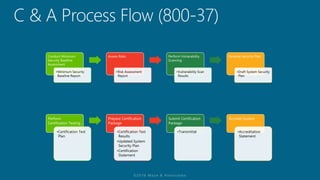
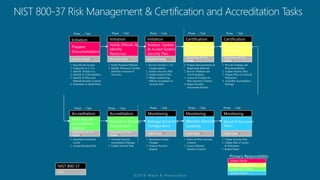
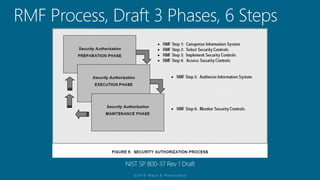
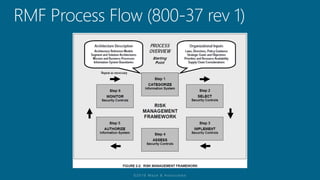
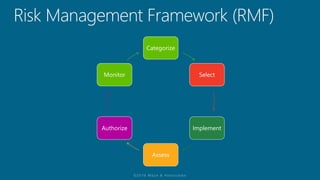
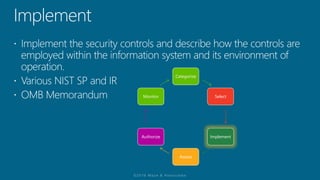
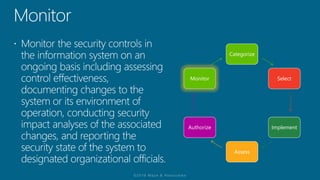
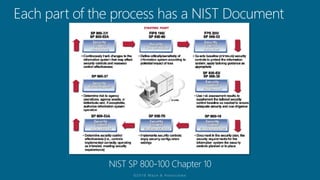
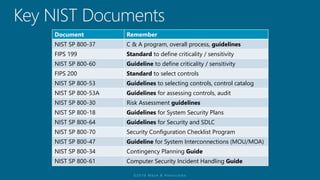
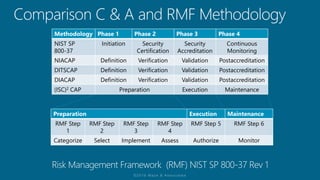
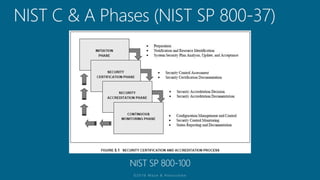
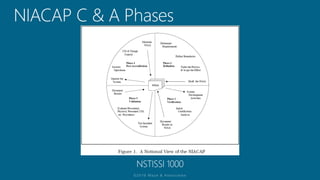
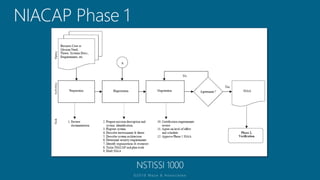
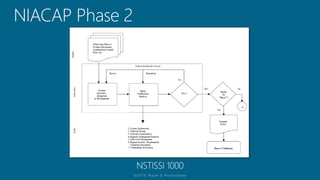
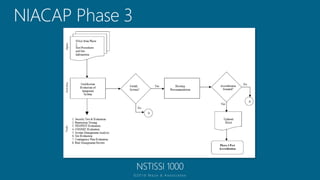
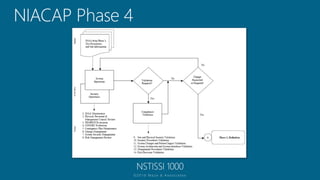
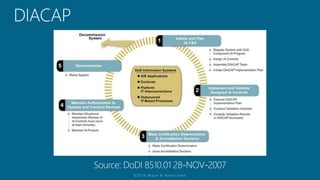
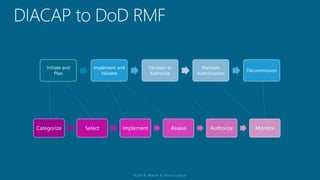
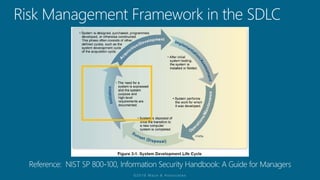
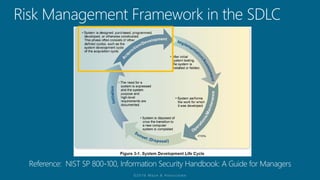
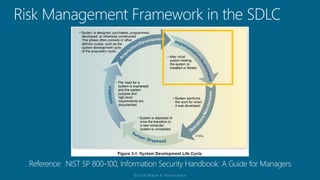
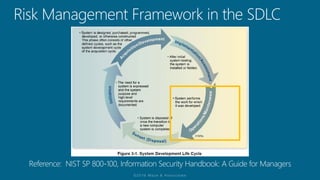
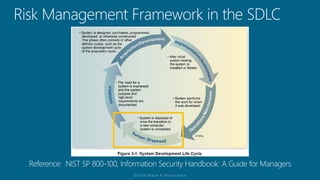
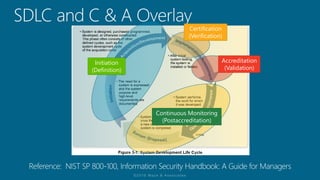
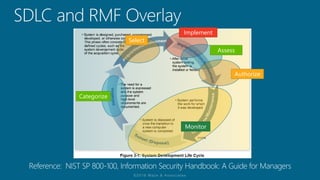
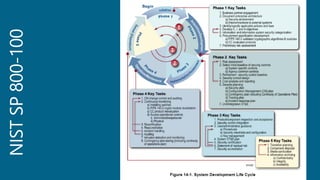
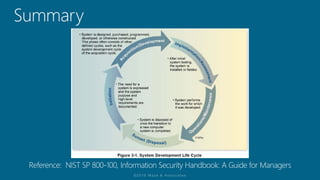
The document outlines a structured approach for conducting a minimum security baseline assessment within the context of the system development life cycle (SDLC) as per NIST guidelines. It details phases such as initiation, planning, implementation, and maintenance, highlighting tasks like risk assessments, vulnerability scans, security control assessments, and the preparation of certification packages. Emphasis is placed on integrating security throughout all phases of the SDLC to maintain compliance with federal regulations and ensure effective overall security management.