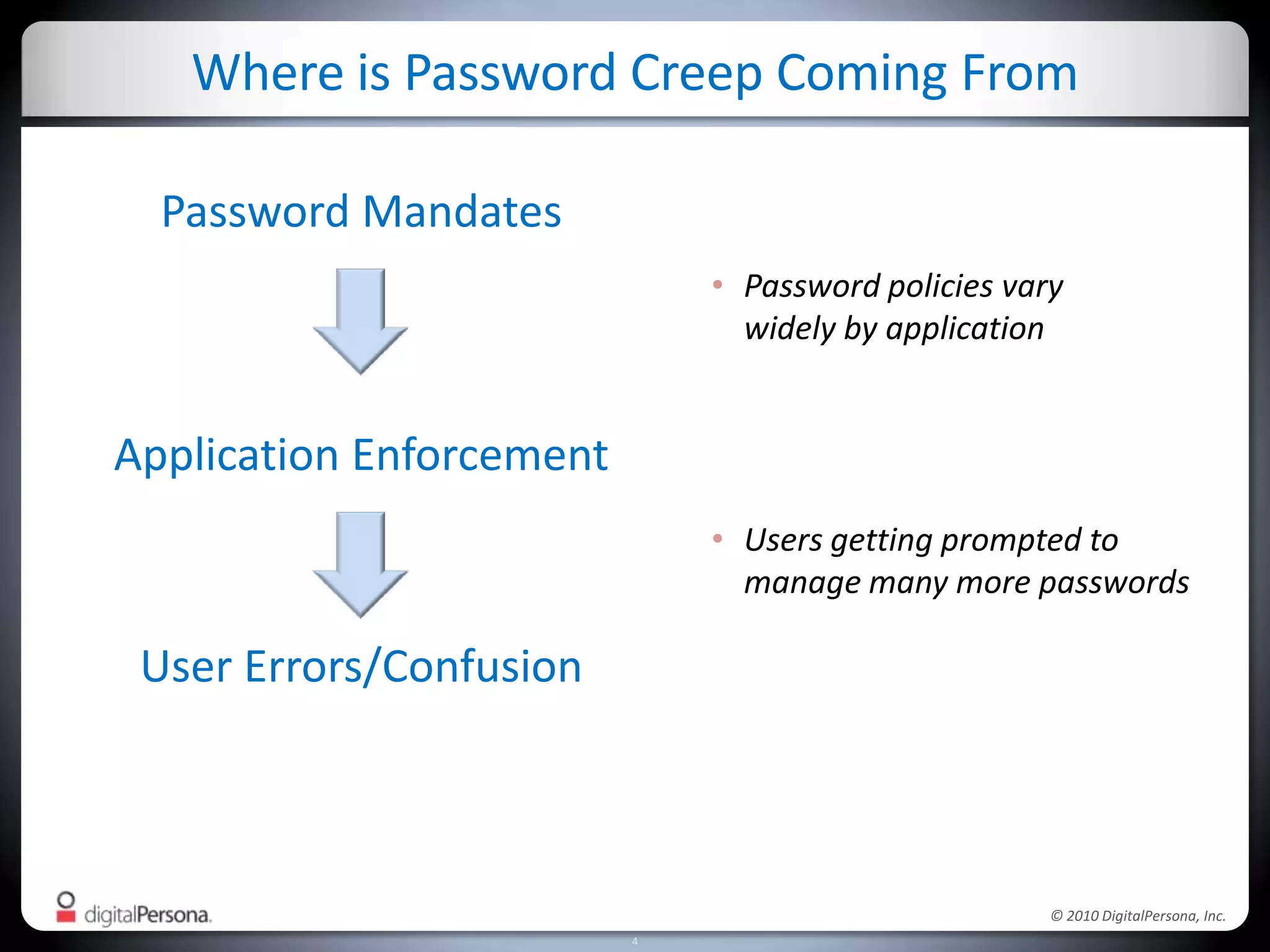
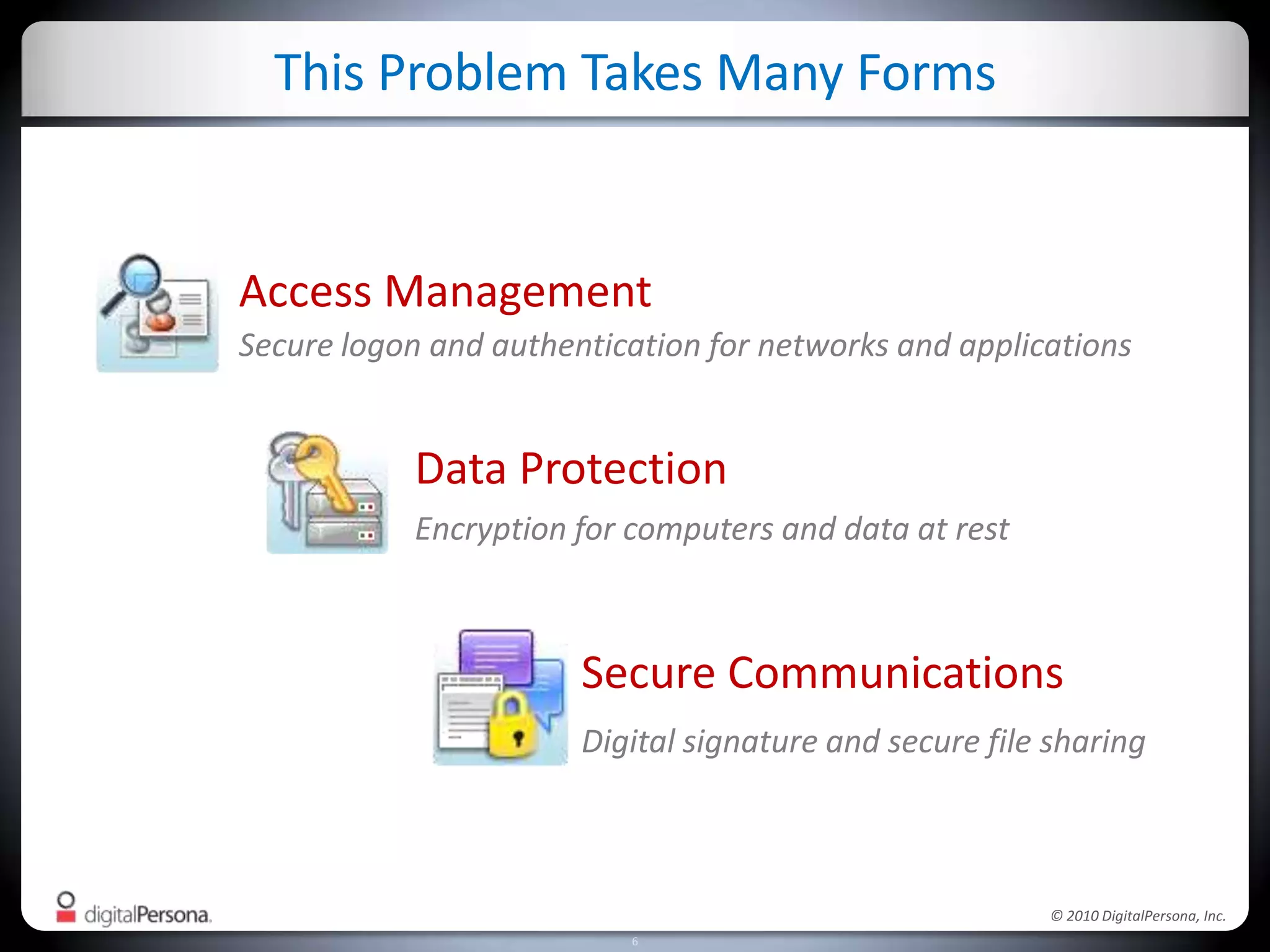
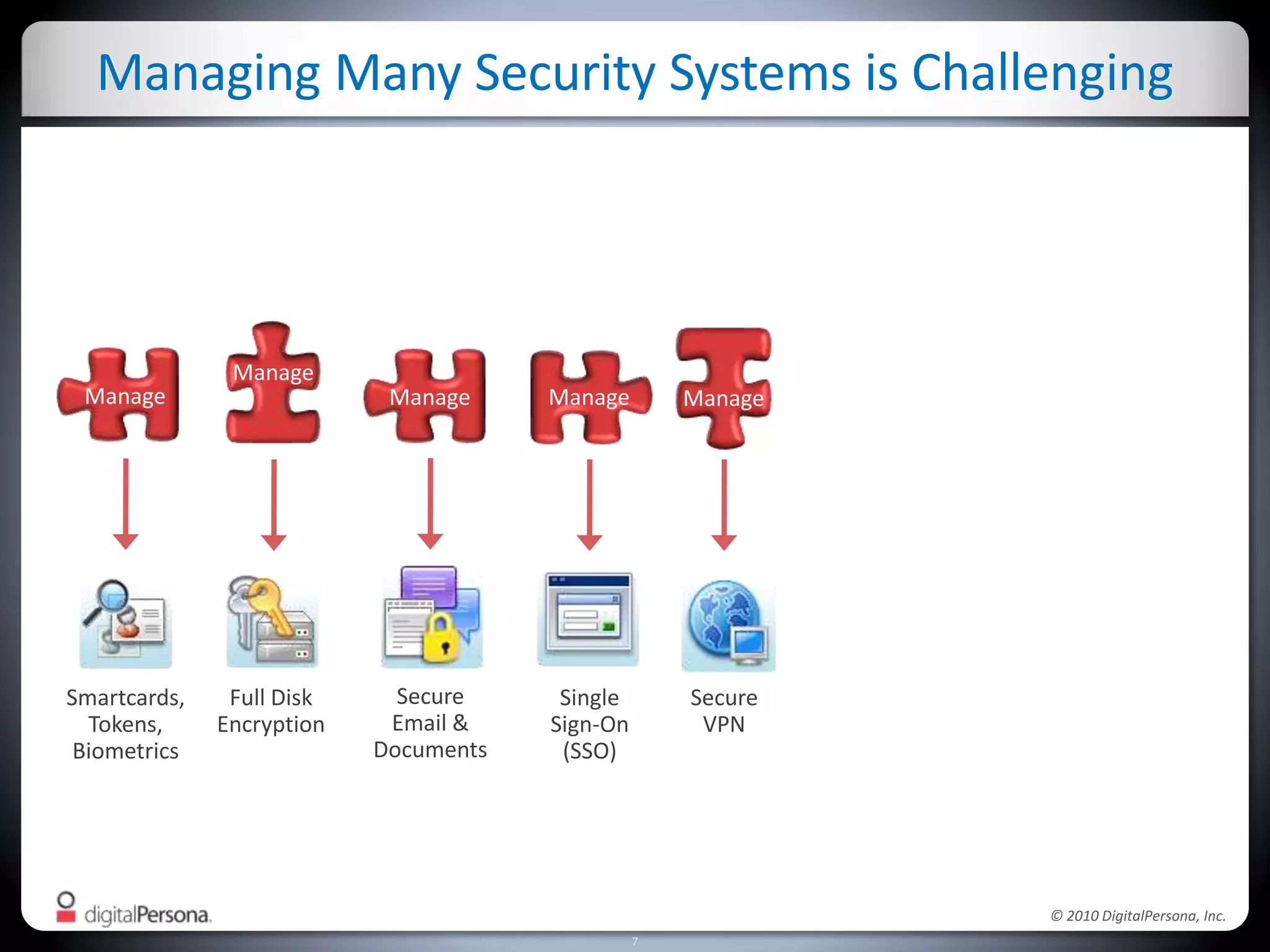
