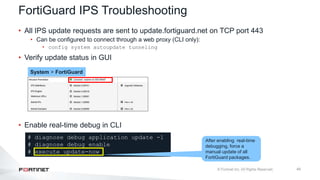
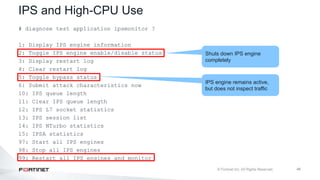
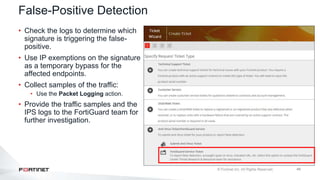
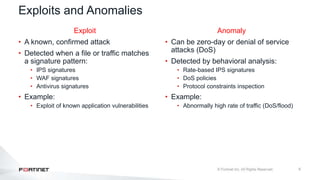
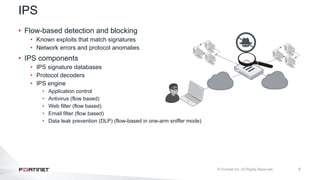
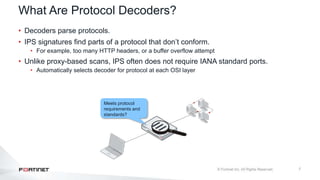
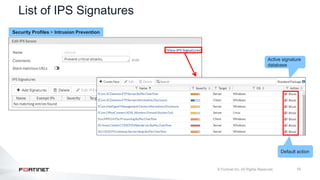
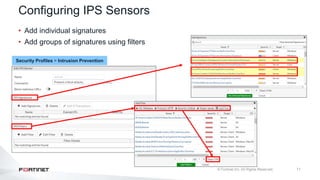
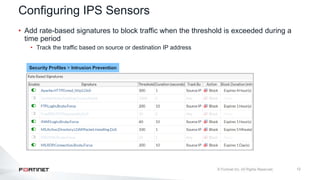
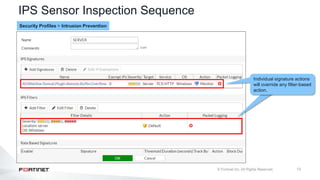
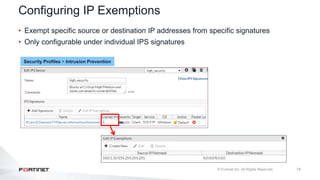
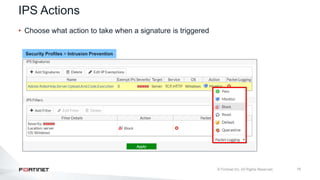
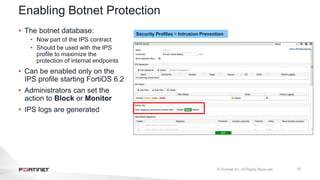
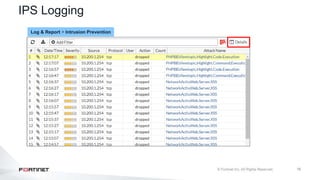
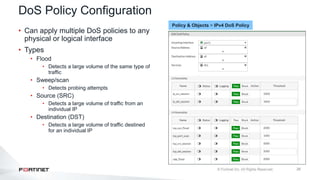
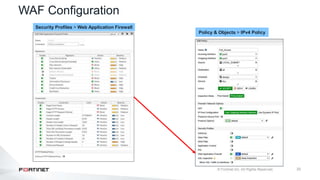
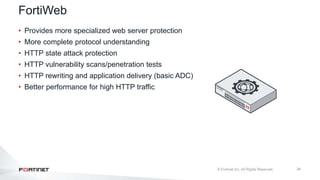
The document provides an overview of FortiOS 6.2's Intrusion Prevention System (IPS), detailing the differentiation between exploits and anomalies, the configuration of IPS sensors, and the application of intrusion prevention techniques to network traffic. It also covers Denial of Service (DoS) attacks, their characteristics, and best practices for web application firewall (WAF) configuration. Troubleshooting guidelines for IPS updates, high CPU usage, and false-positive detections are included for effective management of security measures.

















![41
Hardware Acceleration
• FortiGate models with NP4, NP6, and SoC3 can benefit from NTurbo acceleration
(np-accel-mode).
• FortiGate models that have a CP8 or CP9, support offloading of IPS pattern
matching to the content processor (cp-accel-mode).
fgt # get hardware status
Model name: FortiGate-300D
ASIC version: CP8
ASIC SRAM: 64M
CPU: Intel(R) Core(TM) i3-3220 CPU @ 3.30GHz
Number of CPUs: 4
RAM: 7996 MB
Compact Flash: 15331 MB /dev/sda
Hard disk: 114473 MB /dev/sdb
USB Flash: not available
Network Card chipset: Intel(R) Gigabit Ethernet
Network Driver (rev.0003)
Network Card chipset: FortiASIC NP6 Adapter (rev.)
# config ips global
# set np-accel-mode [ basic | none ]
# set cp-accel-mode [ basic | advanced | none ]
# end
np-accel-mode
o basic: offloads IPS processing to NP
cp-accel-mode
o basic: offloads basic IPS pattern matching to CP8 or
CP9
o advanced: offloads more types of IPS pattern matching
• Only available in units with two or more CP8s or one or
more CP9s](https://image.slidesharecdn.com/fortigatesec11intrusionpreventionsystem-240529191839-126414ff/85/FortiGate_Sec_11_Intrusion_Prevention_S-pptx-41-320.jpg)