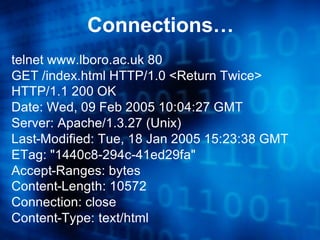
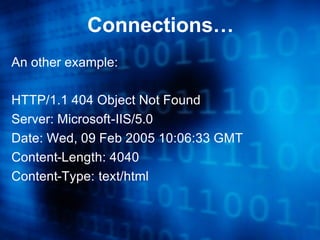
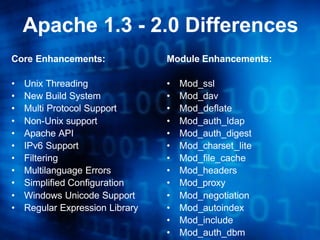
The document discusses securing the Apache web server. It provides an overview of Apache's history and versions. It outlines common system attacks like directory traversals and overflows. It then discusses ways to secure Apache such as running it with limited privileges, chrooting it, trimming the configuration, and using security modules like Mod_Security. The document emphasizes securely configuring the operating system, auditing settings, patching, and monitoring logs.