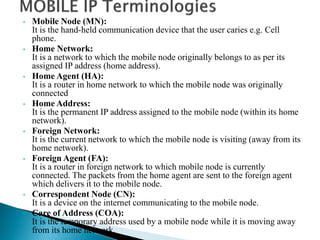
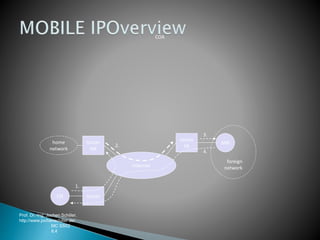
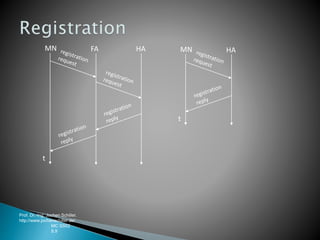
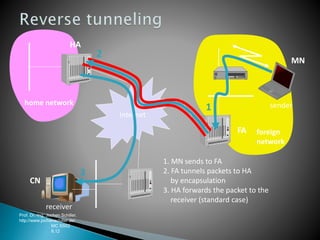
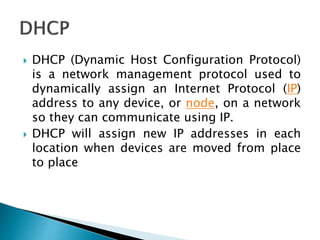
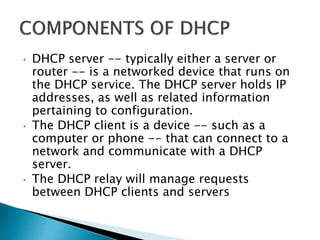
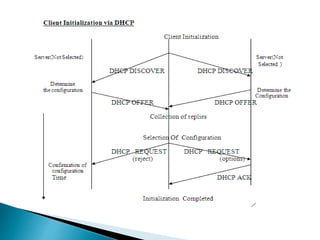
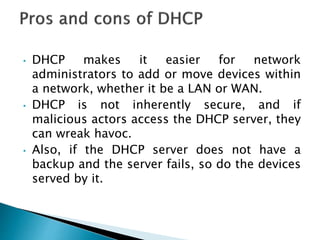
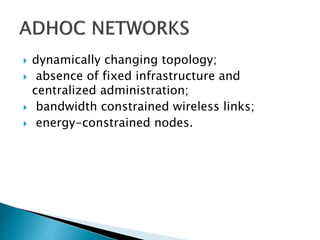
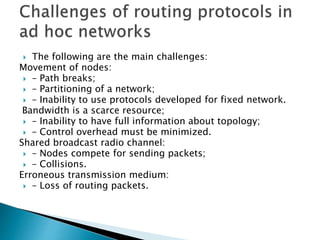
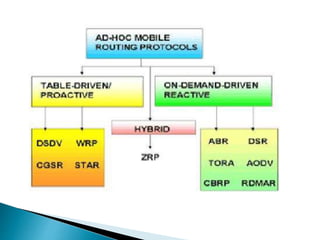
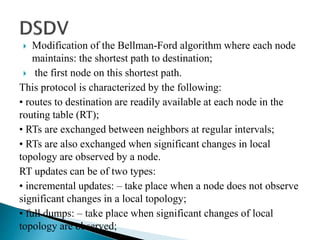
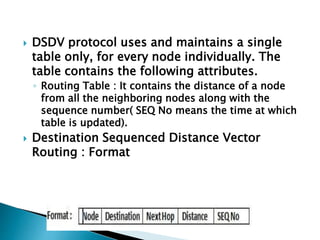
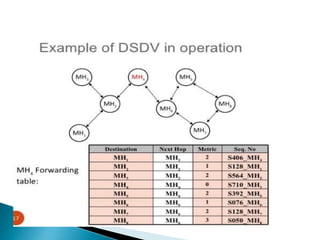
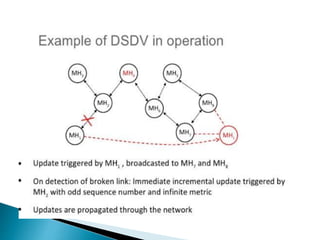
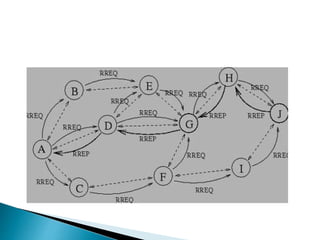
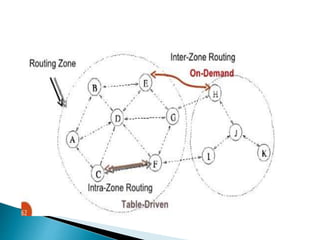
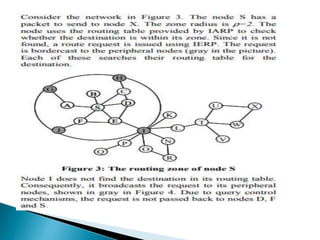
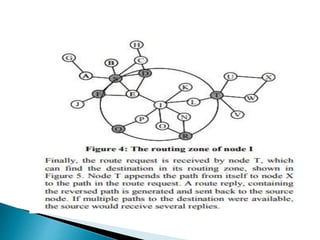
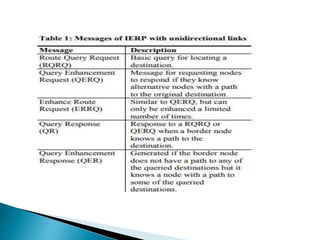
The document discusses Mobile IP, which allows mobile devices to change networks while maintaining the same IP address. It describes key concepts like mobile nodes, home networks, foreign agents, and care-of addresses. The mobile IP process involves agent discovery, registration of the mobile node's location, and tunneling of data packets through foreign agents. Dynamic Host Configuration Protocol (DHCP) is also discussed, which dynamically assigns IP addresses to devices on a network.