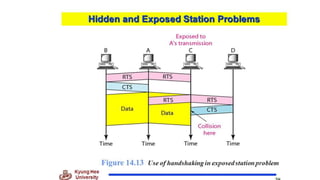
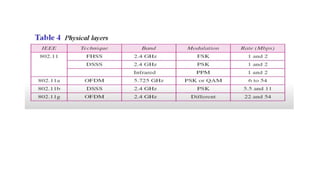
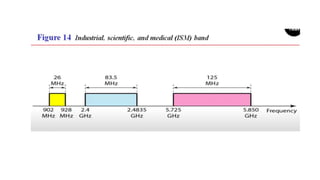
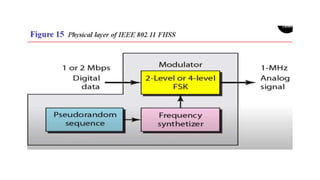
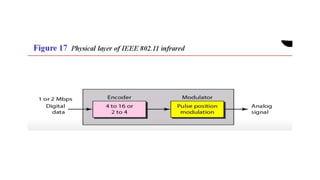
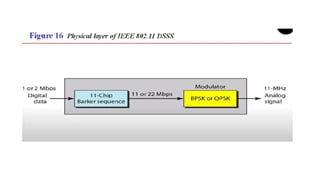
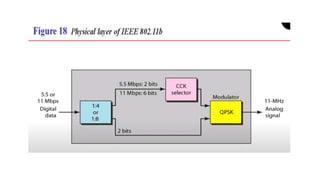
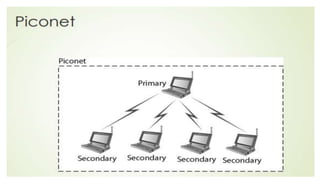
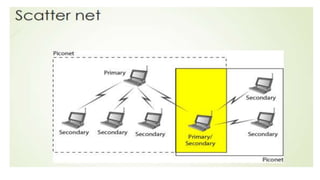
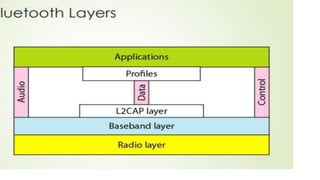
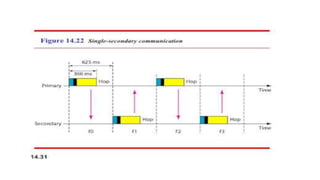
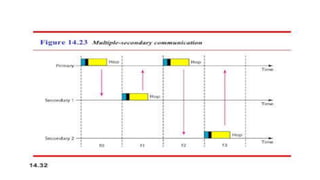
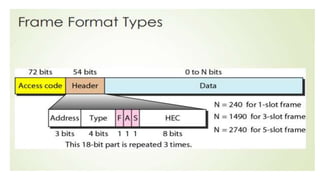
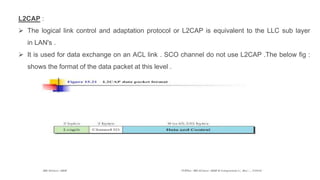
Chapter 14 discusses IEEE 802.11 wireless LAN standards, detailing the protocols for frame transmission, including RTS/CTS handshaking, collision avoidance, and the role of Network Allocation Vector (NAV) in managing access. In addition, Bluetooth networking is introduced, explaining its piconet and scatternet structures, as well as various connection types including SCO and ACL links. The document also covers how Bluetooth layers facilitate communication, error handling, and quality of service in data transmission.