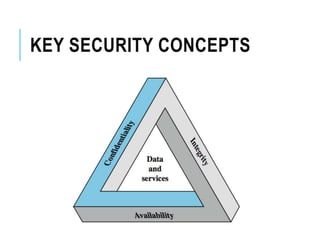
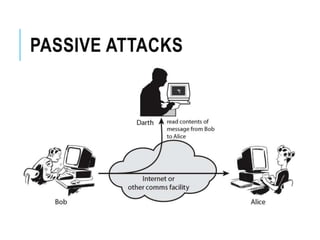
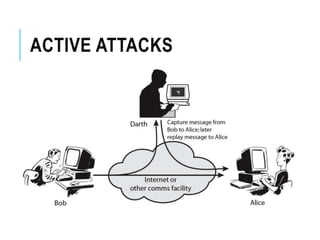
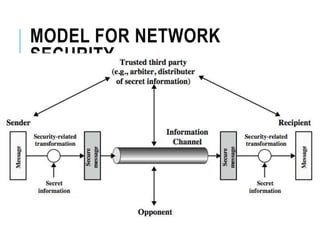
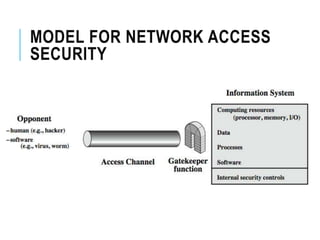
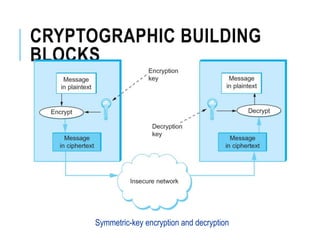
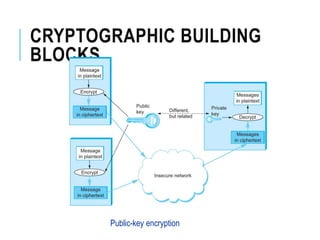
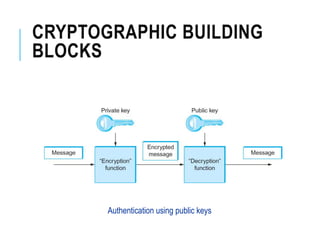
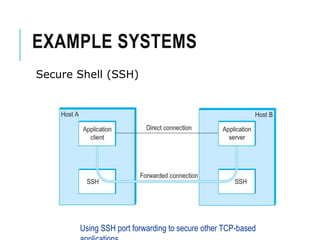
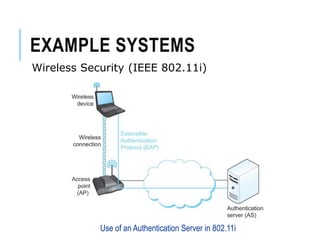
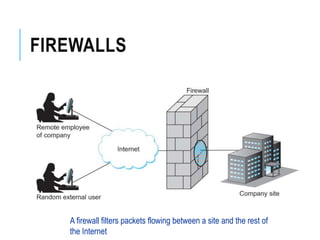
This document discusses network security standards organizations like NIST and ISO, as well as key security concepts like threats, attacks, security services, and security mechanisms. It provides examples of cryptographic techniques like symmetric and public key encryption. It also summarizes standards for wireless security under IEEE 802.11i and the use of firewalls to filter network traffic and protect sites.