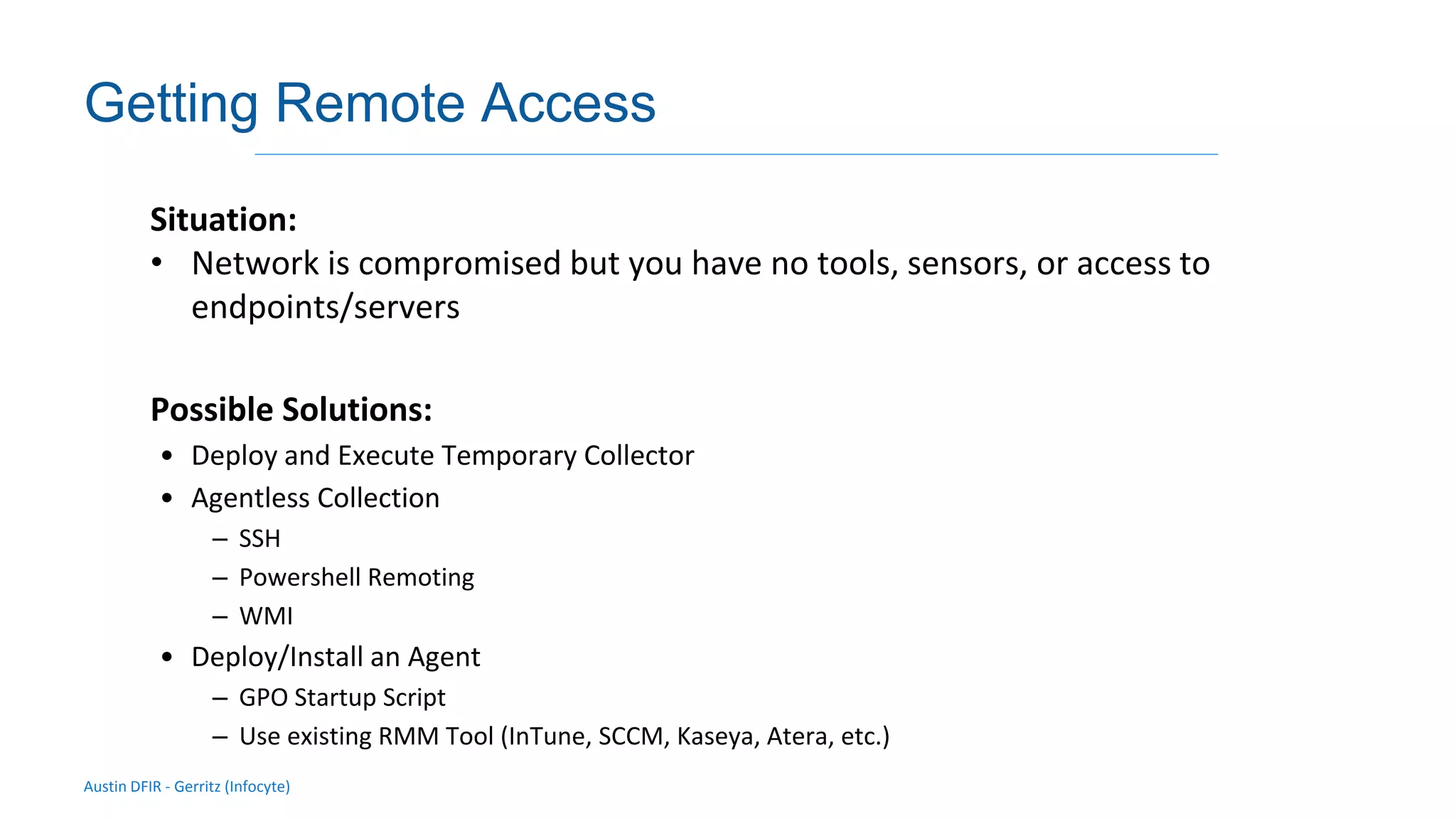
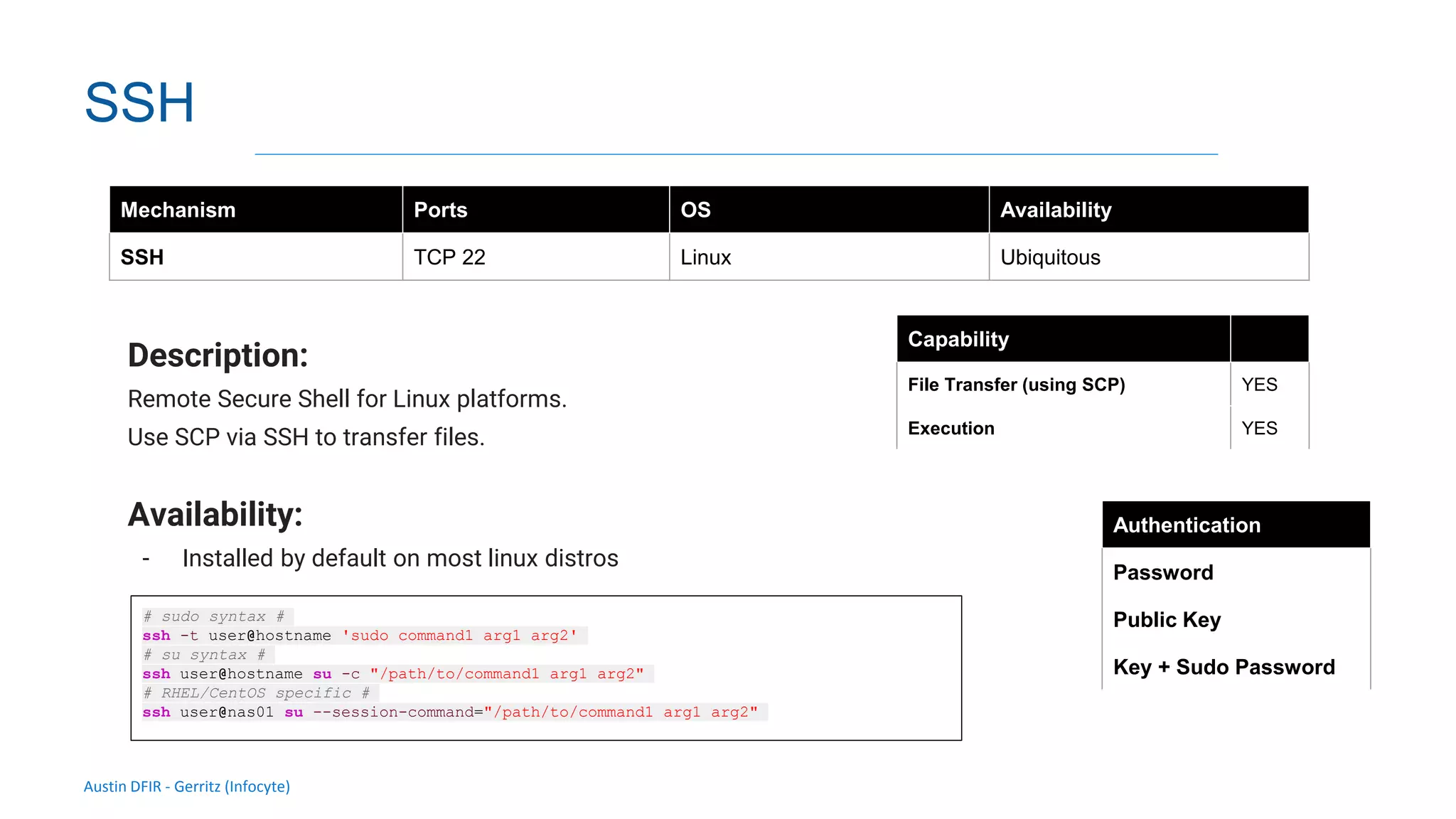
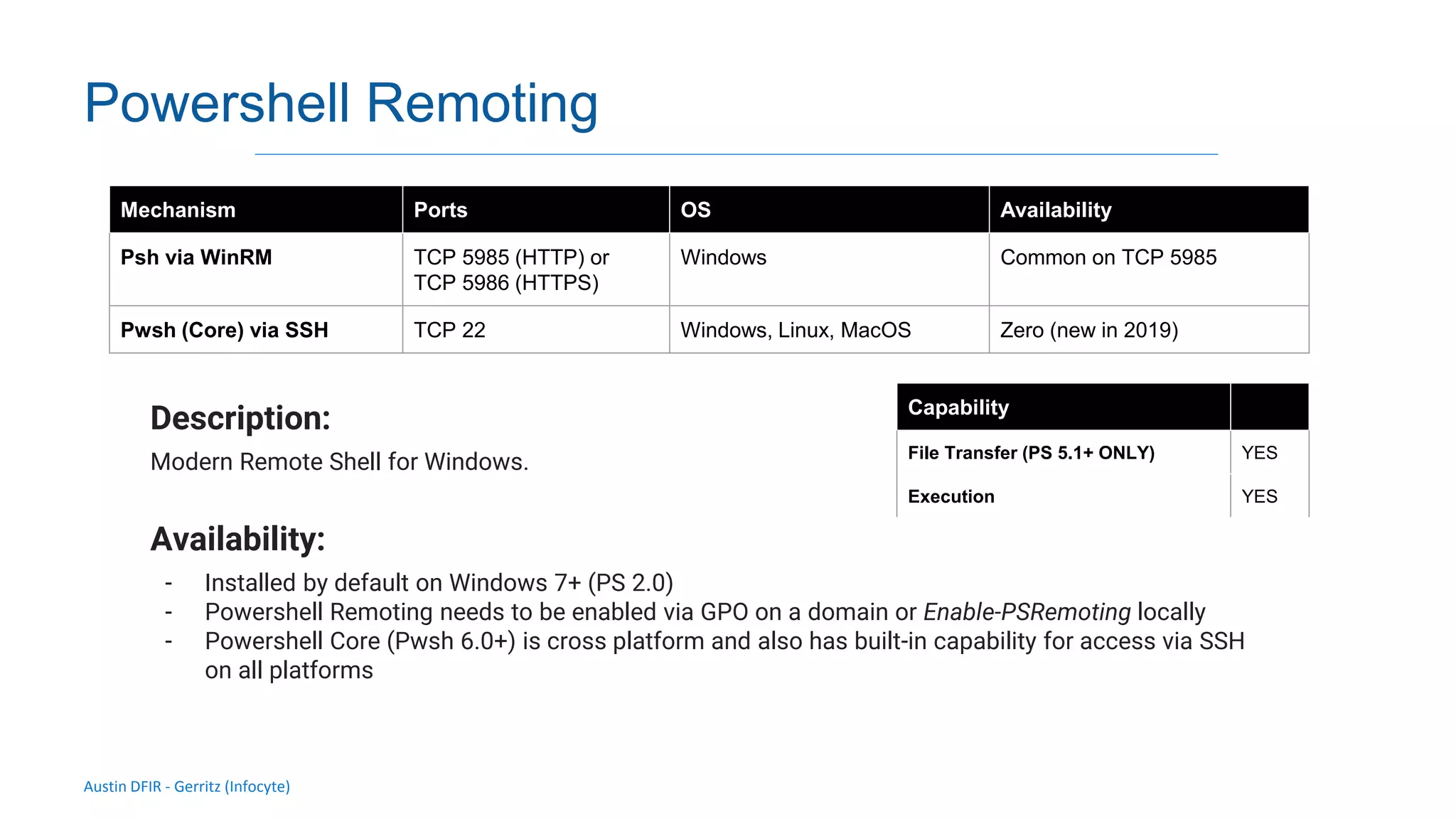
