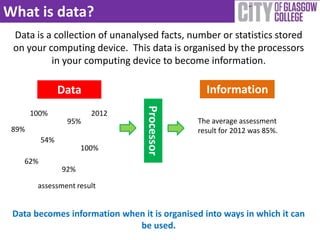
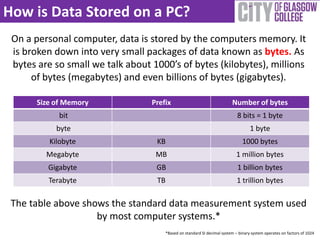
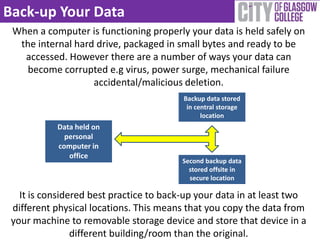
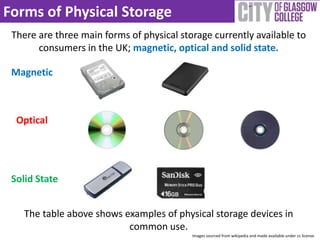
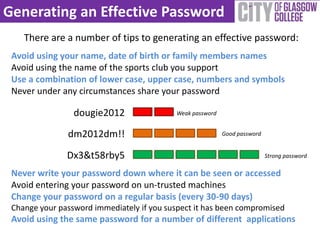
The document provides a comprehensive guide to data storage and protection, emphasizing the importance of properly managing data on computing devices. It discusses methods for storing data, including physical and web-based solutions, as well as best practices for backing up data and securing it against theft. Additionally, it offers tips for generating strong passwords and using security software to protect against malware.