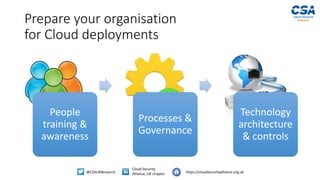
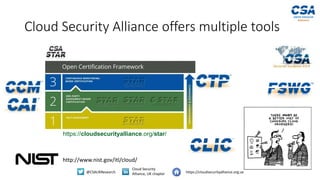
The document discusses the importance of cloud security for organizations and highlights key tools and strategies for C-level executives to make informed decisions about cloud adoption. It outlines essential requirements for cloud service procurement, such as ensuring data security, compliance with regulations, and conducting due diligence on cloud providers. Additionally, it encourages participation in the development of new cloud security guidance from the Cloud Security Alliance.