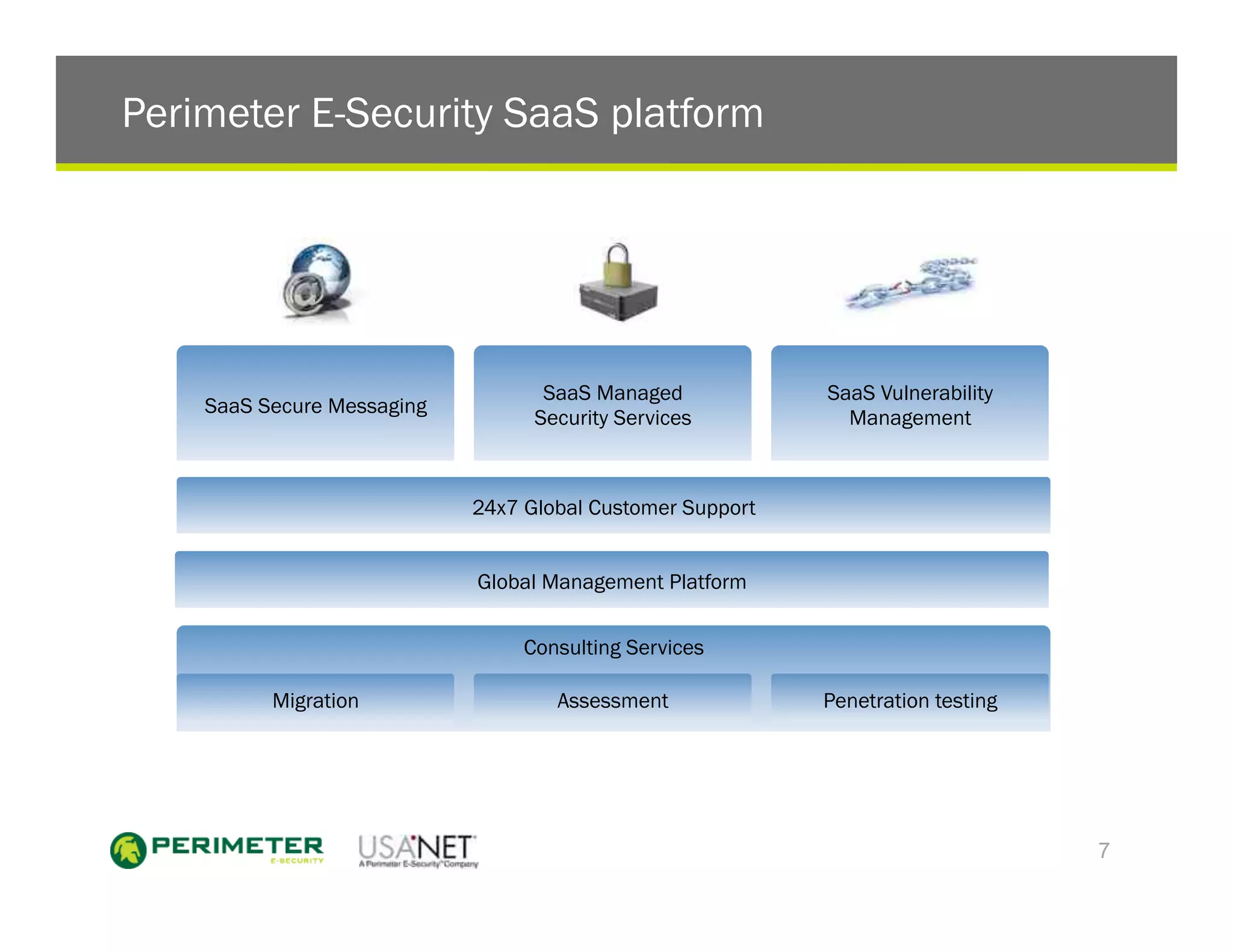
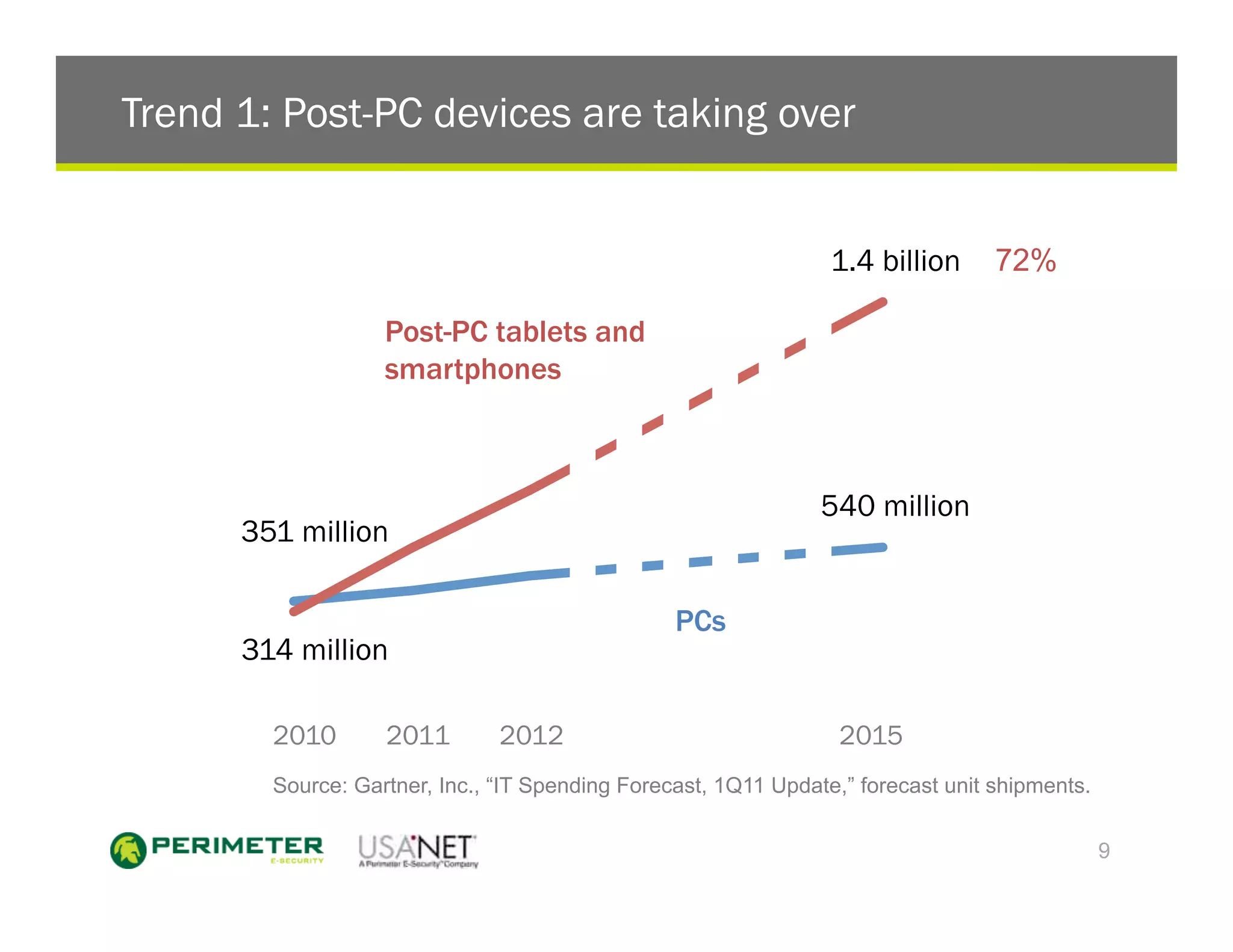
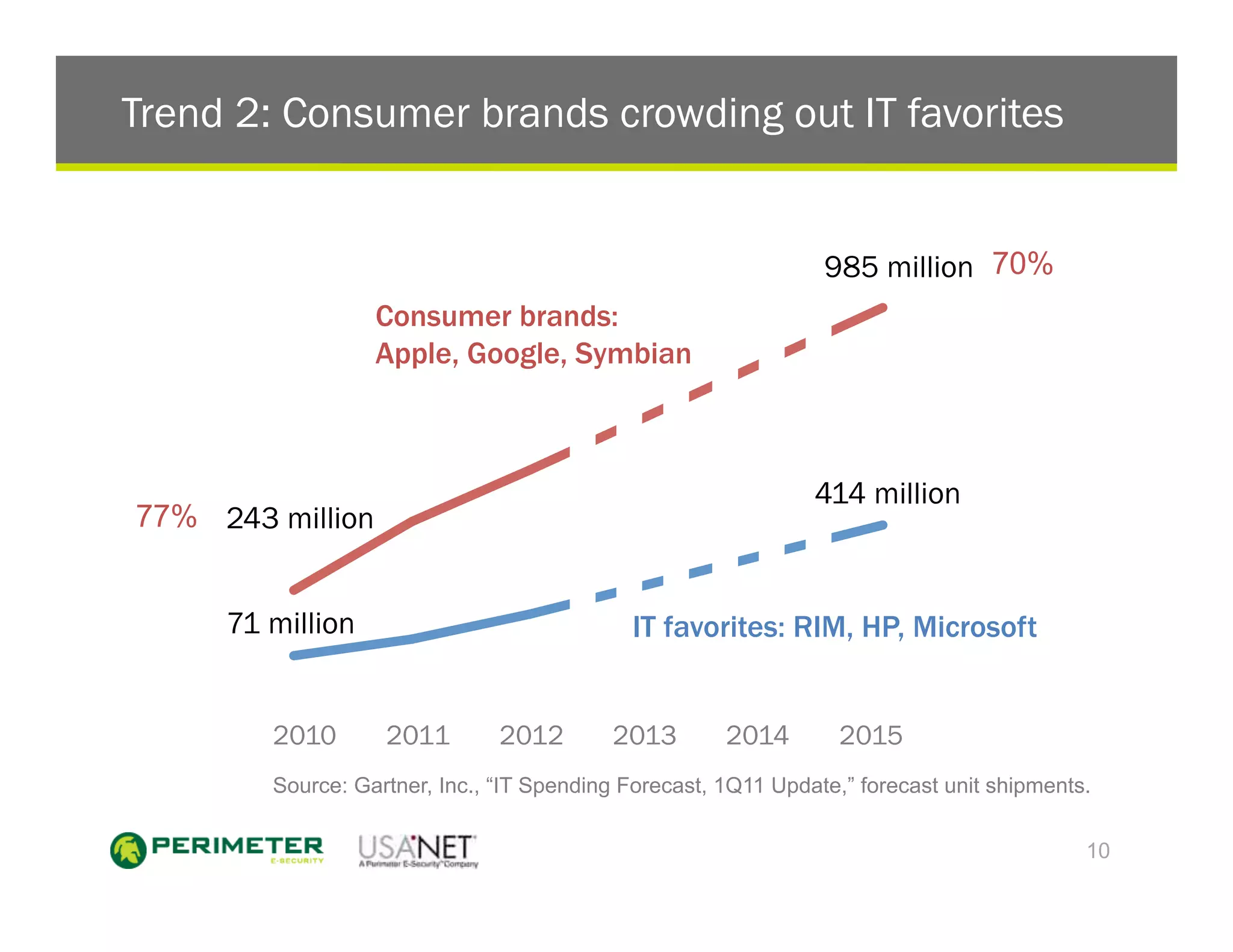
