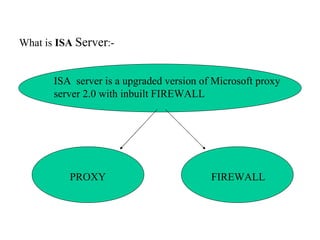
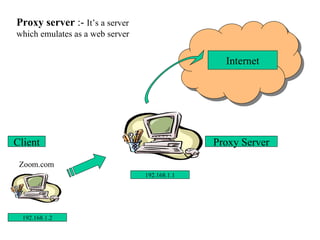
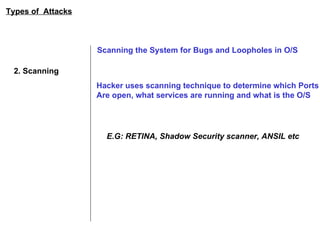
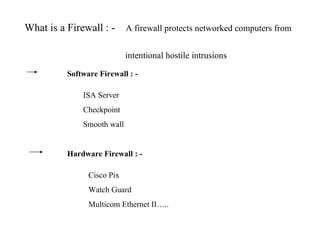
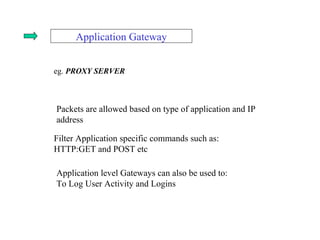
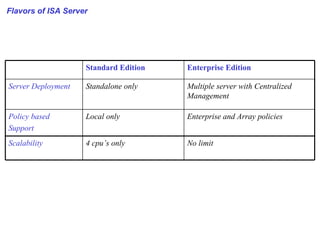
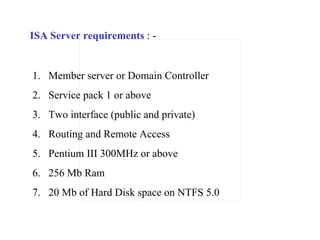
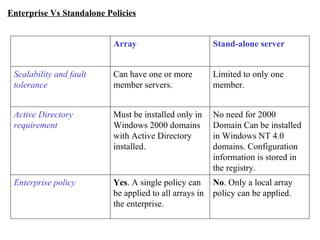
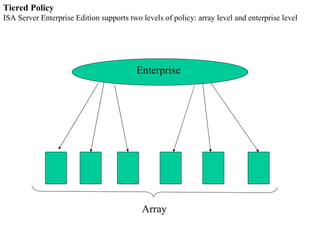
ISA server is an upgraded version of Microsoft proxy server with built-in firewall and proxy firewall capabilities. It functions as a firewall, web cache, and VPN server to protect networks. As a firewall, it uses packet filtering, application gateways, and stateful inspection to control access based on source/destination IP addresses, ports, applications, and traffic rules. It also provides features like server publishing, intrusion detection, quality of service controls, and centralized management of multiple servers through arrays.