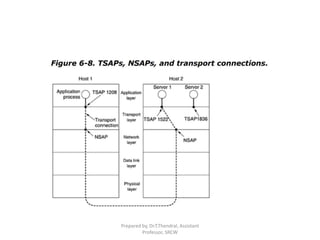
The document discusses various elements of transport layer protocols including establishing connections, addressing, connection establishment, disconnecting connections, flow control, buffering, multiplexing, and crash recovery. Specifically, it describes how connections are established between processes using transport service access points (TSAPs) and addresses (NSAPs), how three-way handshakes are used to set up and tear down connections, and how transport protocols handle issues like flow control, multiplexing of data streams, and recovering from crashes.