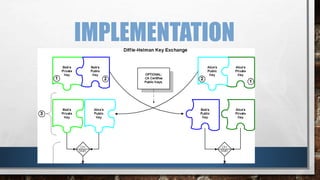
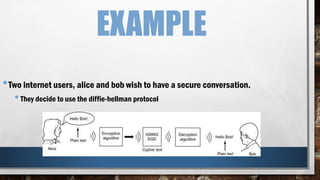
This document discusses man-in-the-middle attacks against cryptographic protocols. It describes two classes of man-in-the-middle attacks - passive attacks where the attacker can only monitor communications, and active attacks where the attacker can modify messages. It then gives an example of how a man-in-the-middle attack works against key exchange protocols by replacing one party's public key. Finally, it provides an example of how the Diffie-Hellman key exchange protocol allows two parties to securely generate a shared secret key to prevent such man-in-the-middle attacks.