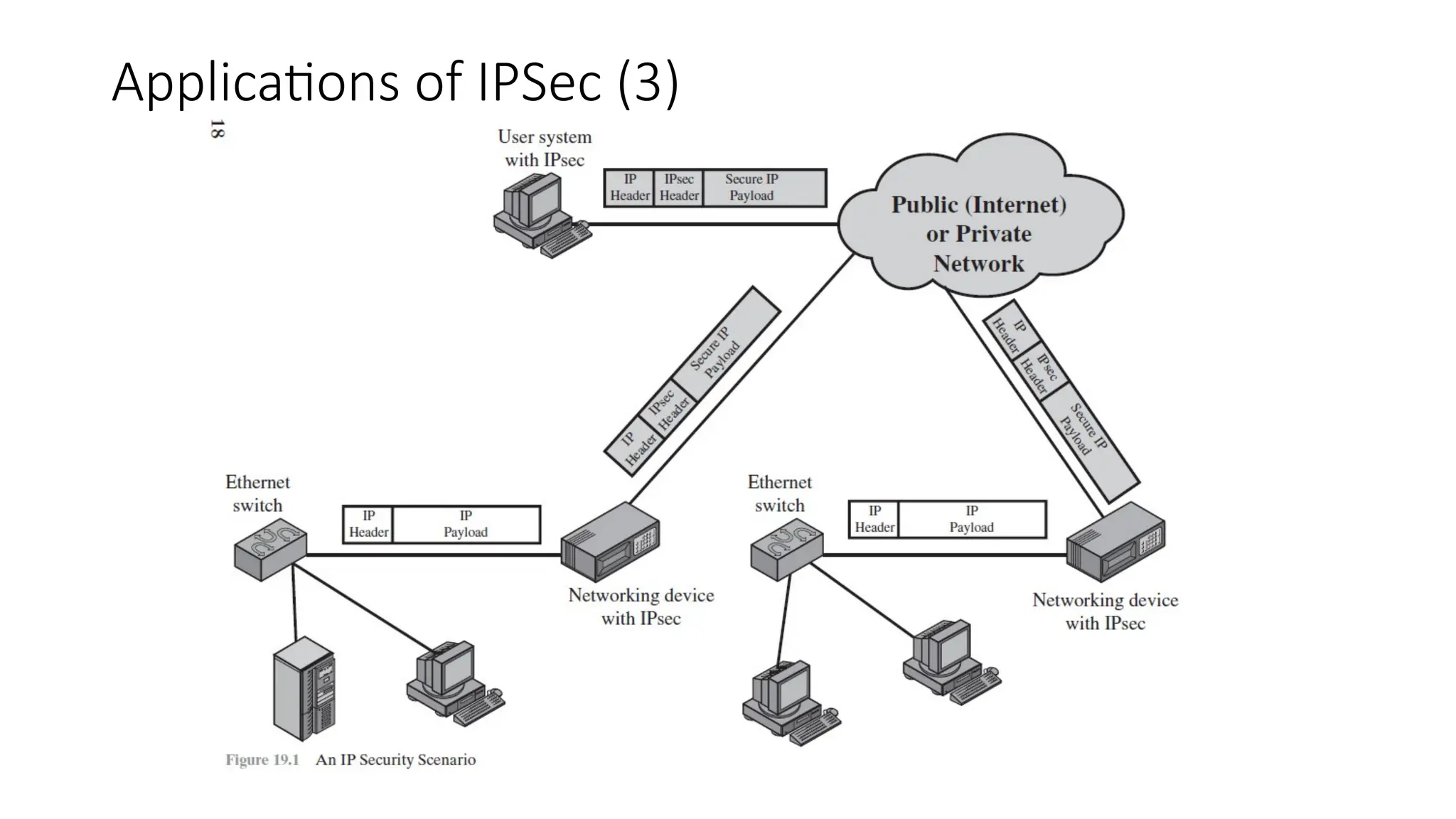
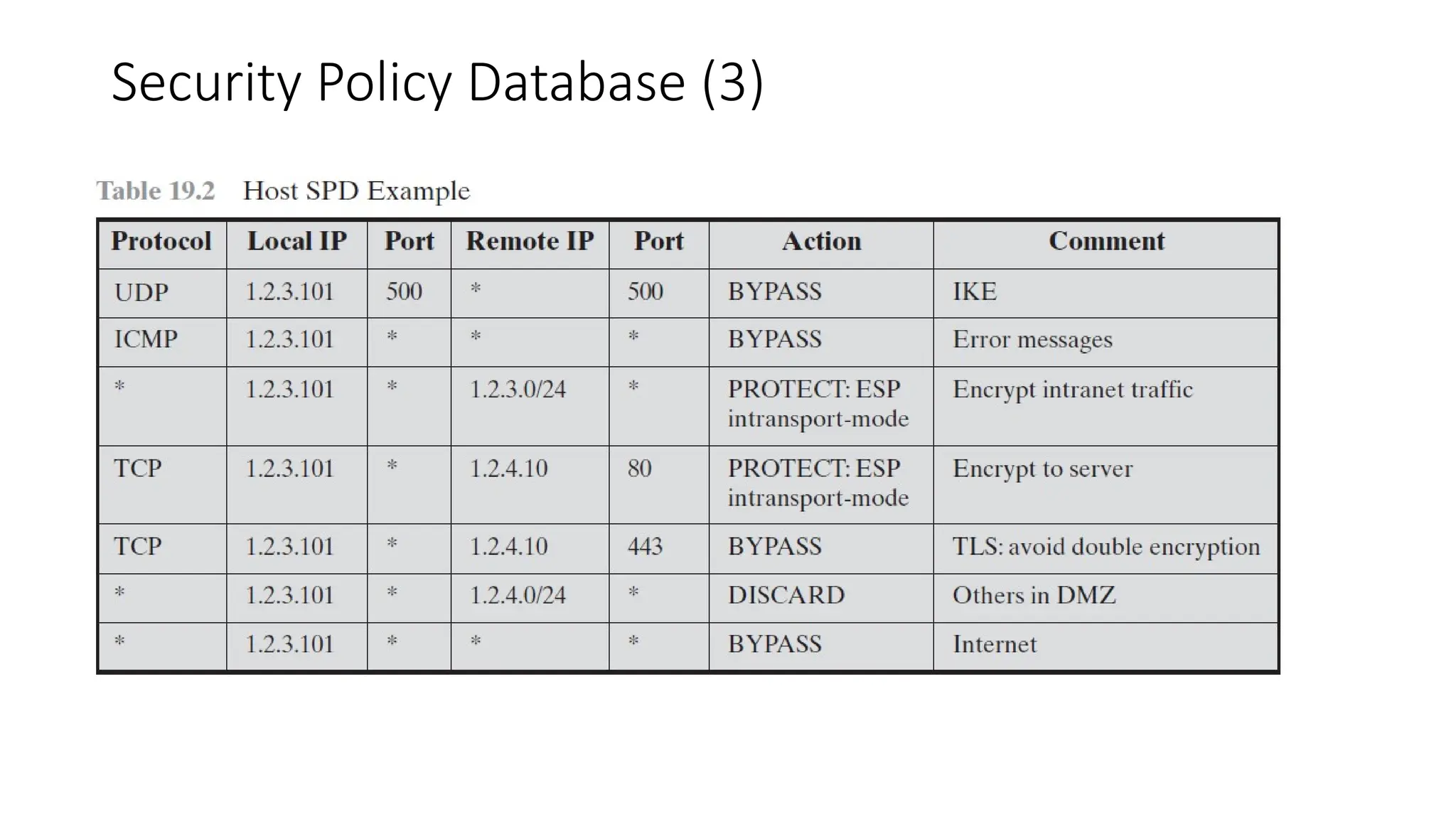
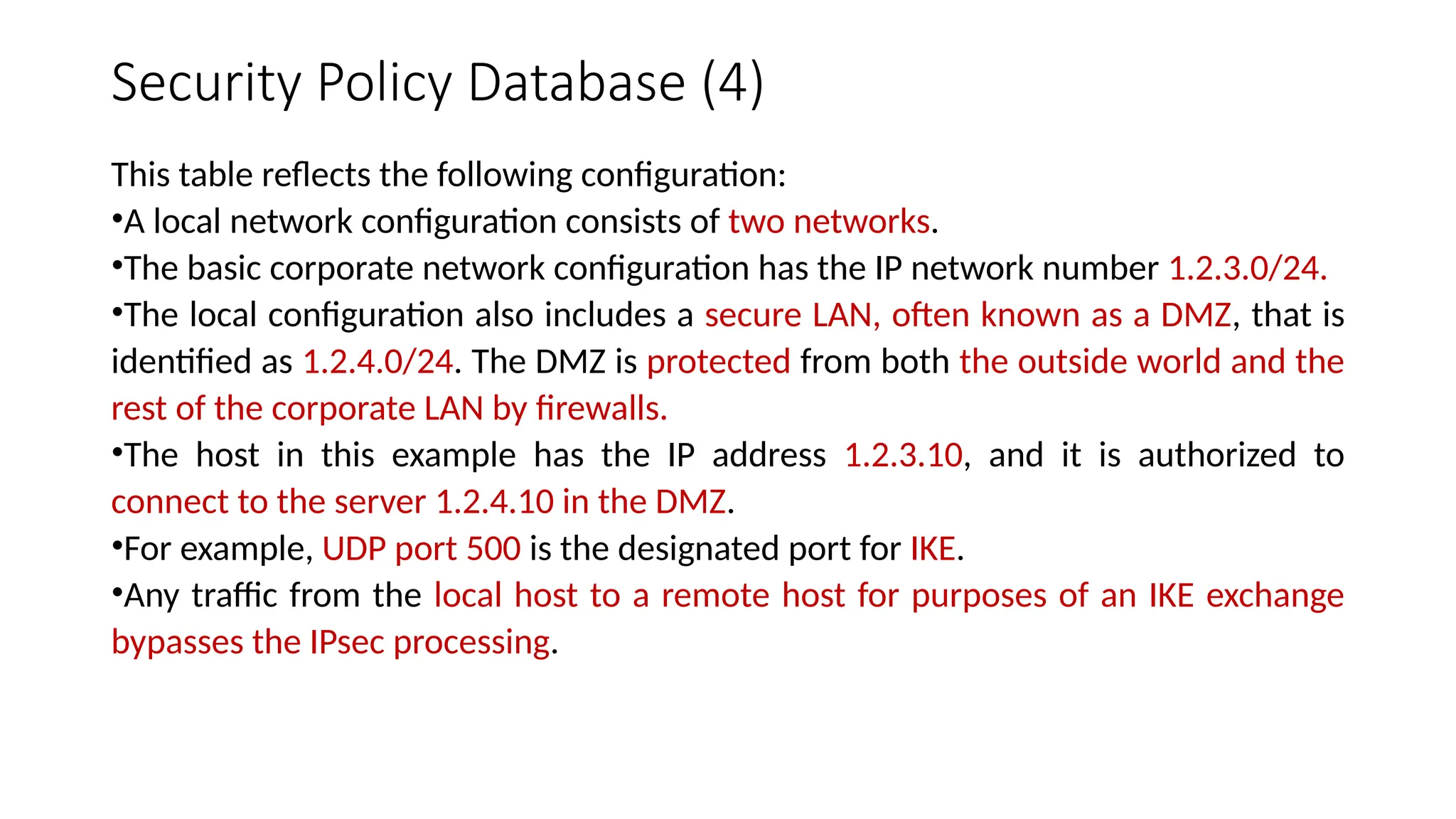
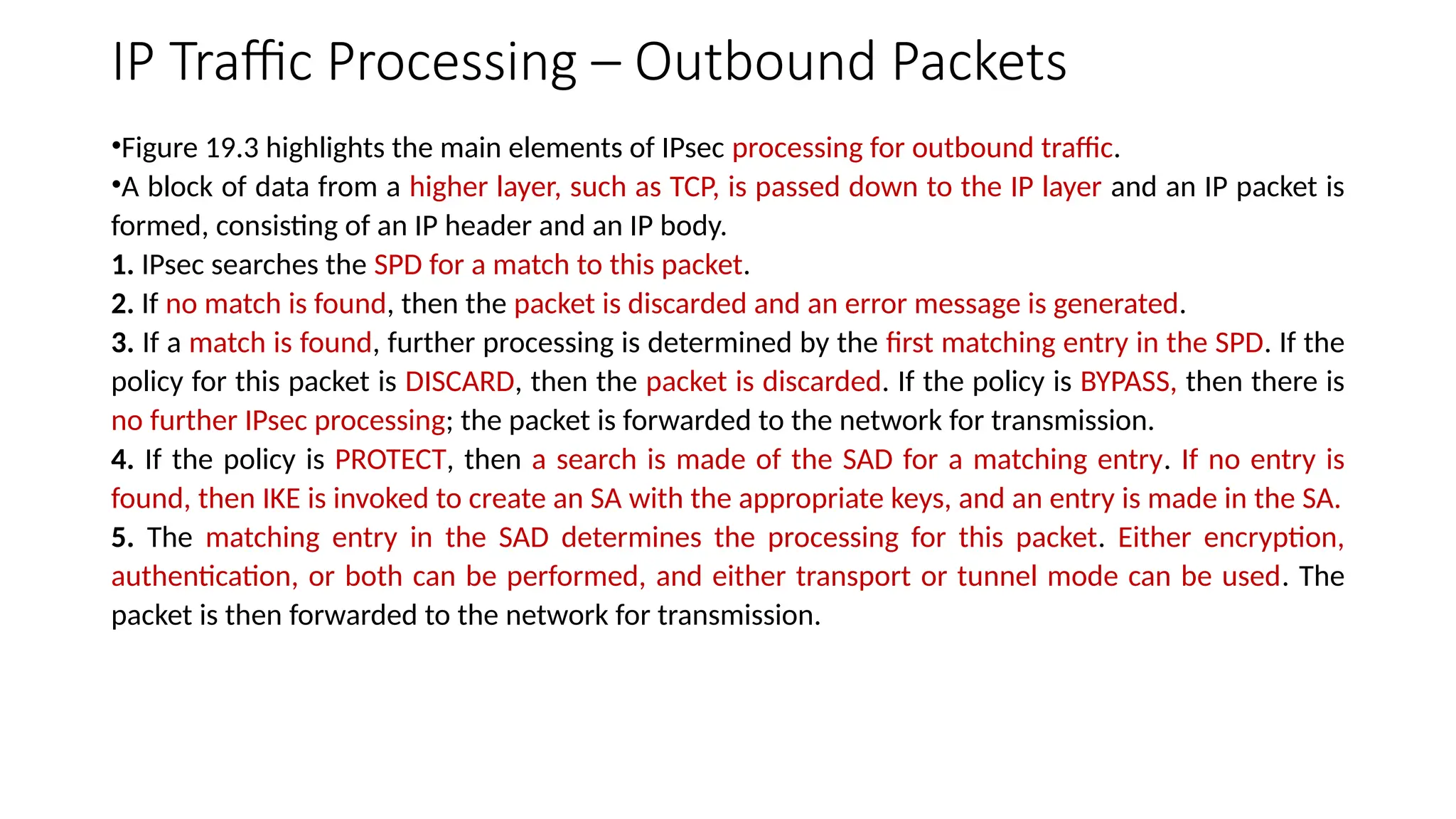
