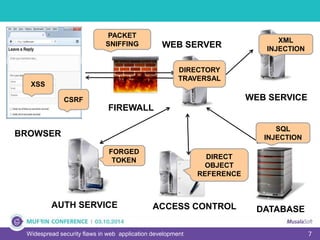
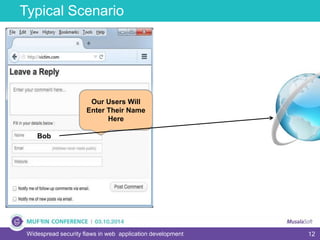
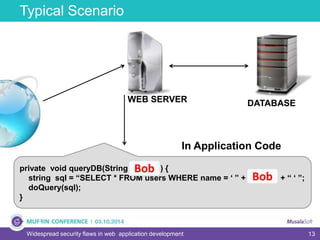
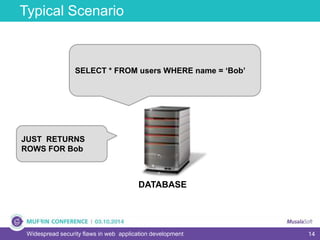
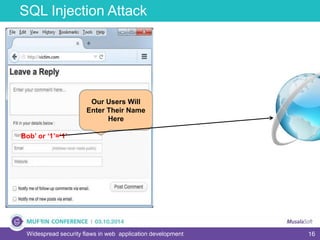
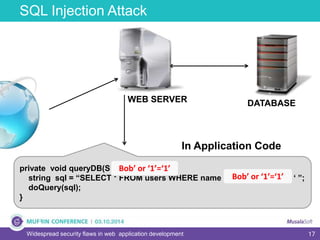
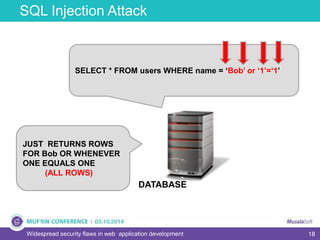
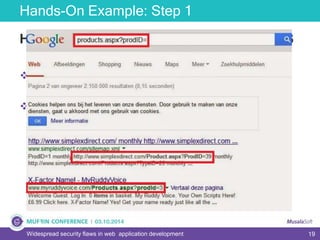
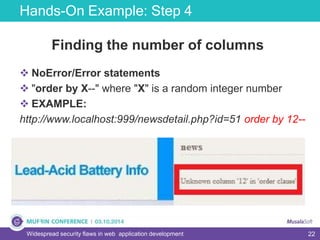
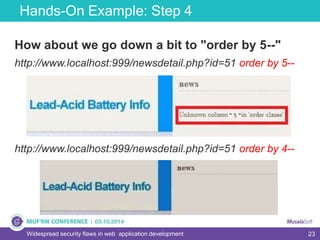
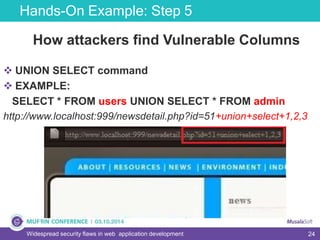
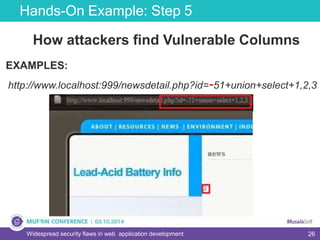
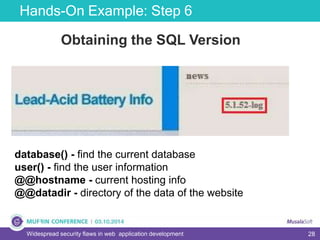
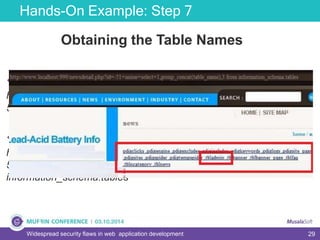
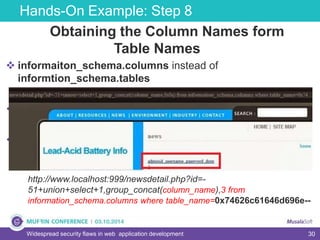
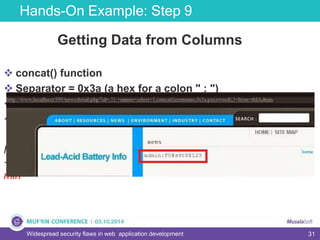
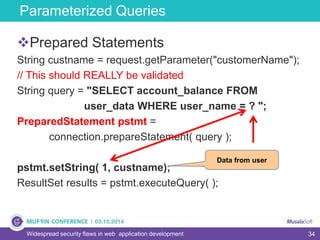
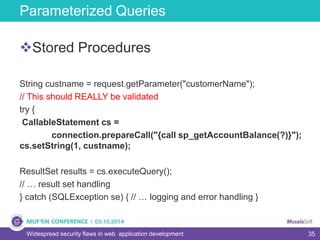
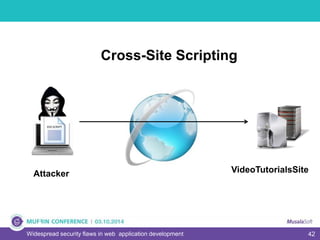
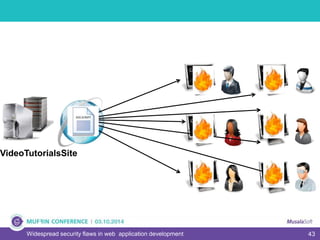
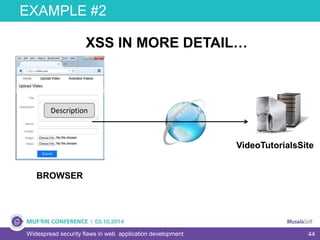
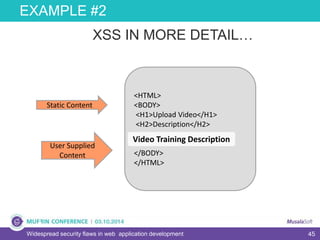
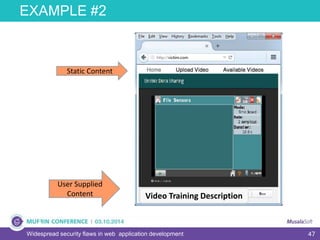
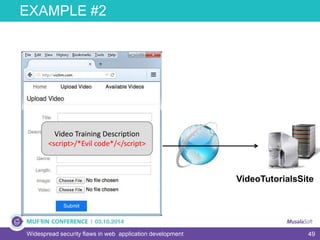
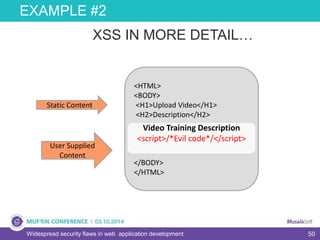
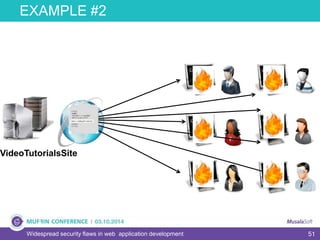