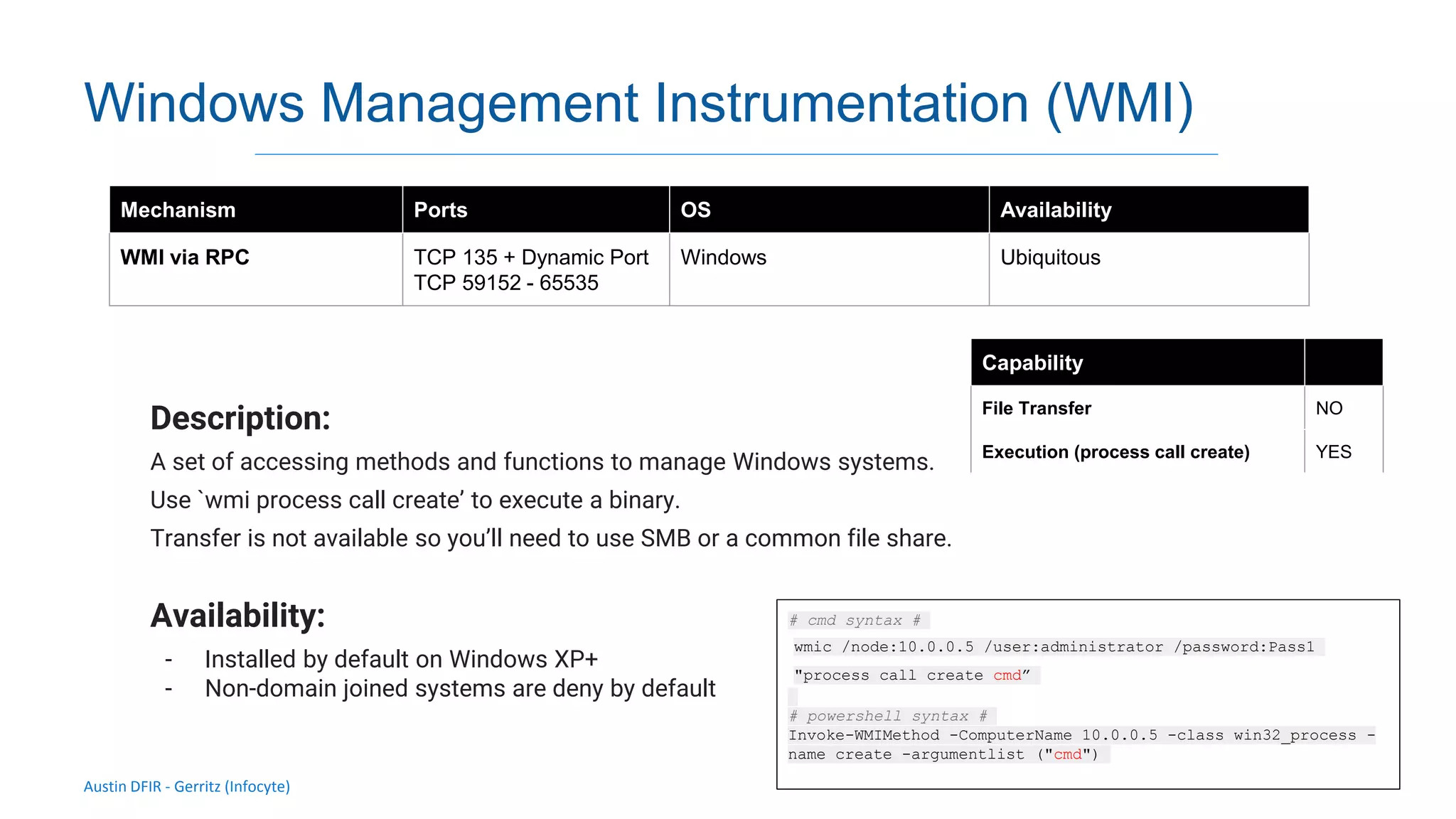
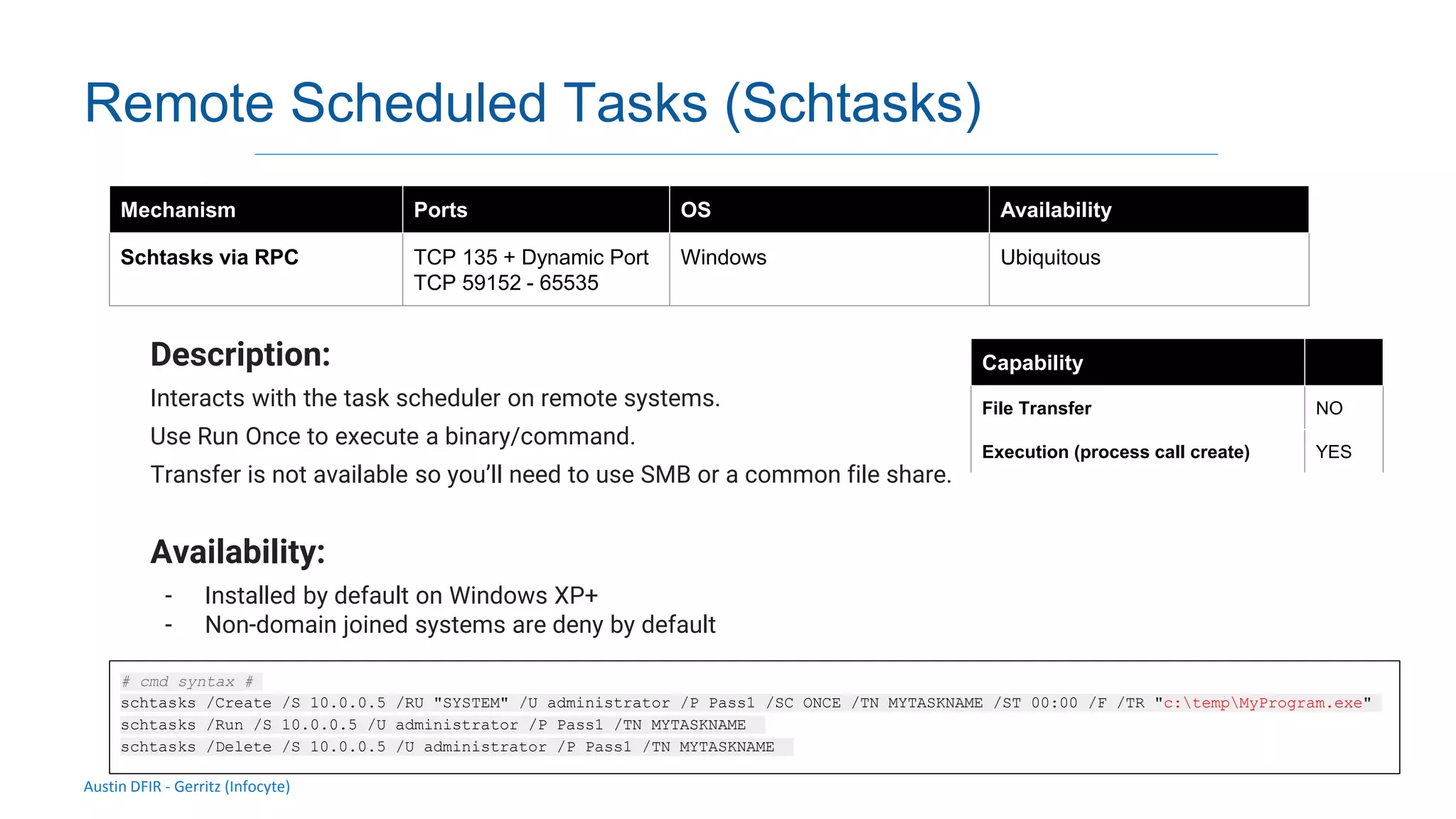
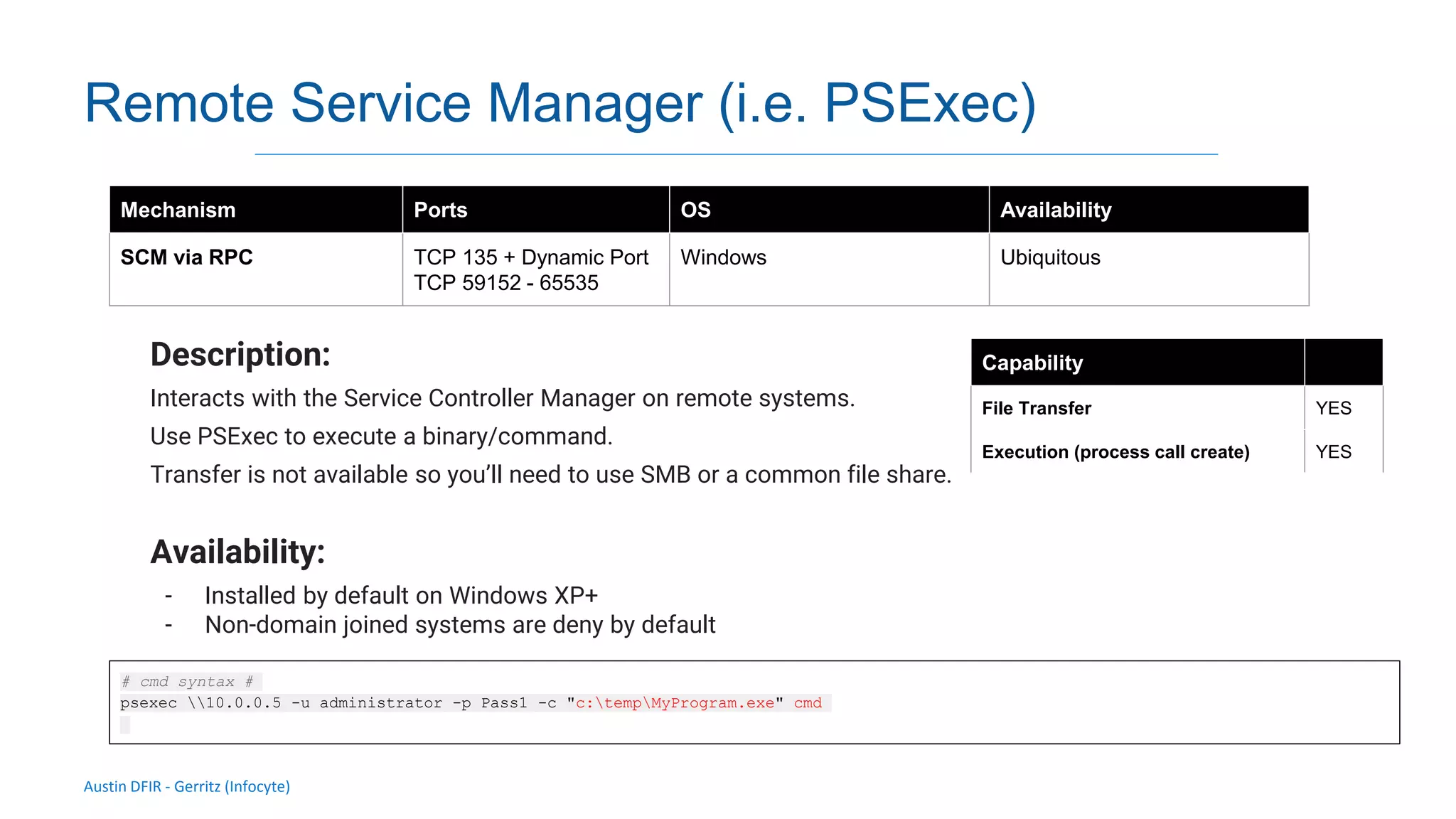
