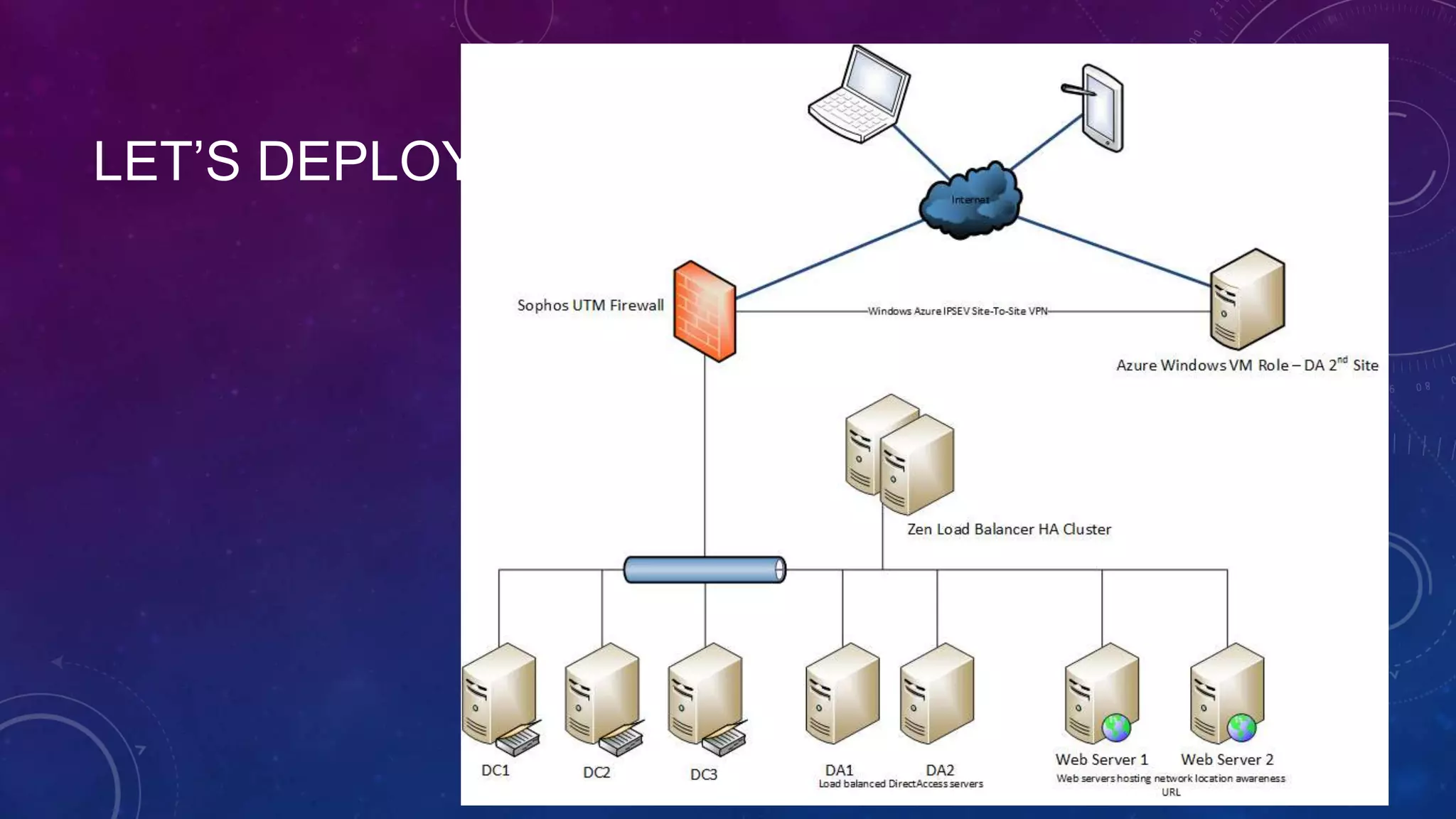
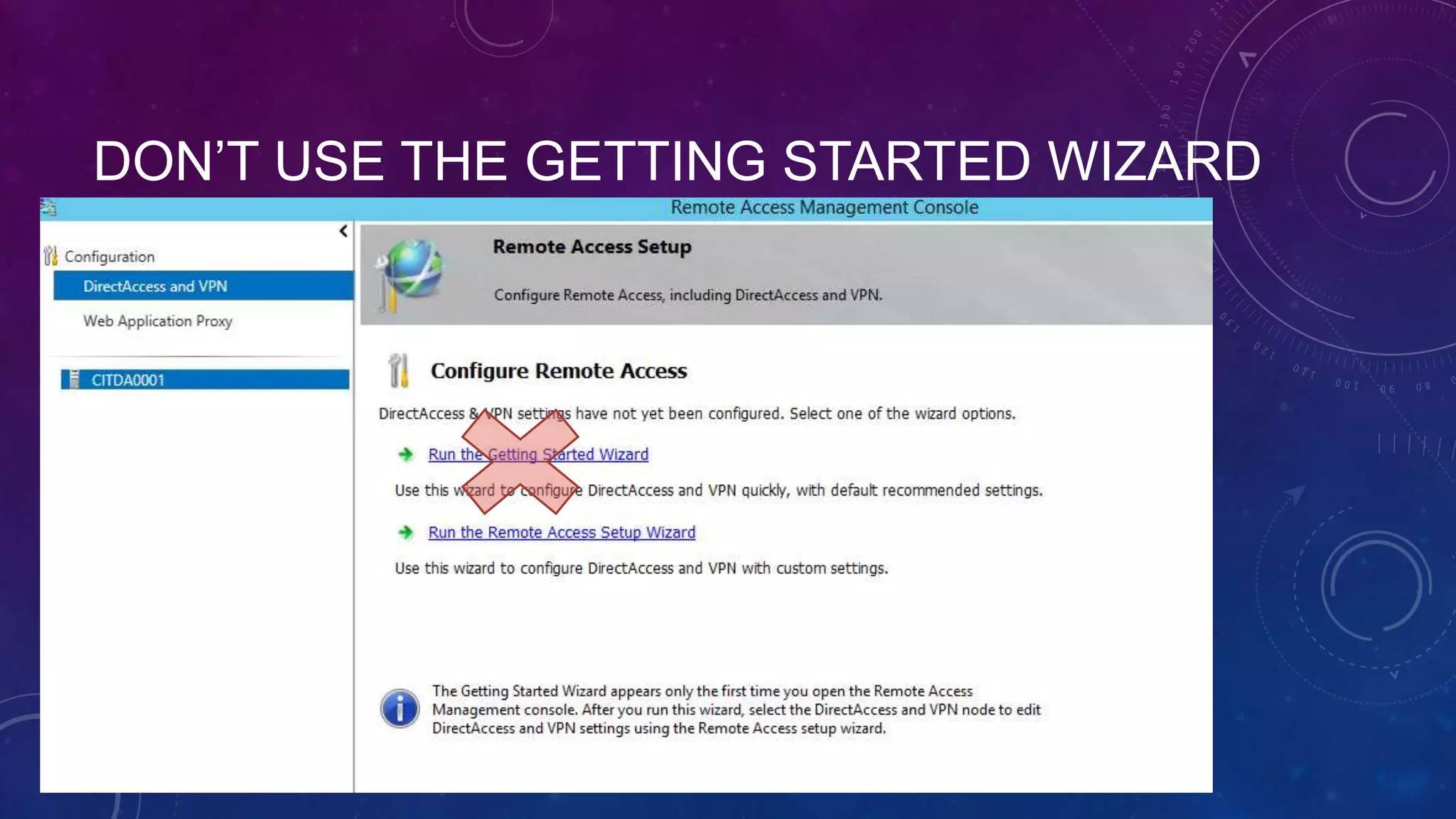
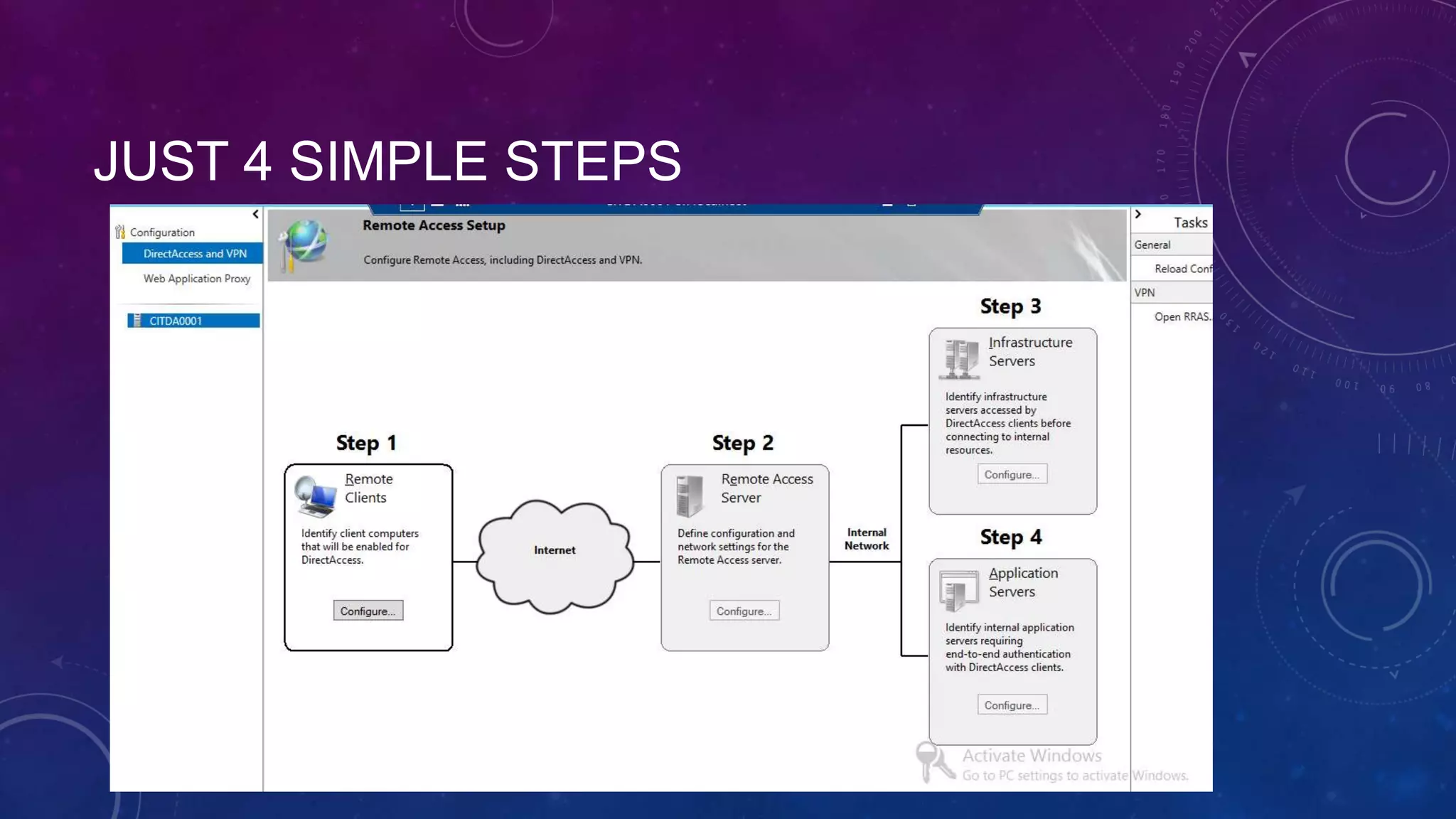
