This document provides an overview and summary of a dissertation submitted by Dashti Abdullah for the degree of Master of Science in Advanced Internetwork Engineering. The dissertation aims to test open source security solutions (mod_evasive, (D)DoS Deflate, and mod_security) against HTTP DoS/DDoS attacks and compare their effectiveness in mitigating these attacks. The dissertation includes chapters on backgrounds/literature review of the topics, methodology for testing the solutions, and analysis of the results.




















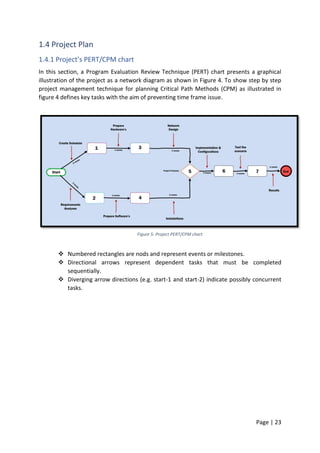




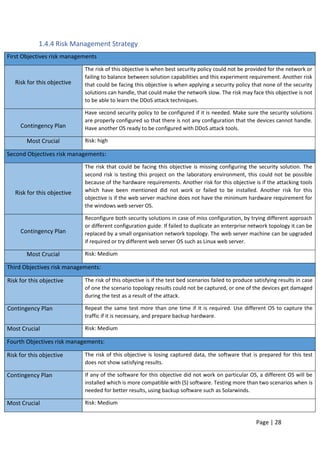





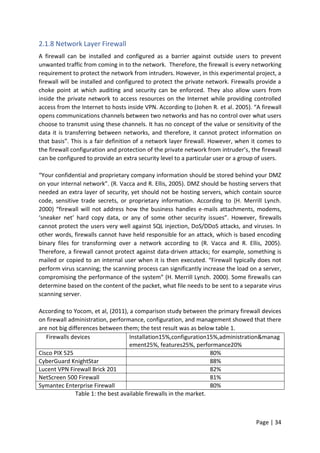







![Page | 42
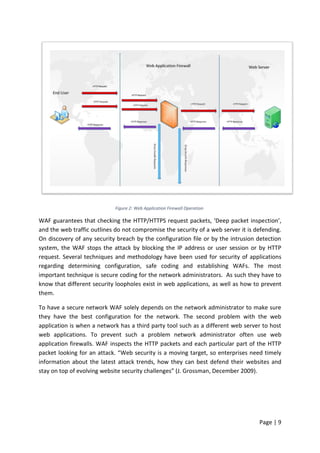
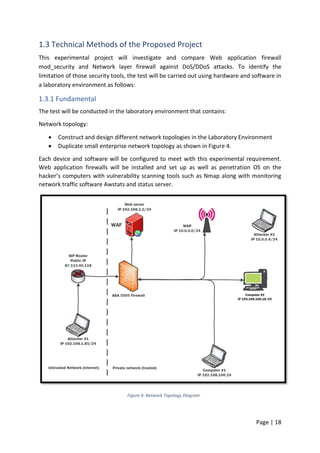
2.2.6 Critical Evaluation for Web Application Firewall Solutions
Eight web application firewall solutions have been selected for comparison: F5,
Mod_Security, WebDefend, Barracuda, Secure IIS, Server Defender VP, WebSniper, and
SecureSphere. The full comparison has been carried out by choosing the measures of attack
prevention, response filtering, blocking, monitoring, website cloaking, deep inspection,
session protection, time efficient, well organised, effective, and total security performance
in Table-2. Tick symbols () indicate that the selected feature is available in the firewall
solution and () indicates that selected feature is not available. A question mark (?) signs
indicate there is no information about that specified feature for the firewall, and also ‘HA’
indicate that the specified feature is only available in hardware machine.
Name of Tools F5 ModSecurity WebDefend Barracuda Secure IIS Server Defender VP WebSniper Secure Sphere
Attack prevention
Response filtering
Blocking HA HA
monitoring HA HA
Website cloaking ?
Deep inspection HA ?
Session protection ? ?
Time efficient
Well organised
Effective
Overall Security Performance ? ? ? ?
Table 2: Web Application Firewall solutions Defence Mechanism, [7]-(A, Razzaq. A, Hur 2013)](https://image.slidesharecdn.com/daec439d-c9bb-4436-a2c8-6a1c794bab98-160912153353/85/Comparative-Study-of-Mod-Security-Autosaved-43-320.jpg)




