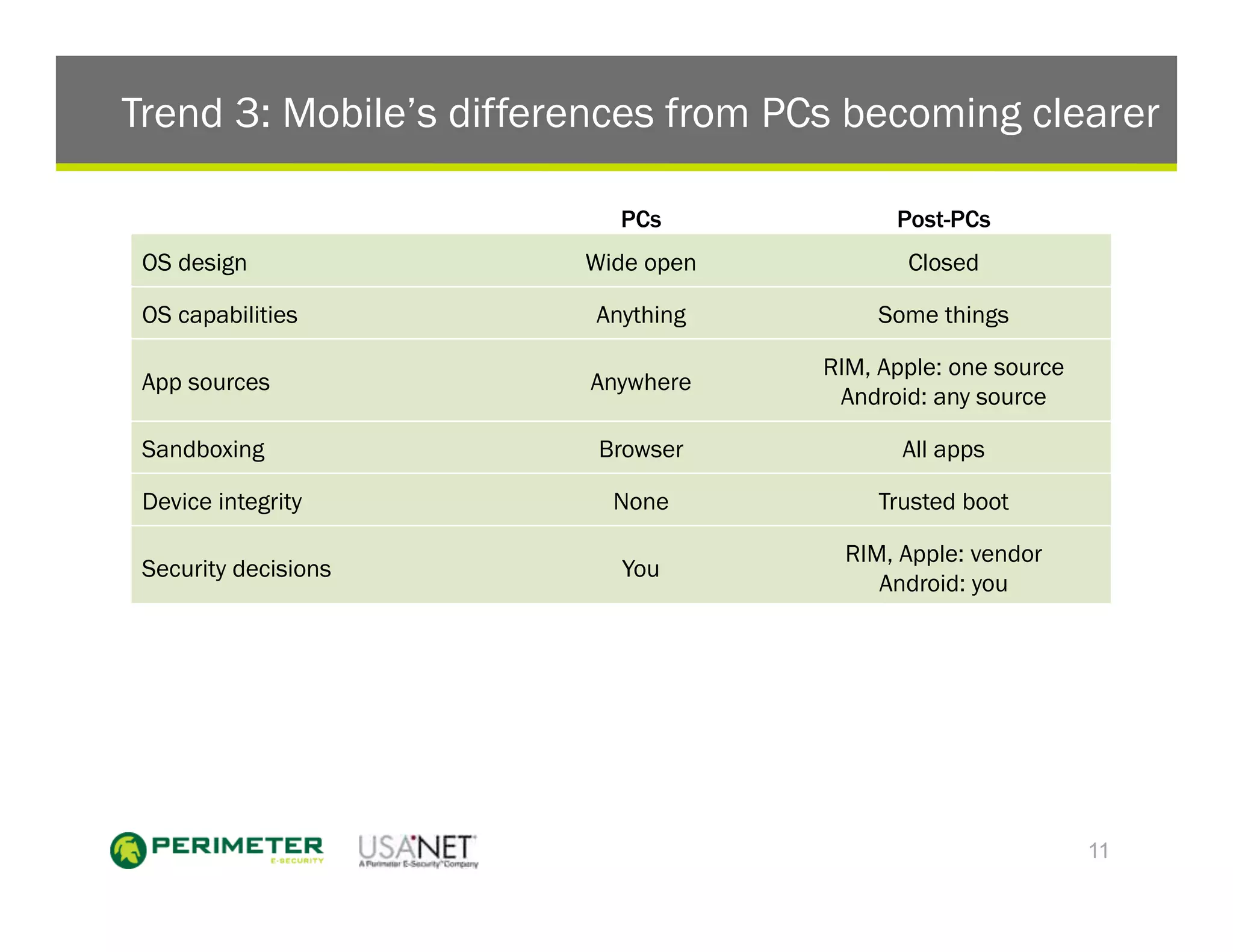
1) The document discusses the trends of post-PC devices taking over the market and consumer brands