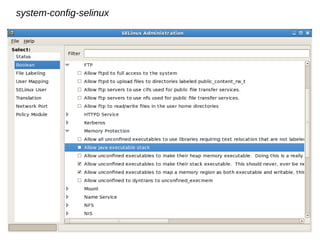
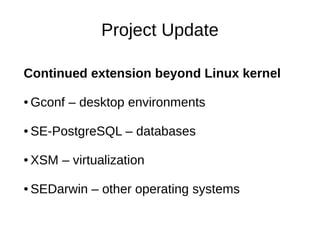
The document provides an overview and update on the State of Security Enhanced (SE) Linux project. It discusses that SE Linux is a security framework that uses type enforcement and mandatory access control to enforce confidentiality and integrity. It then summarizes that the project has expanded its policy tools, added dynamic policy loading, improved certification and protection, and continued extending its support beyond the Linux kernel. It closes by discussing ongoing work and how to get involved in helping the project.