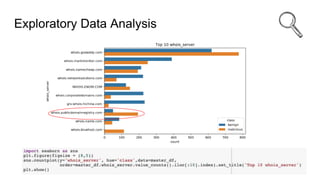
This document discusses using machine learning and Python to detect malicious URLs. It presents a threat science framework with stages including know the user, know the threat, data acquisition and understanding, feature engineering, modeling and evaluation, and deployment. For detecting malicious URLs specifically, it describes collecting benign and malicious URL data, exploring and engineering features, using models like random forest and deep neural networks, and evaluating performance with metrics like F1 score and confusion matrices. Parameter tuning and model explainability are also covered. The overall goal is to build an intelligent ecosystem of ML models to provide superior cyber defense against evolving threats.