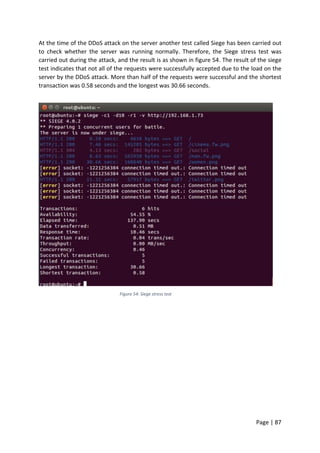
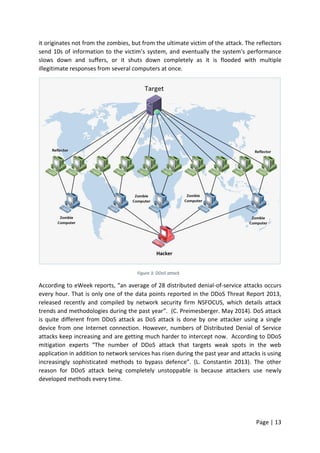
![Page | 88
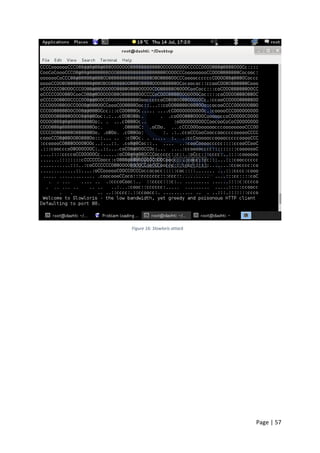
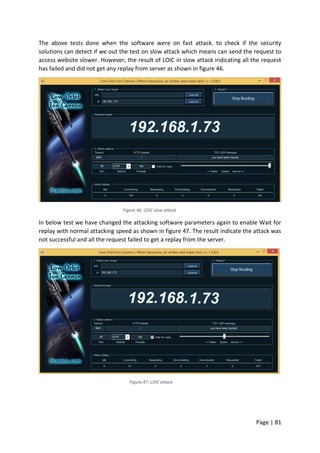
However, after three minutes the web server started to come back on slowly, and the
website was accessible again. As shown in Figure 55 the hping3 attack did not take down the
server completely. During the attack the website was still accessible but not as normal.
Figure 55: website accessibility from web browser during hping3 attack
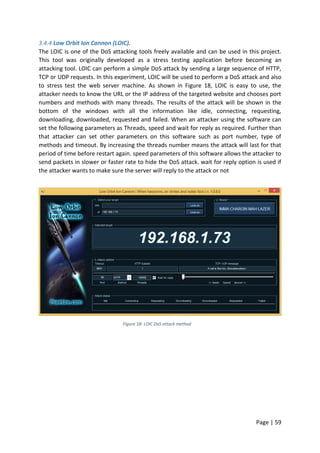
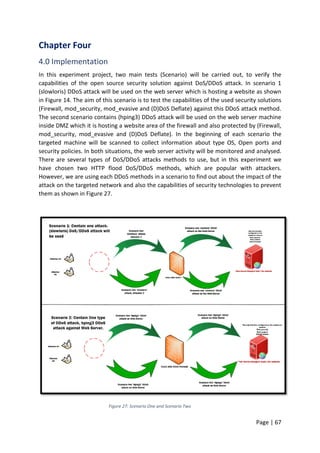
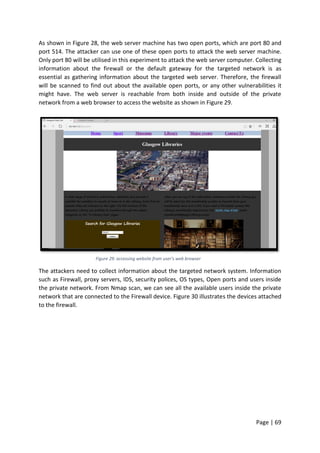
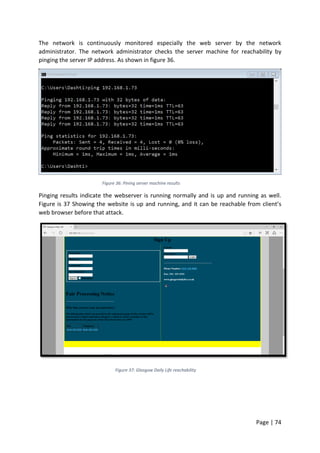
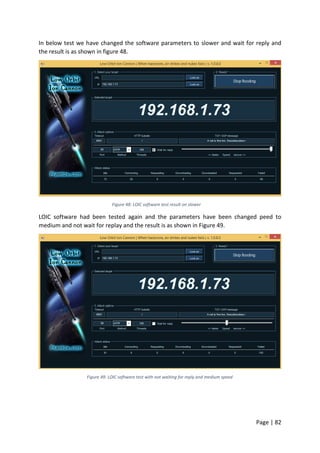
To make sure the server is reachable the network administrator tried to ping the server IP
address for reachability. Pinging the server was also successful from the administrator and
users machine as shown in Figure 56 and appendix [6]. Although all these tests have been
carried out when the web server was still under DDoS attack, but the server was up and
running but not as normal.
Figure 56: pinging webserver IP address](https://image.slidesharecdn.com/daec439d-c9bb-4436-a2c8-6a1c794bab98-160912153353/85/Comparative-Study-of-Mod-Security-Autosaved-89-320.jpg)








