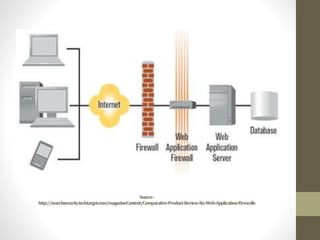
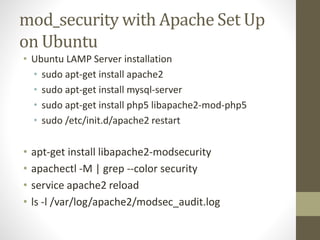
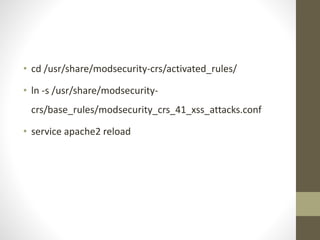
Shruthi Kamath gave an introduction to Mod Security, an open-source web application firewall. She discussed what a WAF is and how it protects web servers from attacks. Mod Security was originally an Apache module but can now be used on other platforms like IIS and Nginx. It uses rule-based filtering to monitor and log HTTP traffic. Kamath provided examples of Mod Security rules and demonstrated how to install, configure, and set up rules for Mod Security on an Apache server.