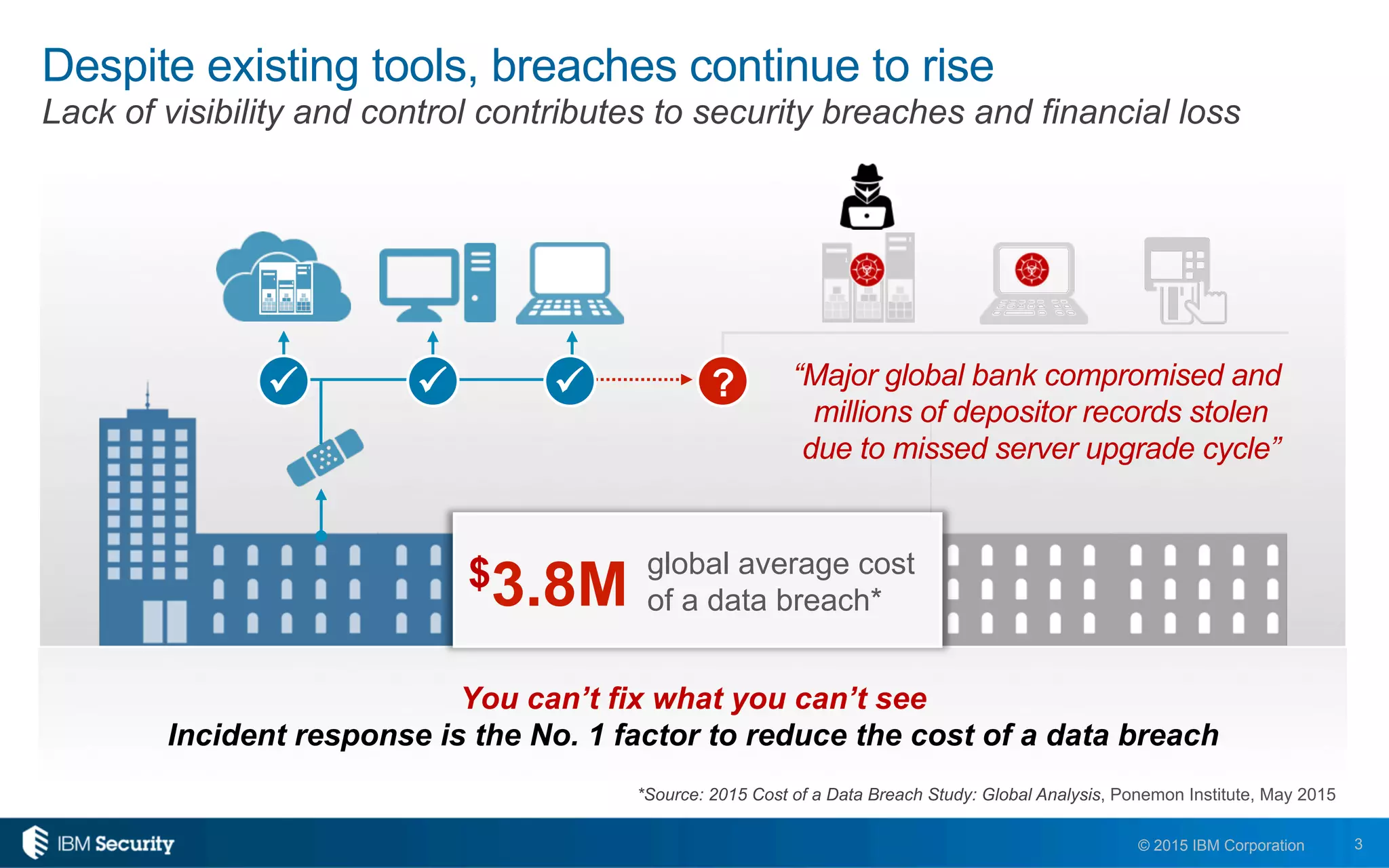
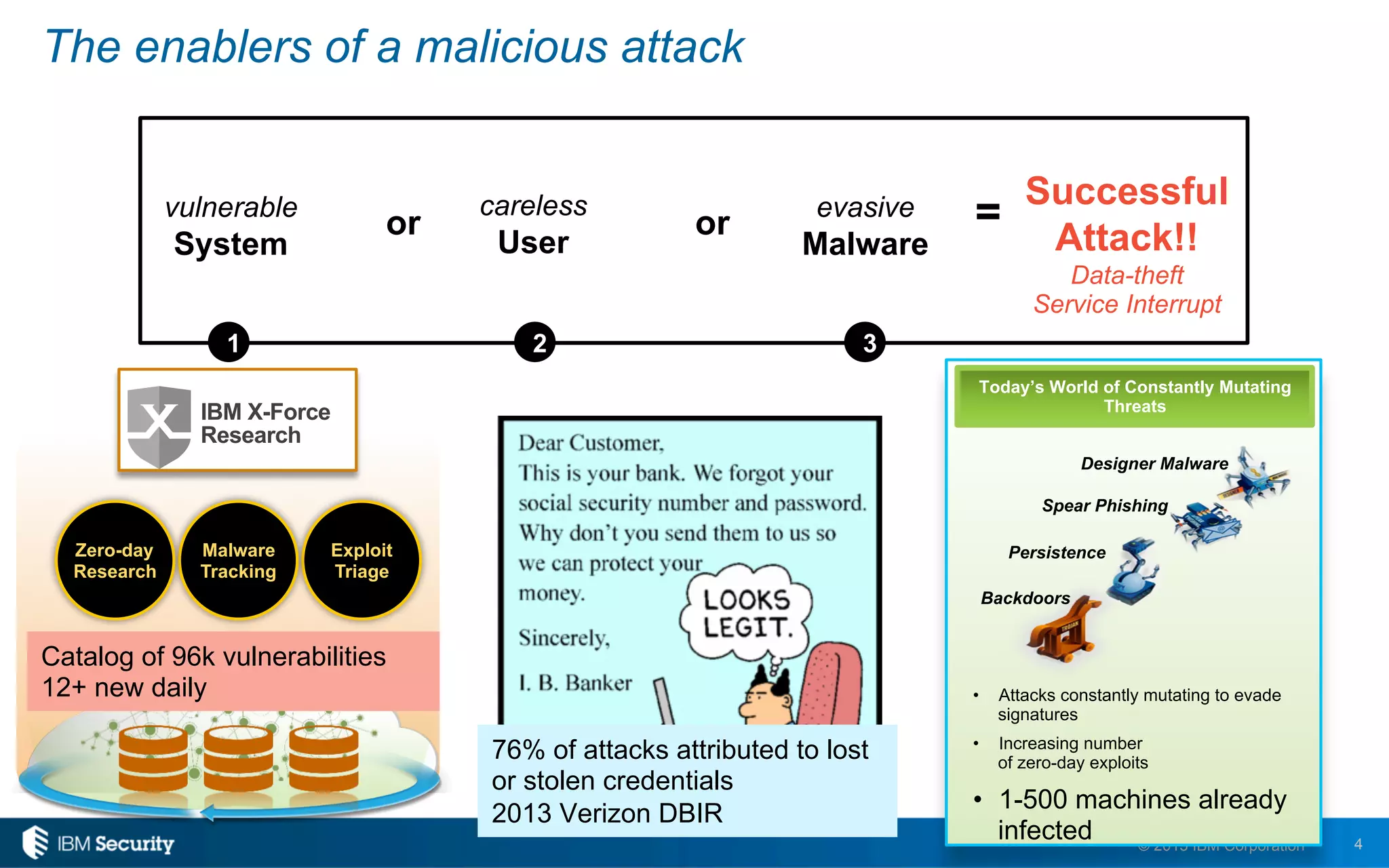
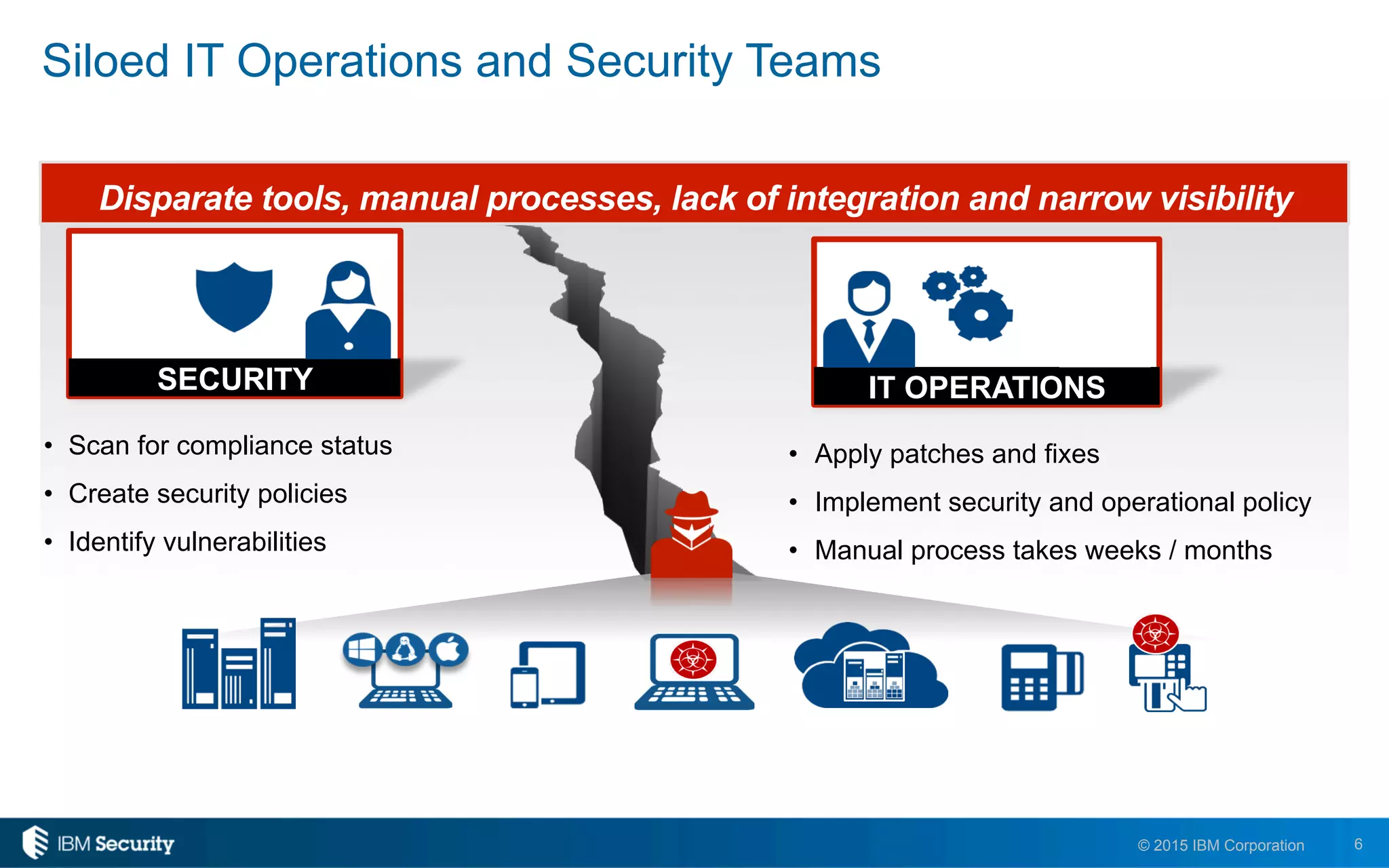
