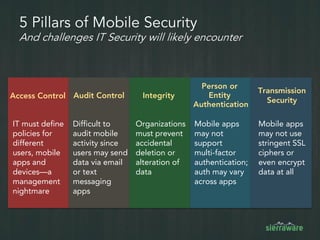
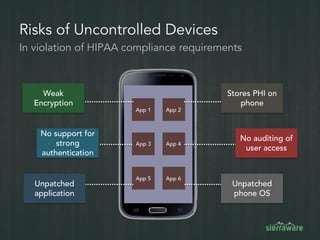
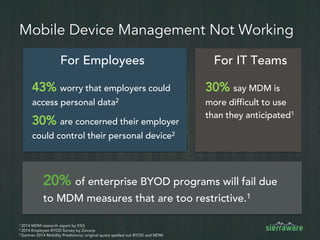
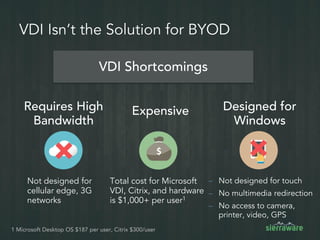
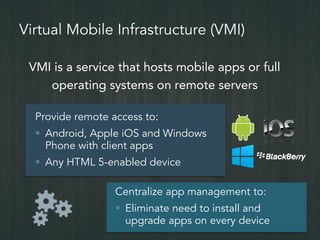
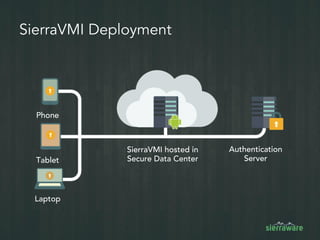
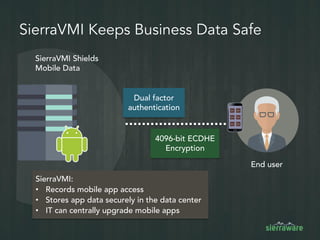
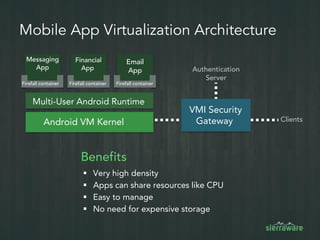
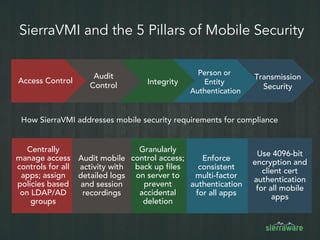
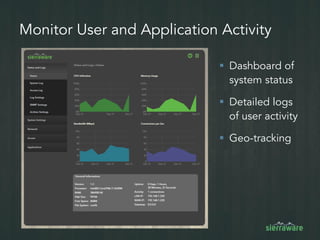
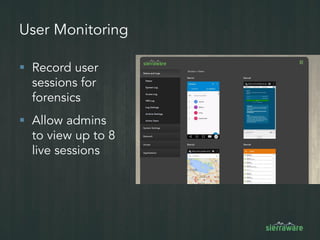
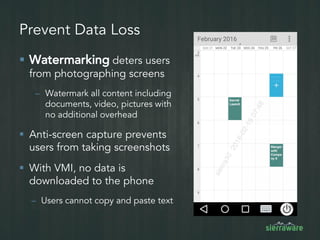
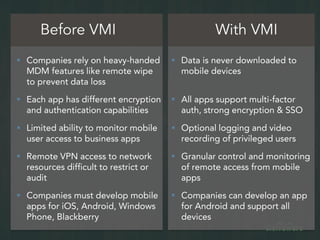
The document outlines the importance of mobile security in the banking and finance sector, highlighting the need for effective data protection and compliance with regulations such as SOX and FINRA. It discusses the challenges posed by BYOD policies, including risks from mobile devices and the prevalence of cyber threats, while promoting the benefits of Virtual Mobile Infrastructure (VMI) solutions like Sierravmi for centralized app management and enhanced security. Key features include strong authentication, encryption, and the prevention of data loss, emphasizing the necessity for organizations to adapt their mobile security strategies.