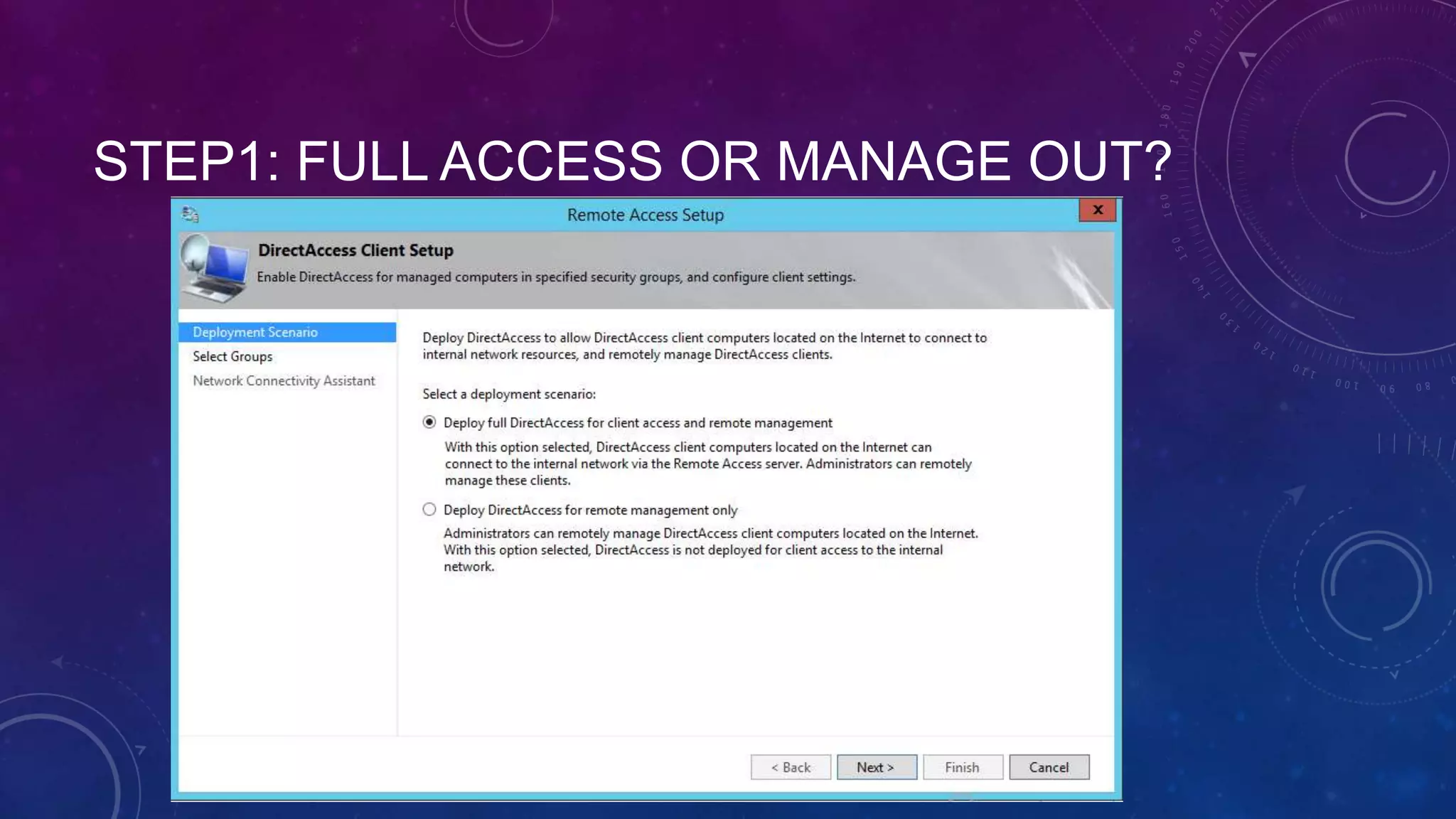
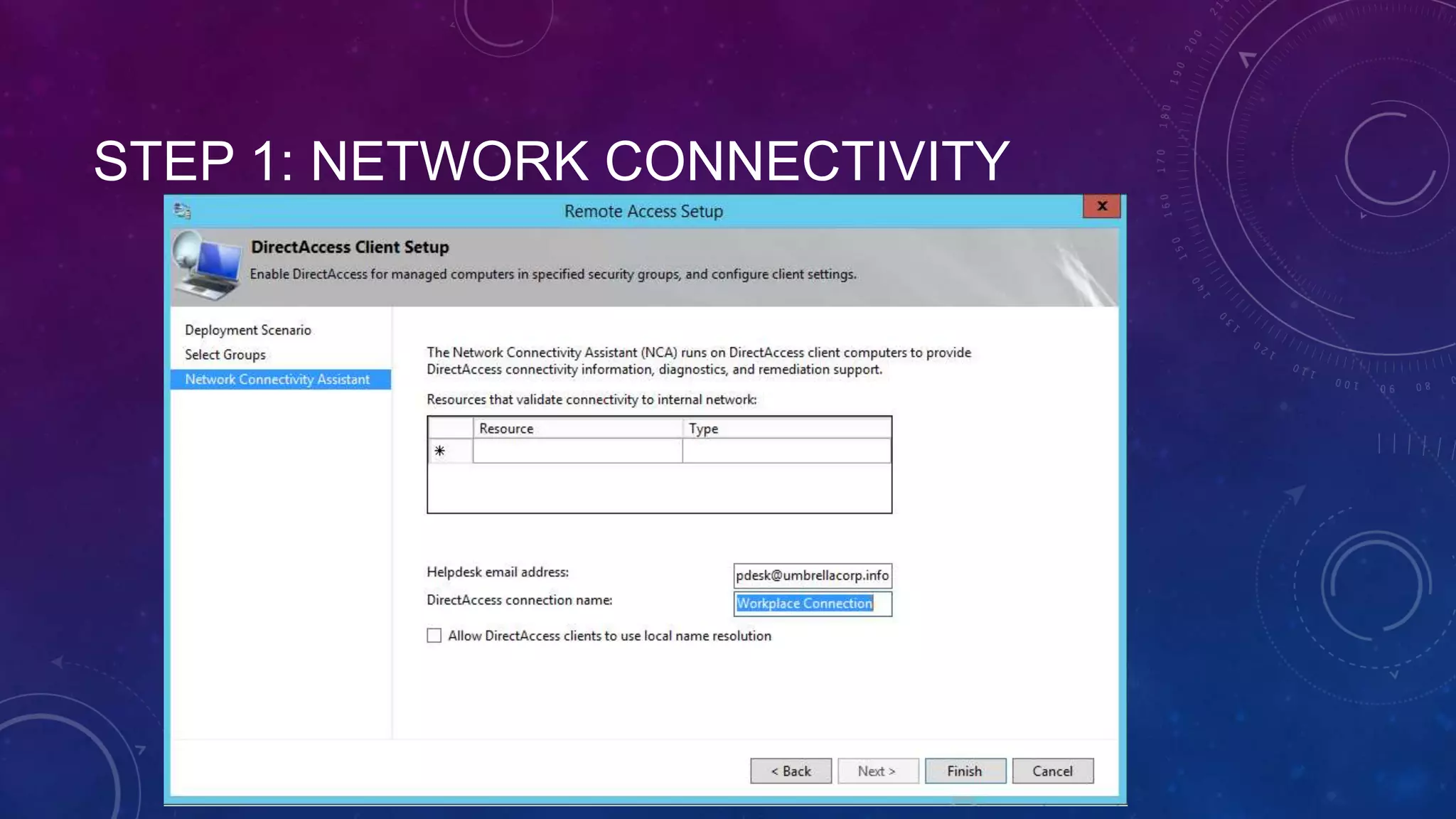
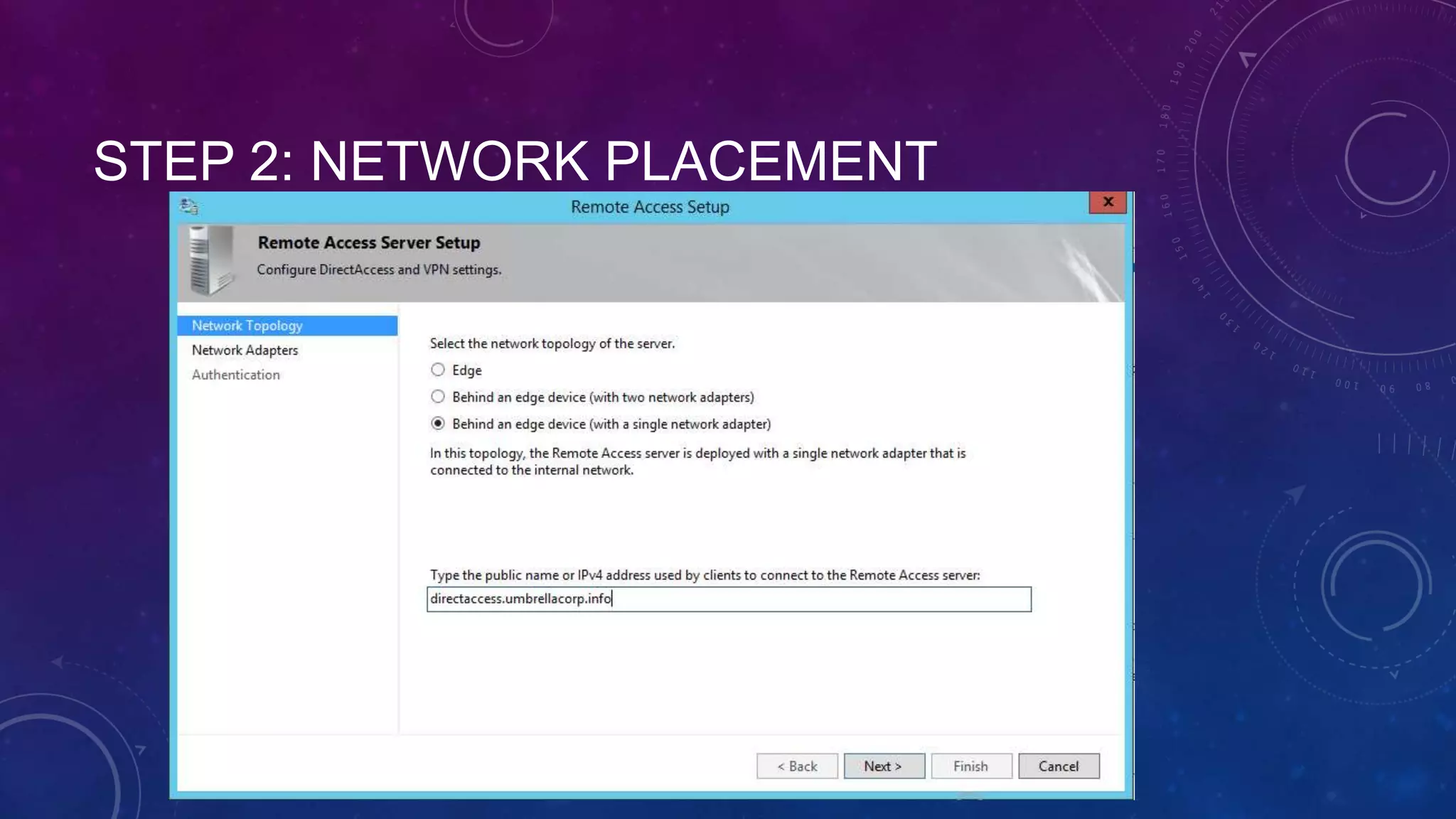
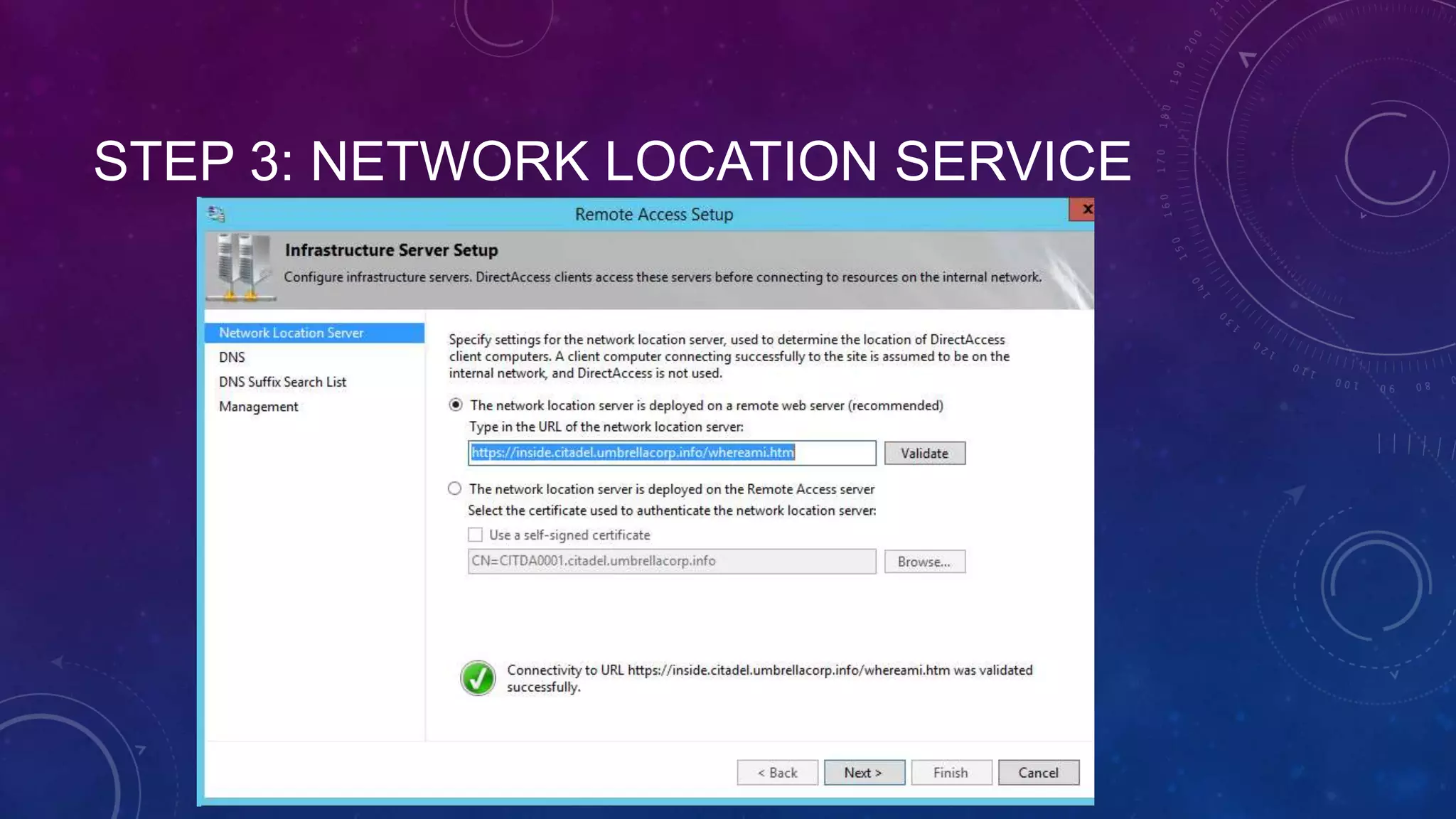