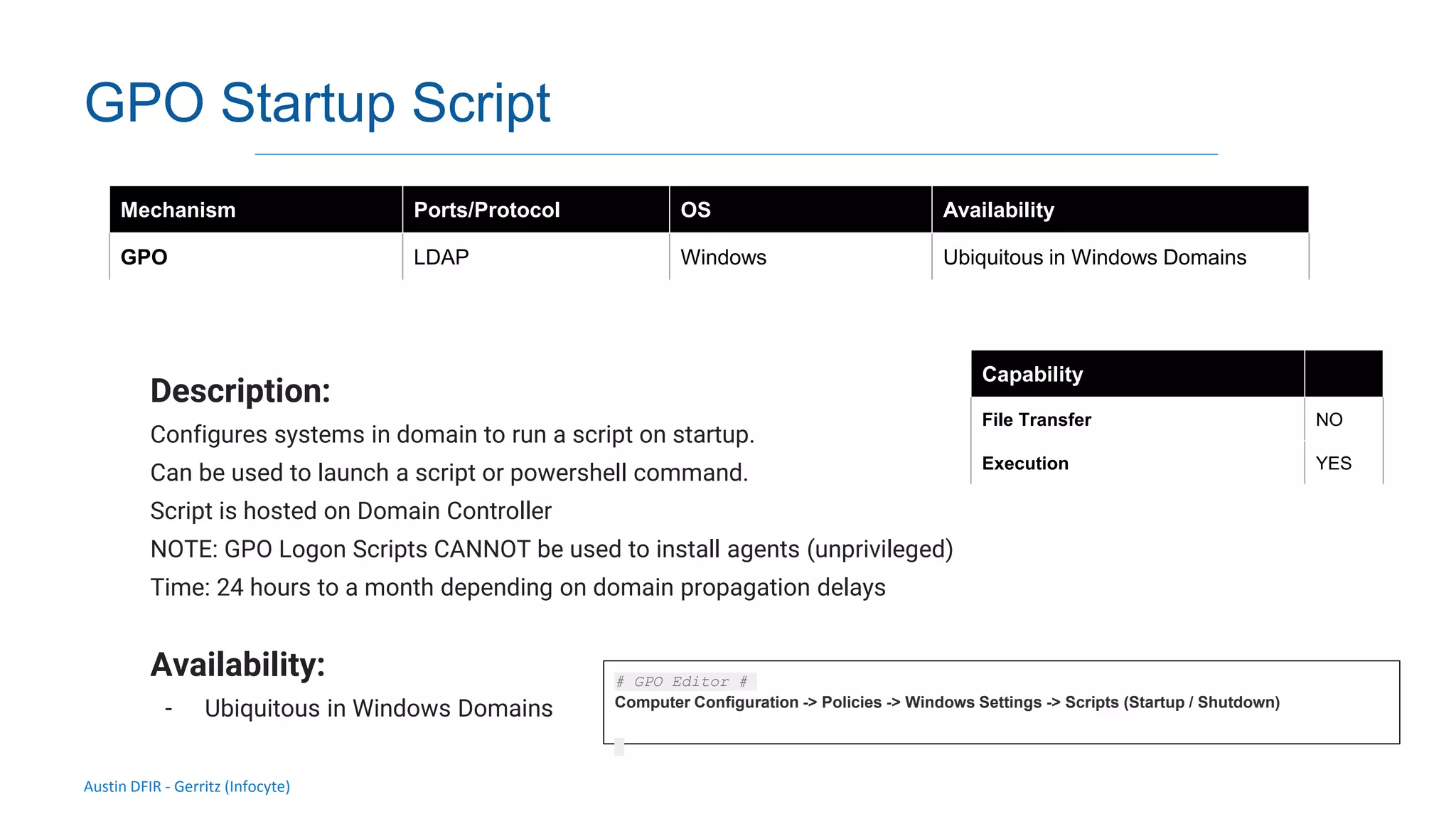
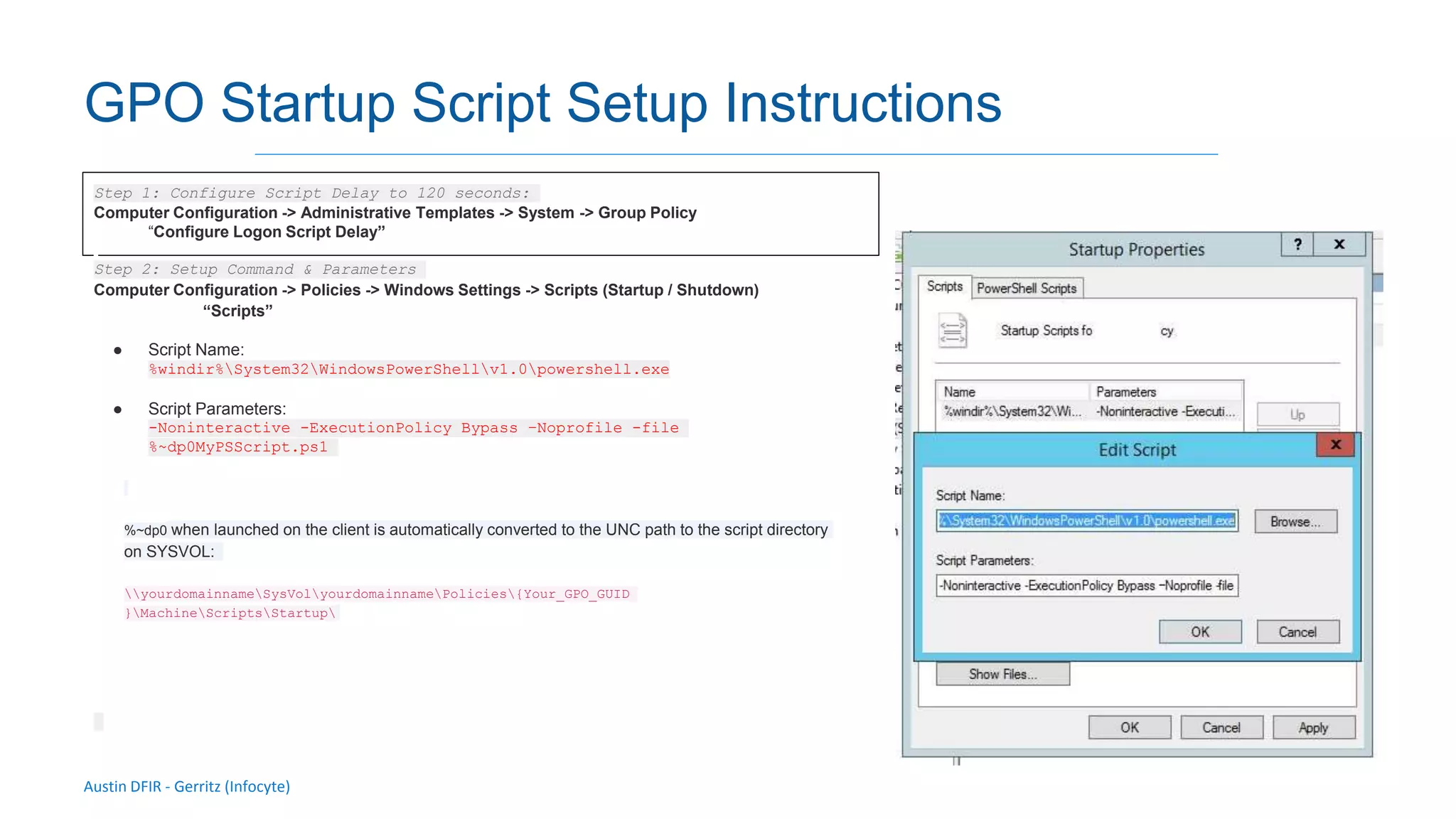
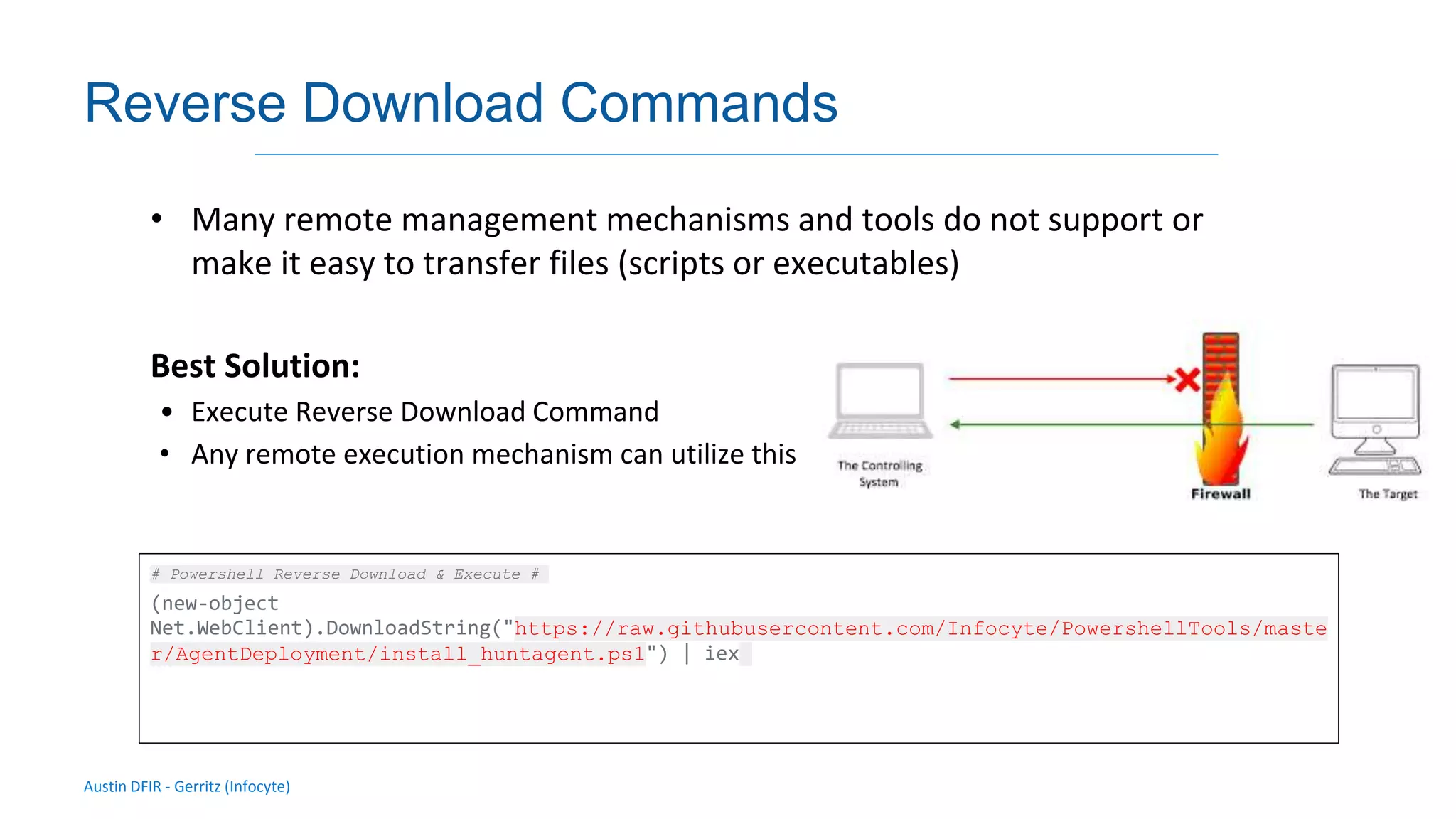