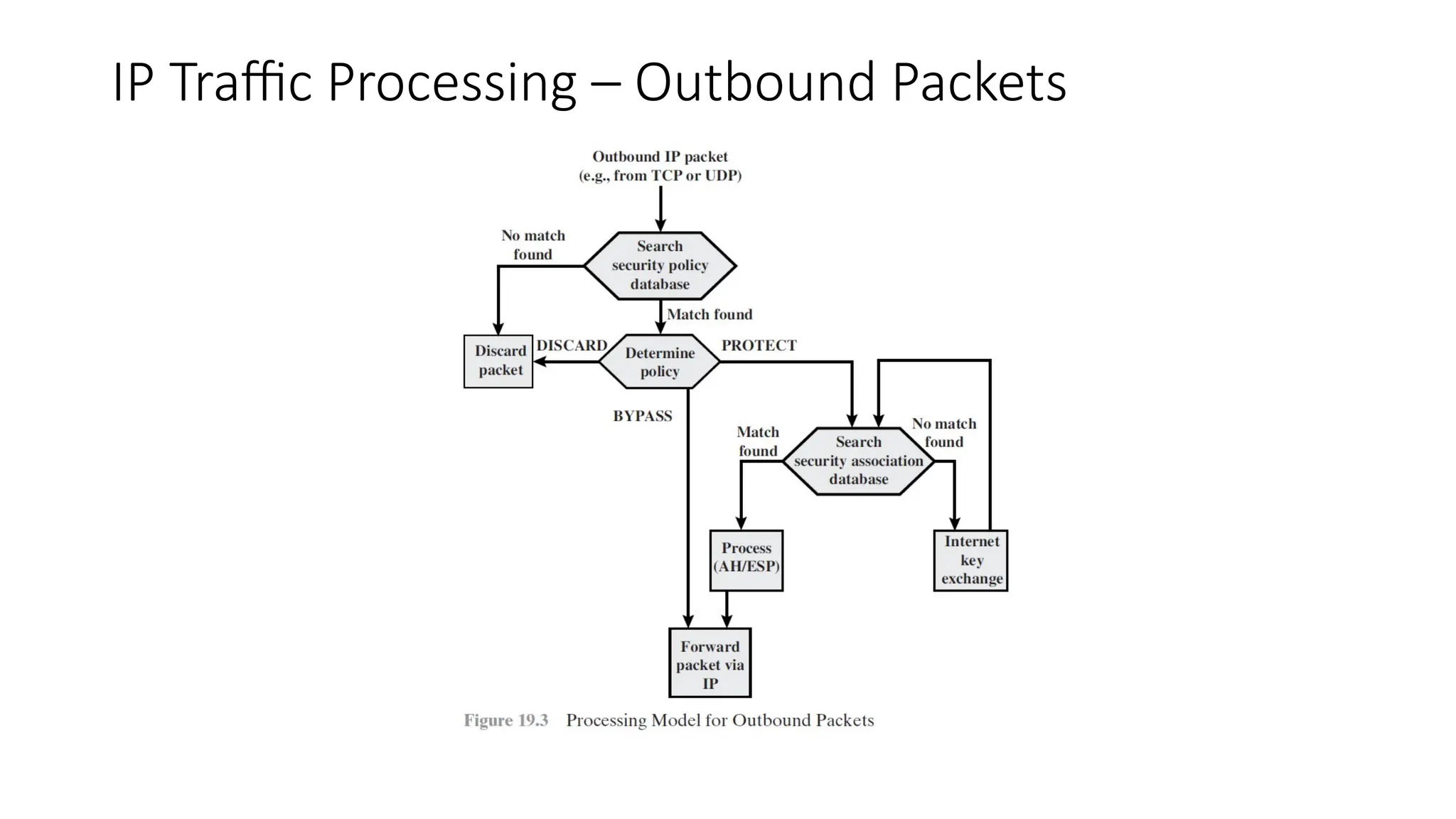
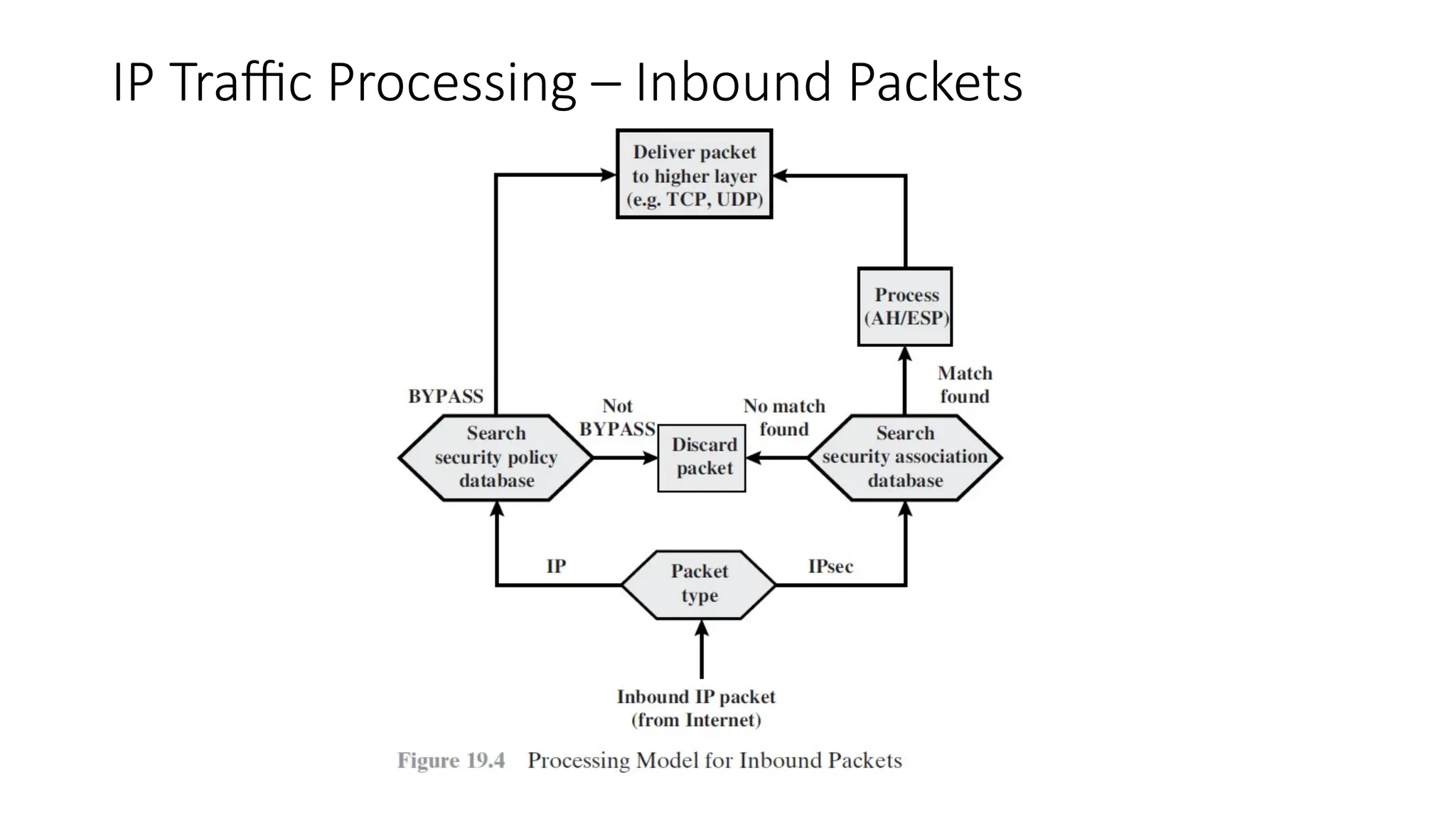
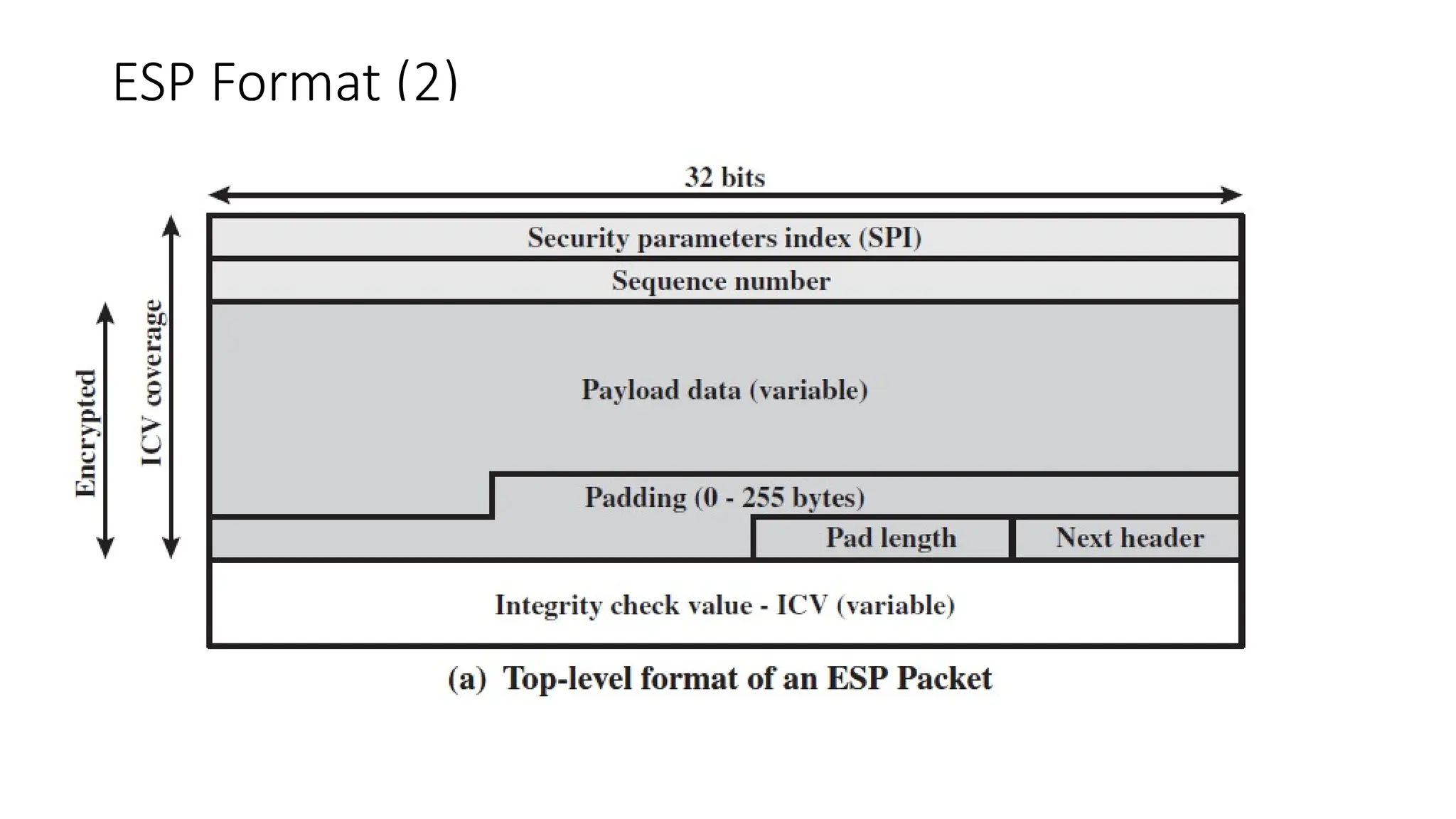
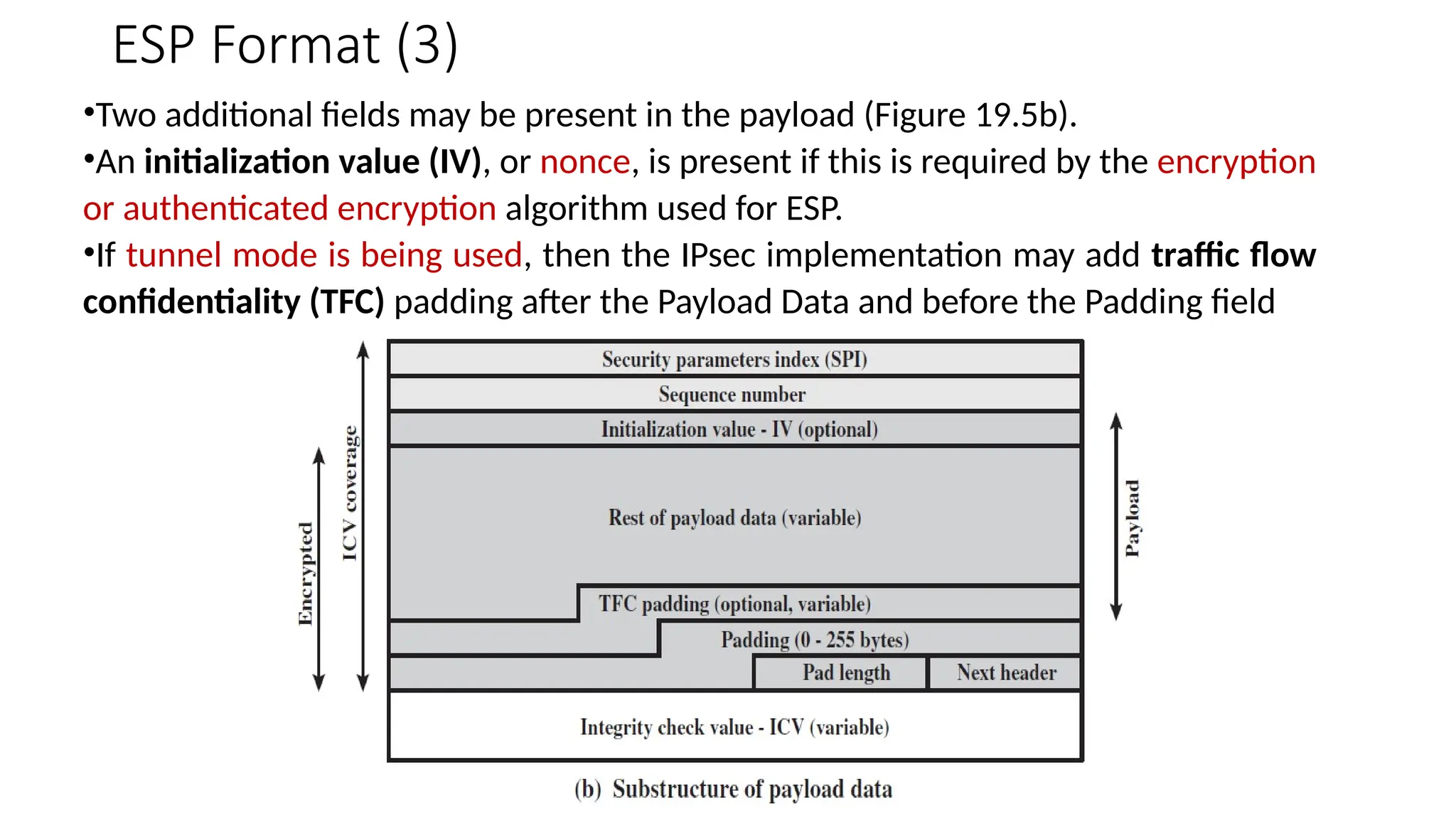
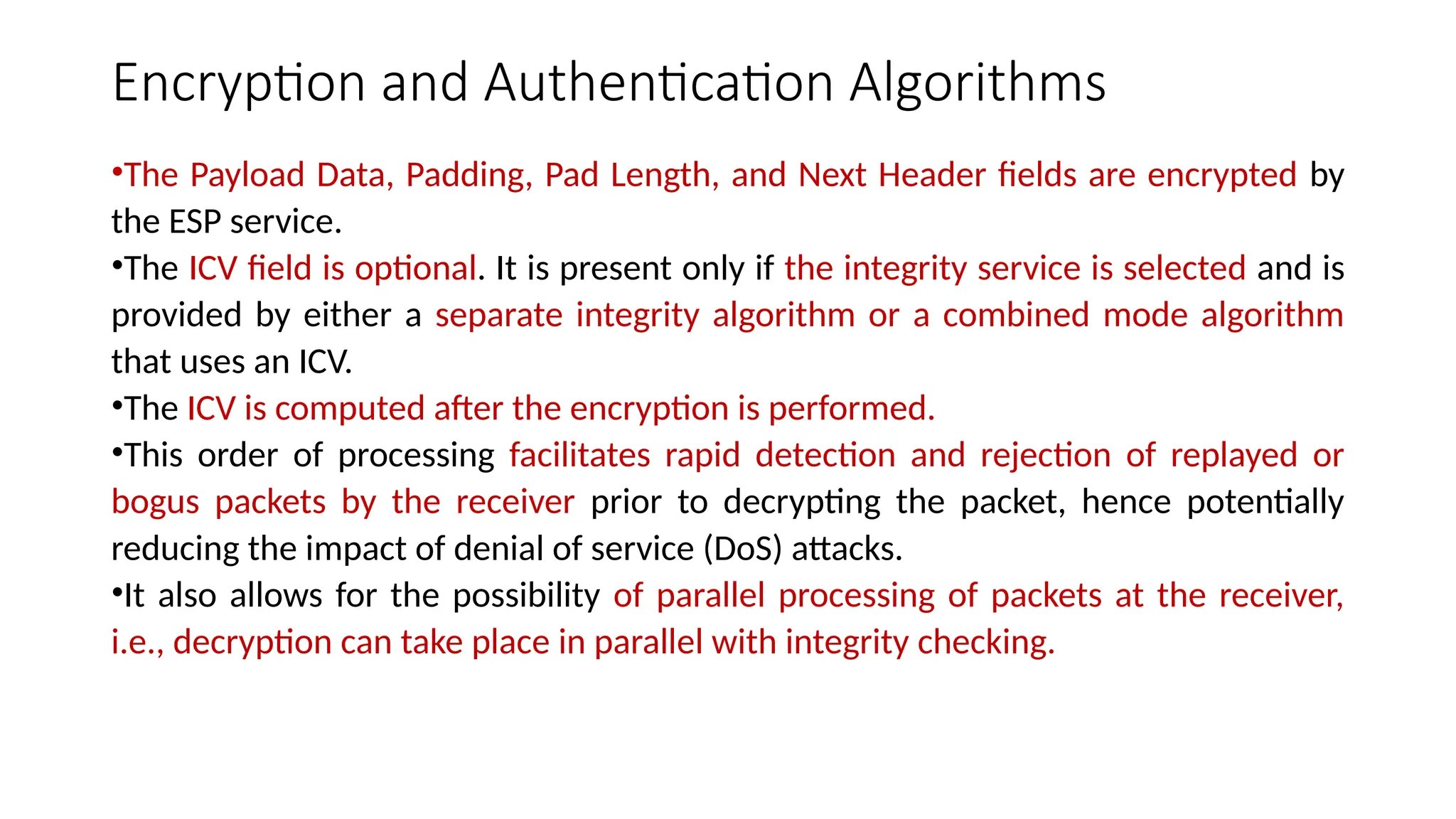