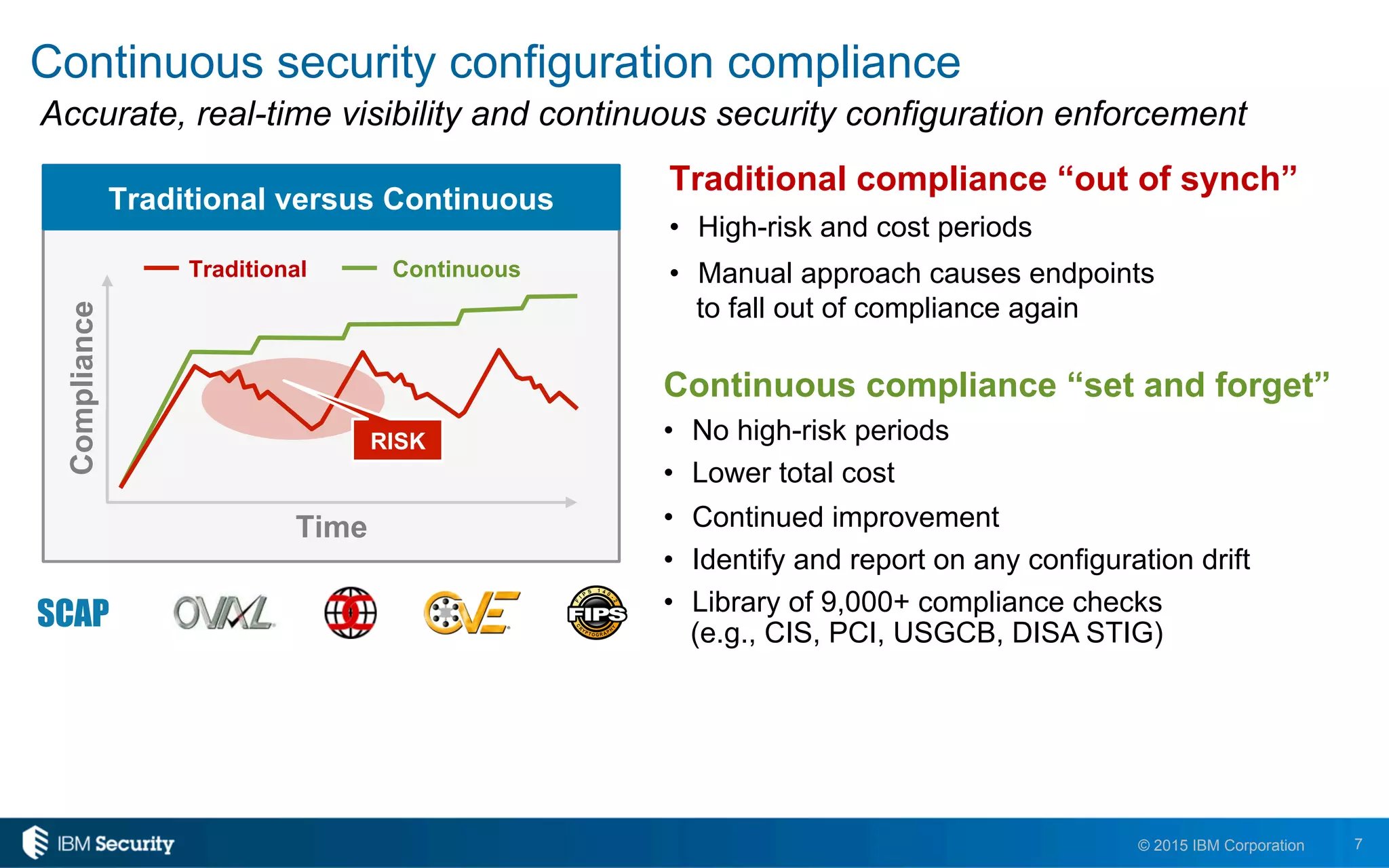
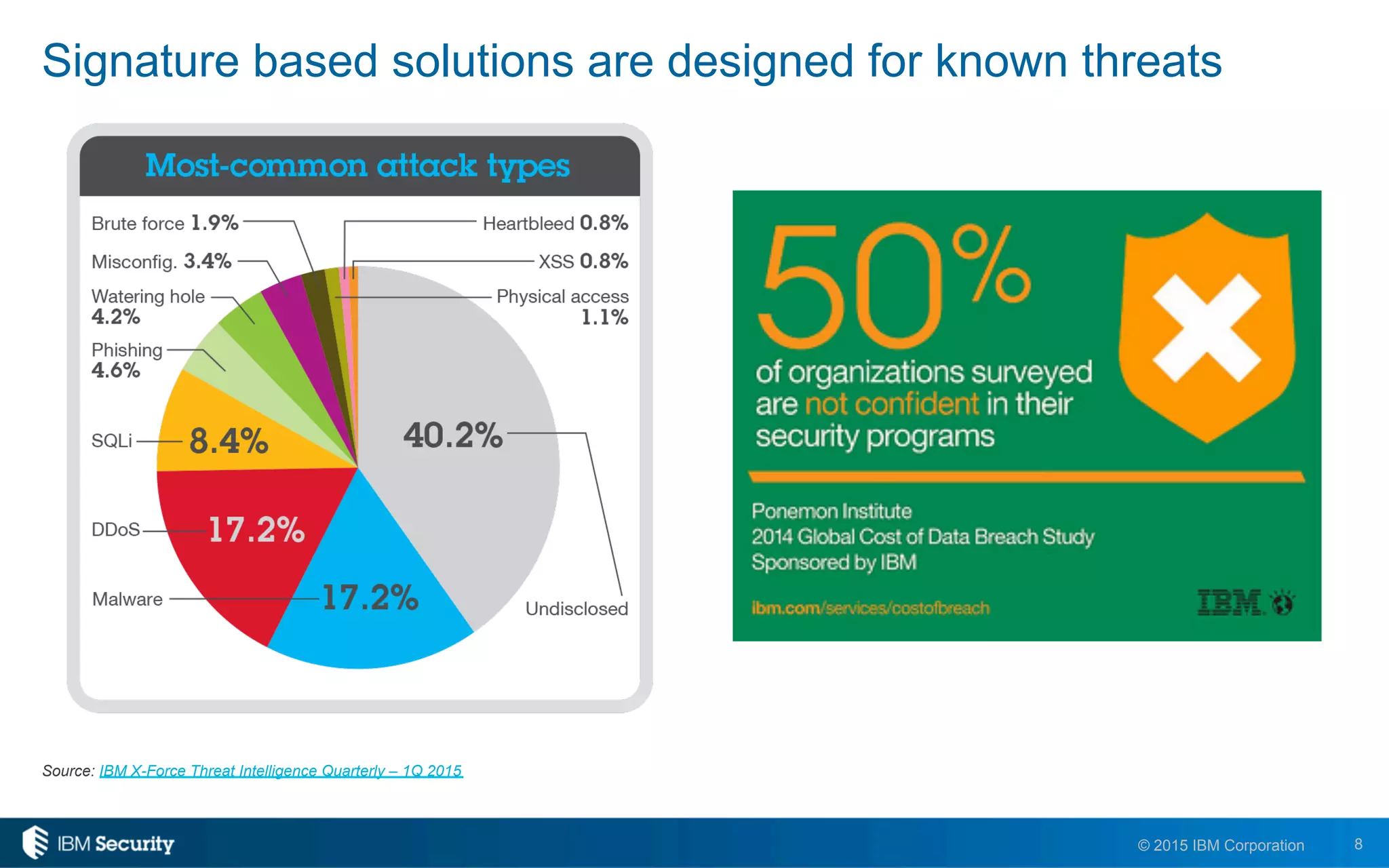
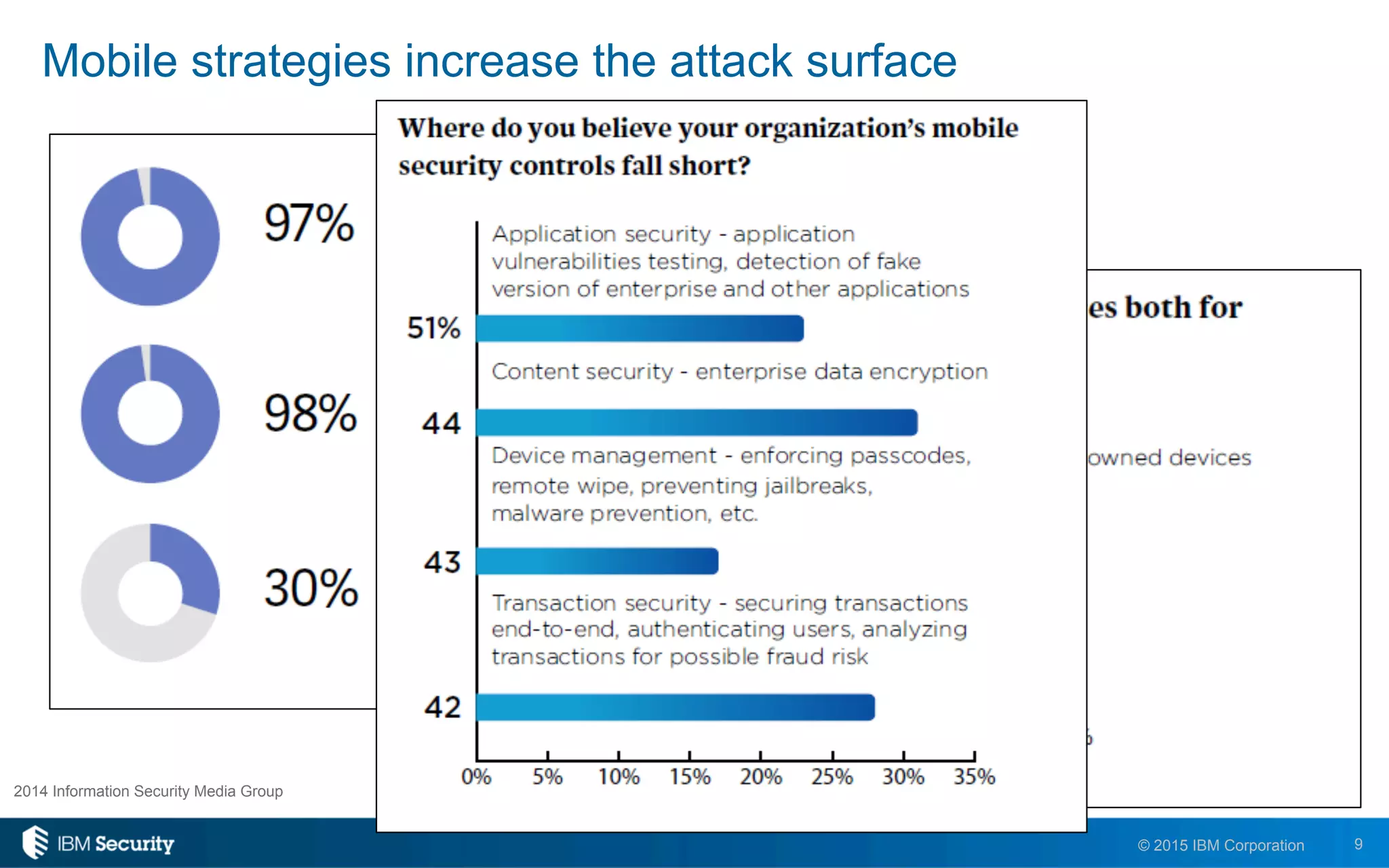
