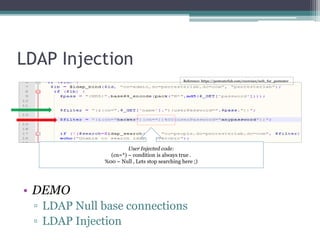
This document discusses LDAP injection and provides information about LDAP, its advantages and allowed operations. It describes LDAP search and retrieval using filters and nested expressions. The document demonstrates LDAP injection using a null base connection and injected code. It recommends preventing injection by validating input and using encoding methods like ESAPI.