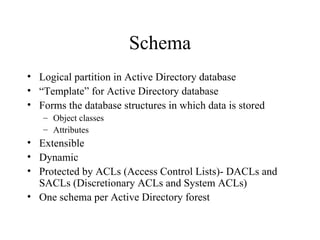
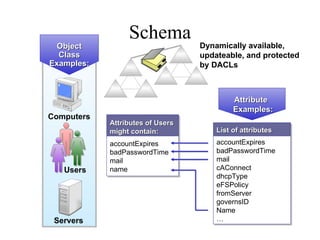
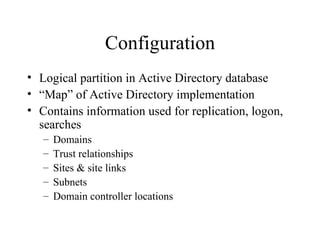
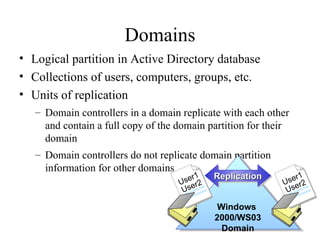
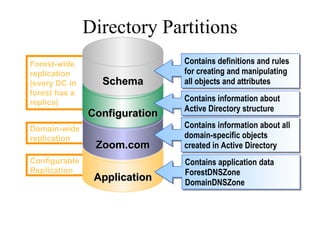
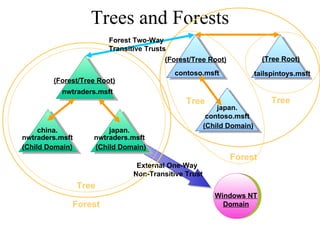
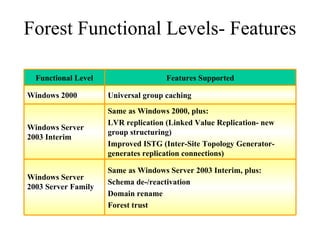
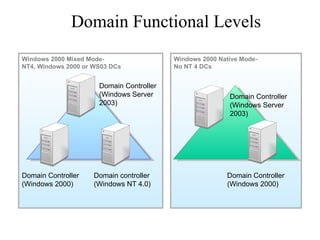
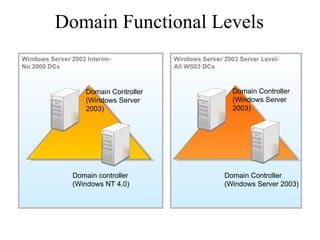
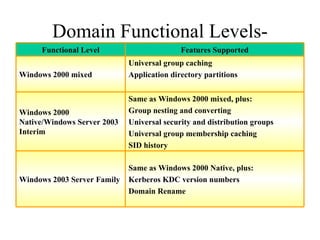
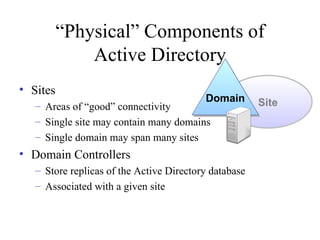
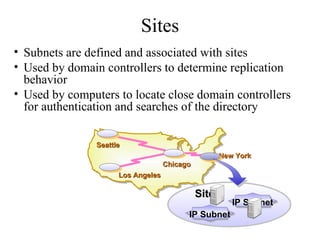
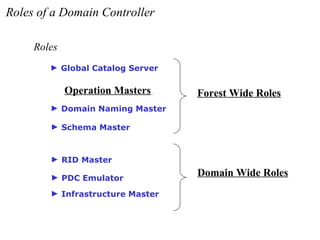
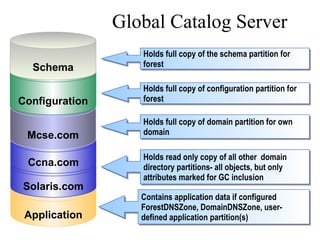
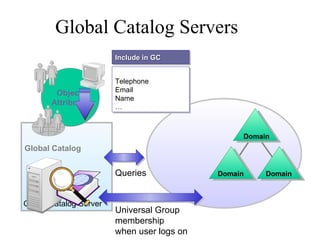
The document discusses the key components and structures of Active Directory, including partitions, domains, sites, domain controllers, functional levels, and roles. It describes the schema, configuration, and domain partitions that make up the Active Directory database. It also explains trust relationships, trees, and forests in an Active Directory implementation.