This document summarizes the Linux audit system and proposes improvements. It begins with an overview of auditd and how audit messages are generated and processed in the kernel. Issues with auditd's performance, output format, and filtering are discussed. An alternative approach is proposed that uses libmnl for netlink handling, groups related audit messages into JSON objects, applies Lua-based filtering, and supports multiple output types like ZeroMQ and syslog. Benchmark results show this rewrite reduces CPU usage compared to auditd. The document advocates for continued abstraction and integration of additional data sources while avoiding feature creep.










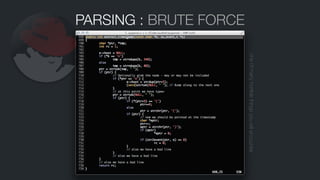
![FORMAT DISAPPROBATION :(
The kernel is to blame for this shameful log format!
audit_log_format(ab,"a0=%lx a1=%lx a2=%lx a3=%lx items=%d"
" ppid=%d pid=%d auid=%u uid=%u gid=%u"
" euid=%u suid=%u fsuid=%u"
" egid=%u sgid=%u fsgid=%u tty=%s ses=%u",
context->argv[0], context->argv[1], ...);
b u t w h a t i s t h e a l t e r n a t i v e ?
You’re insane. A JSON encoder in the kernel?
You’re insane.
An overly complex binary
message format?
How about this JSON thing I’ve
been hearing so much about?](https://image.slidesharecdn.com/audit-140509143909-phpapp01/85/Audit-13-320.jpg)





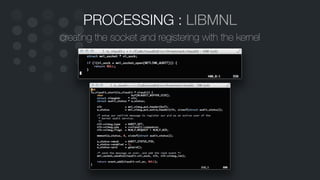
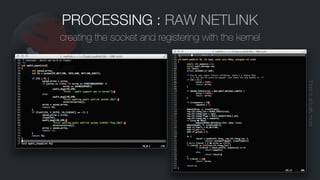

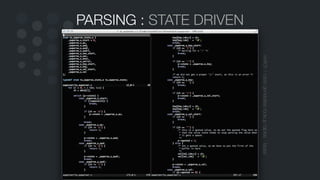
![PROCESSING : MESSAGE GROUPS
an abstract example; executing “tail -f tsaudit.log”
- serial=43480, type=SYSCALL, syscall=“sys_execve”, exe=“/usr/bin/tail”
- serial=43480, type=EXECVE, argc=2, a0=“tail”, a1=“tsaudit.log”
- serial=43480, type=CWD, cwd=“/var/log”
- serial=43480, type=PATH, name=“/usr/bin/tail”
- serial=43480, type=EOE
ungrouped
grouped
[
{
“type" : "SYSCALL",
“syscall" : "execve",
“exe" : "/usr/bin/tail"
},
{
“type" : "EXECVE",
“argc" : 2,
“argv” : [ “tail”, “tsaudit.log” ],
},
{
“type" : "CWD",
“cwd" : "/var/log"
},
{
"type": "PATH",
"name": "/usr/bin/tail"
}
]](https://image.slidesharecdn.com/audit-140509143909-phpapp01/85/Audit-26-320.jpg)
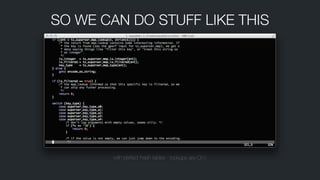
![PROCESSING : MESSAGE GROUPSA few more fun examples of grouping.
[
{
"exe": "/bin/cat",
"comm": "cat",
"ses": 10,
"auid": 4294967295,
"pid": 31335,
"ppid": 31334,
"items": 2,
"exit": 0,
"success": "yes",
"syscall": "execve",
"epoch": 1399248110,
"serial": 855516,
"type": "SYSCALL"
},
{
"a1": "eth0.dhclient",
"a0": "cat",
"argc": 2,
"epoch": 1399248110,
"type": "EXECVE"
},
{
"cwd": "/run/resolvconf/interface",
"epoch": 1399248110,
"type": "CWD"
},
{
"name": "/bin/cat",
"epoch": 1399248110,
"type": "PATH"
}
]
[
{
"res": "success",
"terminal": "ssh",
"addr": "192.168.56.1",
"hostname": "babby.local",
"exe": "/usr/sbin/sshd",
"acct": "mthomas",
"op": "PAM:session_open",
"ses": 24,
"auid": 1000,
"uid": 0,
"pid": 10469,
"epoch": 1393886985,
"serial": 3393,
"type": "USER_START"
}
]
[
{
"exe": "/usr/sbin/nginx",
"comm": "nginx",
"ses": 238,
"pid": 966,
"ppid": 965,
"items": 1,
"a3": "fffffffffffffffb",
"a2": 0,
"a1": "800",
"a0": "ee7c05",
"exit": 13,
"success": "yes",
"syscall": "open",
"epoch": 1392316421,
"serial": 301316,
"type": "SYSCALL"
},
{
"cwd": "/",
"type": "CWD"
},
{
"ogid": 0,
"name": "/www/index.html",
"type": "PATH"
}
]
[
{
"exe": "/usr/sbin/nginx",
"comm": "nginx",
"ses": 238,
"pid": 966,
"ppid": 965,
"items": 0,
"a3": "800",
"a2": "7fff8afba6cc",
"a1": "7fff8afba6d0",
"a0": 0,
"exit": 12,
"success": "yes",
"syscall": "accept4",
"epoch": 1392316421,
"serial": 301314,
"type": "SYSCALL"
},
{
"saddr": "192.168.56.1",
"port": 51997,
"prot": "ipv4",
"type": "SOCKADDR"
}
]
/var/resolvconf/interface$ cat eth0.dhclient nginx: int fd = open(“/www/index.html”); // fd == 13 fd = accept(“192.168.56.1:51997”); user “mthomas” started a pam session](https://image.slidesharecdn.com/audit-140509143909-phpapp01/85/Audit-27-320.jpg)



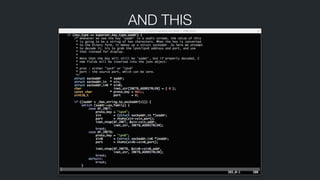

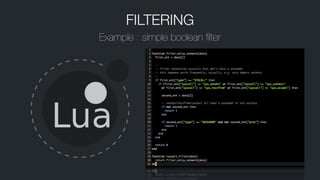
![FILTERING
Example : return a table which is converted to JSON on output
function find_set(k, set)
for _,v in pairs(set) do
if k == v then
return 1
end
end
return 0
end
!
!
function tsaudit_filter(data)
local ret = {}
local comms = { 'irqbalance', 'whoopsie', 'top', 'dhclient' }
!
for k,ent in pairs(data) do
if find_set(ent['comm'], comms) == 1 then
-- if any of the keys are found, return this table which will be
-- transformed into the JSON { "this" : "filtered", "dont" : "log" }
ret = {this="filtered", dont="log" }
end
!
if ent['success'] == 'no' then
-- if the syscall did not succeed, then return 1 which will not generate a
-- log.
ret = 1
end
end
!
return ret
end](https://image.slidesharecdn.com/audit-140509143909-phpapp01/85/Audit-37-320.jpg)