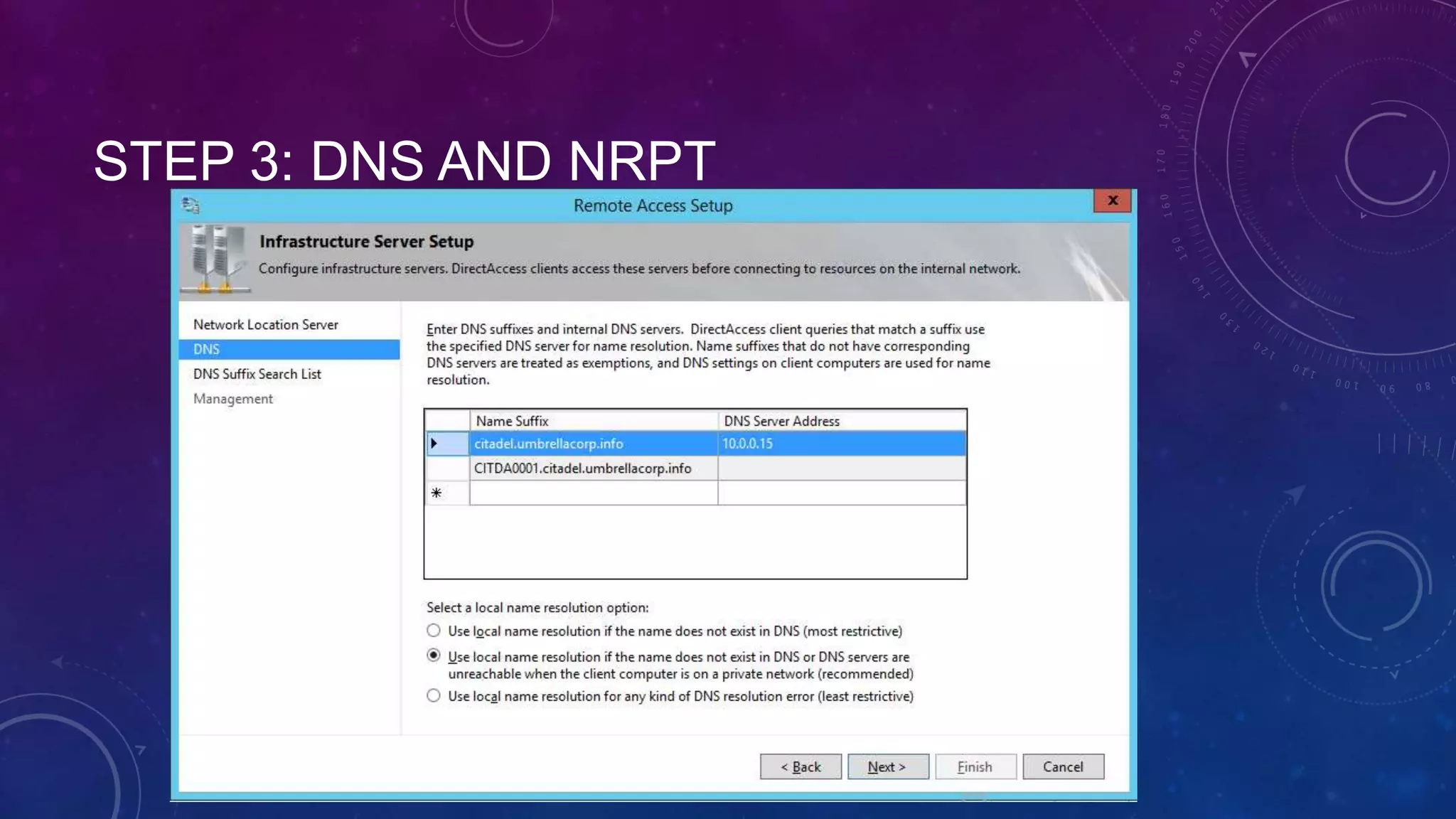
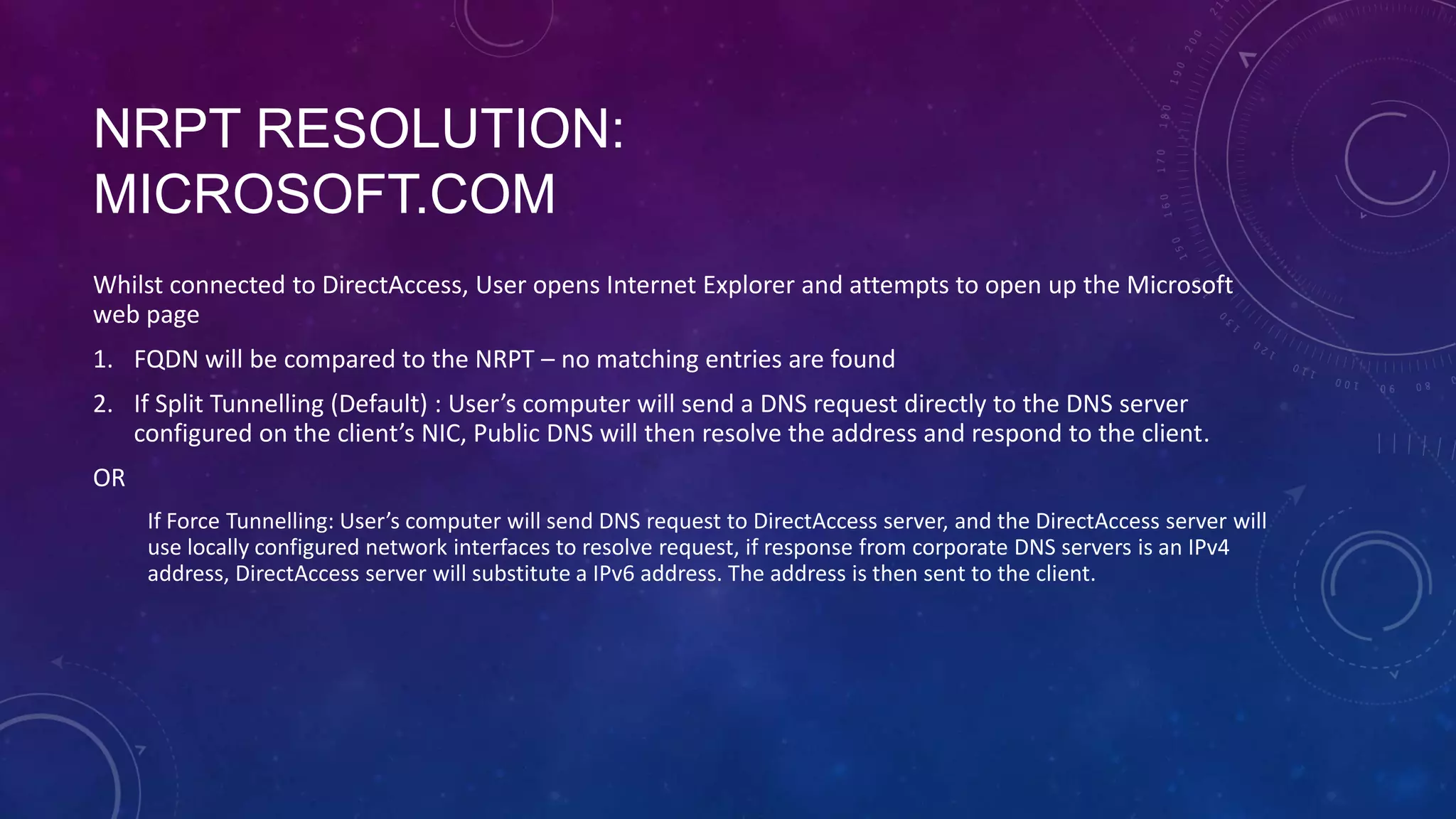
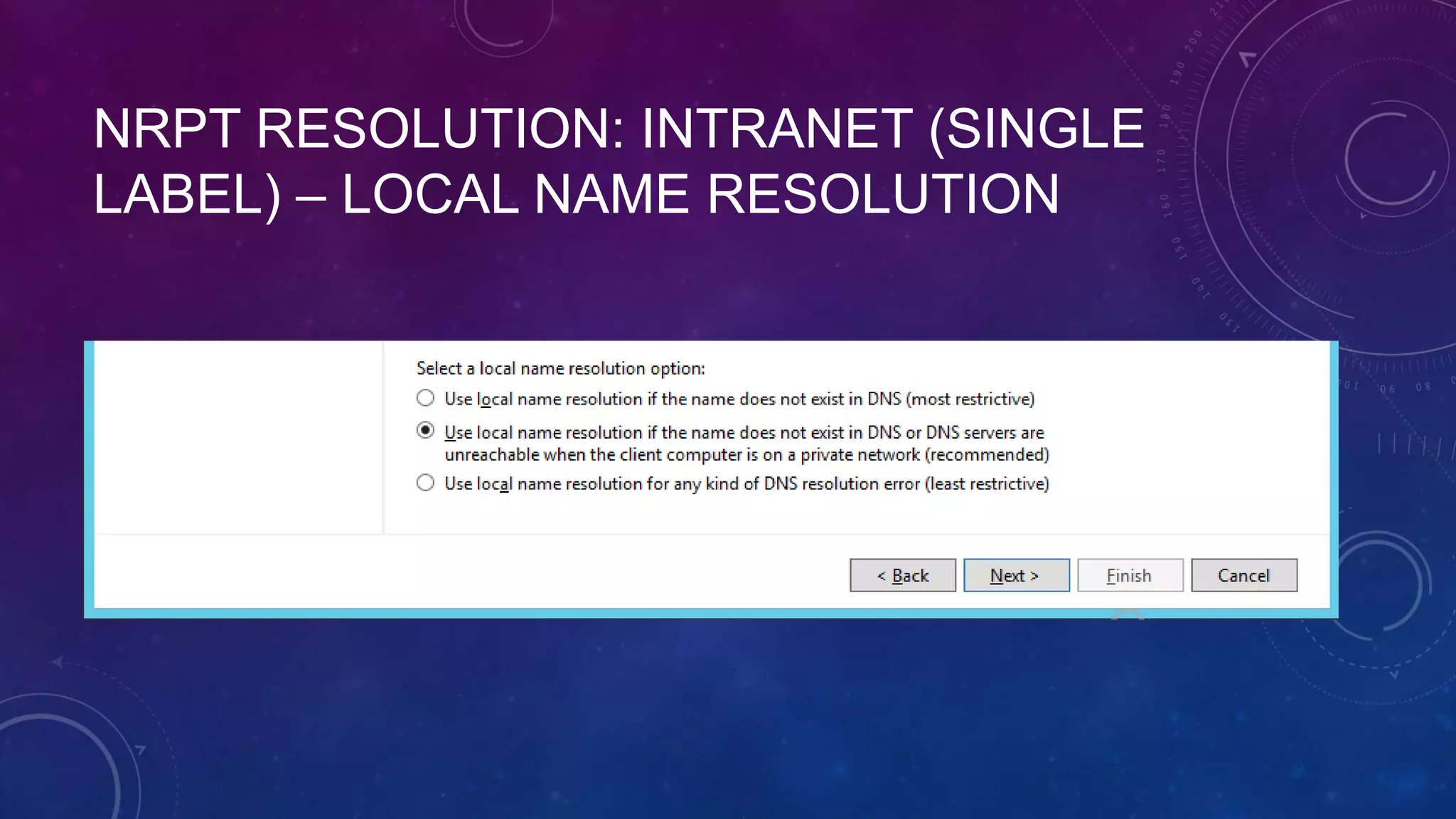
