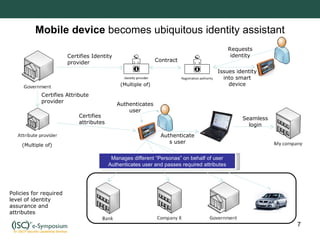
The document discusses the future of mobile devices as trusted personal identity management assistants. It outlines some of the challenges with digital identity in cyber space and how governments are working to address this through initiatives like NSTIC in the US and eID in the EU. The document proposes that mobile devices could become ubiquitous identity assistants, certifying identity and attribute providers and managing a user's different "personas". It discusses some of the necessary technologies and governance models required for mobile devices to securely fulfill this role.







![Mobile device as a trusted device: [4,5] How does mobile HW and OS hold up? Typically contains System on Chip (SoC) Load Kernel and mobile OS Load mobile applications If Trust is not assured from HW up then there is no trust at all! Enterprise apps accessed from mobile devices OS security capabilities are crucial Application segregation, security reviews](https://image.slidesharecdn.com/2011-07-19mobilephoneasiaemassistant-120104165012-phpapp01/85/Mobile-phone-as-Trusted-identity-assistant-9-320.jpg)
![Mobile threats summary [2] Web-based and network-based attacks – mobile device is connected, browsing websites with malicious content Malware – traditional viruses, worms, and Trojan horses Social engineering attacks – phishing. Also used to install malware. Resource and service availability abuse – botnet, spamming, overcharging (SMS and calls) Malicious and unintentional data loss – exfiltration of information from phone Attacks on the integrity of the device’s data – malicious encryption with ransom, modification of data (address book)](https://image.slidesharecdn.com/2011-07-19mobilephoneasiaemassistant-120104165012-phpapp01/85/Mobile-phone-as-Trusted-identity-assistant-10-320.jpg)
![Mobile Security Models [2] Traditional Access Control : passwords and idle-time screen locking. Application Provenance : Application signing and Application review in App store Encryption : Encryption of device data and application data Isolation : traditional Sandboxing and Storage separation Permissions-based access control : Limiting application to needed functionality only All must be supported by Trust from HW up. Jailbreaking breaks the security model!](https://image.slidesharecdn.com/2011-07-19mobilephoneasiaemassistant-120104165012-phpapp01/85/Mobile-phone-as-Trusted-identity-assistant-11-320.jpg)