The document outlines the principles of the Data Link Layer (DLL) in the OSI model, which provides services such as framing, error detection, and flow control between network entities. It discusses various IEEE standards that define specifications for Local Area Networks (LANs) and explains specific functions of the Logical Link Control (LLC) and Medium Access Control (MAC) sublayers, including error control and framing techniques. Additionally, it describes flow control mechanisms, such as Stop-and-Wait ARQ and Sliding Window protocols, which ensure reliable data transmission across networks.


![Framing:
Framing refers to the process of partitioning the bit stram into discrete units or blocks of data called
frames.
Specific formats and timing sequences exist for each LAN type.
By partioning the bit stream into frames framing enables sending and receiving machines to synchronize
the transmission and reception of data.
Framing also facilitates error detection and correction.
Once a bit stream is portioned into frames specific information about the contents of the frame is
computed and transmitted within a frame.
Using this information a receiving node can determine the integrity of the received frame.
One common framing procedure involves inserting flag characters before and after the transmission of
the data message
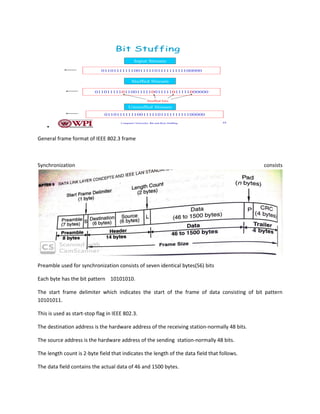
We will use the bit pattern 01111110 as our start-stop flags.
To distinguish the uniqueness of the start-stop flag bit pattern.
One way is bit stuffing
• Each frame begins and ends with a special bit pattern called a flag byte [01111110].
• Whenever sender data link layer encounters five consecutive ones in the data stream, it
automatically stuffs a 0 bit into the outgoing stream.
• When the receiver sees five consecutive incoming ones followed by a 0 bit, it automatically
destuffs the 0 bit before sending the data to the network layer.](https://image.slidesharecdn.com/unit4notes-converted-190324162245/85/PCCN-DATA-LINK-LAYER-UNIT-4-NOTES-3-320.jpg)