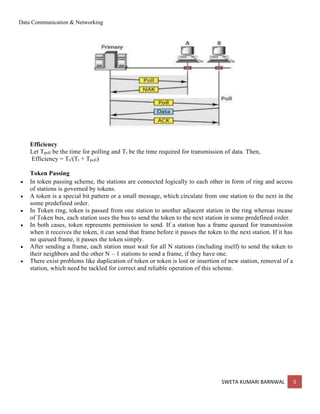
The document discusses multiple access protocols in computer networks. It describes several random access protocols like ALOHA, slotted ALOHA, and CSMA. It also discusses controlled access protocols like reservation, polling, and token passing. For multiple access control, protocols are needed to manage sharing of non-dedicated channels and decrease collisions. Random access protocols allow any station to transmit without priority while controlled access protocols determine transmission order to avoid collisions. The document also covers wireless LAN standards and security.