Embed presentation
Downloaded 25 times

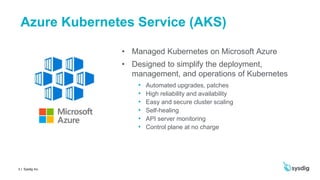
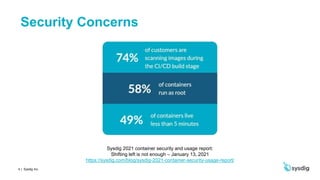

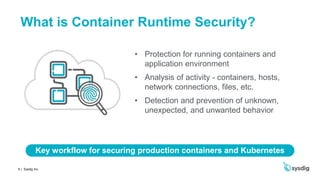
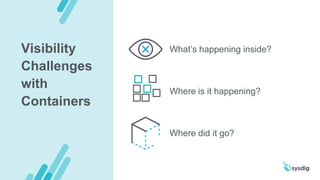
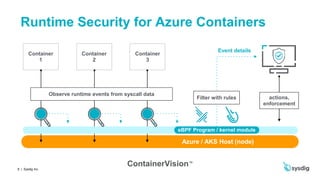
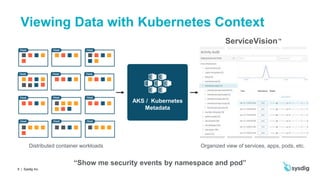
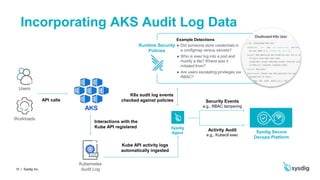
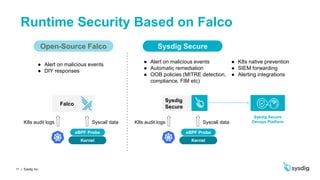
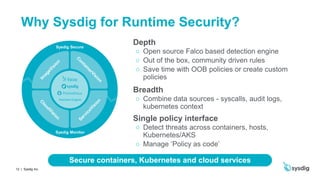
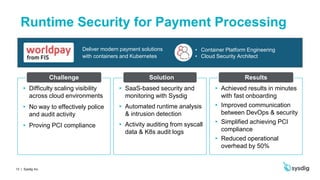

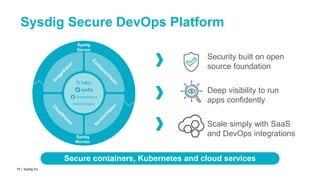


This document discusses runtime security on Azure Kubernetes Service (AKS). It begins by introducing AKS and how it simplifies Kubernetes deployment and management. It then discusses the security concerns with containers and the need for runtime security. Runtime security involves monitoring activity within containers to detect unwanted behaviors. The document outlines how Sysdig provides runtime security for AKS through its agents that collect syscall data and Kubernetes audit logs. It analyzes this data using policies to detect anomalies and threats across containers, hosts, and Kubernetes clusters. Sysdig also integrates with other tools like Falco and Anchore to provide breadth and depth of security.
