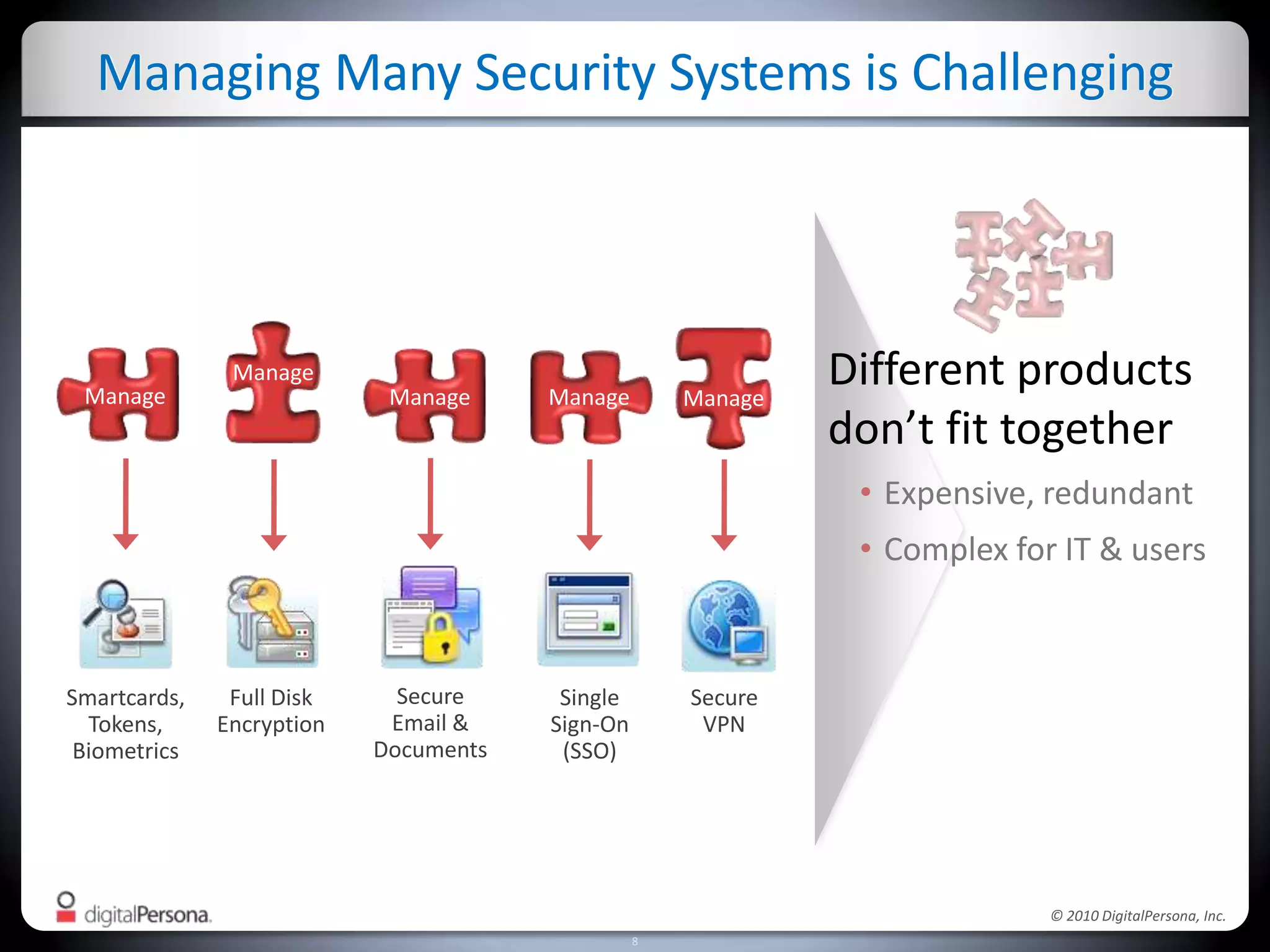
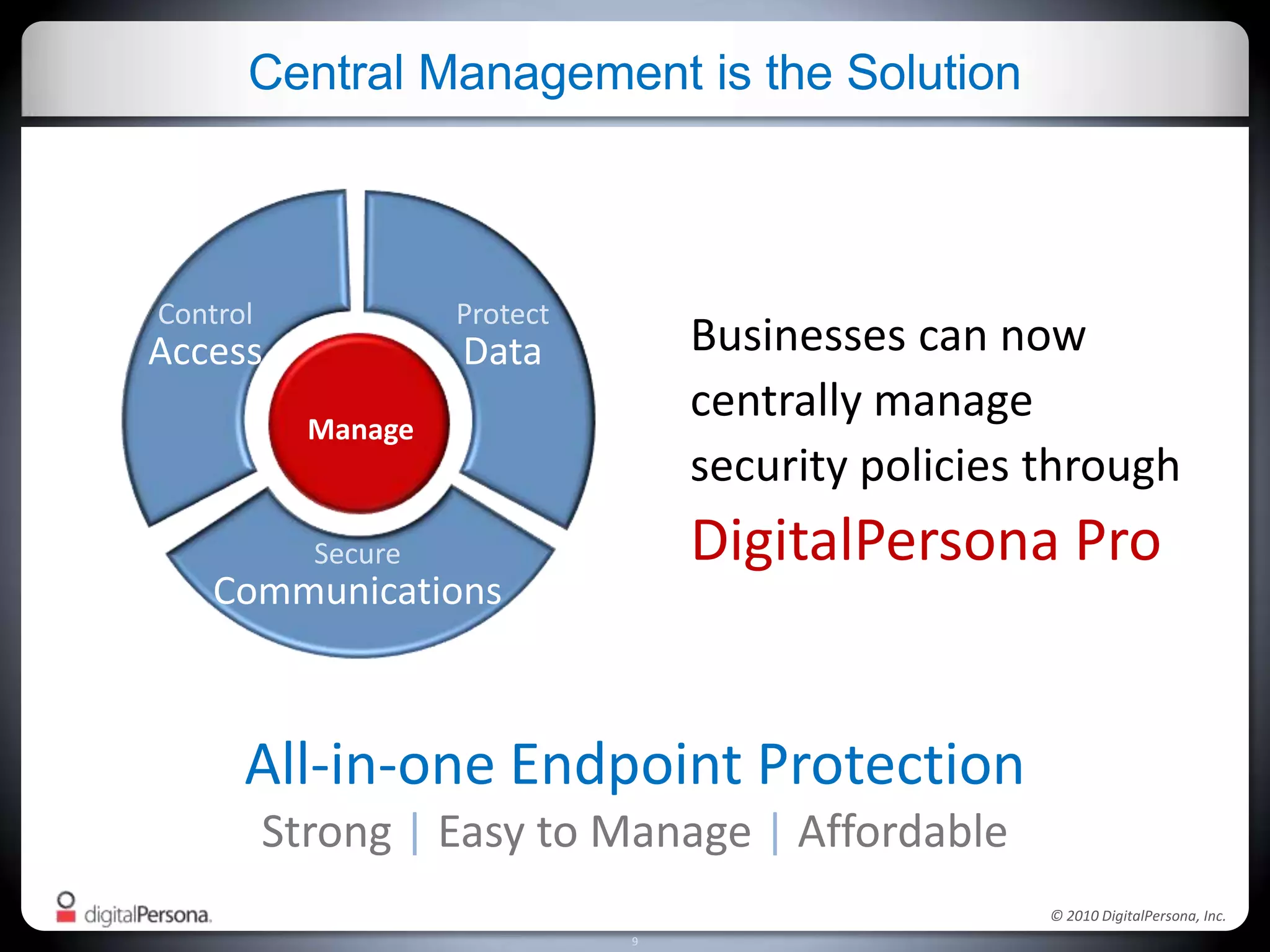
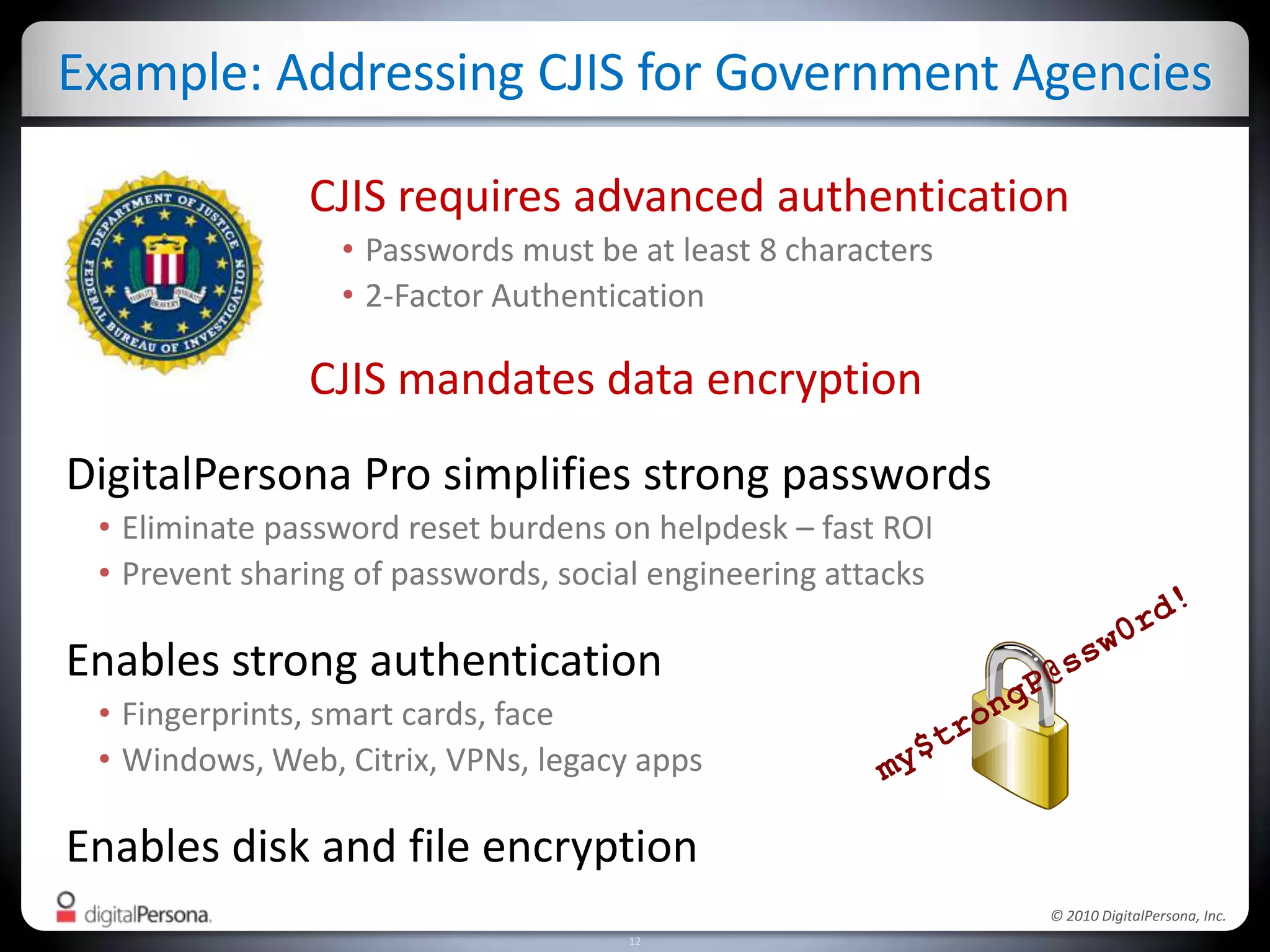
