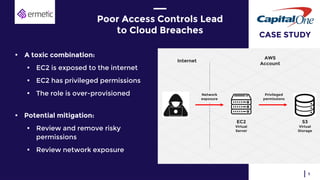
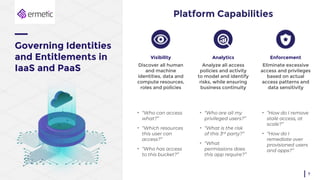
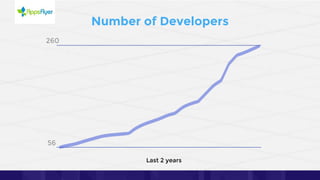
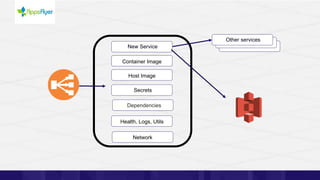
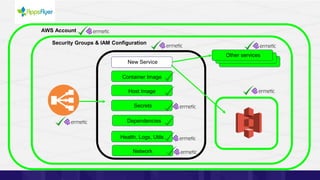
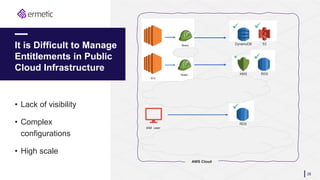
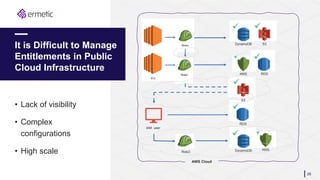
The document discusses the challenges of managing identities and entitlements in cloud infrastructure, highlighting that by 2023, 75% of security failures will stem from IAM mismanagement. It cites a case study from Appsflyer, emphasizing the risks associated with poor access controls and misconfigurations, as well as the emergence of new categories like Cloud Infrastructure Entitlement Management (CIEM). Additionally, it presents a solution through Ermetic's full-stack governance and entitlement management to enhance visibility and control in cloud environments.