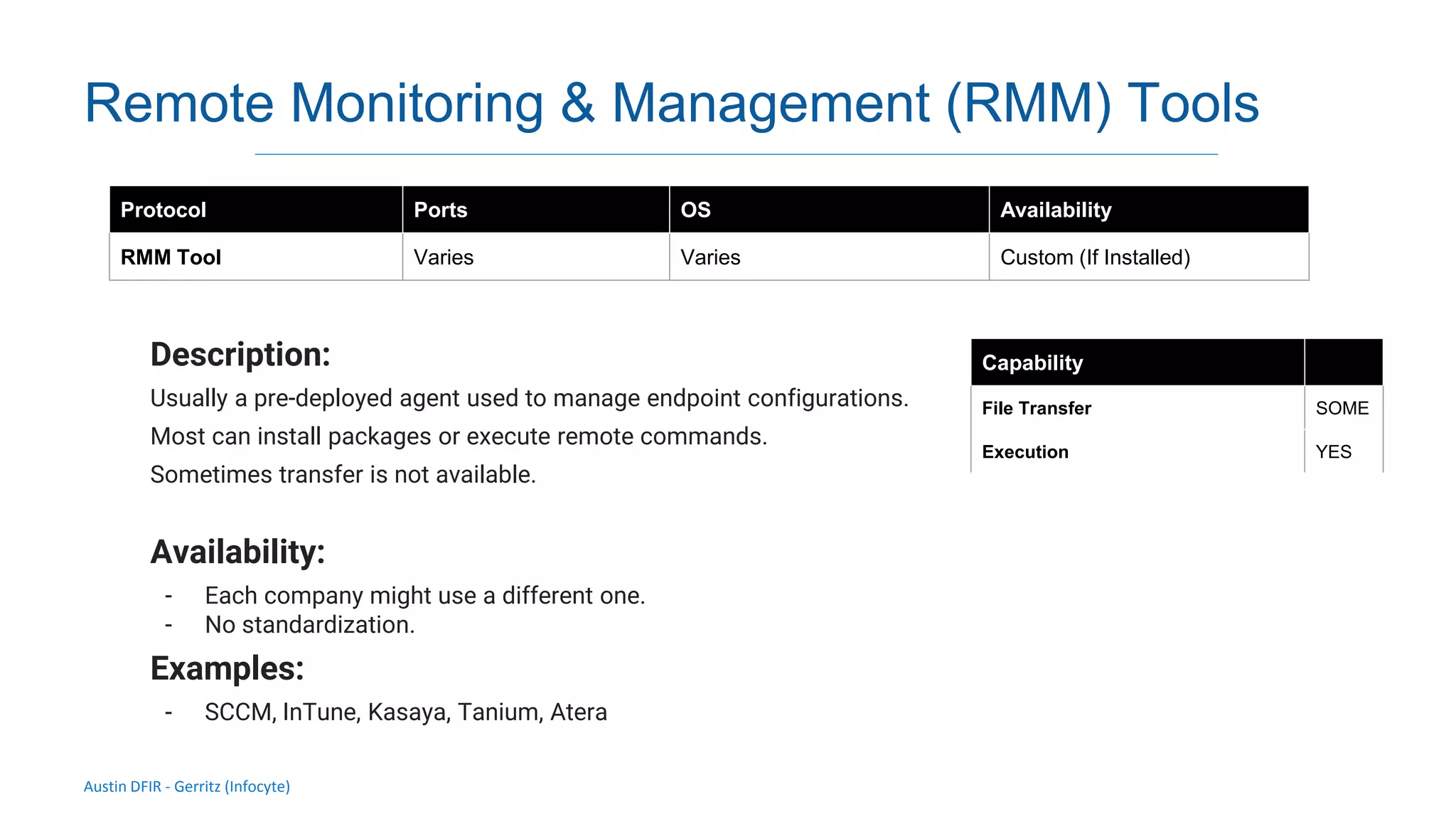
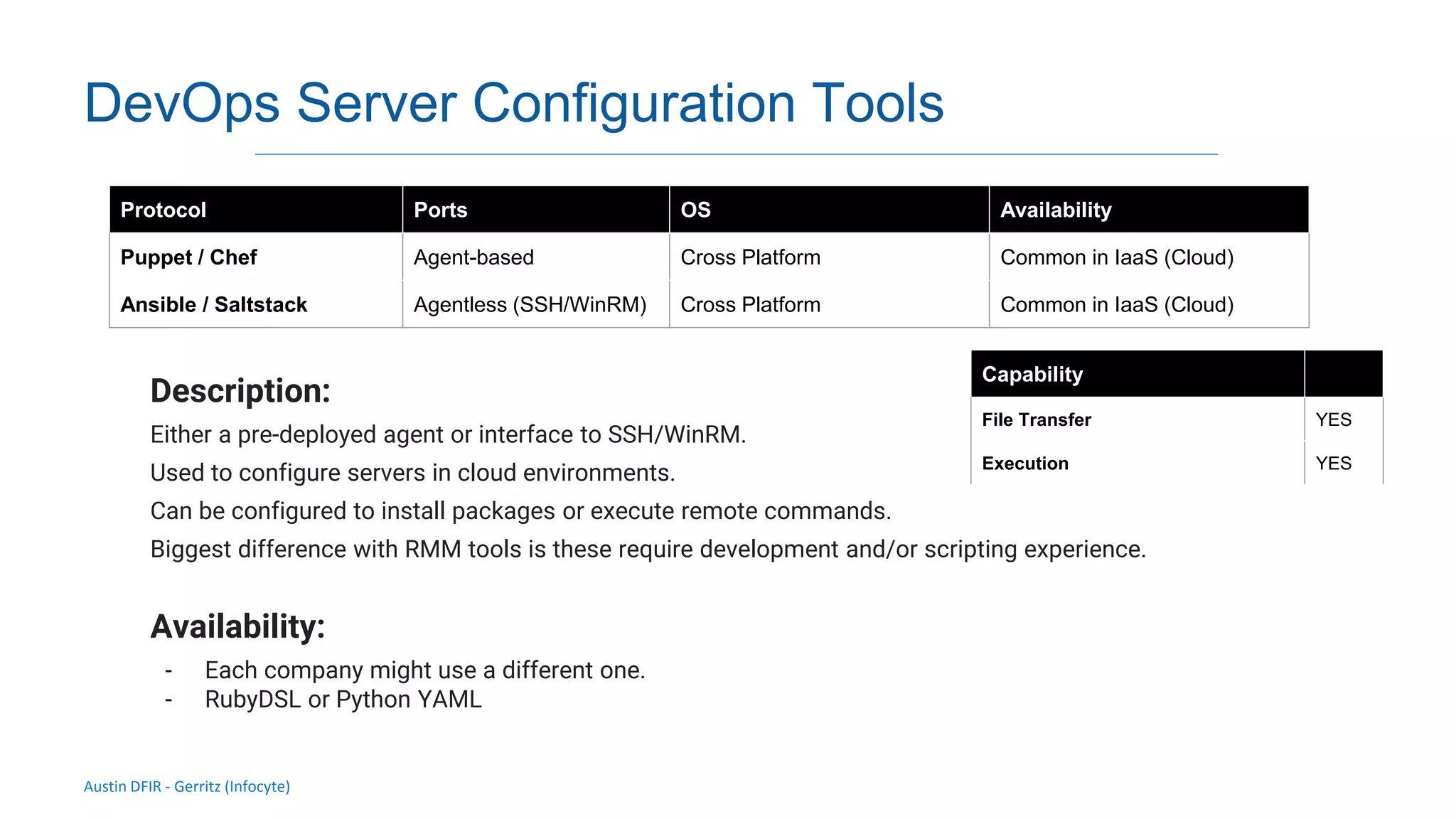
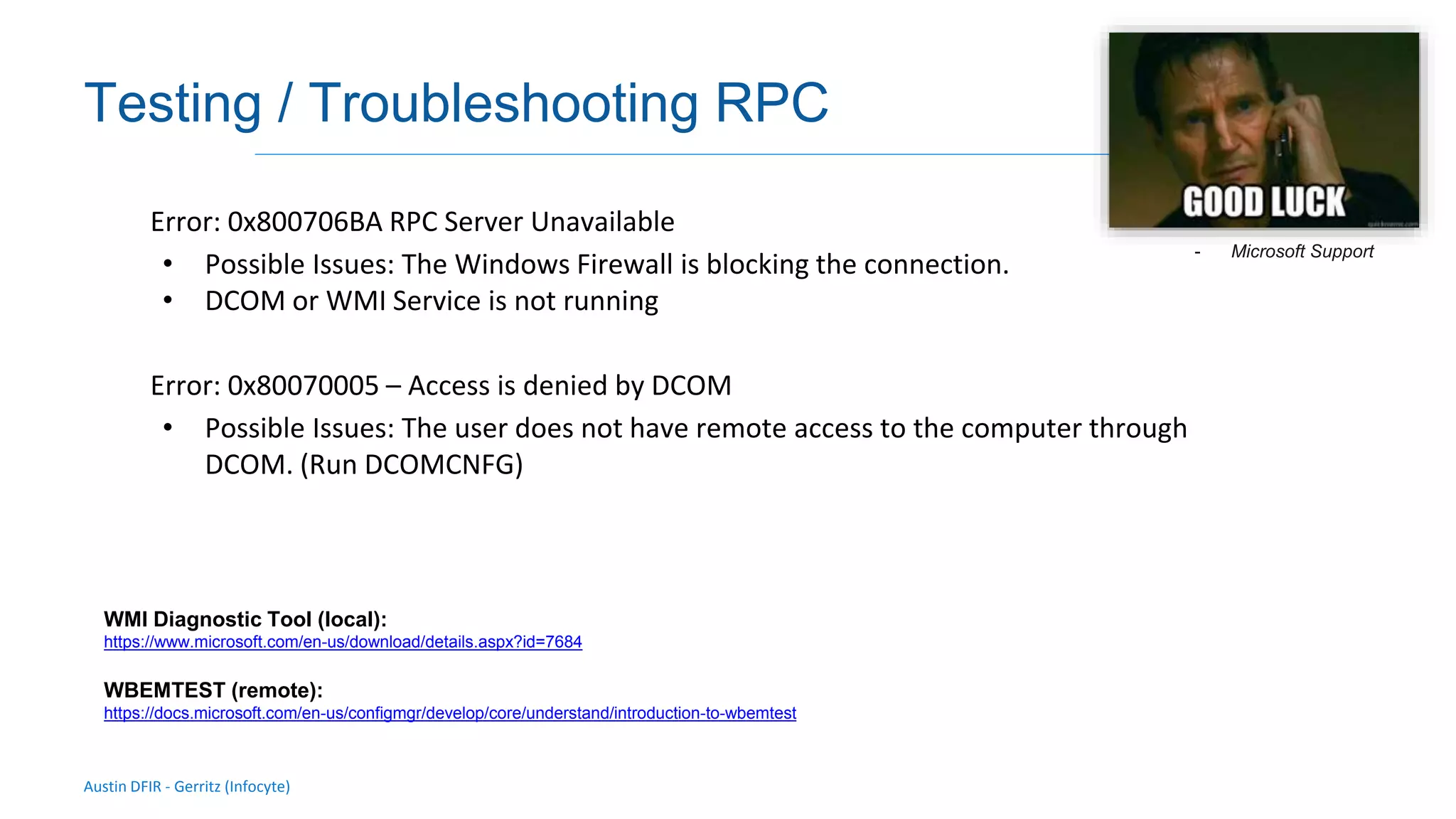
