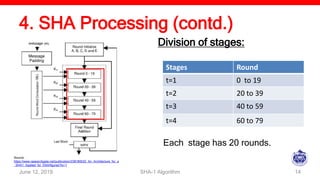
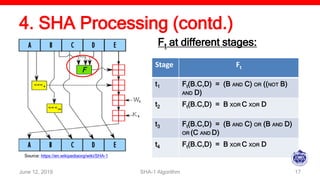
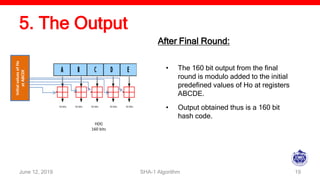
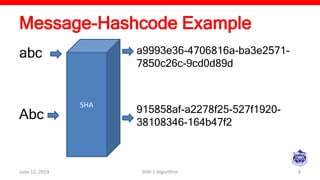
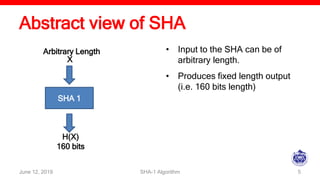
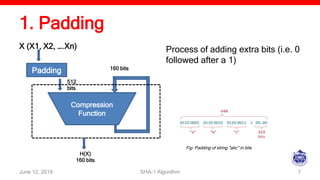
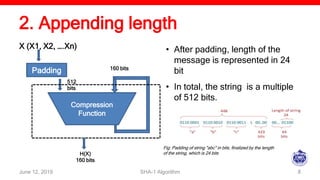
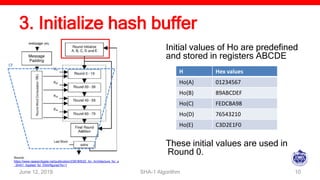
The document describes the SHA-1 hashing algorithm. SHA-1 produces a 160-bit hash value from an input of arbitrary length. It works by padding the input, appending the length, initializing hash buffers, processing the message through 80 rounds of compression, and outputting the final hash value. The compression function divides the padded message into 16-word blocks and schedules the words through the rounds using a message scheduling algorithm. It performs logical and bitwise operations on the words and chaining variables to generate a new hash.






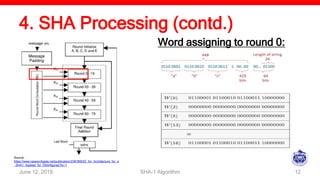
![4. SHA Processing (contd.)
June 12, 2019 SHA-1 Algorithm 13
Source:
https://www.researchgate.net/publication/238180532_An_Architecture_for_a
_SHA1_Applied_for_DSA/figures?lo=1
Word assigning to other rounds:
For others (i.e round 16- 79)
W[t] = S1(w[t-16] XOR W[t-14] XOR W[t-8] XOR W[t-3])
For example: when round is 16,
• W[16] = S1(w[16-16] XOR W[16-14] XOR W[16-8] XOR W[16-3])
• Here W0, W2, W8 and W13 are XORed.
• The output is the new word for round 16.](https://image.slidesharecdn.com/sha-1algorithm-190612032648/85/SHA-1-Algorithm-13-320.jpg)