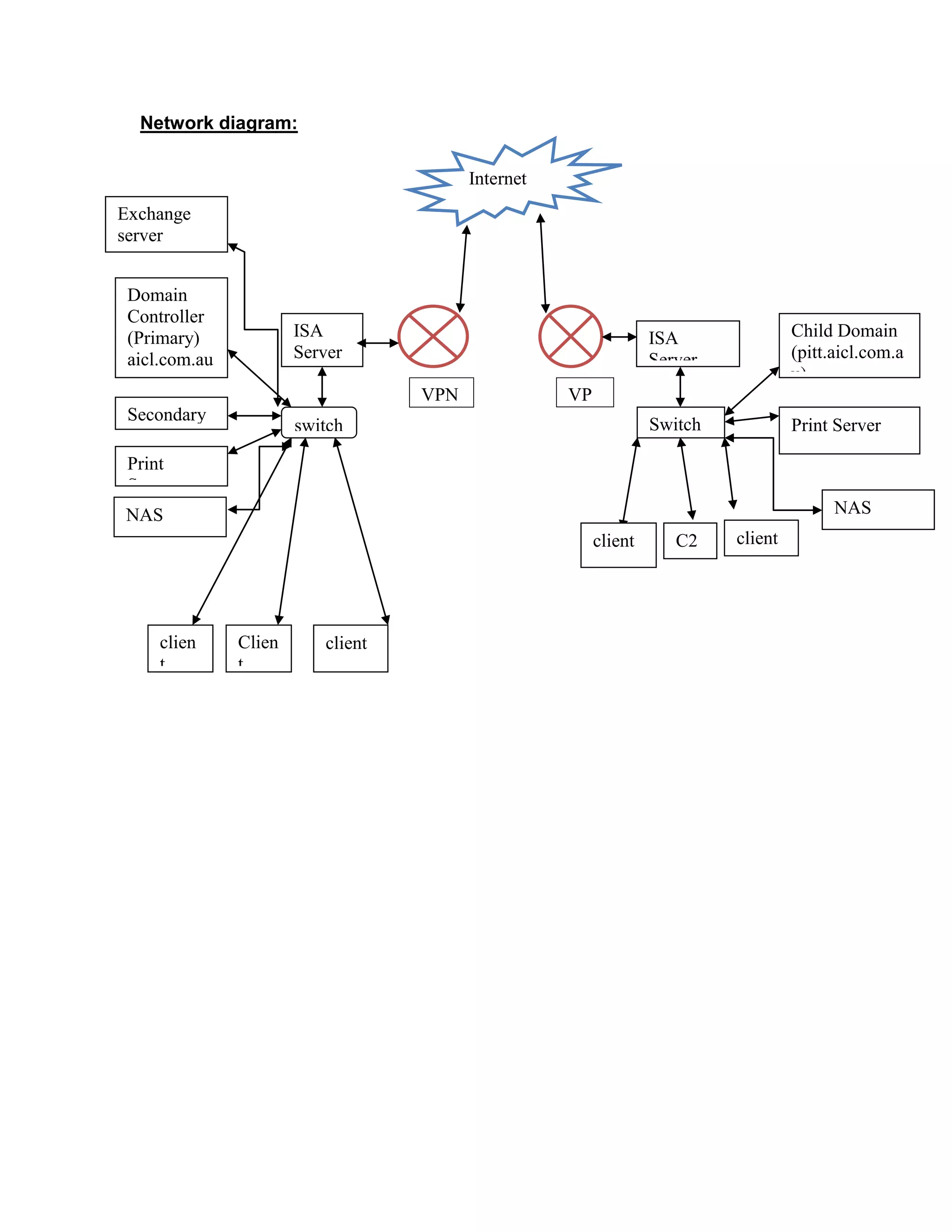
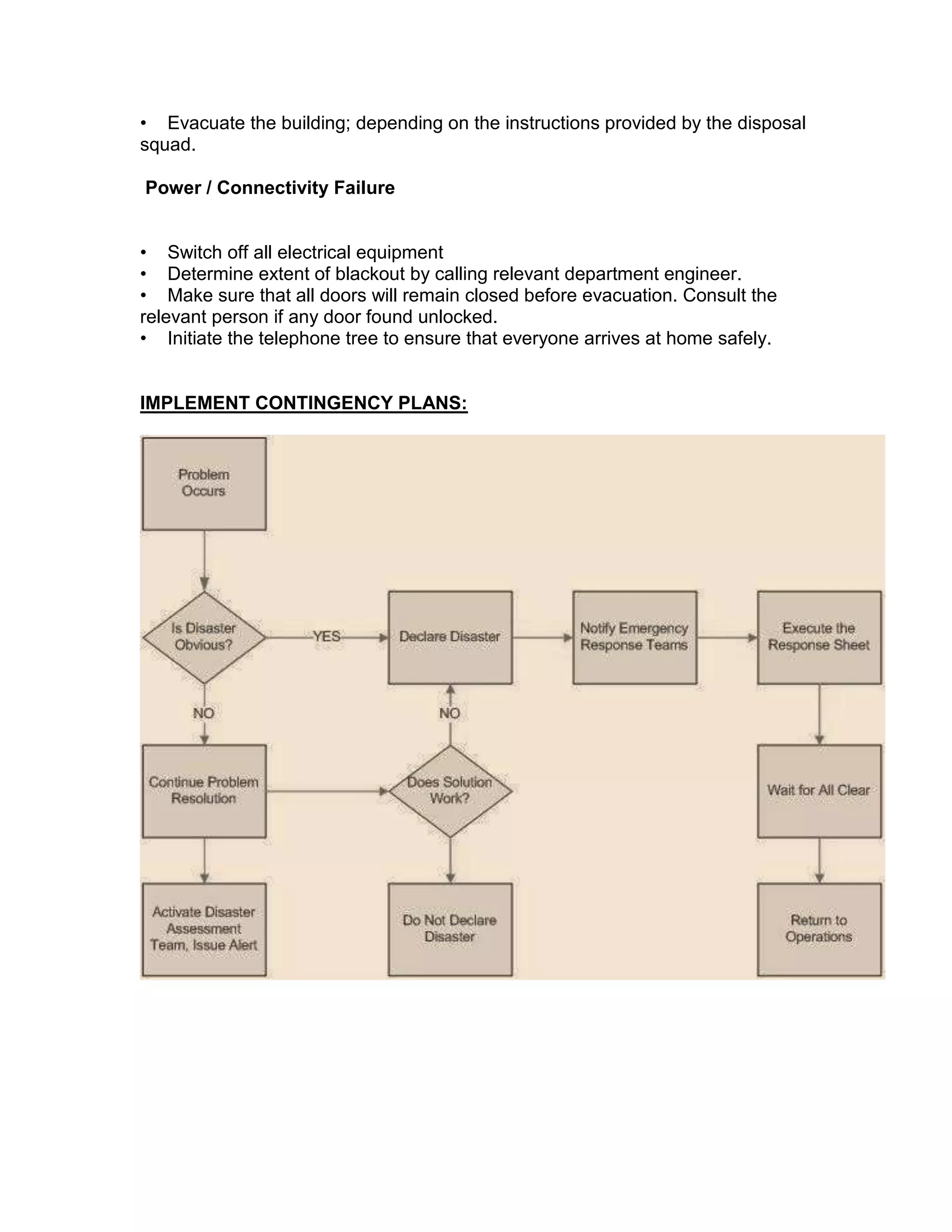
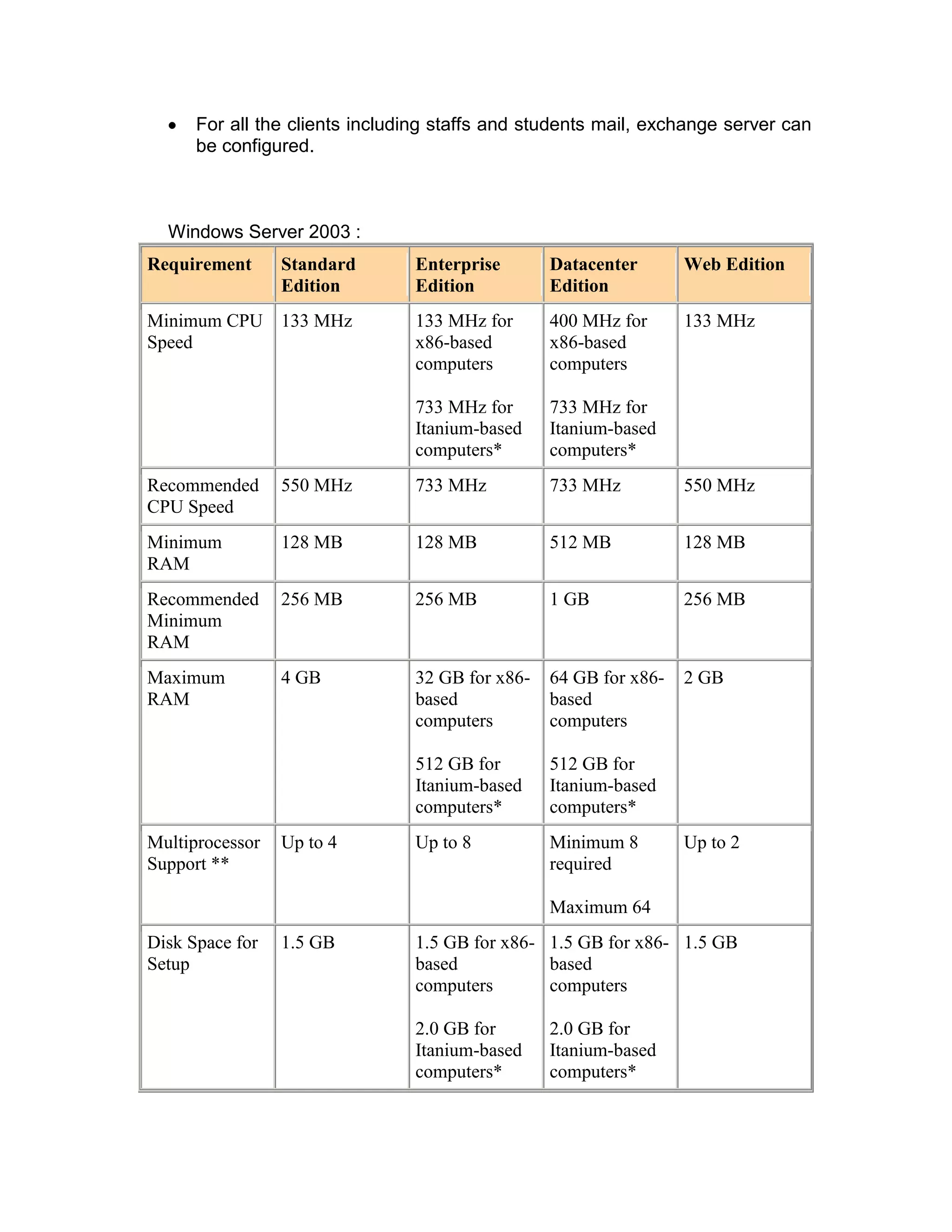
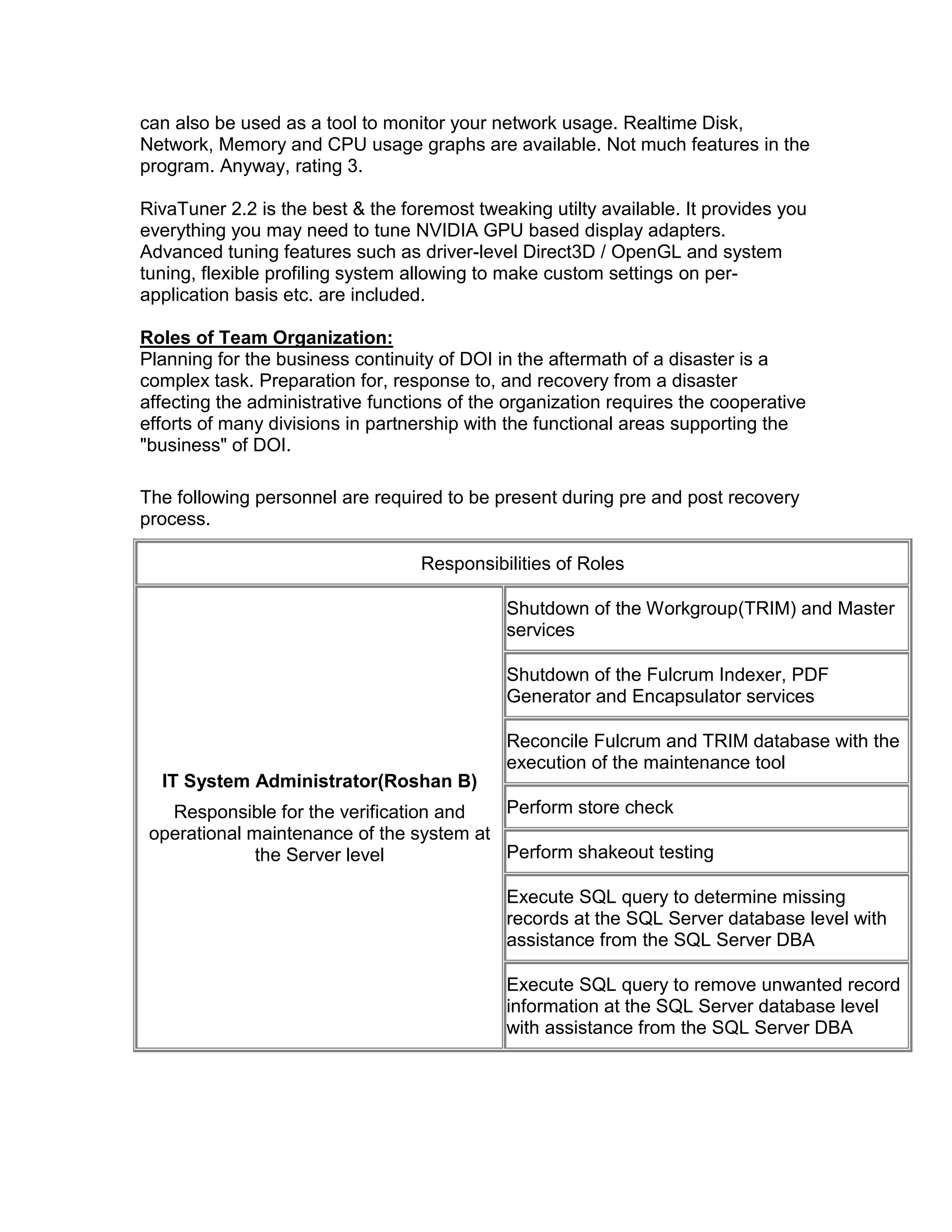
AUSTECH pharmaceutical company is planning to expand its operations by opening a new branch office. It wants to centralize its servers in the head office located in North Sydney to manage the network infrastructure across locations. The key servers implemented include a domain controller, print server, proxy server, and exchange server. The company will apply the same network design at the new branch but update devices as needed. It has identified various IT and disaster recovery risks and developed contingency plans to address threats that could disrupt operations.