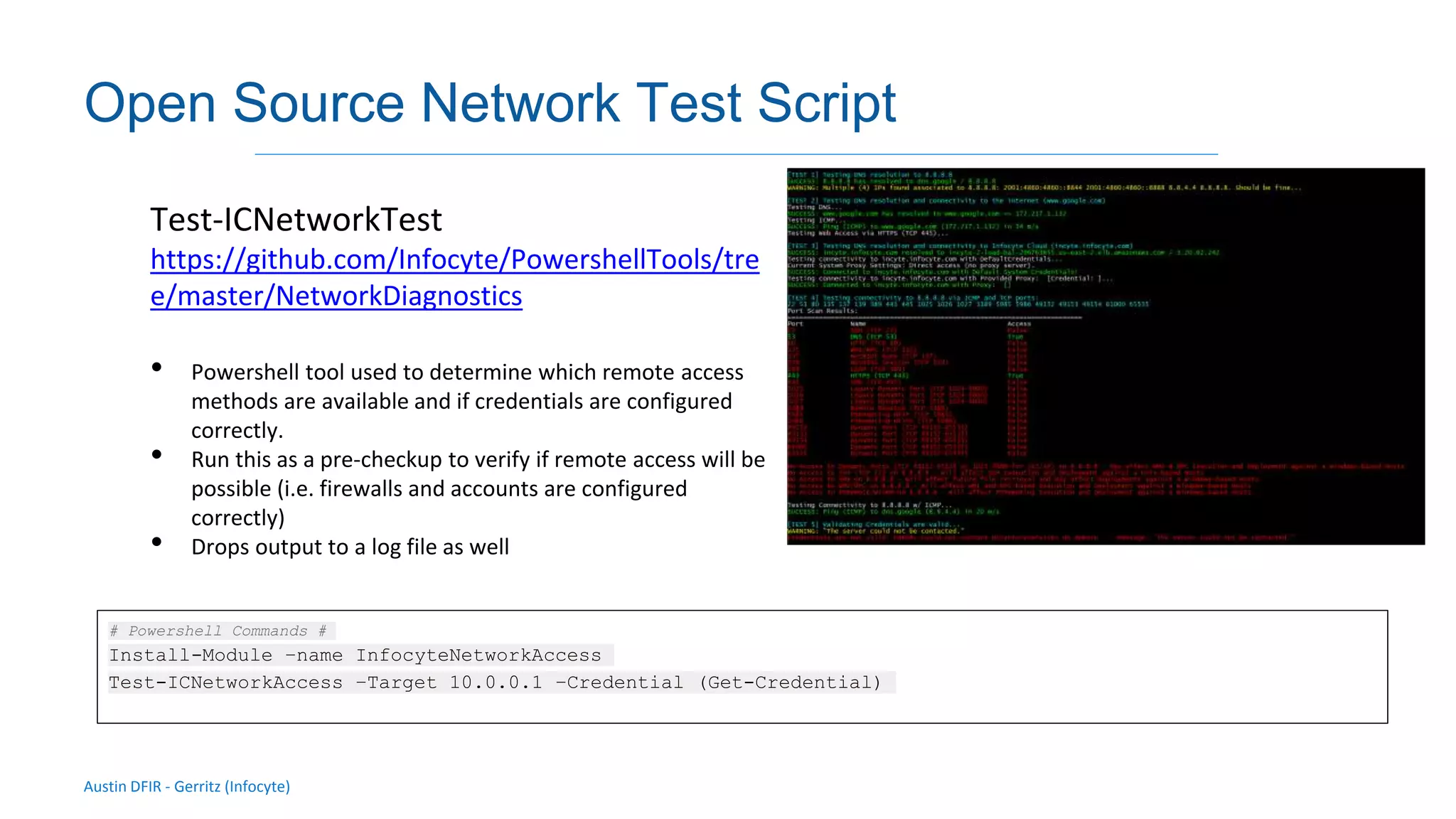
The document discusses methods for remote access and agent deployment in compromised networks, detailing various techniques such as SSH, PowerShell Remoting, and Windows Management Instrumentation. It provides information on executing commands remotely, validating integrity via live forensic analysis, and troubleshooting RPC errors. Additionally, it highlights tools for remote management and DevOps server configuration, along with guidelines for testing remote access capabilities.