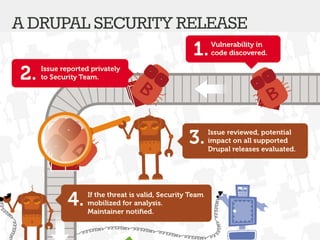
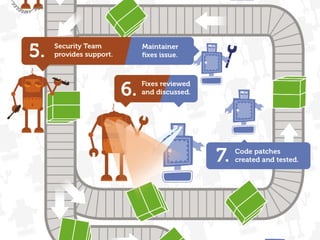
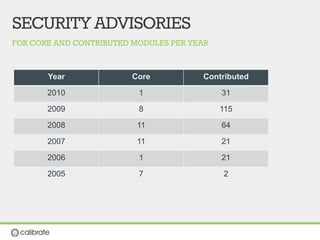
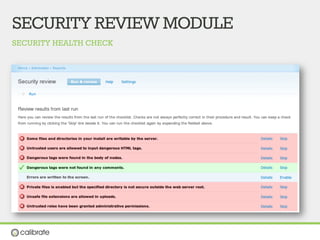
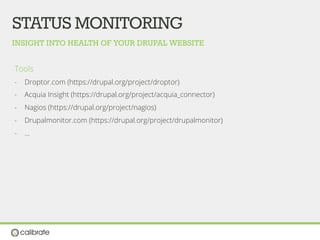
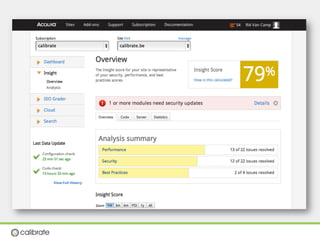
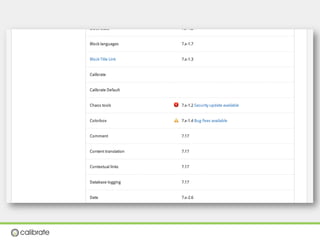
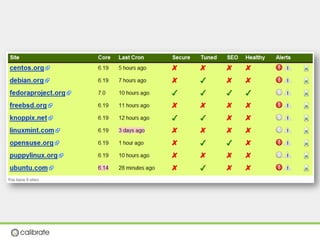
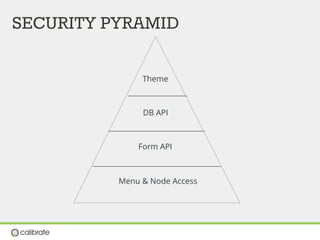
The document discusses securing Drupal websites through best practices, addressing vulnerabilities, and outlining the responsibilities of security teams. It highlights the importance of community involvement and regular updates to address security issues, while providing guidelines on using the Drupal API securely. Additionally, it lists common vulnerabilities and emphasizes the need for secure configurations and continuous monitoring.



















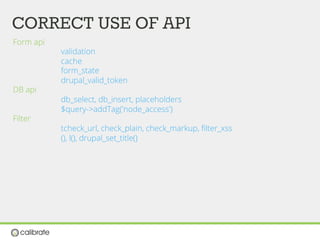




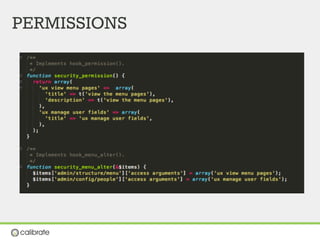

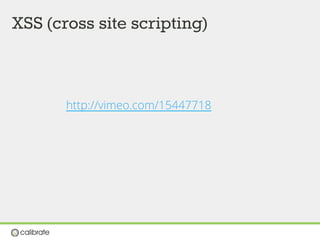
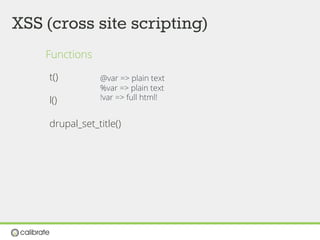
![XSS (cross site scripting)
Validate forms
User input should never contain javascript
Form api
Never use $_POST variables
$form_state['values']
Form caching](https://image.slidesharecdn.com/drupal-security-seminar-130628091555-phpapp01/85/Drupal-Security-Seminar-49-320.jpg)
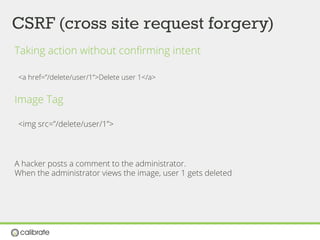
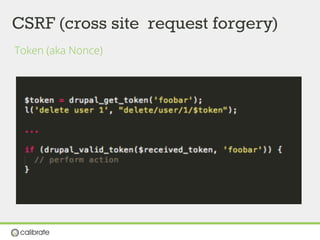
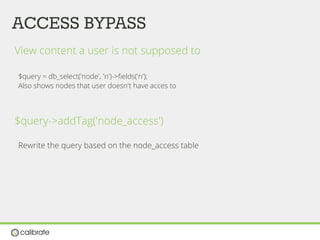

![ACCESS BYPASS
Rabbit_hole module
Rabbit Hole is a module that adds the ability to control what should happen
when an entity is being viewed at its own page.
Field access
$form['#access'] = custom_access_callback();
Menu access
$item['access callback'] = 'custom_access_callback',](https://image.slidesharecdn.com/drupal-security-seminar-130628091555-phpapp01/85/Drupal-Security-Seminar-58-320.jpg)