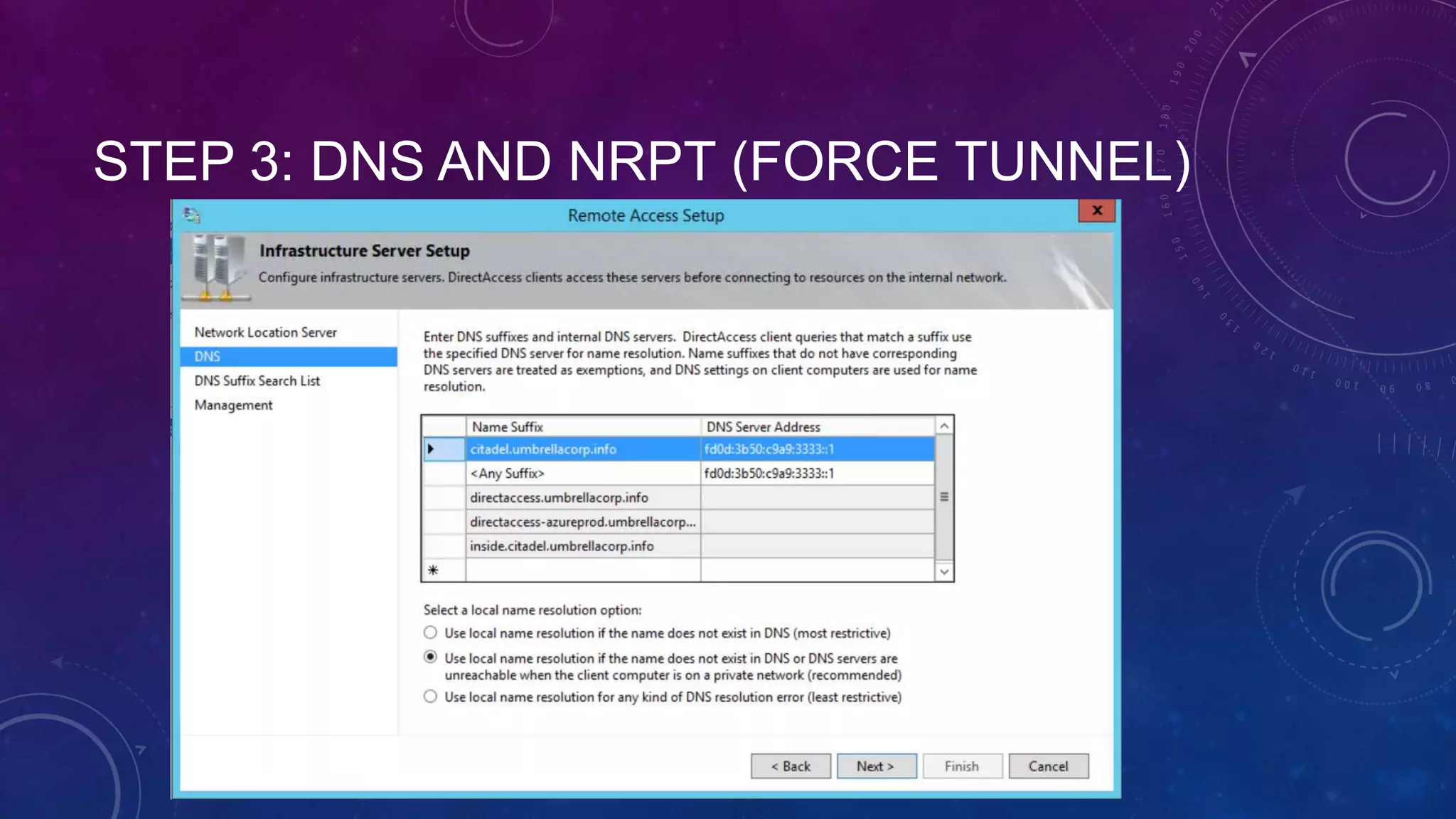
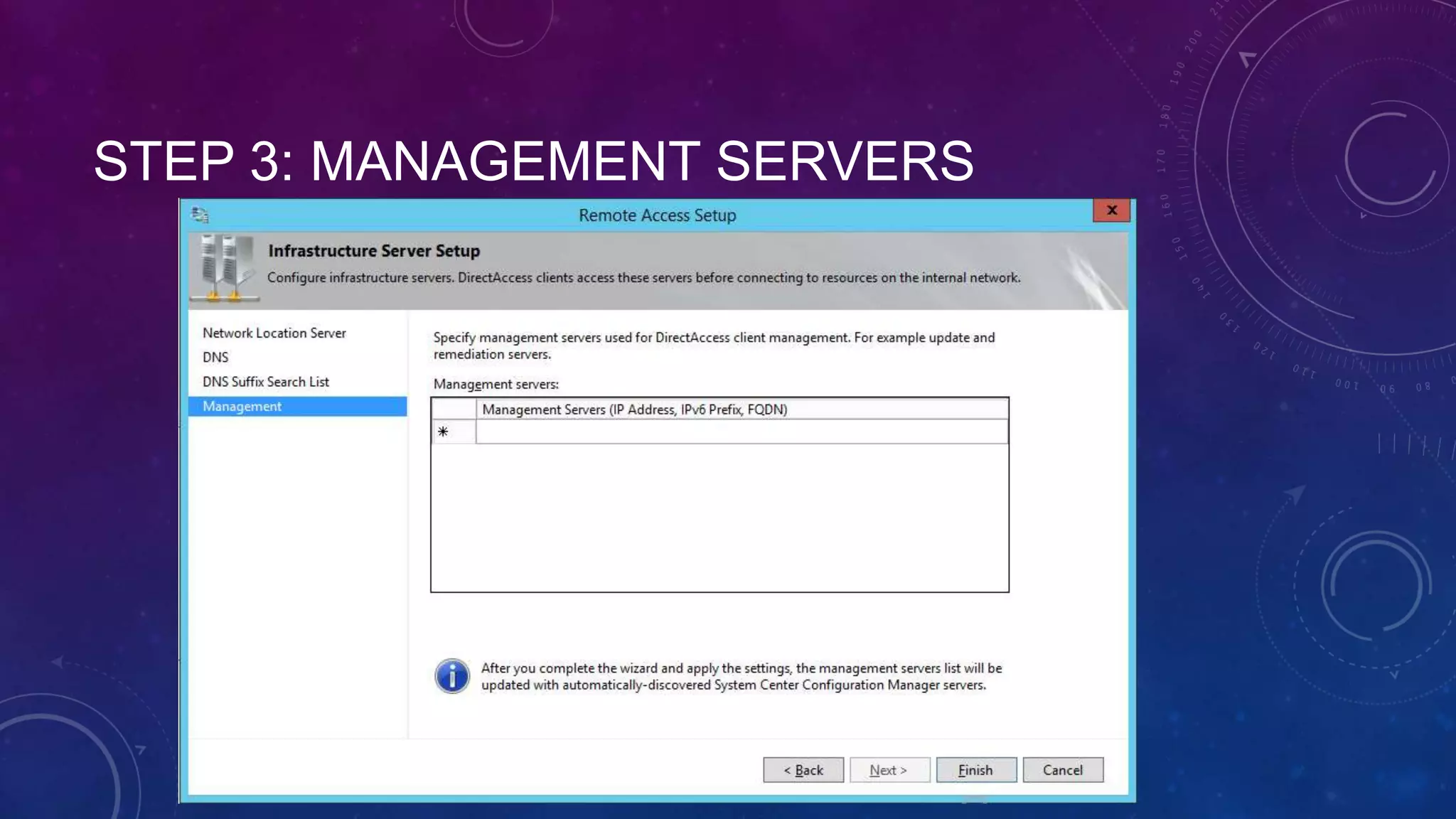
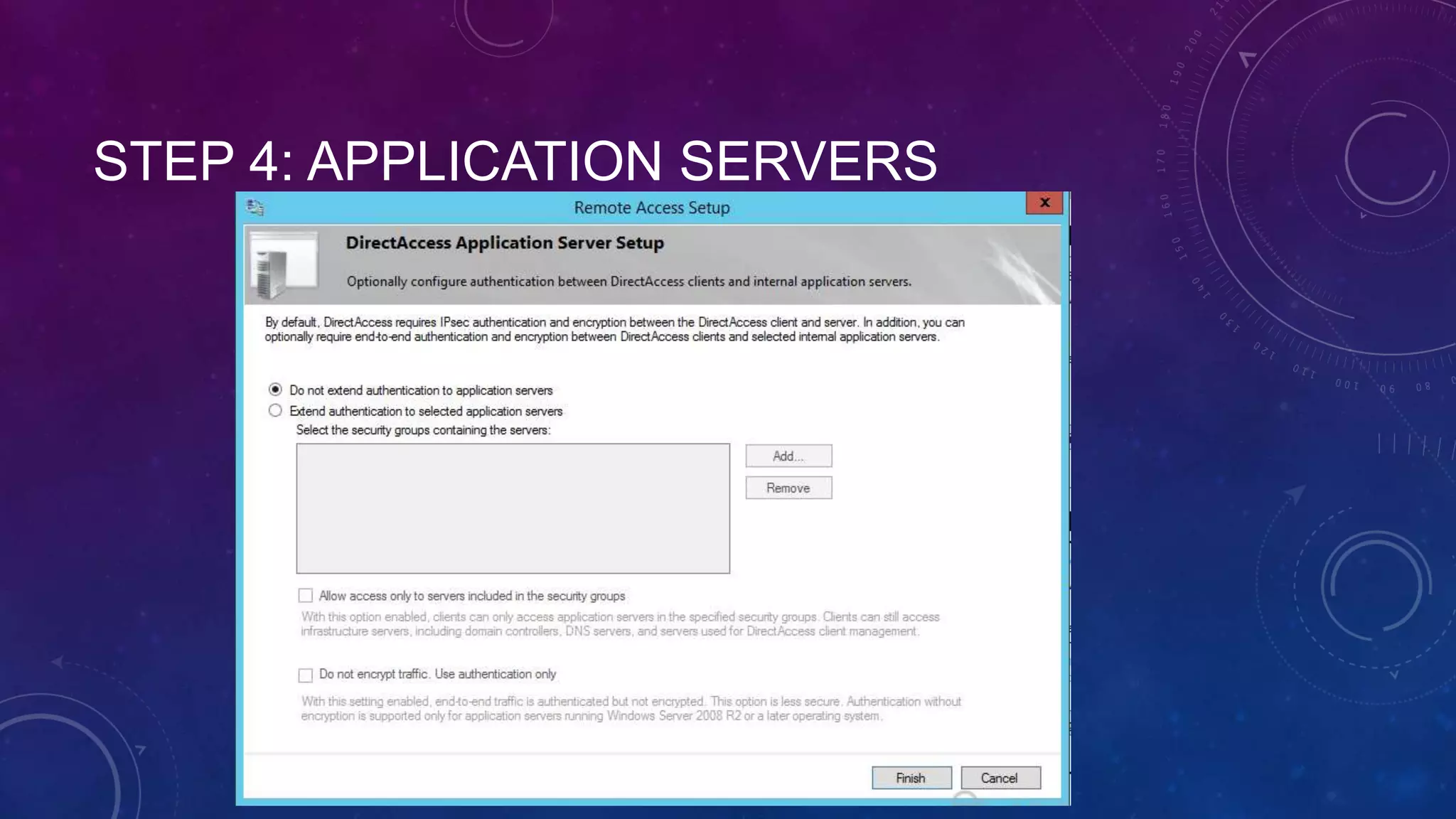