![Page | 97
Joseph Muniz, Aamir Lakhani, Web Penetration Testing with Kali Linux. Packt Publishing ©2013
ISBN:1782163166 9781782163169.
Johen R. Vacca & Scott R. Ellis Firewalls Jumpstart for Network and System Administrations.
Copyright © 2005, Elsevier Inc. All rights reserved.
J, Frahim & O, Santos, 2010, "Cisco ASA: All-in-one Firewall, IPS, Anti-X, AND VPN Adaptive
security appliance, 2nd edition*
J. Wack, K. Cutler, and J. Pole, “Guidelines on Firewalls and Firewall Policy”. National Institute of
Standards and Technology, Jan. 2002.
Jim Beechey, “Web Application Firewalls: Defence in Depth for Your Web Infrastructure” March
2009
Kenneth Ingham and STEPHANIE FORRESTA History and Survey of Network Firewalls University of
New Mexico 2002.
Ken Hess, BackTrack Linux: The Ultimate Hacker's Arsenal. Admin Network & Security
Magazine,2013. http://www.admin-magazine.com/Articles/BackTrack-Linux-The-Ultimate-Hacker-
s-Arsenal
Lee Allen, Tedi Heriyanto, Shakeel Ali. Kali Linux – Assuring Security by penetration testing
Publisher, Packt Publishing Ltd, 2014. ISBN: 1849519498, 9781849519496
M.G. Gouda and A.X. Liu, “A Model of Stateful Firewalls and Its Properties,” Proc. IEEE Int’l Conf.
Dependable Systems and Networks (DSN), June 2005.
M. Gouda and A. Liu, “A model of stateful firewalls and its properties,” Proceedings of International
Conference on Dependable Systems and Networks, 2005 (DSN), pp. 128–137, 28 June-1 July
2005.
M. Sharma NETWORK SECURITY USING FIREWALLS, September 2009
http://ggnindia.dronacharya.info/Downloads/Seminars/Proceedings_ETCT.pdf#page=64
Mick Bauer. Getting started with mod_security, Journal Linux Journal Archive Volume 2006 Issue
143, March 2006.
Mohd Faris Mohd Fuzi, Ros Syamsul Hamid, Muhammad Akram Ahmad, Virtual Desktop
Environment on Cloud Computing Platform. 2014 IEEE 5th Control and System Graduate Research
Colloquium, Aug. 11 - 12, UiTM, Shah Alam, Malaysia.
Nilesh Khochare, Satish Chalurkar, B.B.Meshram. Web Application Vulnerabilities Detection
Techniques Survey. IJCSNS International Journal of Computer Science and Network Security,
VOL.13 No.6, June 2013.
Namit Gupta and Abakash Saikia. Web Application Firewall. 30/04/2007.
PR Newswire [New York] 09 May 2001: 1. eEye(TM) Digital Security Releases SecureIIS(TM), the
Application Firewall For Microsoft IIS Web Server. New York.
http://search.proquest.com/docview/444009692/9859B42E7C374BEDPQ/1?accountid=15977
PCI-DSS -Information Supplement: Application Reviews and Web Application Firewalls Clarified.
Saikat Guha, Paul Francis. Characterization and Measurement of TCP Traversal through NATs and
Firewalls 2008. http://nutss.gforge.cis.cornell.edu/pub/imc05-tcpnat/#note2
Sandeep PK, August 2009. Mod Security Intro.
http://www.supportpro.com/blog/2009/08/mod_security-intro/](https://image.slidesharecdn.com/daec439d-c9bb-4436-a2c8-6a1c794bab98-160912153353/85/Comparative-Study-of-Mod-Security-Autosaved-98-320.jpg)