crowding out traditional IT favorites. It also outlines how mobile operating systems differ from PCs in being more closed and focused on security.
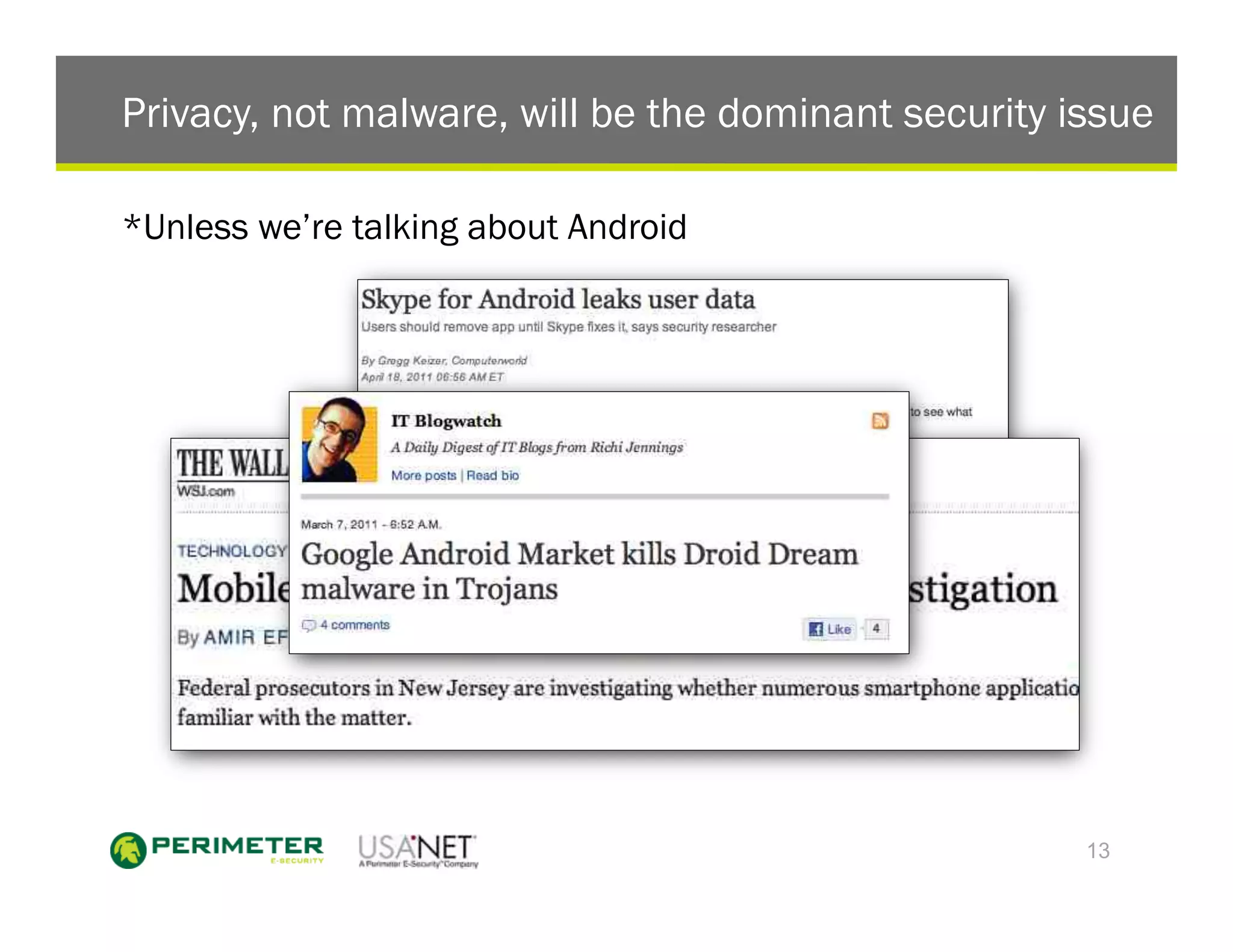
2) It recommends that enterprises do not need mobile antivirus except for