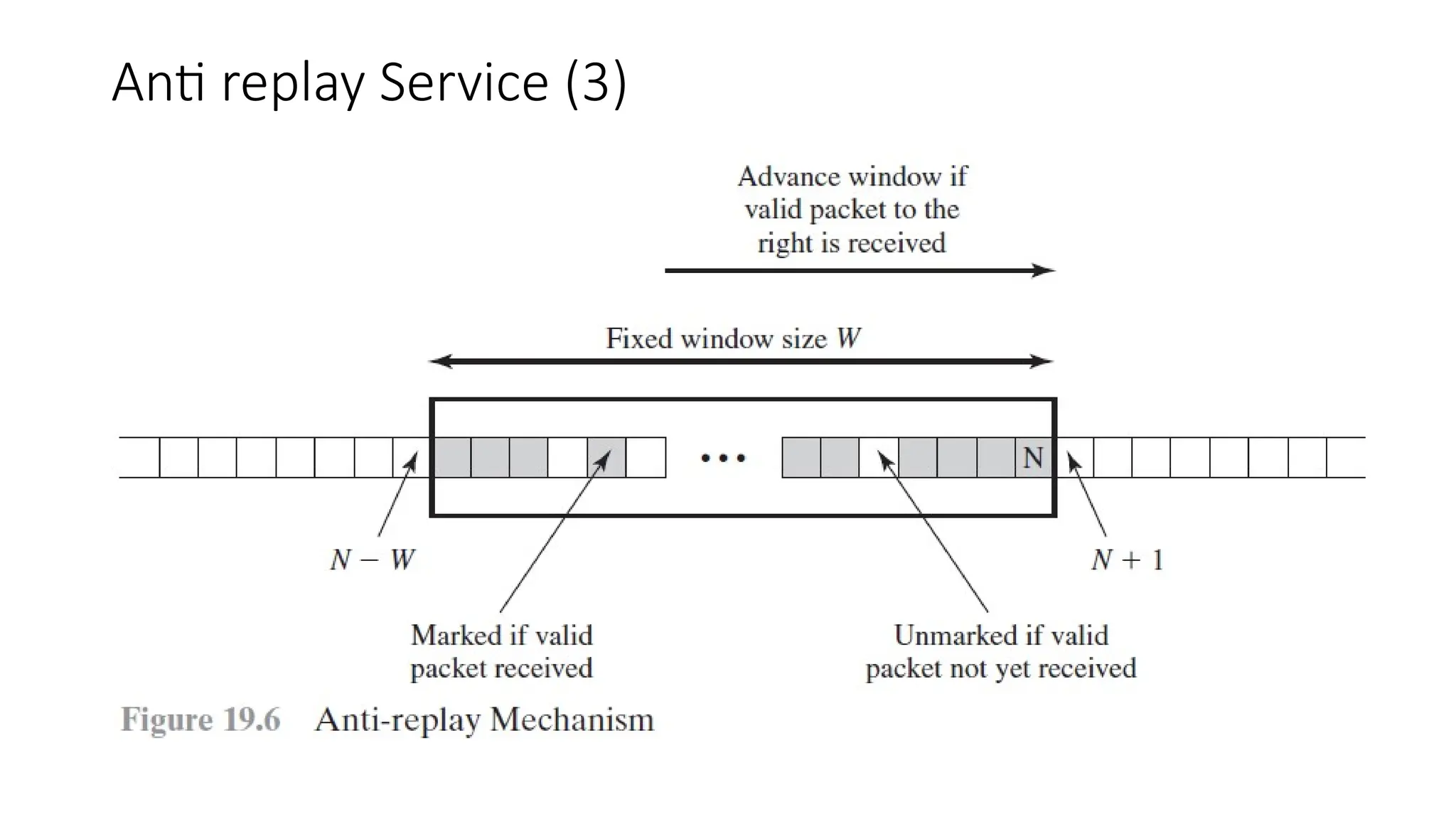
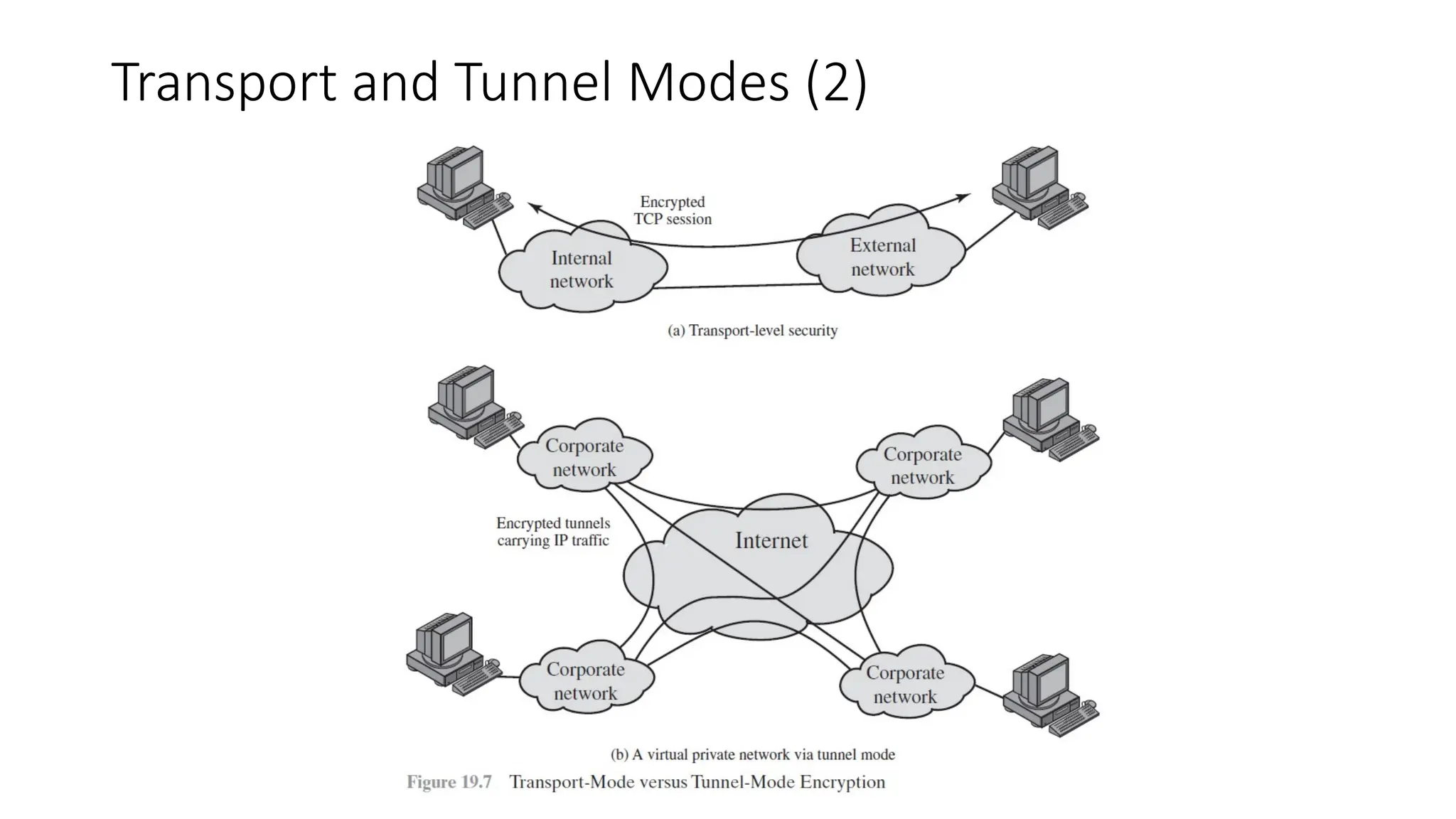
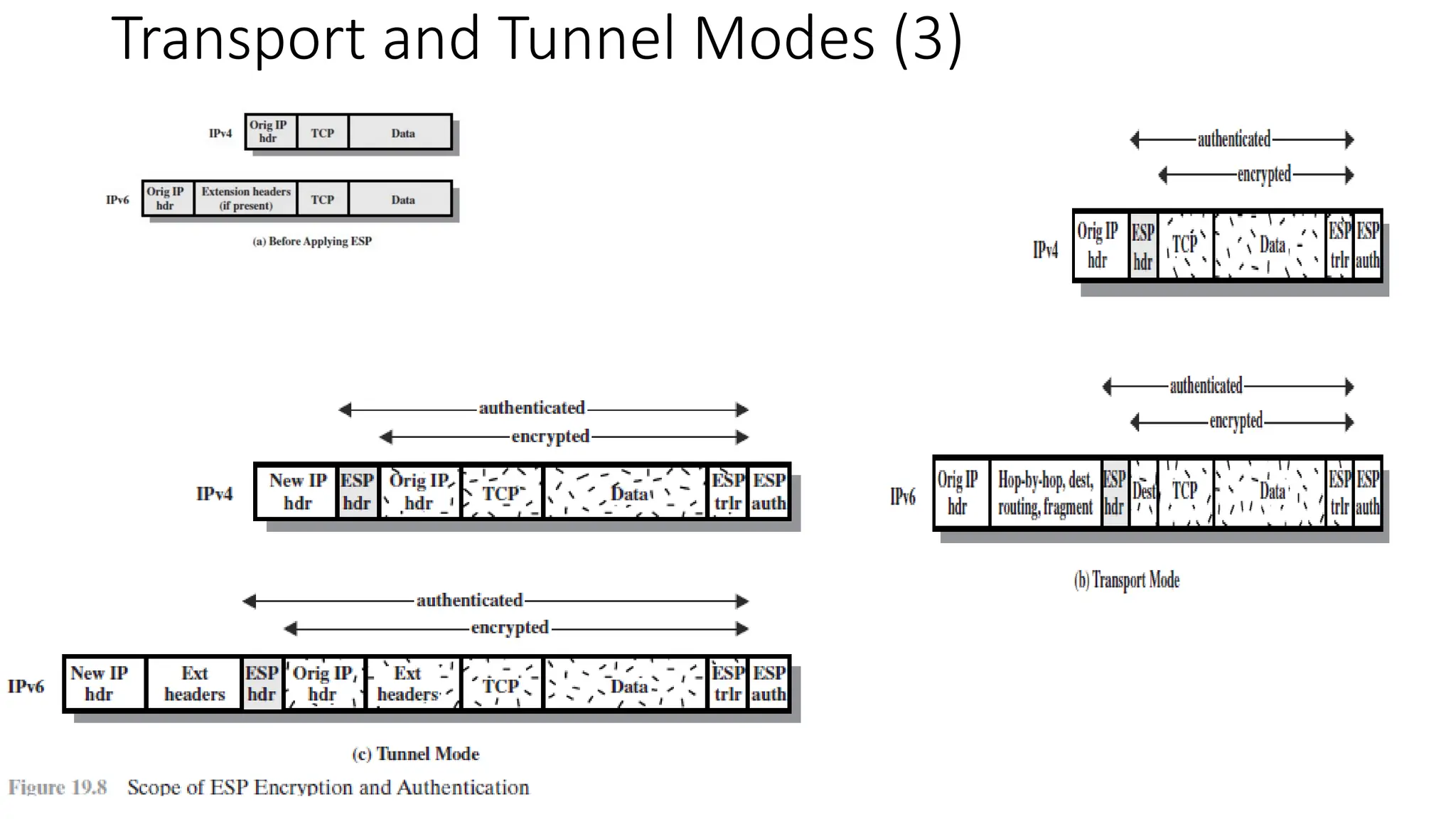
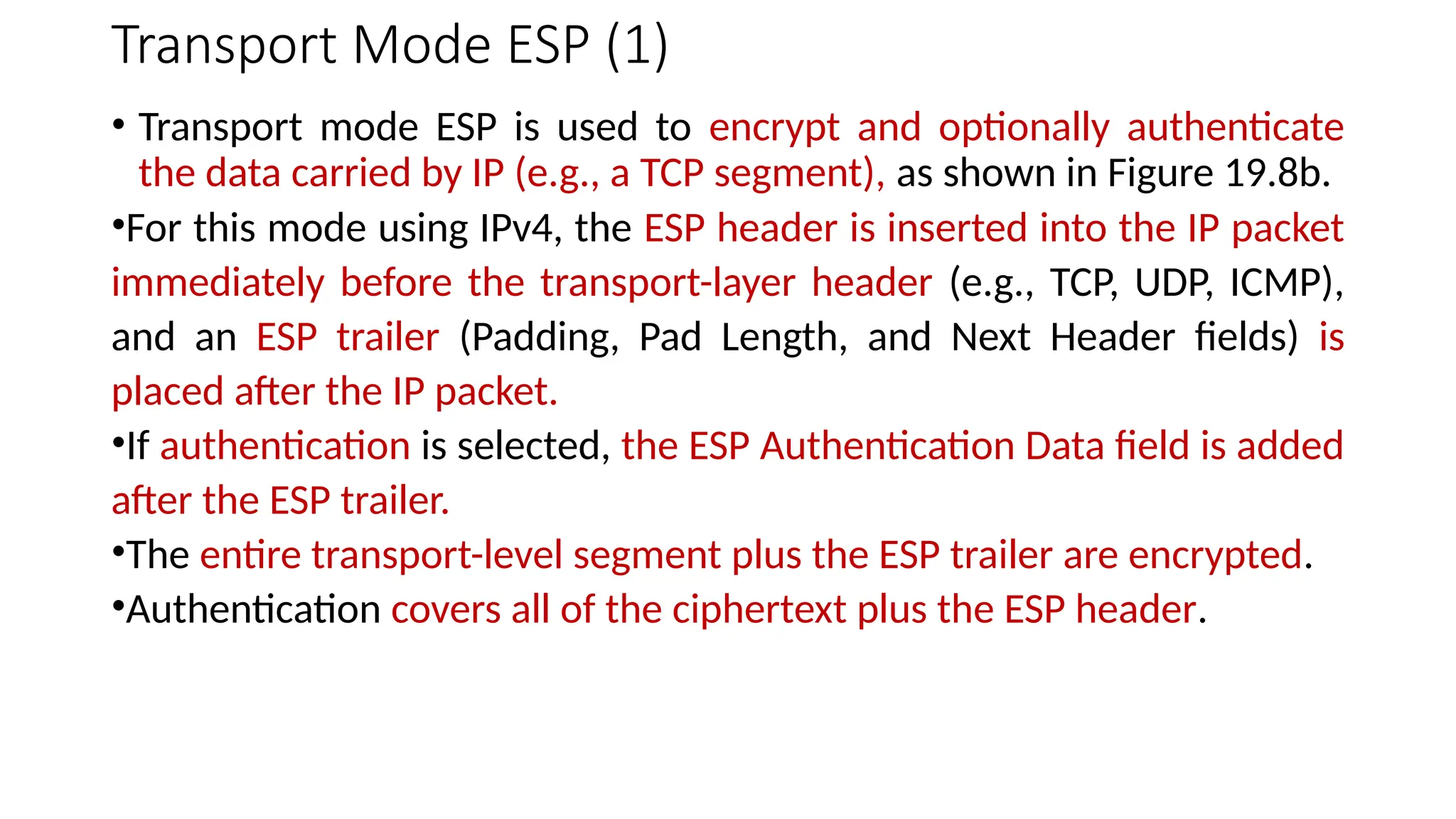