![Page | 99
Chapter Nine
9.0 Appendices
[1]- firewall ‘show running configuration’
Firewall# show running-config
: Saved
:
ASA Version 8.3(2)
!
hostname Firewall
enable password 4uQtljz7JQzBIRhg encrypted
passwd 2KFQnbNIdI.2KYOU encrypted
names
!
interface Vlan1
nameif inside
security-level 100
ip address 192.168.106.1 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
ip address dhcp setroute
!
interface Vlan3
no forward interface Vlan1
nameif dmz
security-level 50
ip address 192.168.1.1 255.255.255.128
!](https://image.slidesharecdn.com/daec439d-c9bb-4436-a2c8-6a1c794bab98-160912153353/85/Comparative-Study-of-Mod-Security-Autosaved-100-320.jpg)




![Page | 104
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
inspect icmp
!
service-policy global_policy global
prompt hostname context
Cryptochecksum:d41d8cd98f00b204e9800998ecf8427e
: end
Firewall#
[2]- Firewall ‘show interface vlan 1’
Firewall# show interface vlan 1
Interface Vlan1 "inside", is up, line protocol is up
Hardware is EtherSVI, BW 100 Mbps, DLY 100 usec
MAC address 68ef.bd02.1a02, MTU 1500
IP address 192.168.106.1, subnet mask 255.255.255.0
Traffic Statistics for "inside":
13657691 packets input, 2544313124 bytes
22454716 packets output, 27376492803 bytes
32699 packets dropped
1 minute input rate 3 pkts/sec, 975 bytes/sec
1 minute output rate 3 pkts/sec, 1642 bytes/sec
1 minute drop rate, 0 pkts/sec
5 minute input rate 3 pkts/sec, 935 bytes/sec
5 minute output rate 3 pkts/sec, 1394 bytes/sec](https://image.slidesharecdn.com/daec439d-c9bb-4436-a2c8-6a1c794bab98-160912153353/85/Comparative-Study-of-Mod-Security-Autosaved-105-320.jpg)
![Page | 105
5 minute drop rate, 0 pkts/sec
[3]- Firewall ‘show interface vlan 2’
Firewall# show interface vlan 2
Interface Vlan2 "outside", is up, line protocol is up
Hardware is EtherSVI, BW 100 Mbps, DLY 100 usec
MAC address 68ef.bd02.1a02, MTU 1500
IP address 192.168.1.82, subnet mask 255.255.255.0
Traffic Statistics for "outside":
22607873 packets input, 27402744781 bytes
13628975 packets output, 2542441578 bytes
50276 packets dropped
1 minute input rate 3 pkts/sec, 1922 bytes/sec
1 minute output rate 3 pkts/sec, 777 bytes/sec
1 minute drop rate, 0 pkts/sec
5 minute input rate 3 pkts/sec, 1213 bytes/sec
5 minute output rate 2 pkts/sec, 785 bytes/sec
5 minute drop rate, 0 pkts/sec
[4]- Firewall ‘show interface vlan 3’
Firewall# show interface vlan 3
Interface Vlan3 "dmz", is up, line protocol is up
Hardware is EtherSVI, BW 100 Mbps, DLY 100 usec
MAC address 68ef.bd02.1a02, MTU 1500
IP address 192.168.2.1, subnet mask 255.255.255.0
Traffic Statistics for "dmz":
3595 packets input, 530035 bytes
4166 packets output, 3097897 bytes
46 packets dropped
1 minute input rate 0 pkts/sec, 0 bytes/sec
1 minute output rate 0 pkts/sec, 0 bytes/sec](https://image.slidesharecdn.com/daec439d-c9bb-4436-a2c8-6a1c794bab98-160912153353/85/Comparative-Study-of-Mod-Security-Autosaved-106-320.jpg)
![Page | 106
1 minute drop rate, 0 pkts/sec
5 minute input rate 0 pkts/sec, 6 bytes/sec
5 minute output rate 0 pkts/sec, 17 bytes/sec
5 minute drop rate, 0 pkts/sec
[5]- ciscoasa(config)# show traffic
outside:
received (in 339033.460 secs):
206 packets 22456 bytes
0 pkts/sec 0 bytes/sec
transmitted (in 339033.460 secs):
3 packets 1180 bytes
0 pkts/sec 0 bytes/sec
1 minute input rate 0 pkts/sec, 0 bytes/sec
1 minute output rate 0 pkts/sec, 0 bytes/sec
1 minute drop rate, 0 pkts/sec
5 minute input rate 0 pkts/sec, 0 bytes/sec
5 minute output rate 0 pkts/sec, 0 bytes/sec
5 minute drop rate, 0 pkts/sec
inside:
received (in 339033.560 secs):
67543 packets 4126581 bytes
0 pkts/sec 12 bytes/sec
transmitted (in 339033.560 secs):
2 packets 56 bytes
0 pkts/sec 0 bytes/sec
1 minute input rate 0 pkts/sec, 28 bytes/sec
1 minute output rate 0 pkts/sec, 0 bytes/sec
1 minute drop rate, 0 pkts/sec
5 minute input rate 0 pkts/sec, 19 bytes/sec](https://image.slidesharecdn.com/daec439d-c9bb-4436-a2c8-6a1c794bab98-160912153353/85/Comparative-Study-of-Mod-Security-Autosaved-107-320.jpg)





