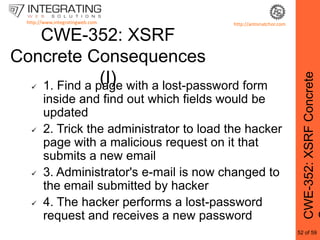
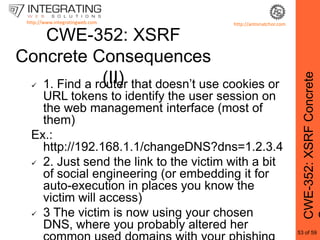
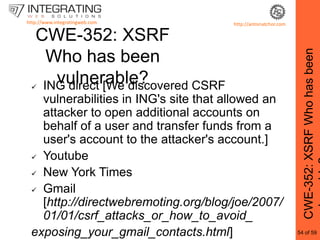
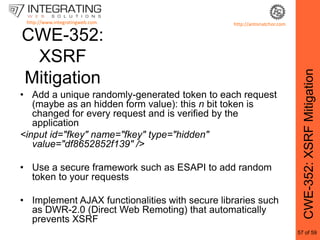
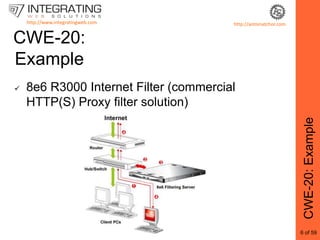
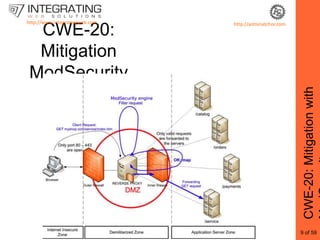
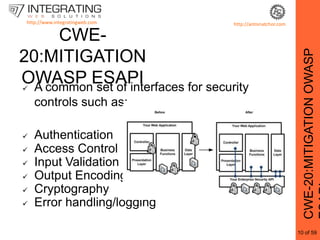
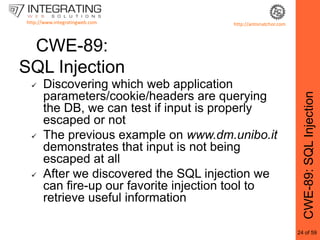
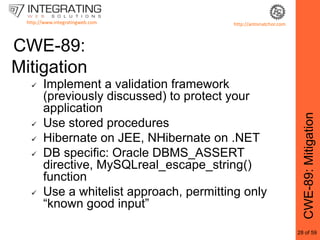
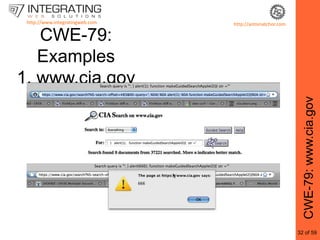
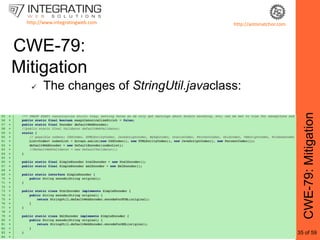
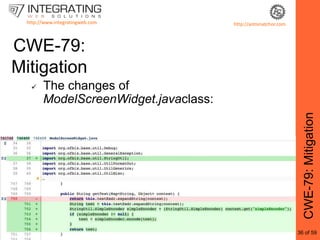
This document provides an outline for a seminar on web insecurity and browser exploitation. It introduces the speaker and their background and experience. The seminar will discuss the top 25 security errors from SANS, with practical demonstrations of vulnerabilities in real world web applications. Specific vulnerabilities that will be covered include improper input validation, improper output encoding, information leaks in error messages, SQL injection, and cross-site scripting. Mitigation strategies and frameworks for each vulnerability will also be discussed. Practical examples of discovered vulnerabilities are provided for selected websites.









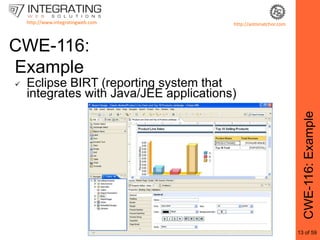



















![http://www.integratingweb.comhttp://antisnatchor.comCWE-116: ExampleCredits: antisnatchor[http://antisnatchor.com/2008/12/18/eclipse-birt-reflected-xss]](https://image.slidesharecdn.com/webinsecurityandbrowserexploitation-munichmicheleorru-jan2010-100129124709-phpapp02/85/Web-Insecurity-And-Browser-Exploitation-42-320.jpg)







![MySQL error when forging a malicious request altering the anno parameterGET /seminari/archivio.php?anno=2008%27 HTTP/1.1Host: www.dm.unibo.it[...]Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7Keep-Alive: 300Proxy-Connection: keep-aliveCookie: dm=[...]CWE-209: www.dm.unibo.it17 of 59](https://image.slidesharecdn.com/webinsecurityandbrowserexploitation-munichmicheleorru-jan2010-100129124709-phpapp02/85/Web-Insecurity-And-Browser-Exploitation-51-320.jpg)