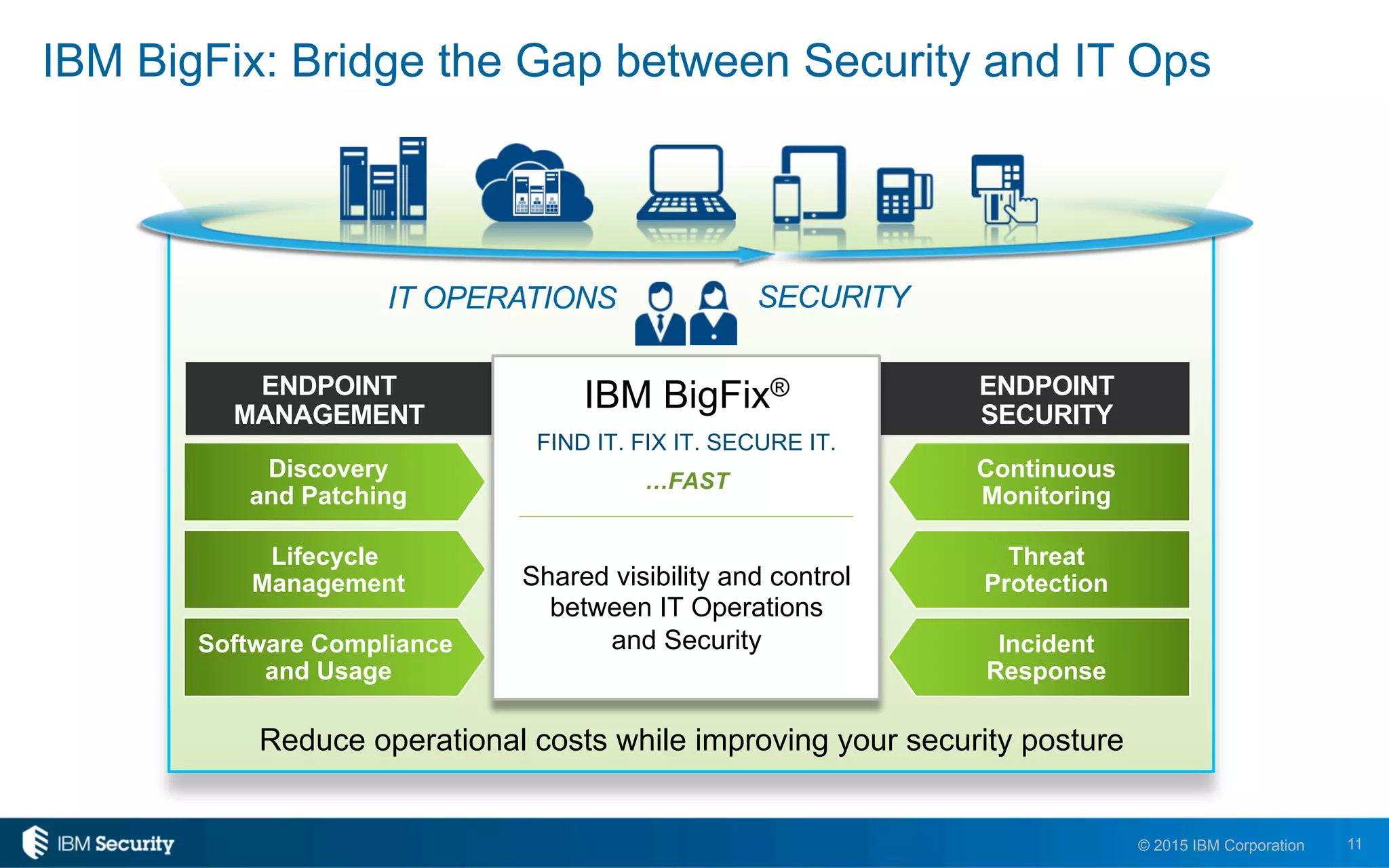
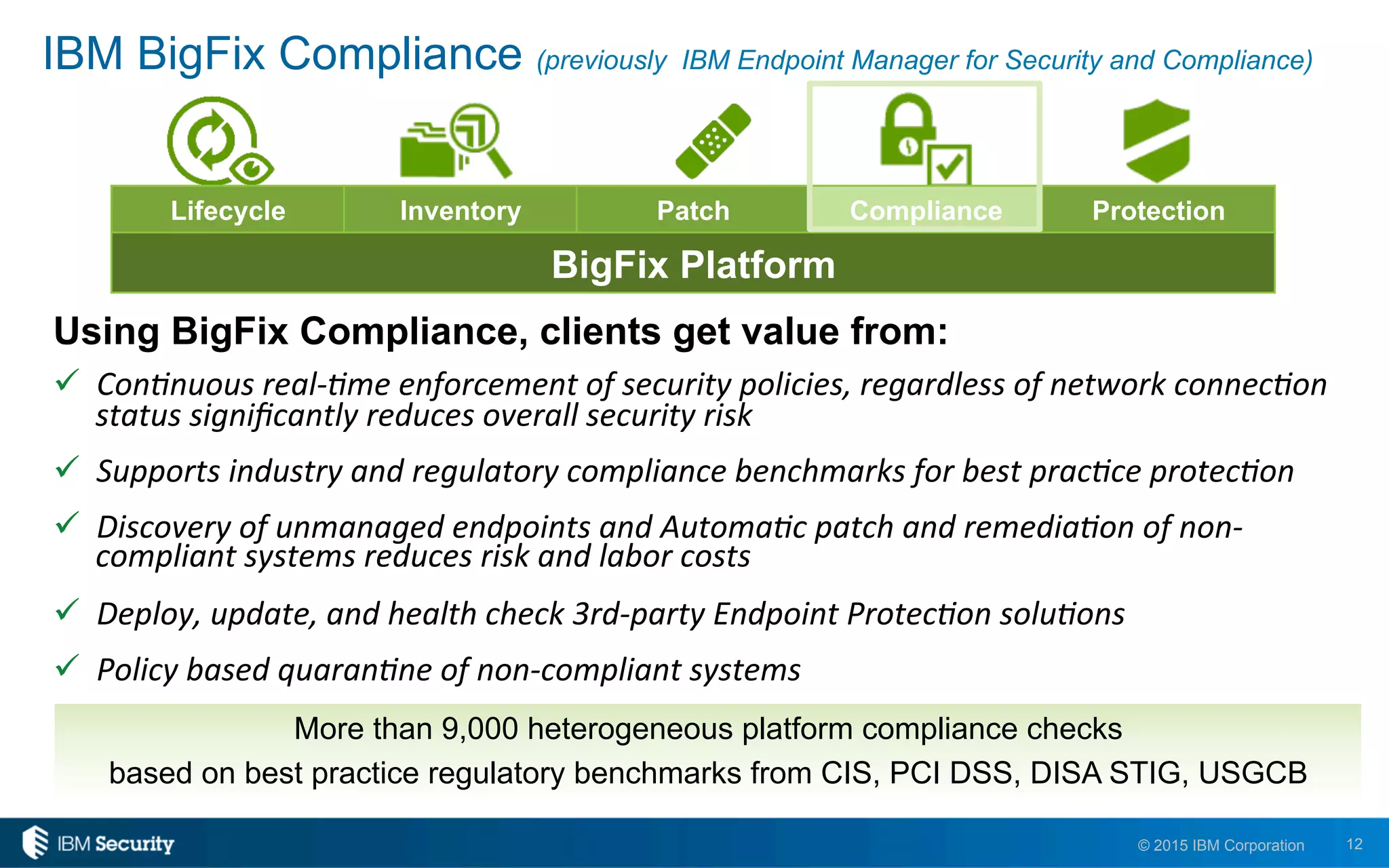
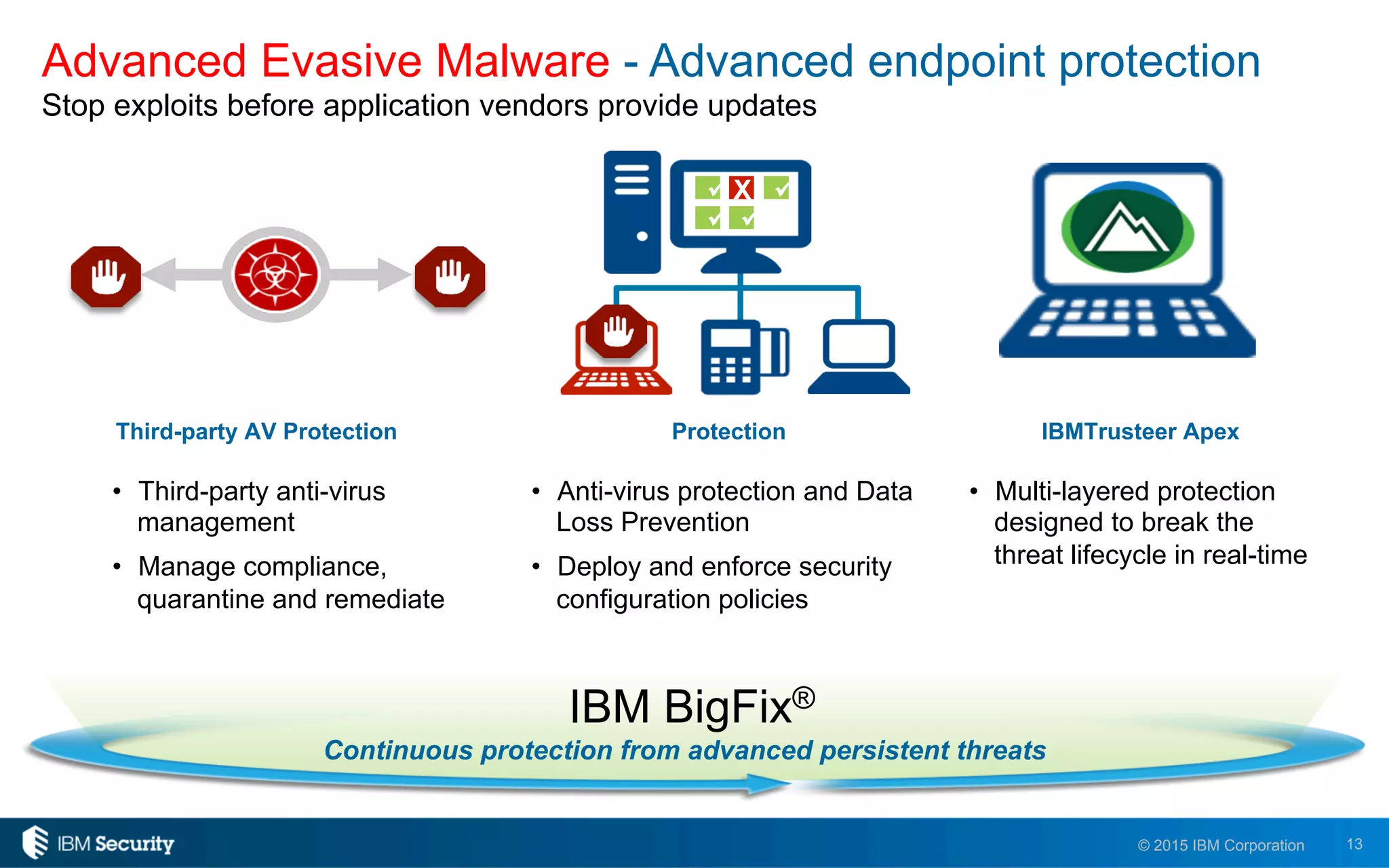