![Page | 112
1 minute drop rate, 0 pkts/sec
5 minute input rate 0 pkts/sec, 28 bytes/sec
5 minute output rate 0 pkts/sec, 0 bytes/sec
5 minute drop rate, 0 pkts/sec
Internal-Data0/1:
received (in 2548113.460 secs):
74107583 packets 61521631699 bytes
0 pkts/sec 24000 bytes/sec
transmitted (in 2548113.460 secs):
74544939 packets 61629734776 bytes
0 pkts/sec 24001 bytes/sec
1 minute input rate 0 pkts/sec, 0 bytes/sec
1 minute output rate 0 pkts/sec, 101 bytes/sec
1 minute drop rate, 0 pkts/sec
5 minute input rate 0 pkts/sec, 0 bytes/sec
5 minute output rate 0 pkts/sec, 28 bytes/sec
5 minute drop rate, 0 pkts/sec
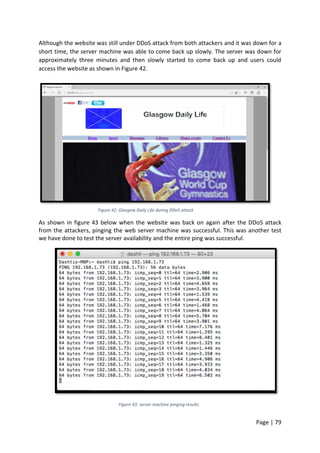
[6]- Pinging the webserver results](https://image.slidesharecdn.com/daec439d-c9bb-4436-a2c8-6a1c794bab98-160912153353/85/Comparative-Study-of-Mod-Security-Autosaved-113-320.jpg)
![Page | 113
[7]- Glasgow Daily Life Website pages
Home page:](https://image.slidesharecdn.com/daec439d-c9bb-4436-a2c8-6a1c794bab98-160912153353/85/Comparative-Study-of-Mod-Security-Autosaved-114-320.jpg)