Android devices. They also do not need mobile data leak prevention or enforcing the same device brands.
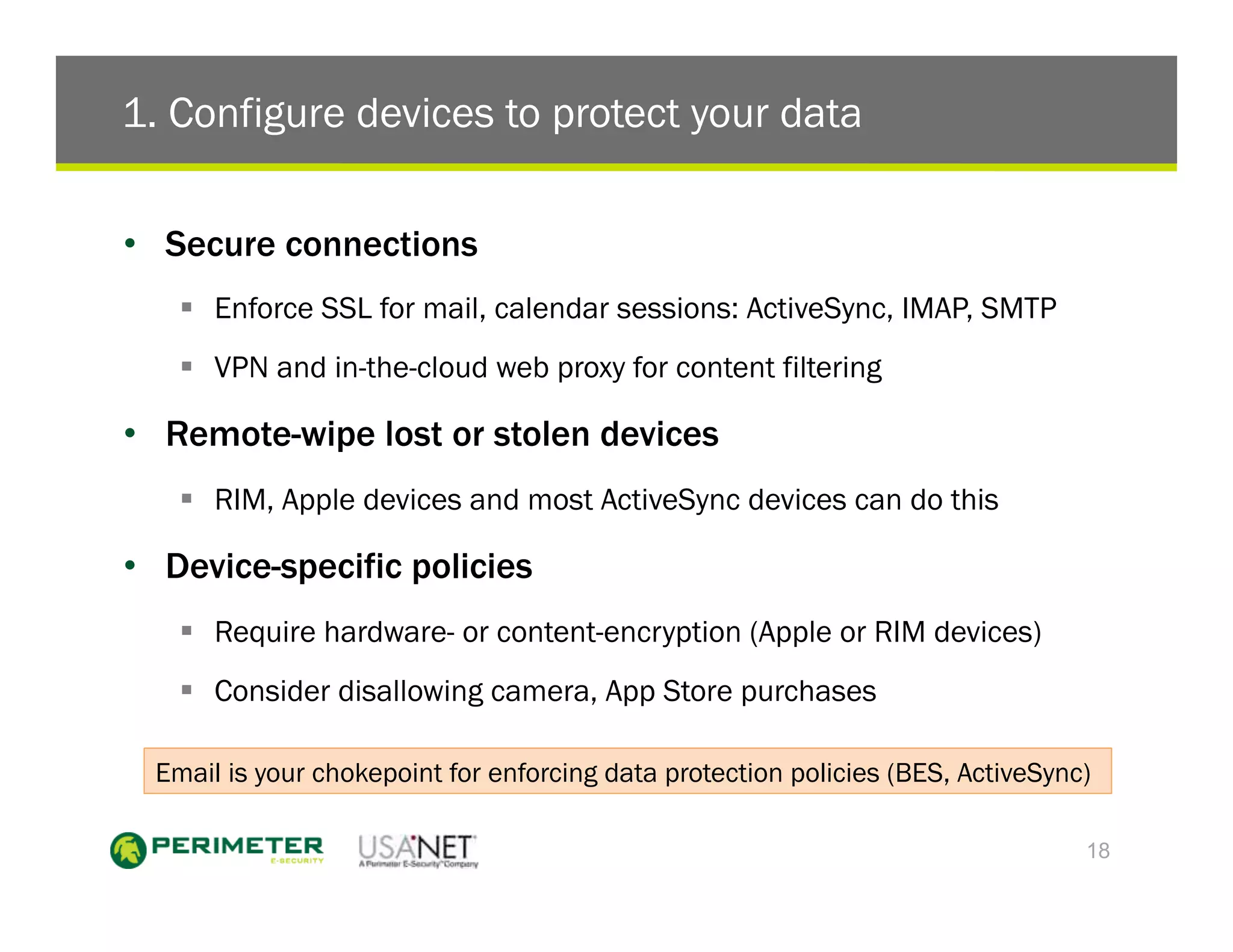