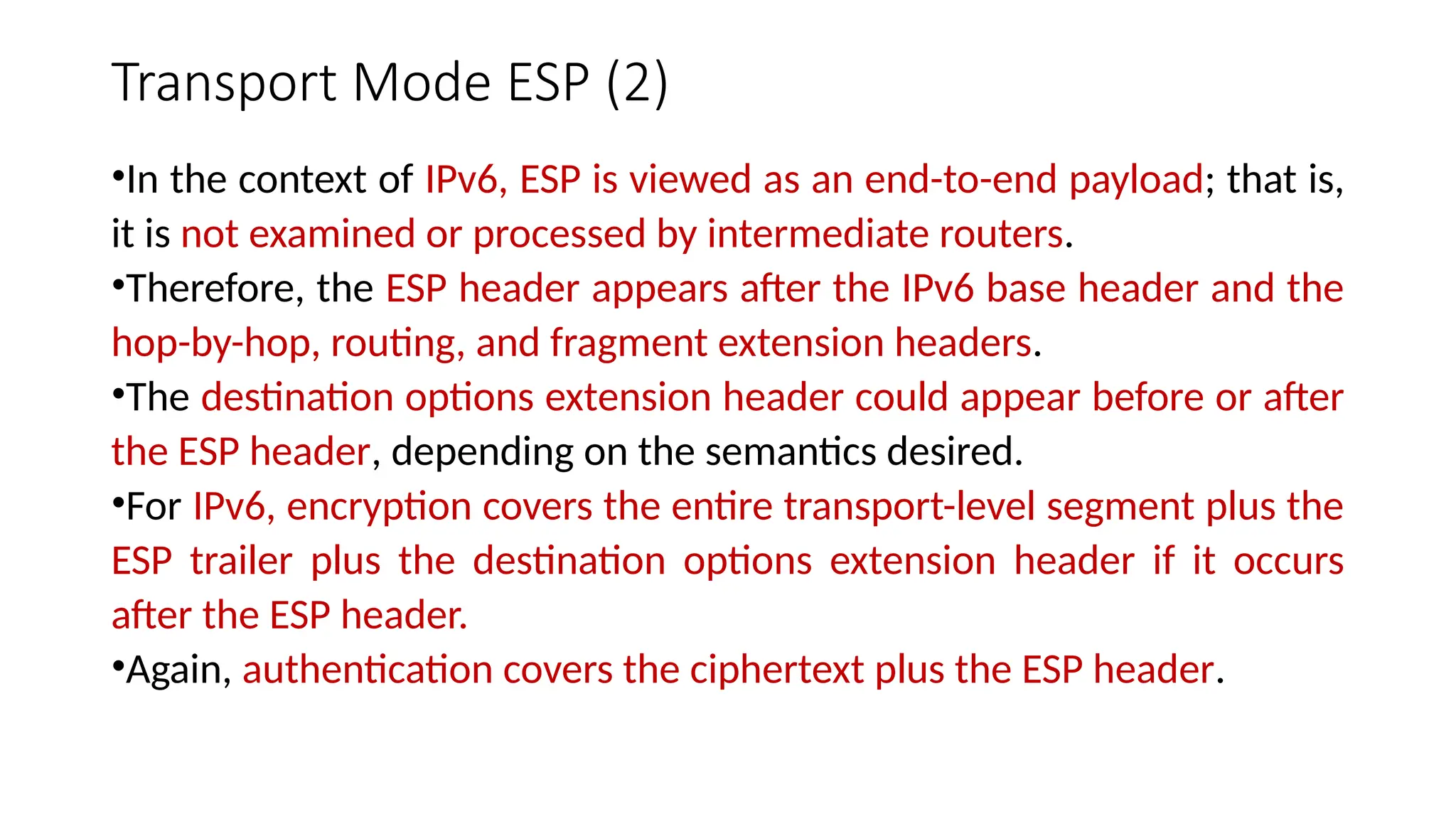
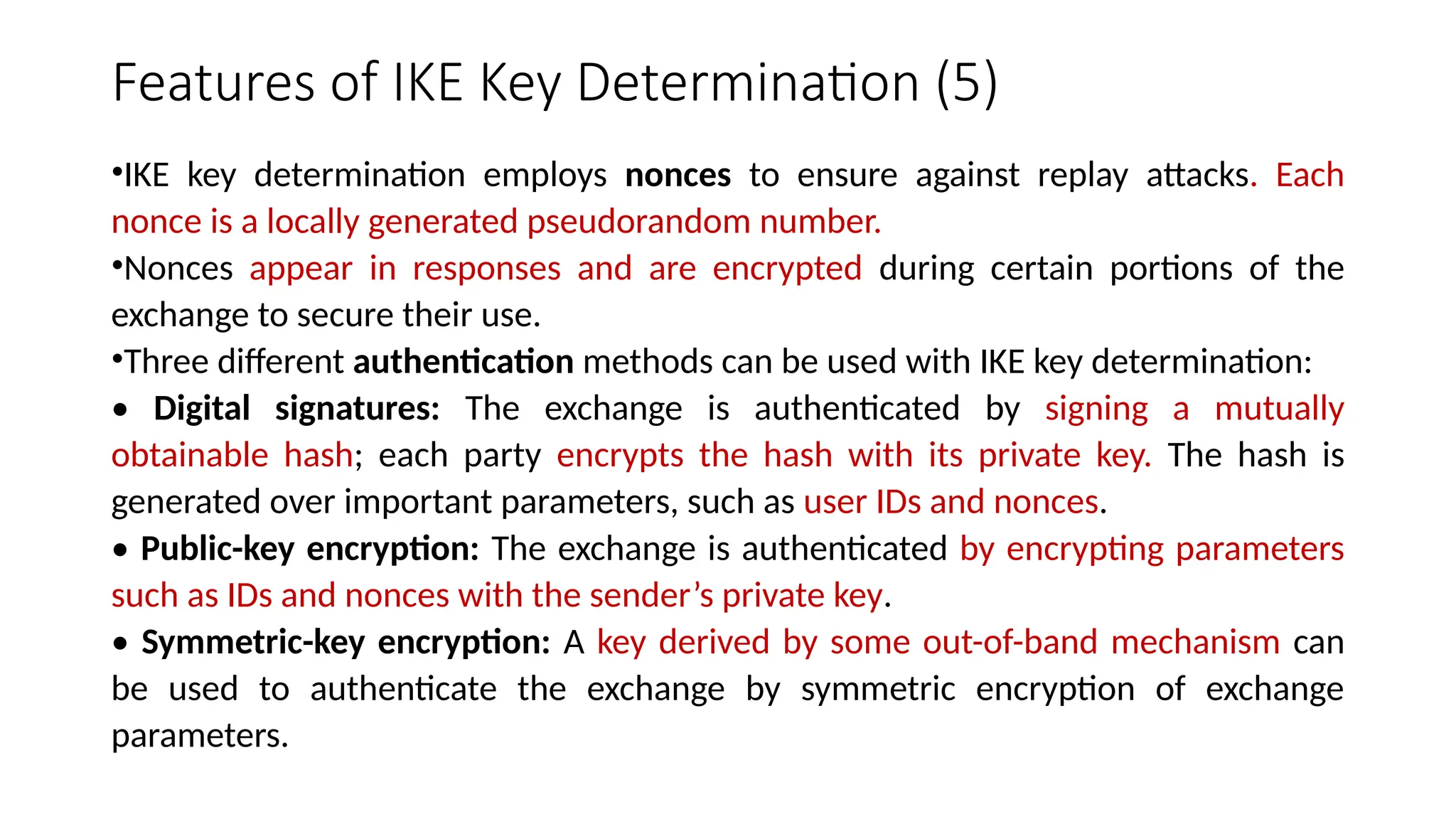
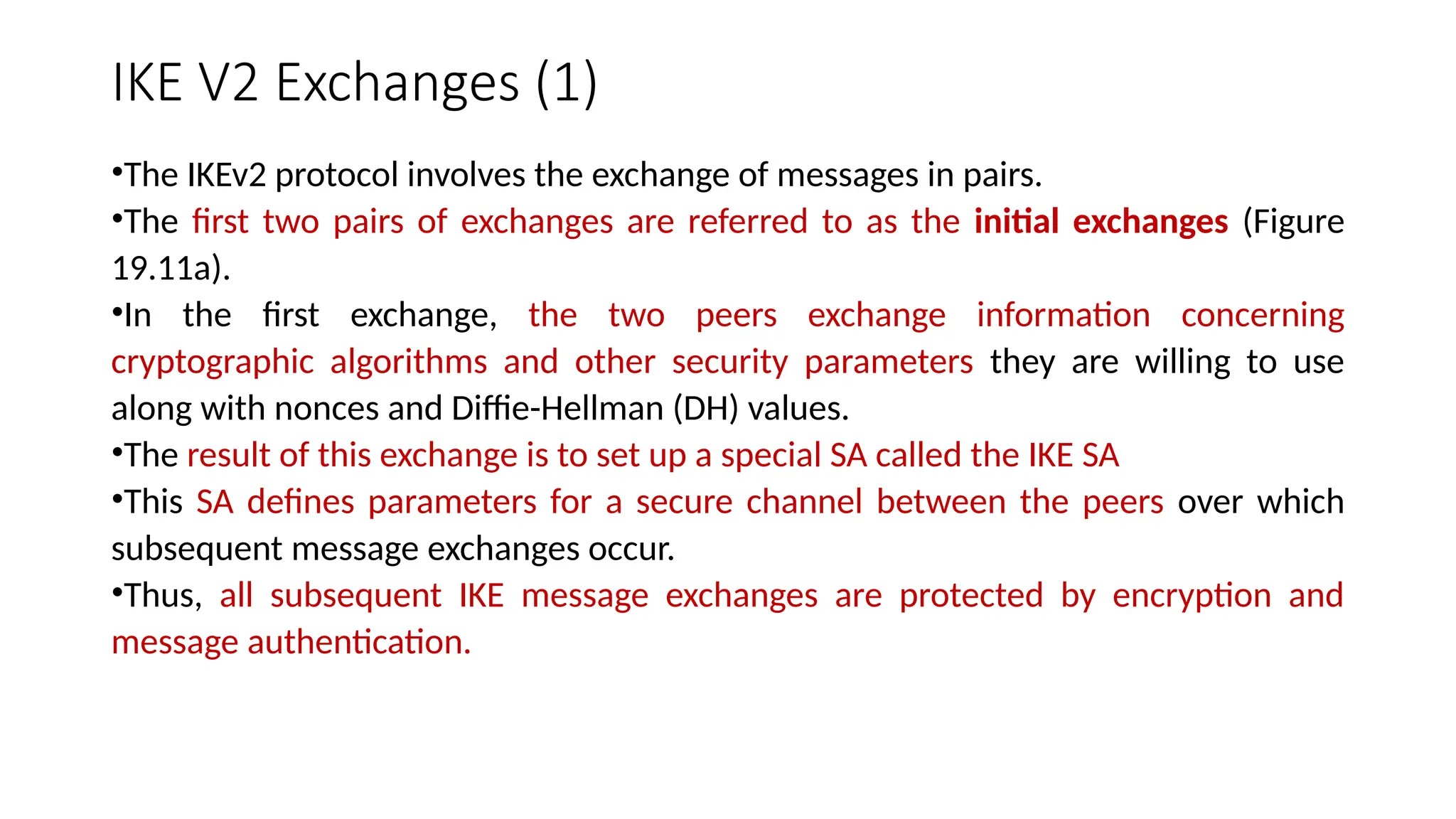
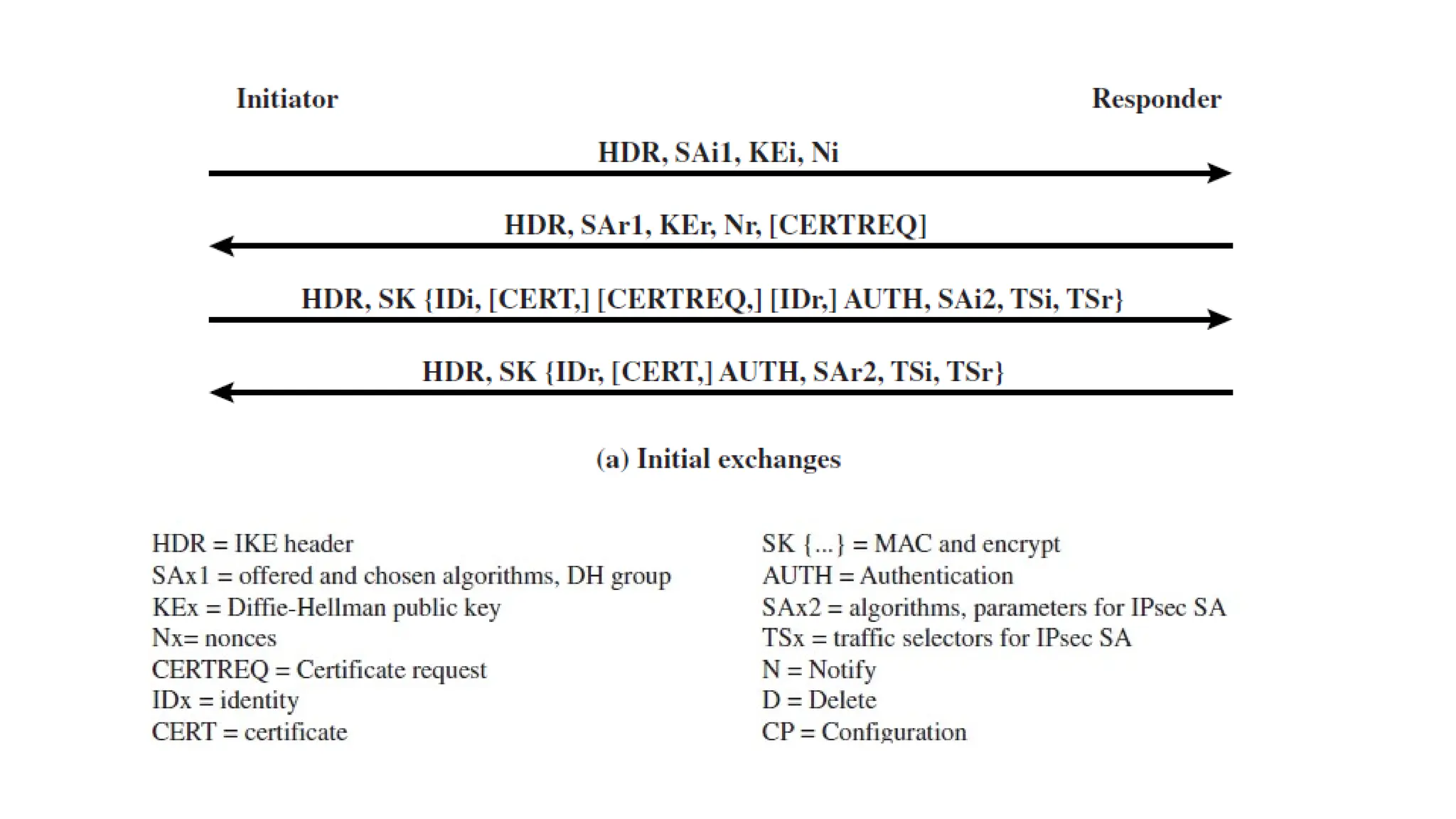
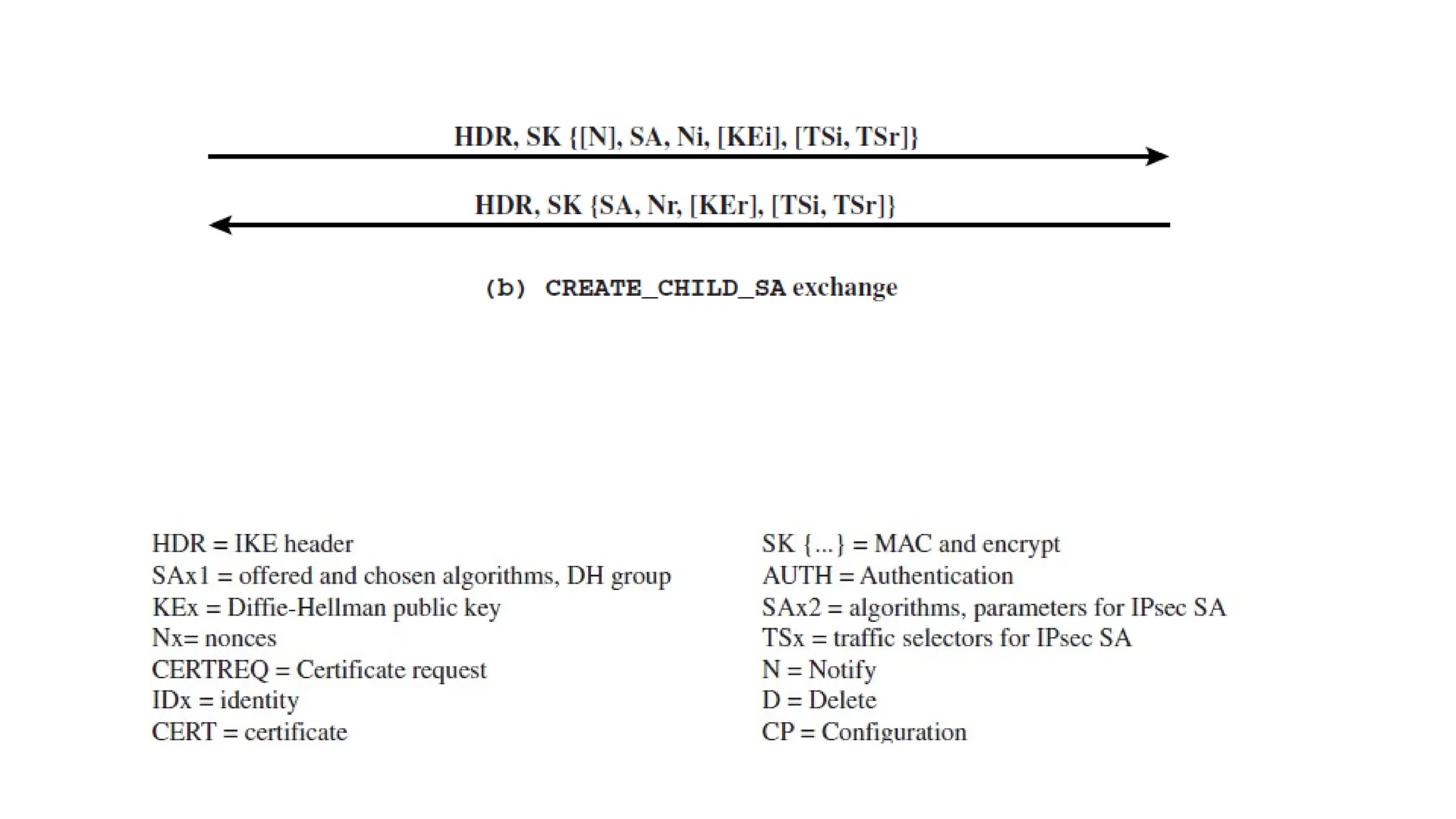
