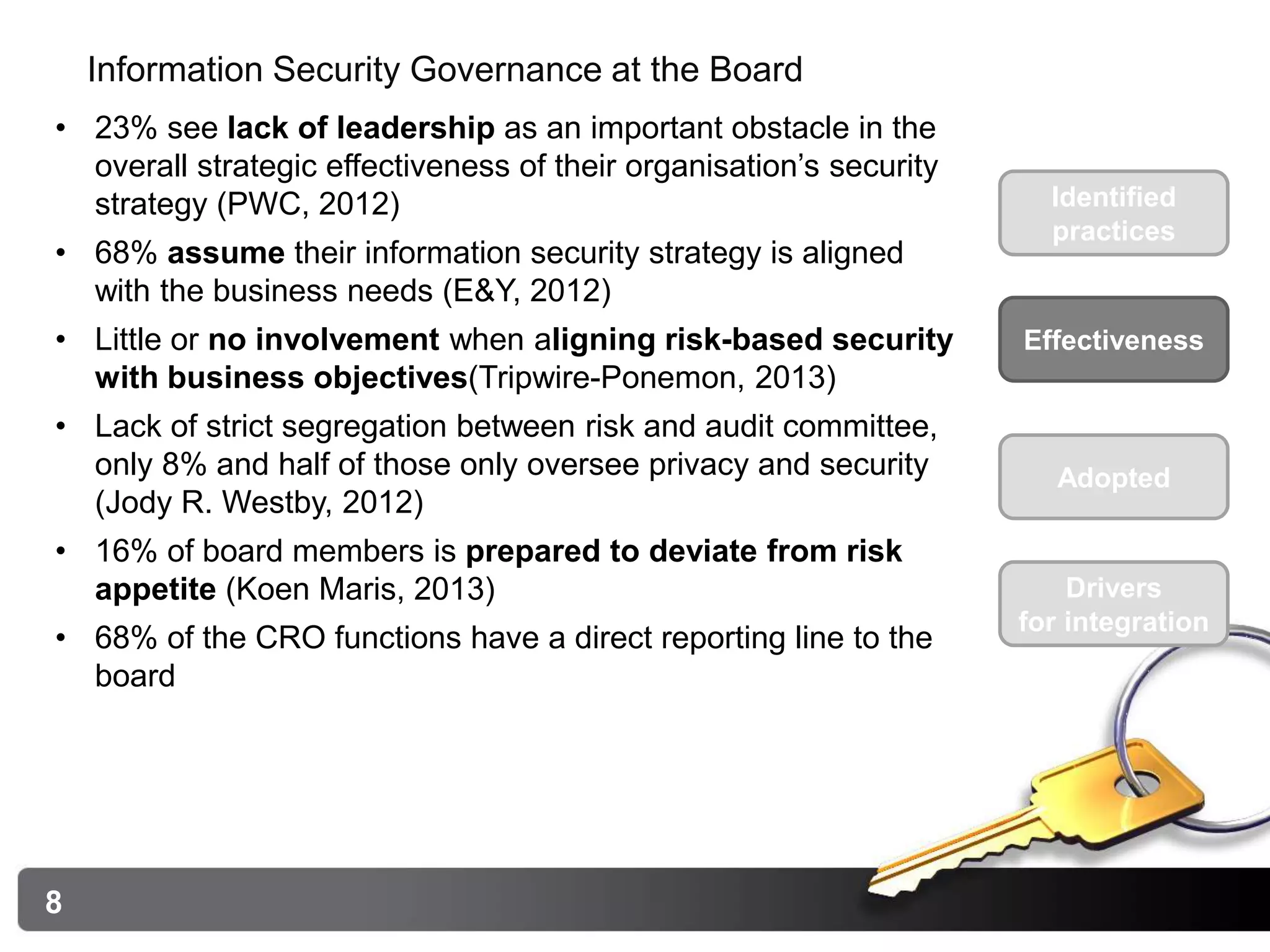
The document summarizes research into information security governance awareness at the board of director and executive committee levels. It finds that while many organizations have information security practices in place, such as a chief information security officer and security policies, the effectiveness and alignment with business objectives is unclear. Reporting and monitoring have room for improvement, and awareness remains a challenge. Drivers for implementing governance are typically severe security incidents and legal/regulatory compliance pressures rather than proactive alignment with business strategy.