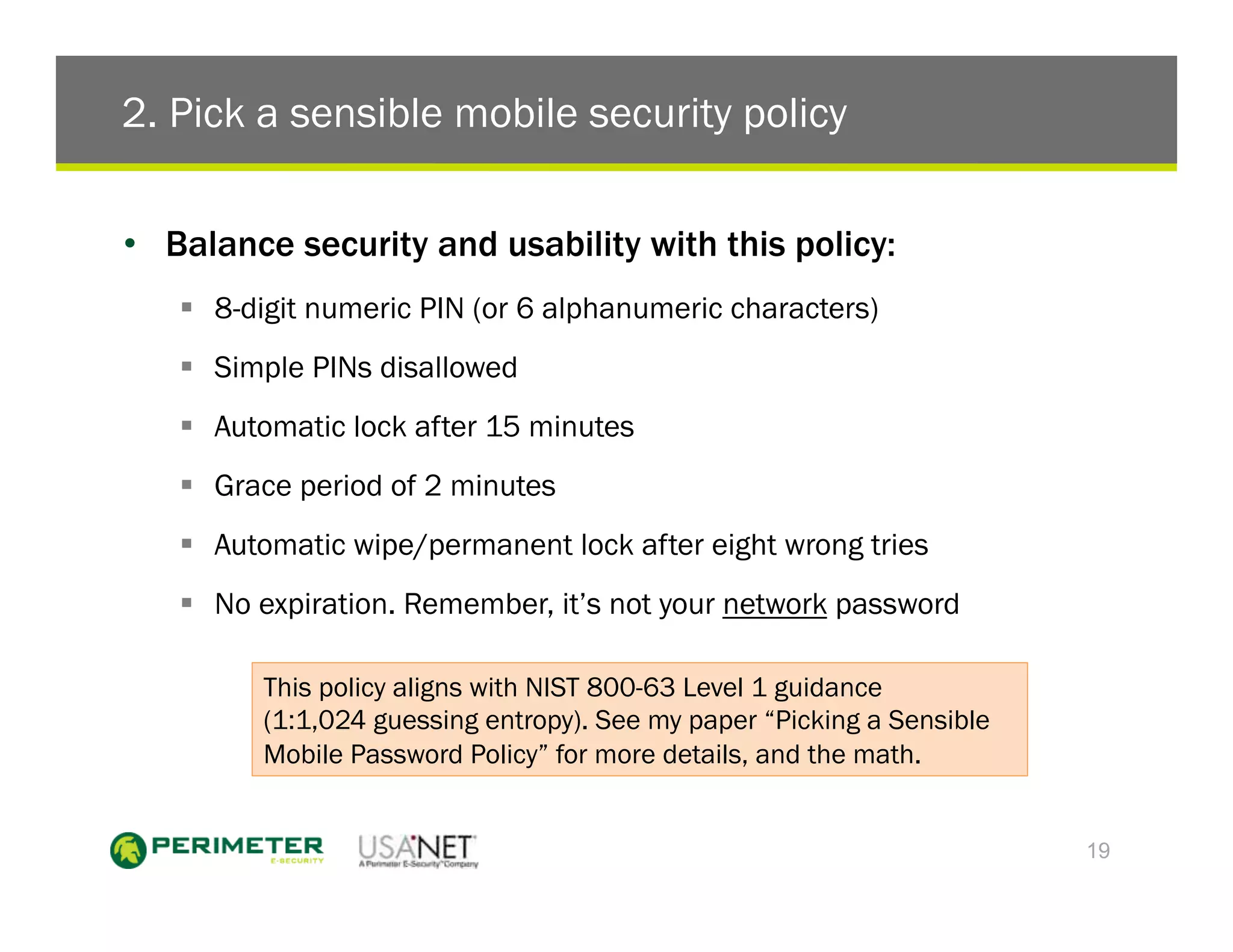
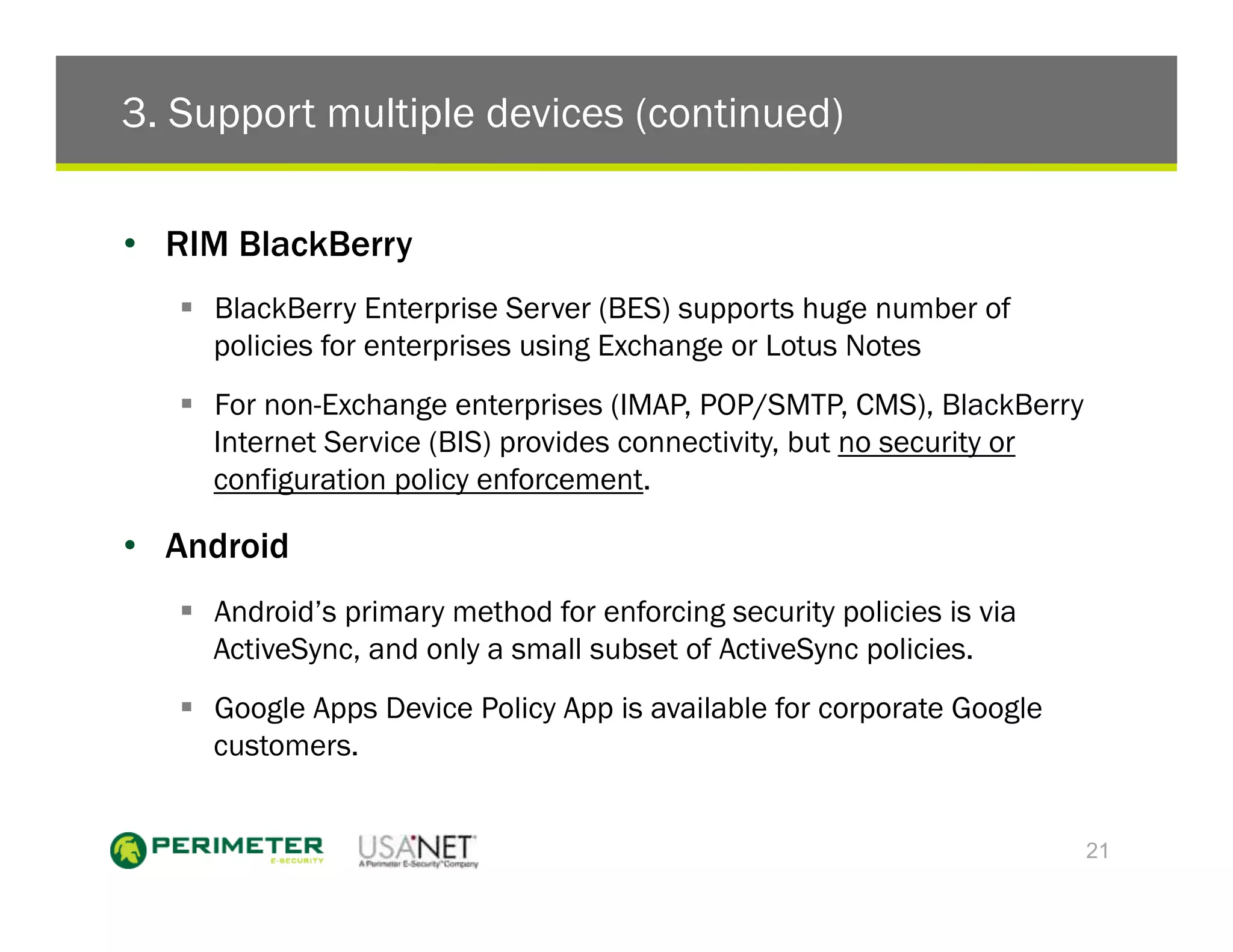
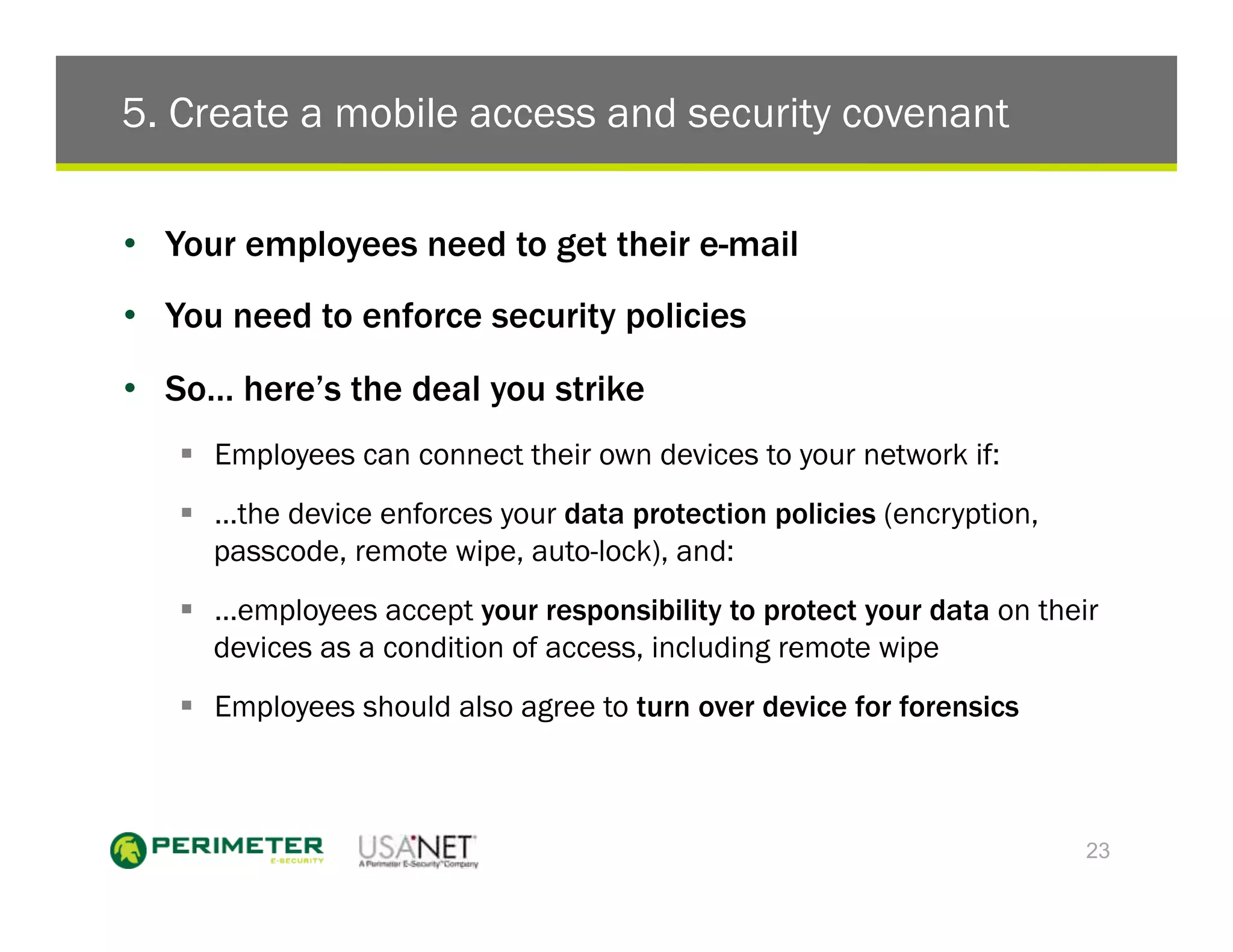
3) The document outlines five things enterprises must do which include configuring devices to protect data, picking a sensible mobile password policy, supporting multiple devices, merging mobile IT and security teams, and creating a mobile access security covenant.