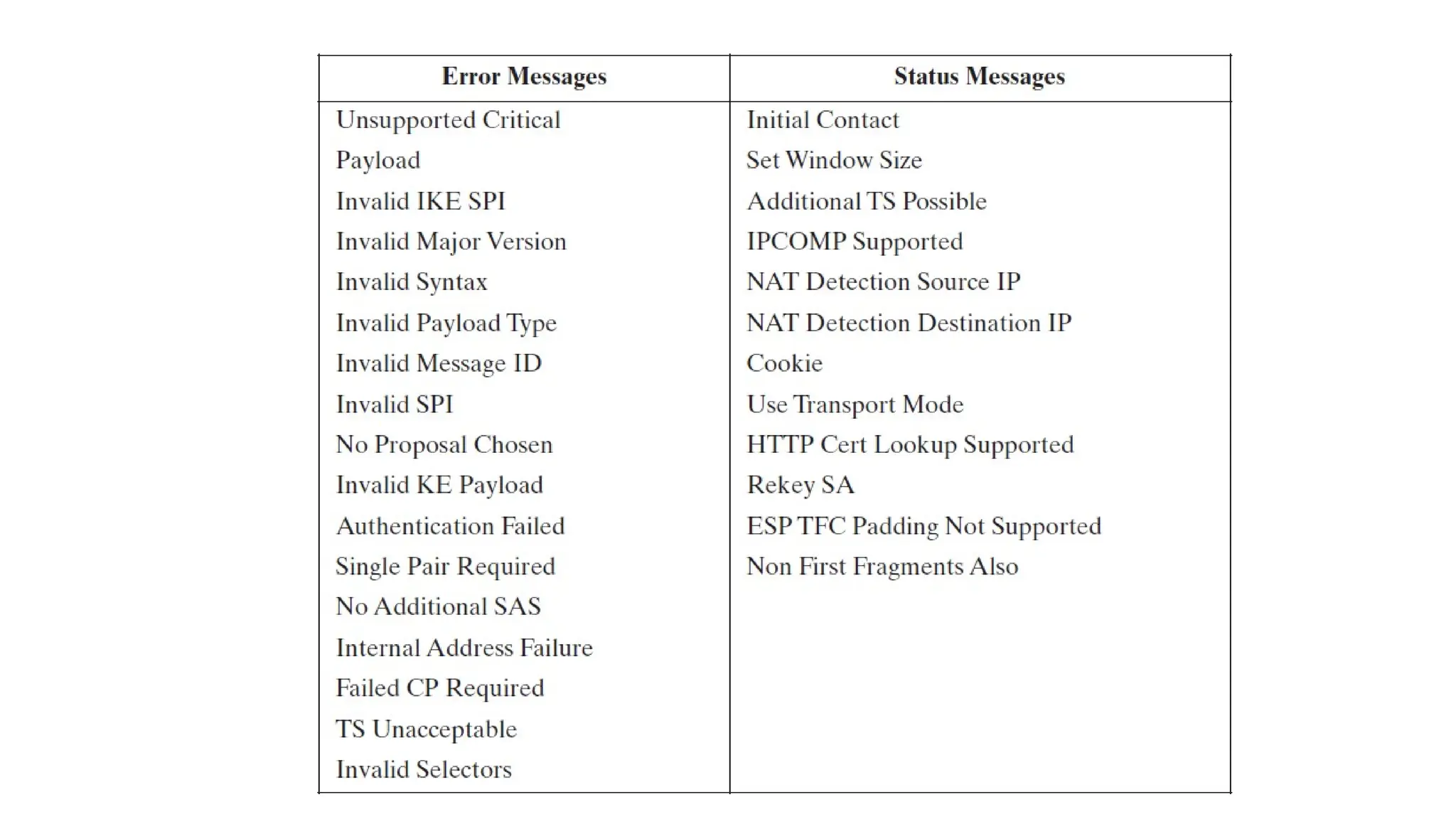
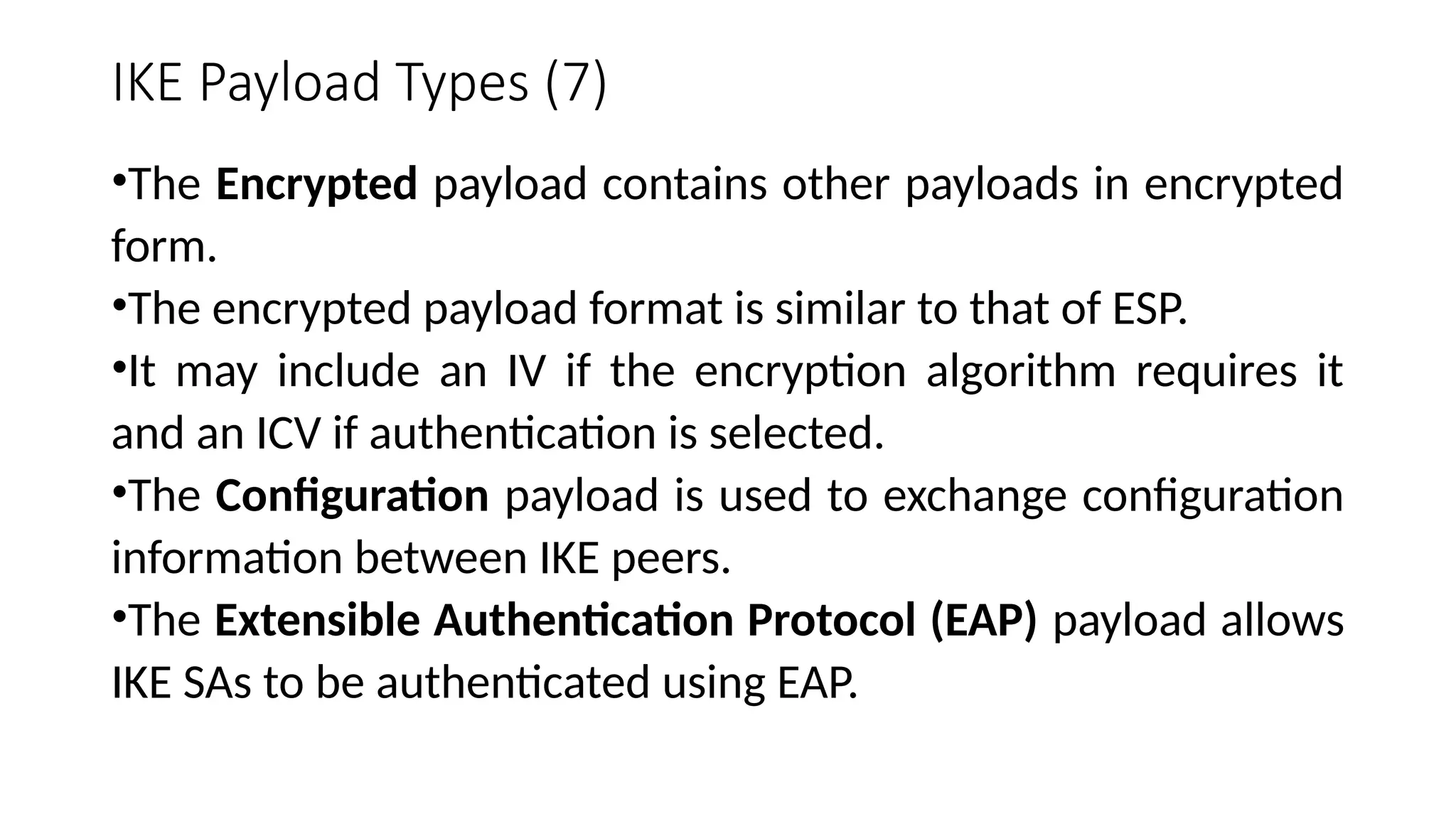
The document provides an overview of Internet Protocol Security (IPsec), detailing its architecture, operational modes (tunnel and transport), and applications for securing network communications across various scenarios, such as remote access and e-commerce. It explains the roles of authentication and confidentiality, the Internet Key Exchange (IKE) protocol for key management, and how Security Associations (SAs) and Security Policy Databases (SPDs) guide IPsec's functionality. Key benefits include transparency to applications and users while providing robust encryption and authentication to safeguard all IP-level traffic.