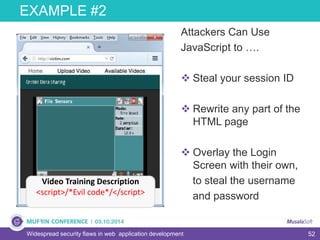
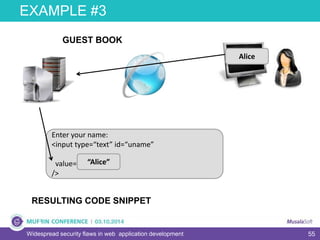
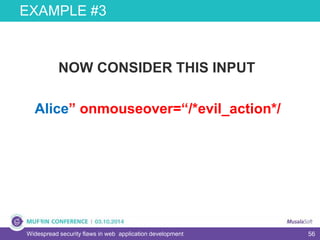
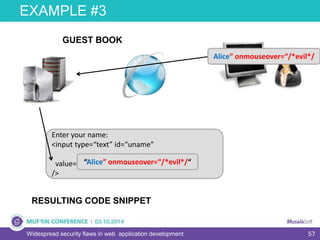
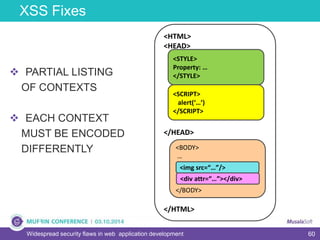
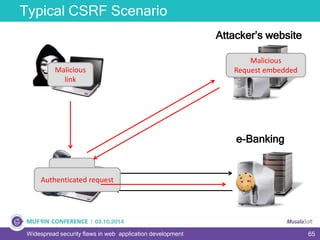
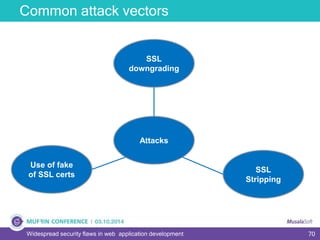
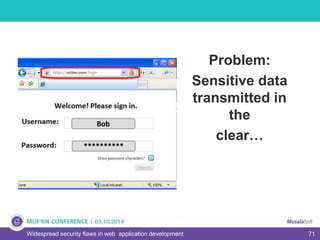
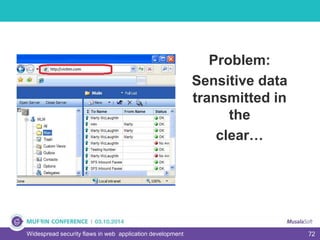
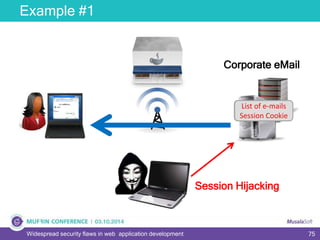
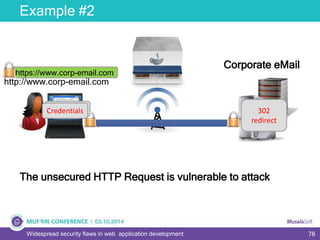
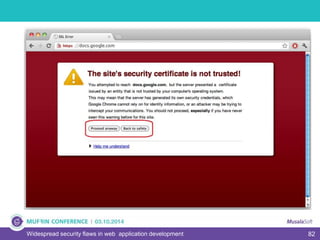
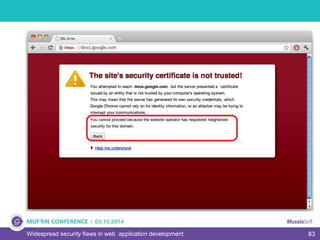
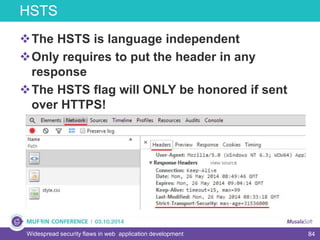
The document discusses widespread security flaws in web application development, emphasizing that most web applications have vulnerabilities due to their design not being inherently secure. It outlines common attack methods like SQL injection, Cross-Site Scripting (XSS), and Cross-Site Request Forgery (CSRF), along with preventive measures such as prepared statements and input validation. The content serves as an introductory guide to improving web application security by addressing these critical risks.