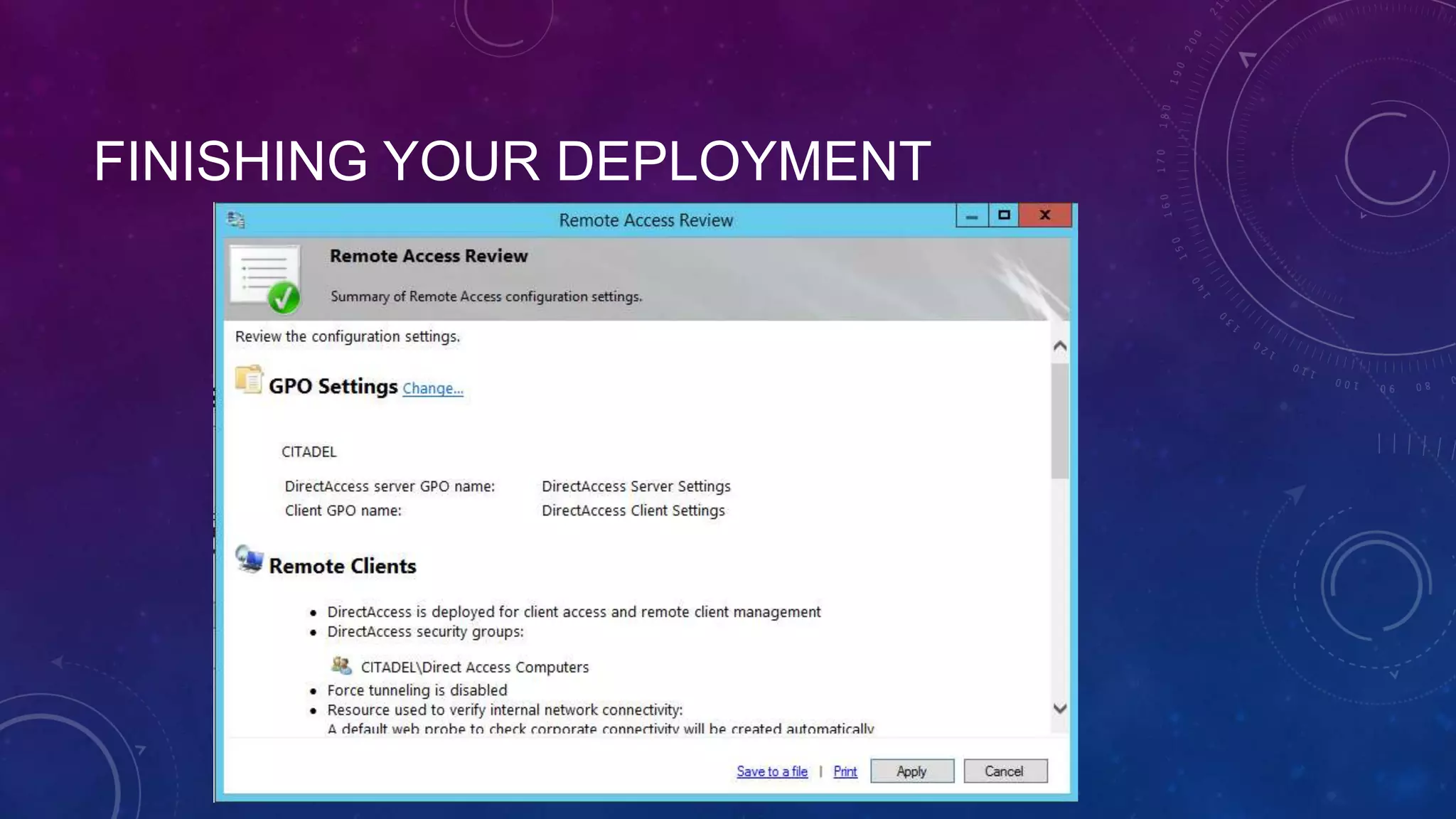
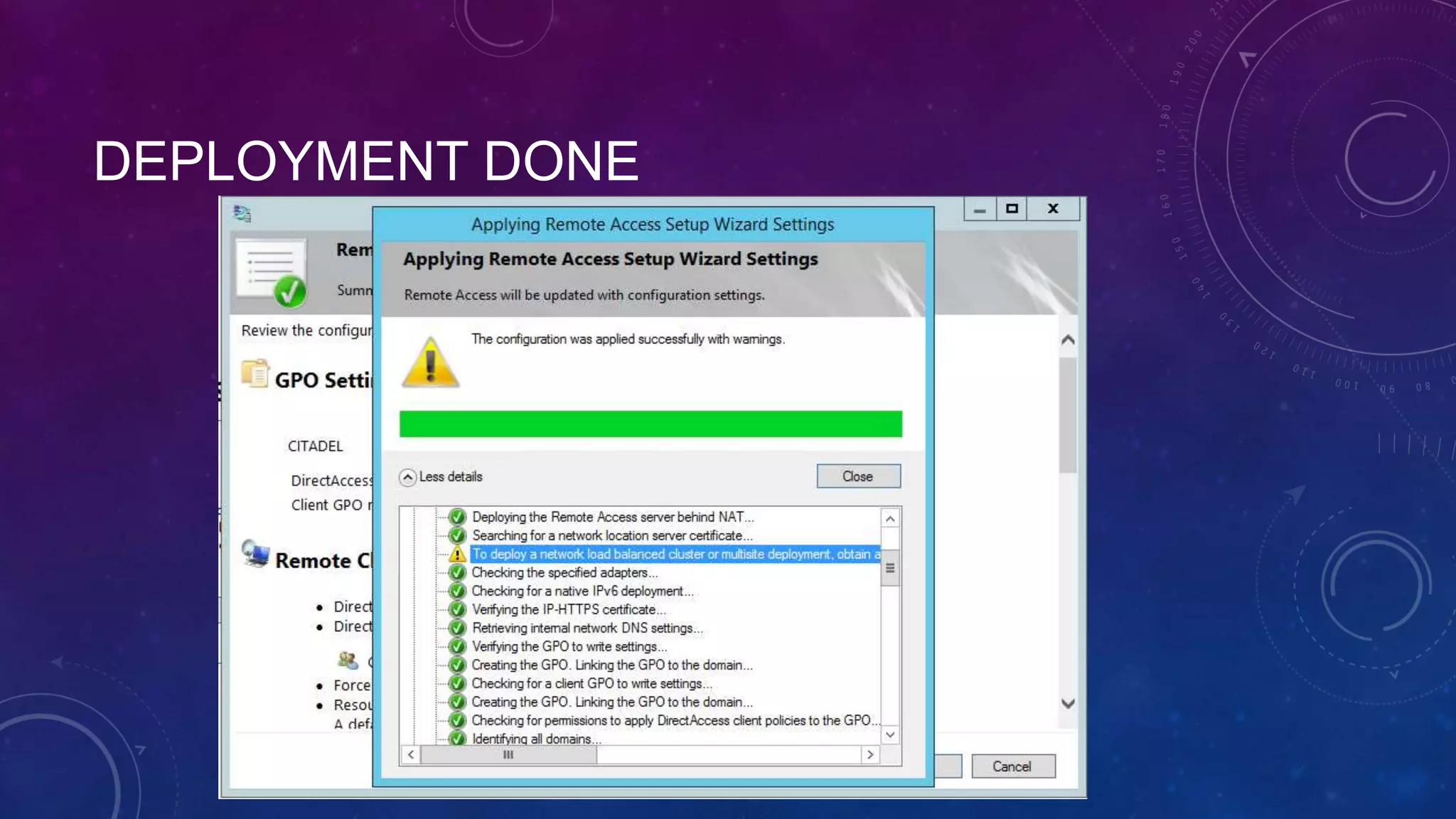
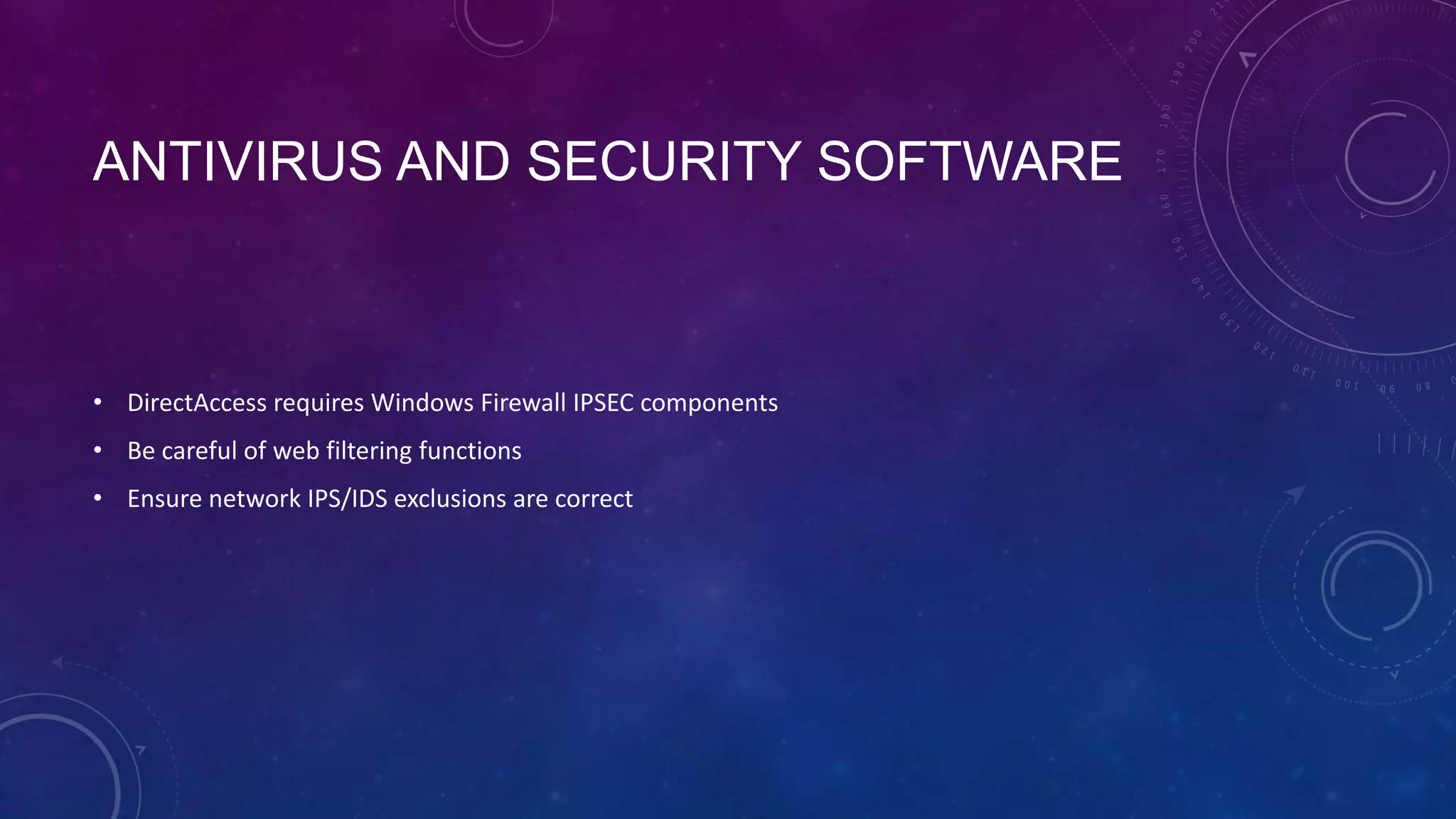
This document outlines the considerations and steps for deploying DirectAccess with emphasis on network configuration, authentication, and troubleshooting. It includes instructions on handling network location service, name resolution, managing group policies, and diagnostics for successful implementation. The document also provides best practices for configuring firewall and security measures relevant to DirectAccess deployment.