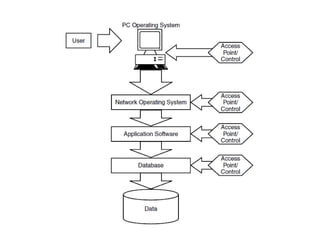
Compliance measures adherence to defined policies and procedures through auditing, monitoring, and investigating at multiple organizational levels. Level one focuses on component owners ensuring appropriate access controls. Level two involves auditing functions assessing internal controls. Level three is the security team responsible for organization-wide implementation of security. Effective compliance requires coordination across these levels.