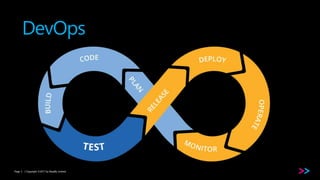
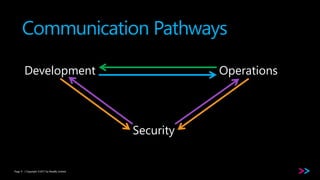
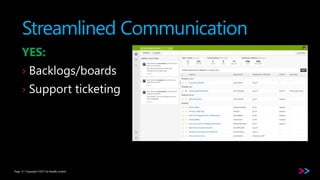
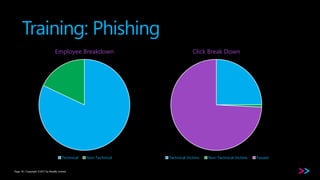
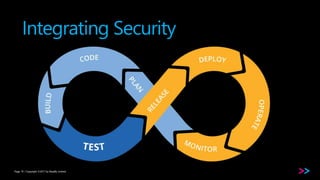
The document discusses the integration of security within DevOps through a concept called DevSecOps, emphasizing clear communication, streamlined processes, and the need for security as code. It outlines the importance of proper training and the incorporation of security in all phases of the development cycle, from planning to deployment and monitoring. Key strategies include using backlogs for communication, employing security tools, and developing comprehensive testing cases.