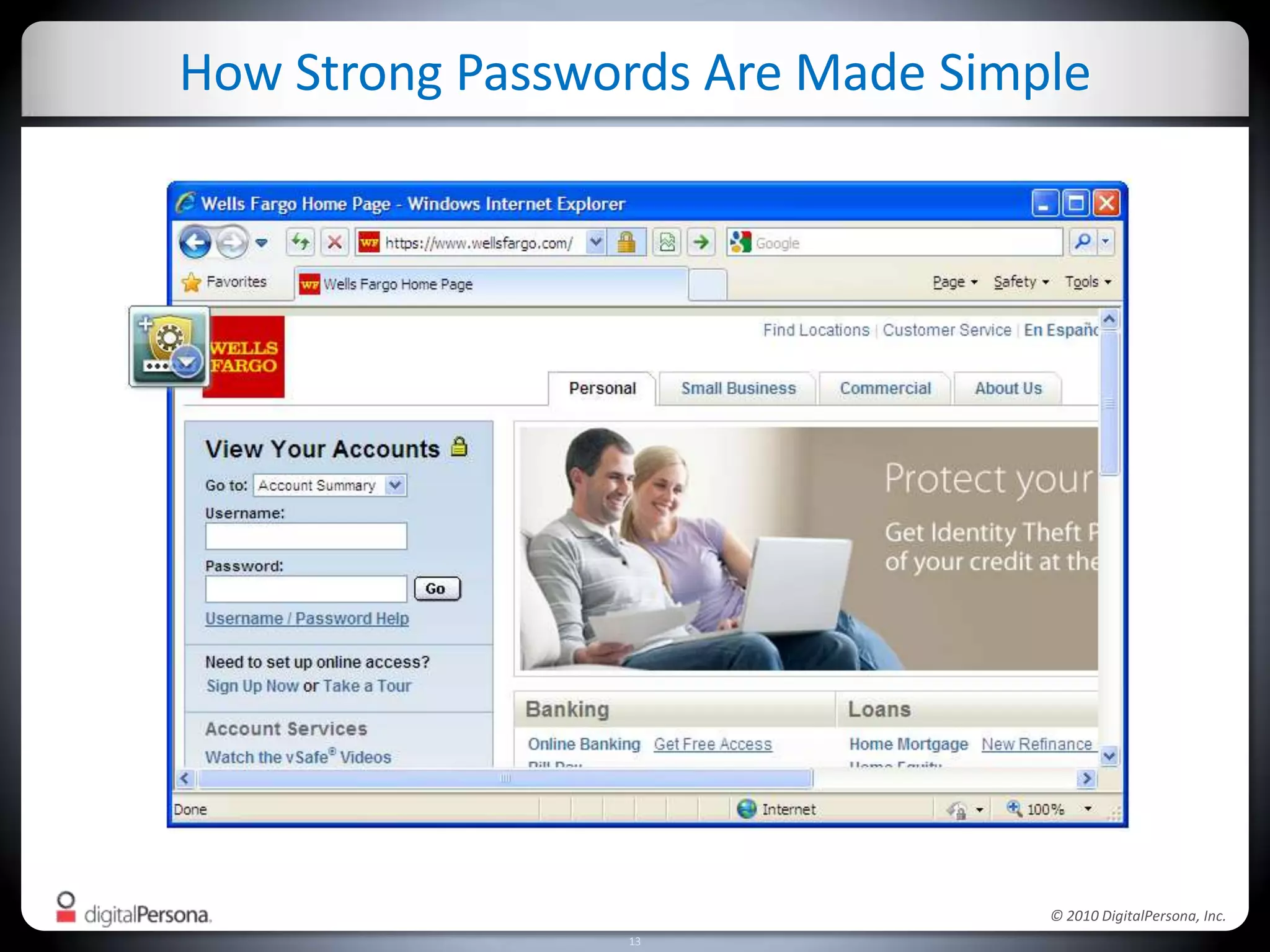
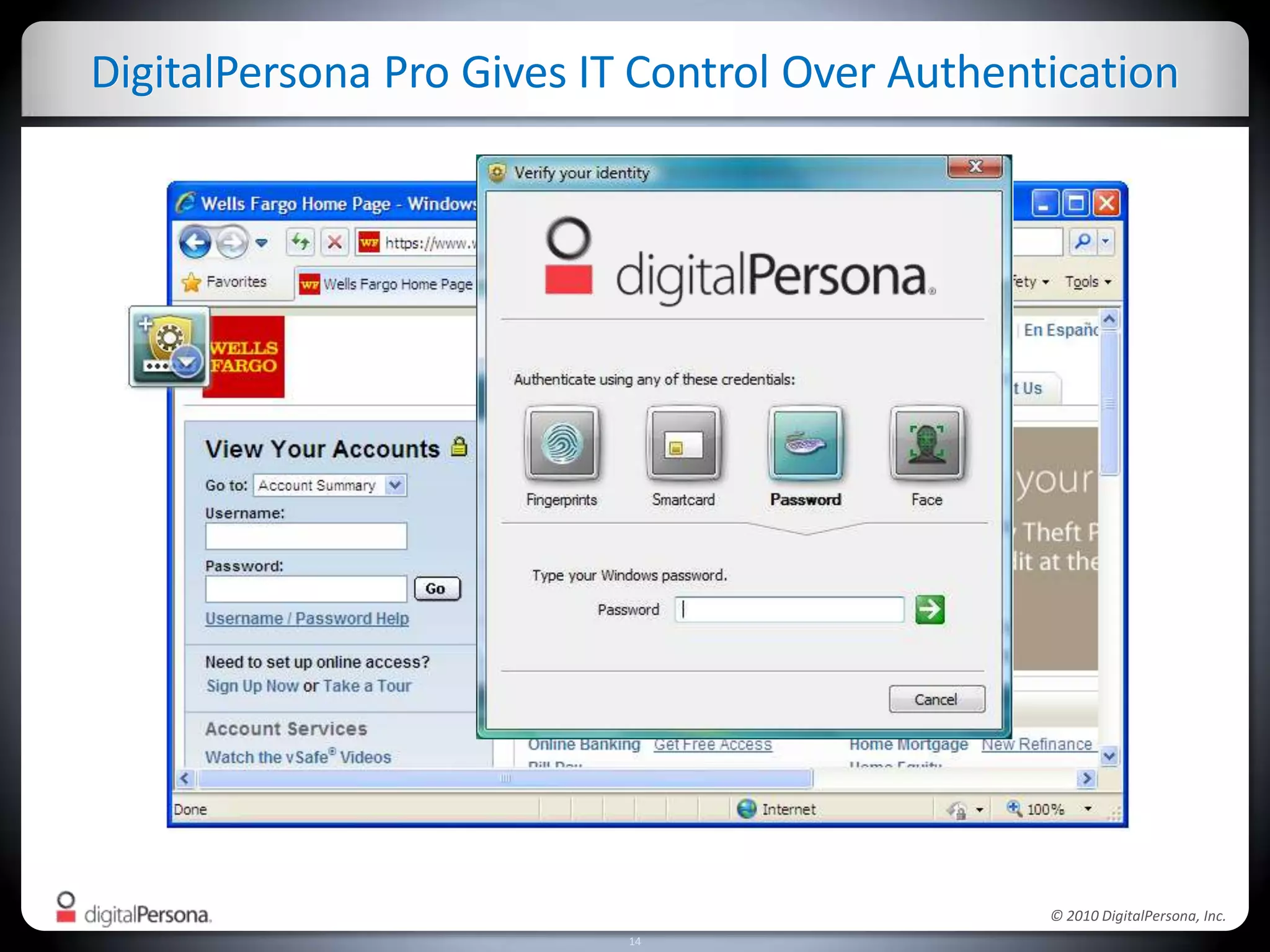
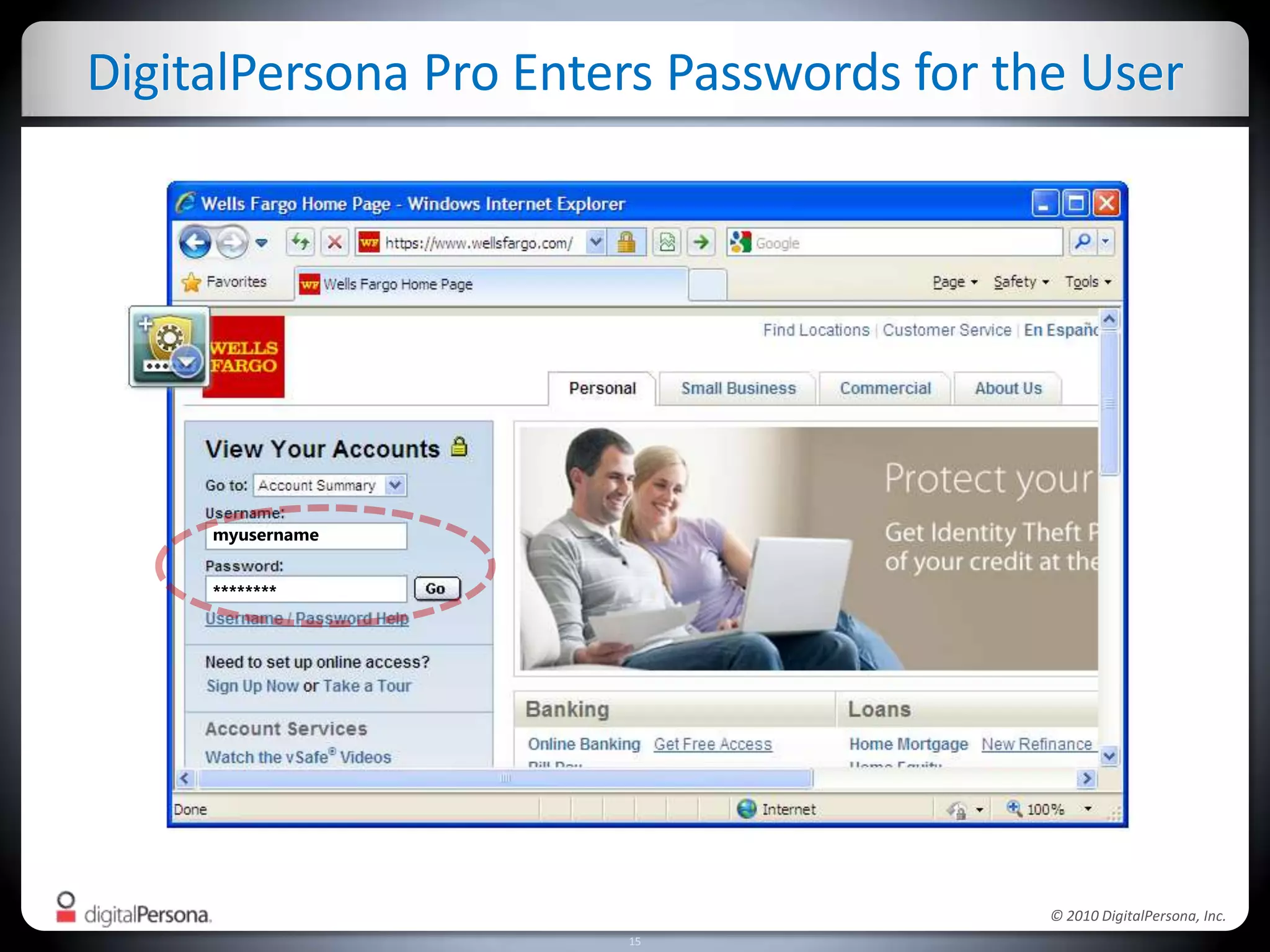