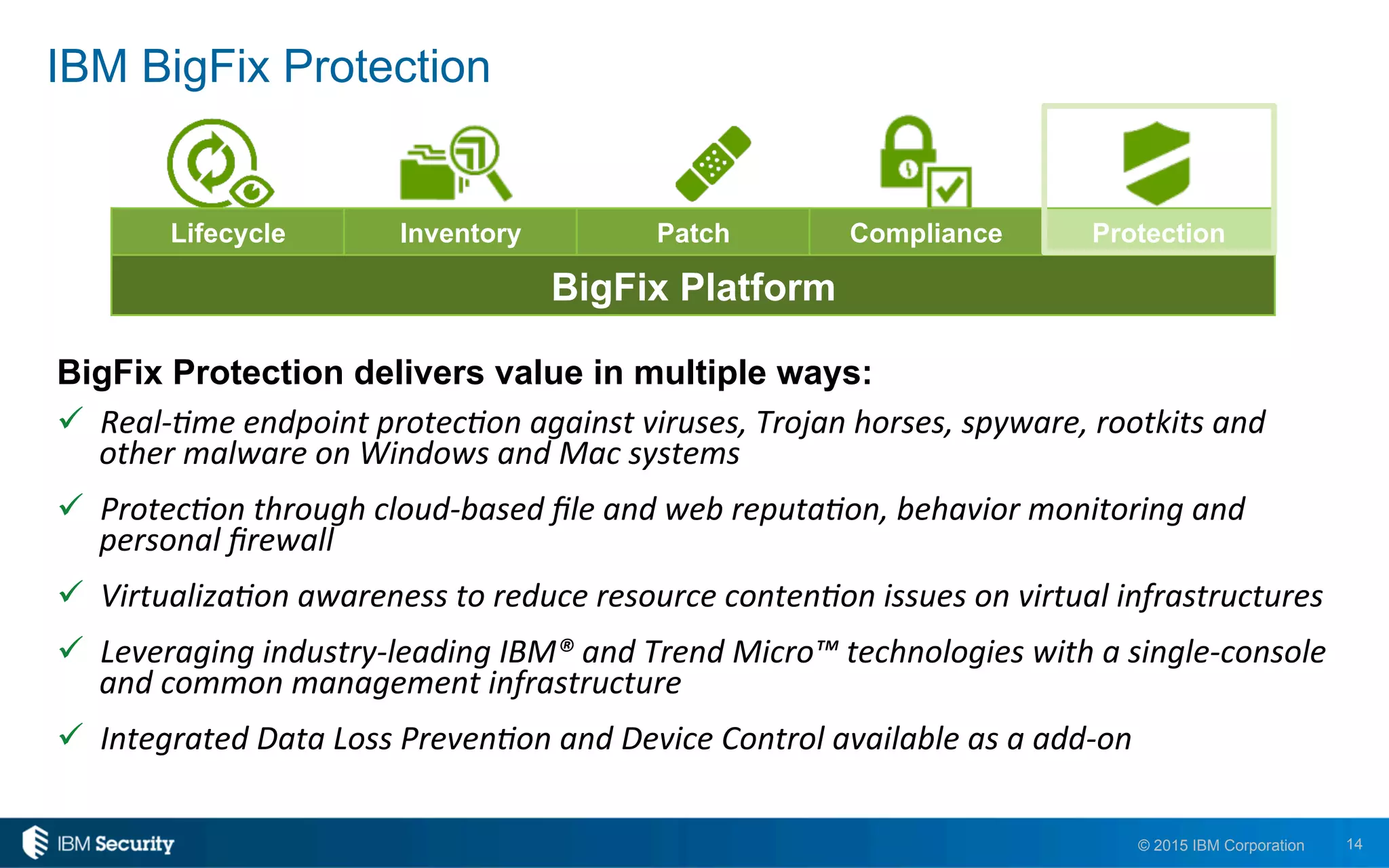
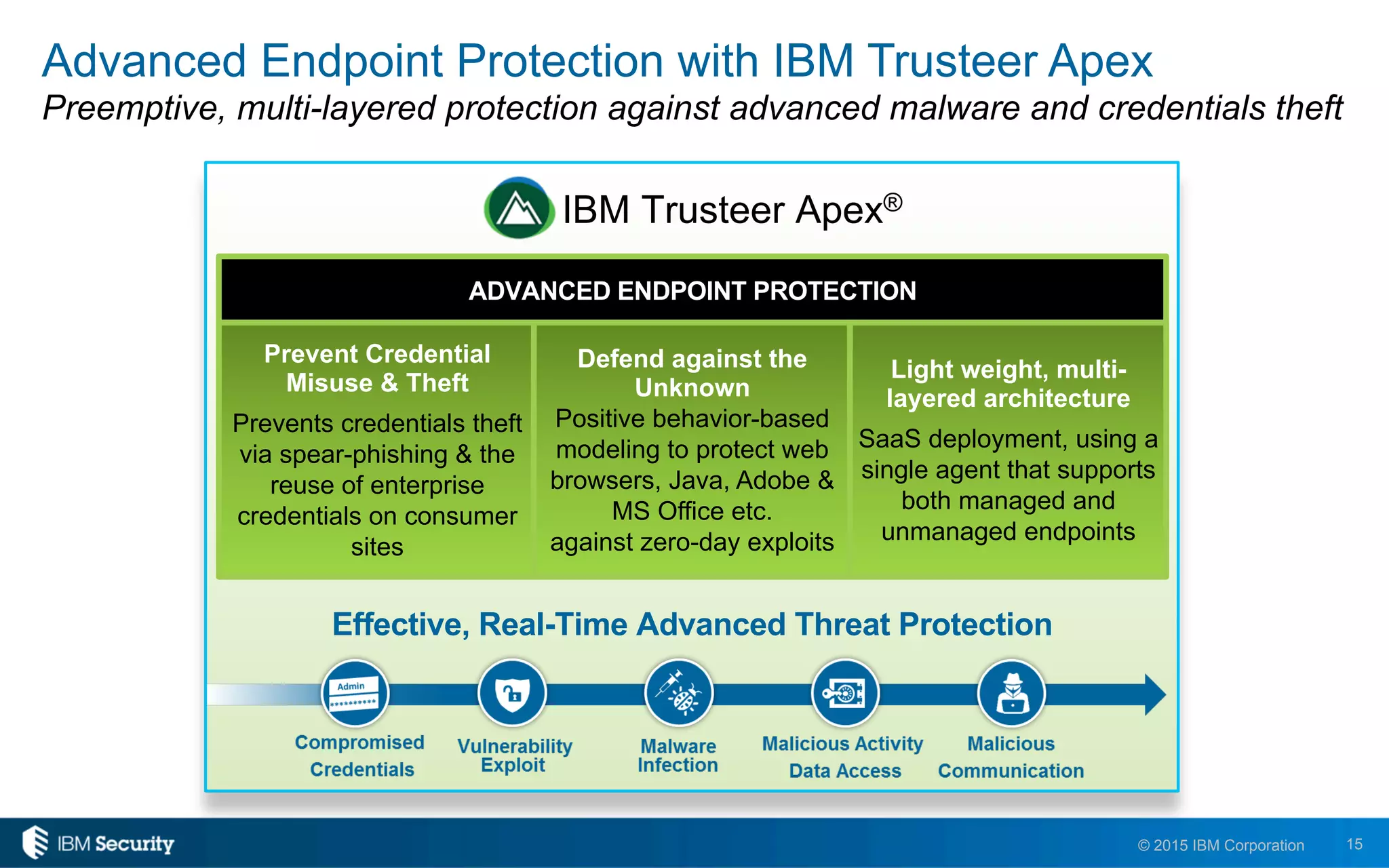
