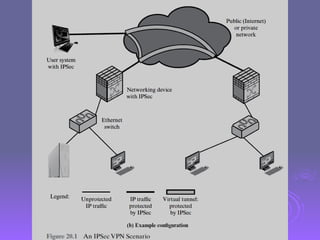
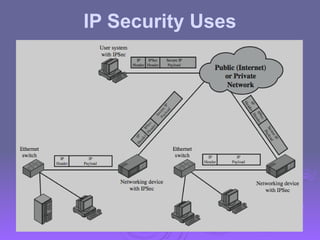
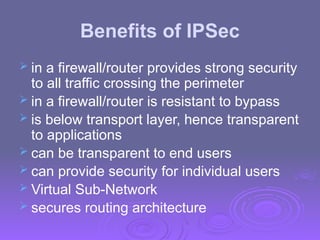
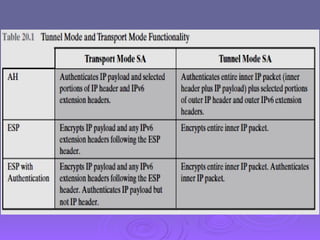
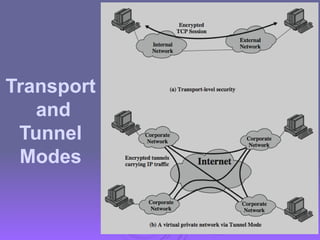
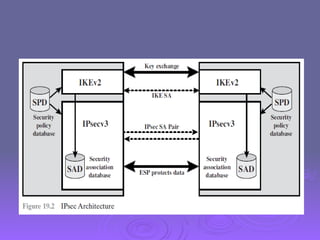
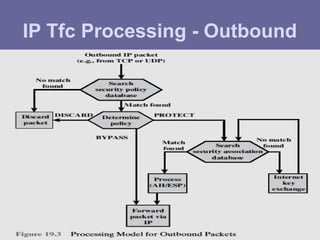
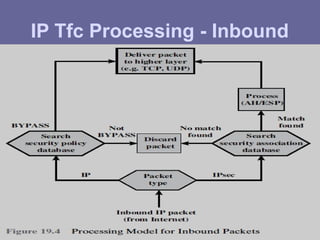
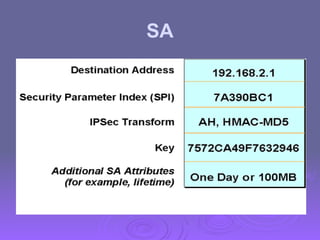
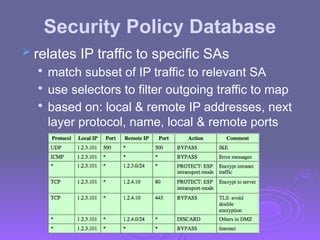
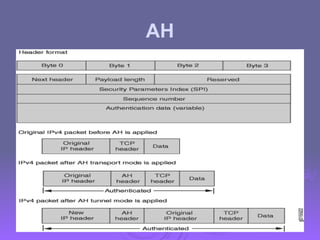
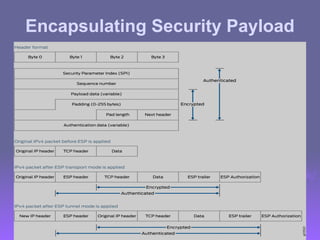
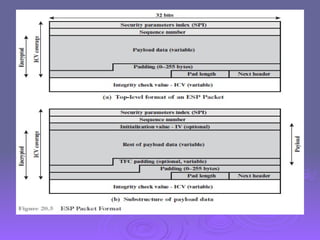
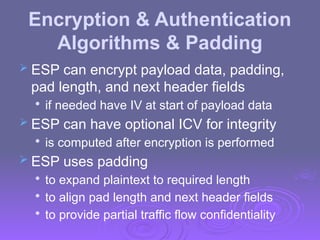
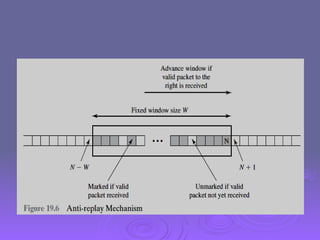
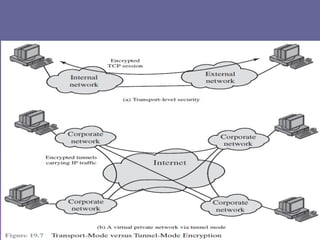
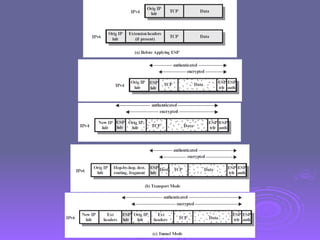
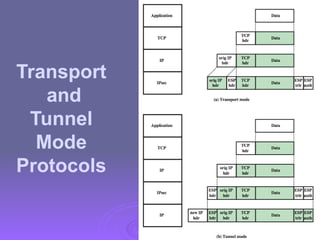
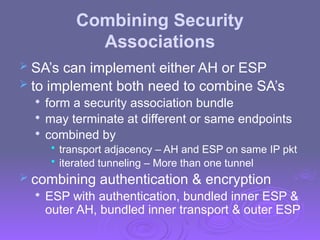
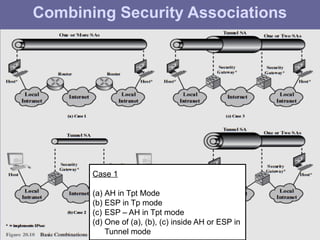
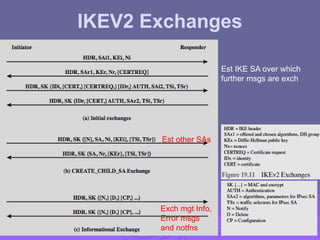
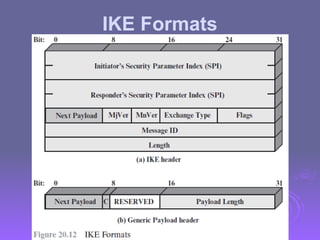
The document outlines IP security (IPsec) mechanisms, which provide authentication, confidentiality, and key management for various applications across networks, including LANs and the internet. It details the architecture, security associations, encapsulating security payload (ESP), and authentication header (AH) protocols, emphasizing their importance for secure branch connectivity, remote access, and e-commerce security. Additionally, it covers key management procedures, cryptographic algorithms, and the complexities of combining security associations to enhance network security.