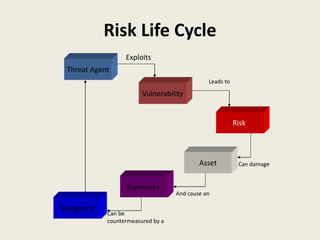
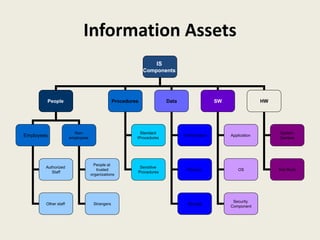
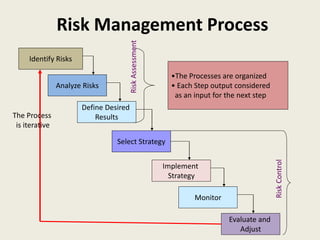
The document presents an overview of information risk management, defining key terms such as risk, threats, vulnerabilities, and assets. It details the risk management process, including risk assessment and risk control, emphasizing the importance of identifying risks for effective management. Strategies for treating risks, such as acceptance, avoidance, mitigation, and transfer, are also discussed, along with monitoring and reviewing risks to adapt to changing conditions.