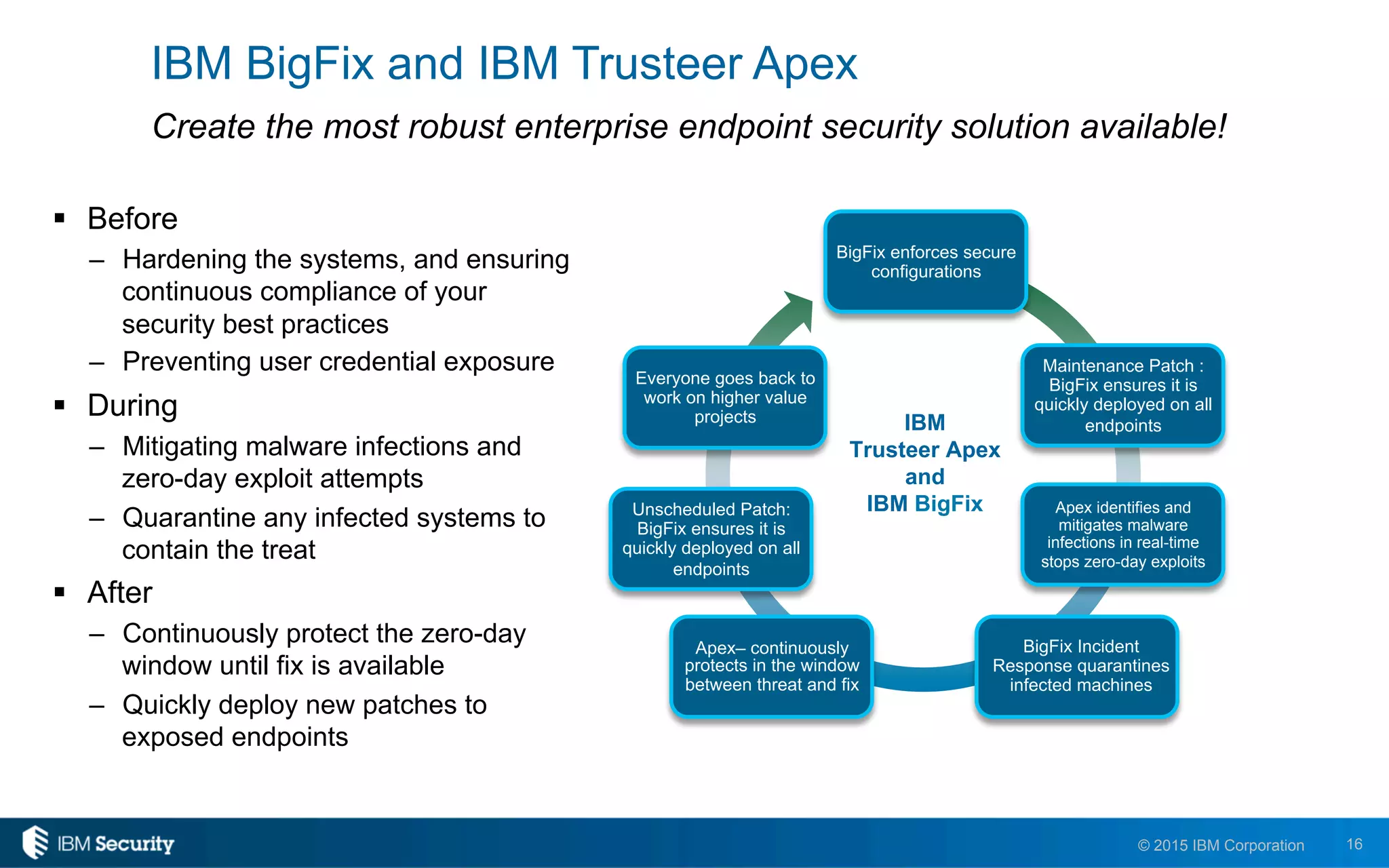
The document discusses enablers of successful cyber attacks, highlighting that existing security approaches often fall short due to siloed processes and lack of visibility. It emphasizes the importance of a unified ecosystem for security intelligence and continuous compliance in mitigating risks. The solution proposed includes IBM BigFix for endpoint protection and incident response to bolster security posture against evolving threats.