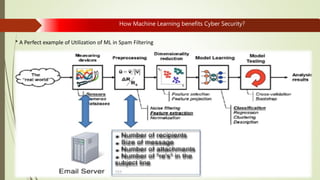
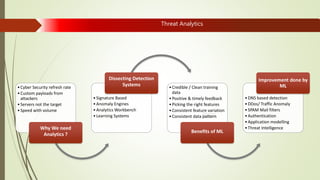
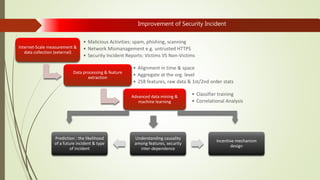
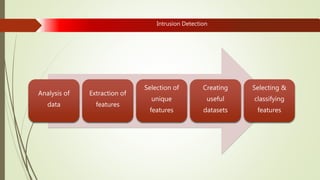
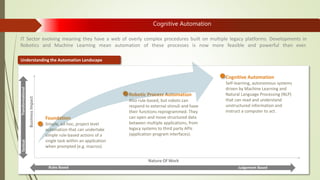
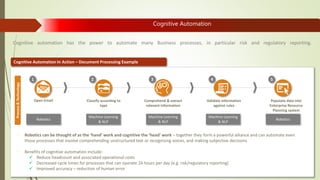
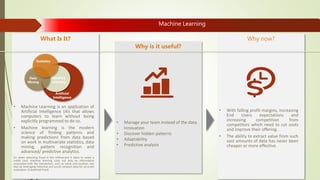
Machine learning and artificial intelligence techniques are increasingly being used in cyber security to detect threats like malware, fraud, and intrusions. By analyzing large amounts of data, machine learning algorithms can learn patterns of both normal and anomalous behavior and make predictions about new or unseen data. This allows threats to be identified more accurately and in real-time without being explicitly programmed. Some key benefits of machine learning for cyber security include improved spam filtering, malware detection, identifying advanced threats, and detecting insider threats and data leaks. It is helping to address challenges of data overload, speed of threats, and unknown threats that traditional rule-based detection was unable to handle effectively.

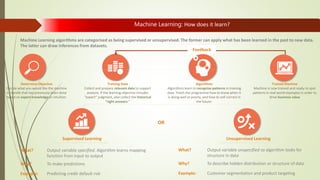

![How Machine Learning benefits Cyber Security?
Traditionally Cyber Security
Deals problems were aided by Mathematical model.
e.g. – Data transformation[cryptography]
Modern Cyber Security
Deals with abstract threats which cannot be solved only by using mathematical models.
E.g. - Malware detection,
Intrusion detection,
Data leakage
SPAM mitigation
etc
Solution of Modern Cyber Security](https://image.slidesharecdn.com/mlforcs-rishikant-180917100045/85/Machine-Learning-in-Cyber-Security-5-320.jpg)