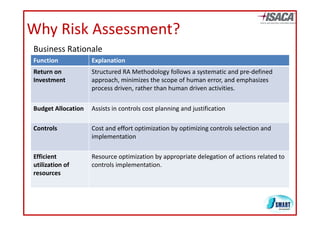
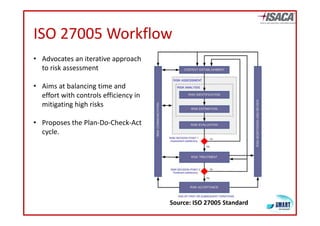
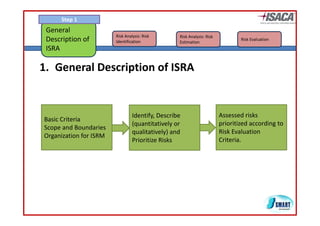
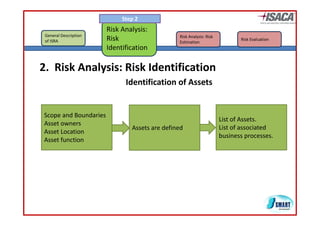
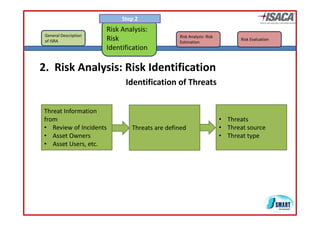
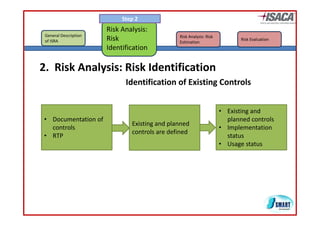
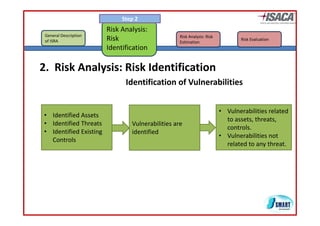
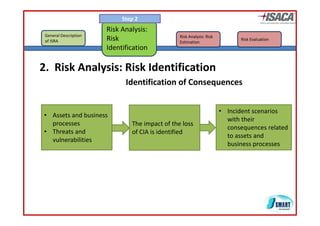
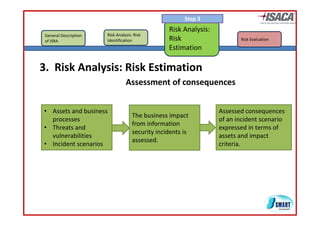
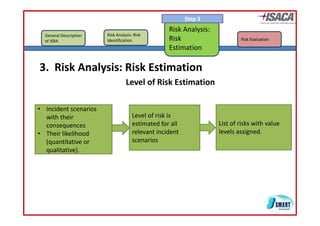
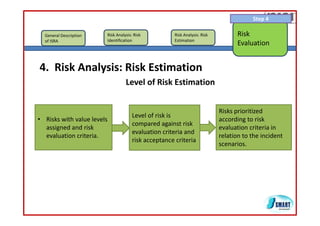
The document discusses risk assessment as per ISO 27005, detailing its methodology, importance for regulatory compliance, and its structured approach which minimizes human error. It emphasizes risk analysis, estimation, and evaluation as key components in developing an organization's security profile. Additionally, it outlines the iterative workflow of risk assessment, focusing on identifying assets, threats, existing controls, and vulnerabilities.