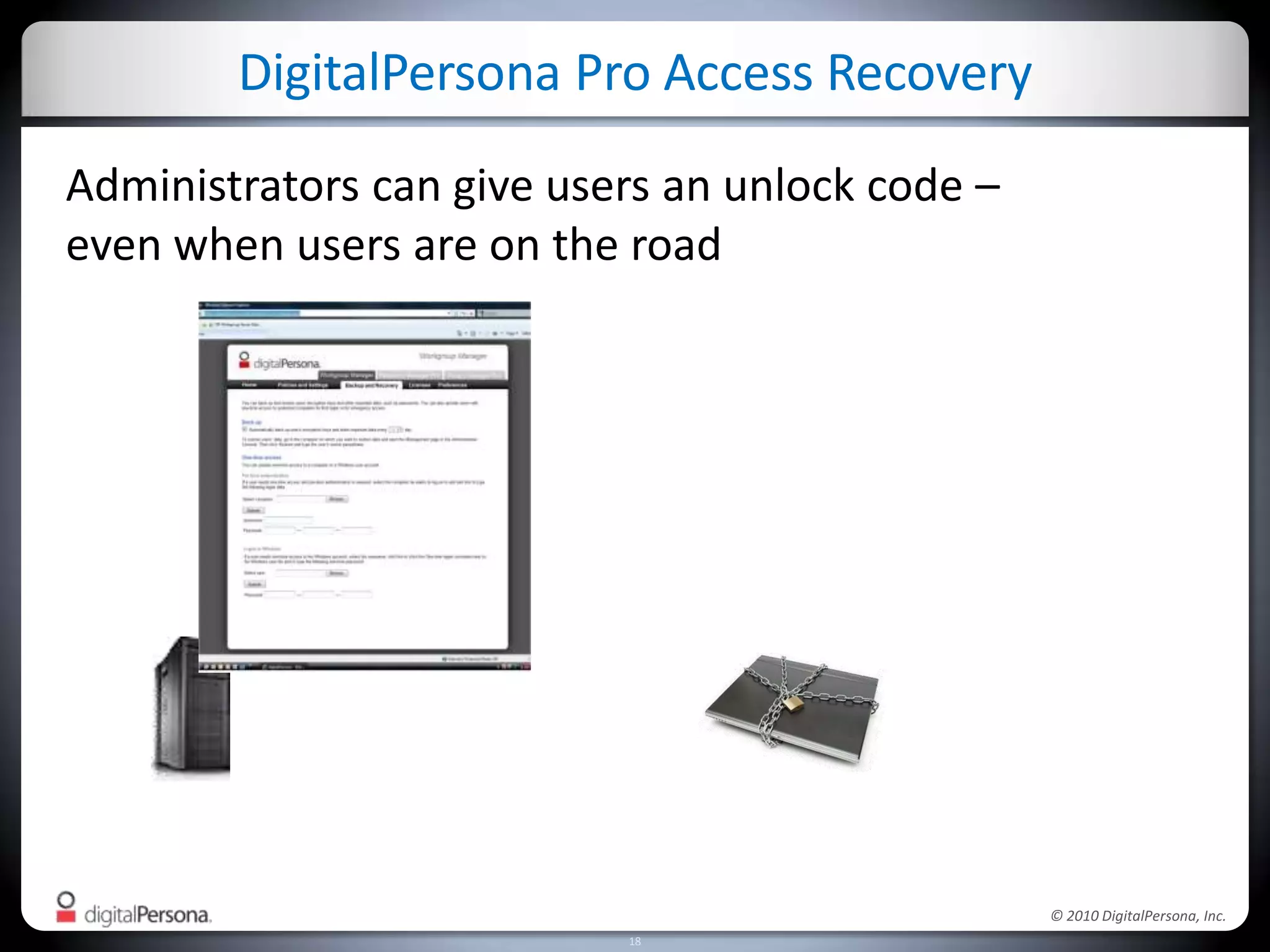
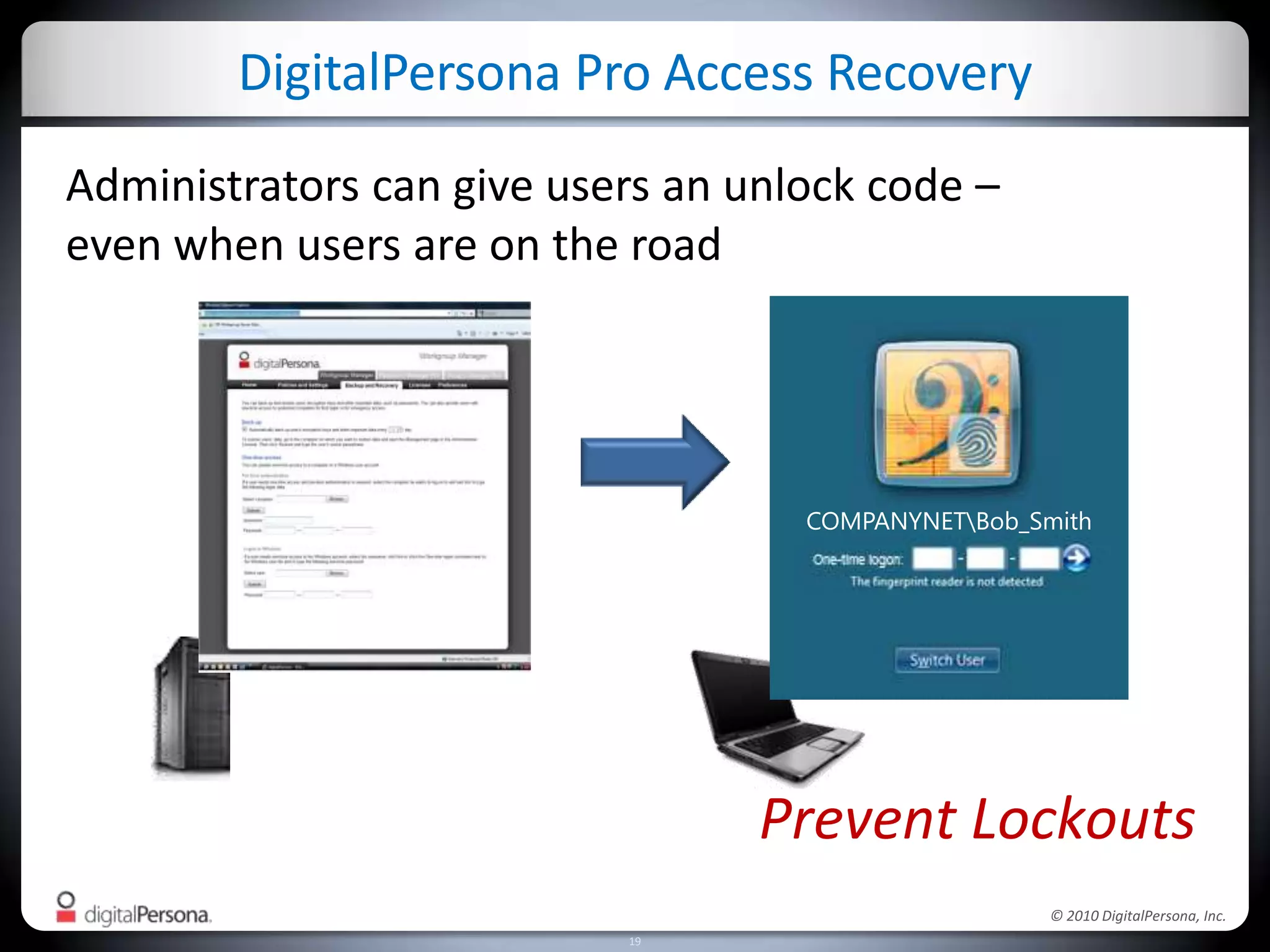
DigitalPersona Pro offers centralized management solutions for authentication and security, addressing the challenges of password management and compliance faced by businesses. With features like strong authentication, data encryption, and simplified access recovery, it aims to reduce the burden of password complexity and enhance productivity. The platform is particularly beneficial for sectors requiring high security, such as government and healthcare, ensuring compliance with regulations while streamlining processes.