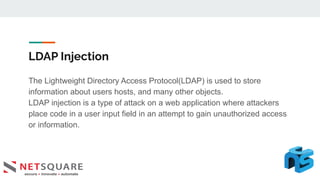
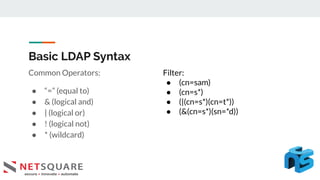
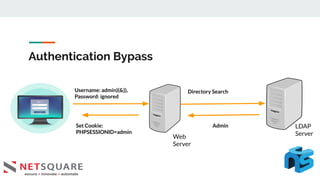
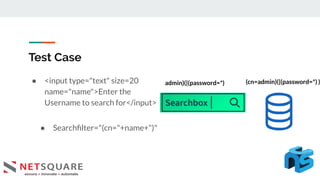
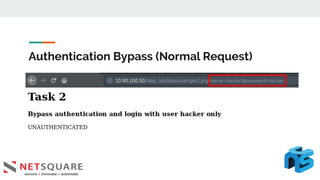
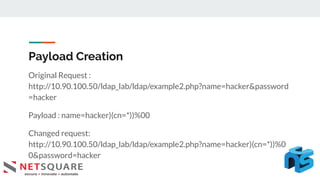
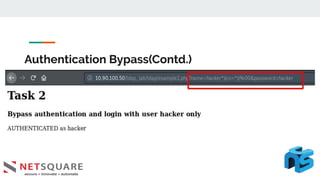
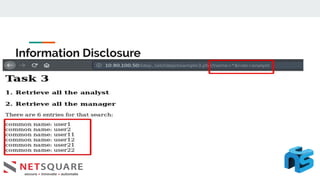
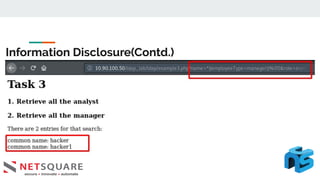
This document discusses LDAP injection, an attack where malicious code is inserted into a user input field to gain unauthorized access. It provides an overview of LDAP syntax and injection, demonstrating how an attacker can bypass authentication by closing parentheses in the username field. The document also notes LDAP injection can lead to privilege escalation and information disclosure. It recommends escaping special characters, using frameworks that encode LDAP queries, and applying least privilege to secure applications from LDAP injection.