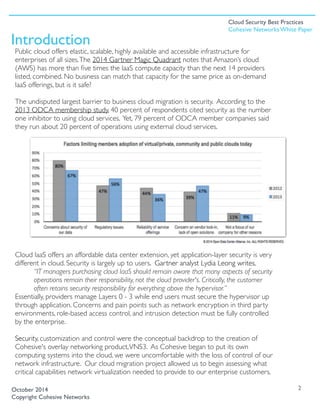
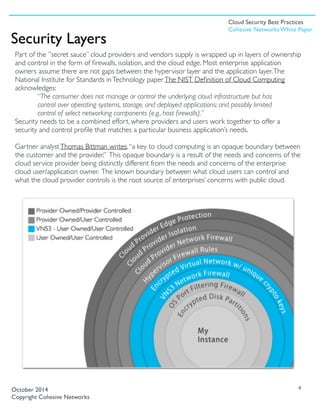
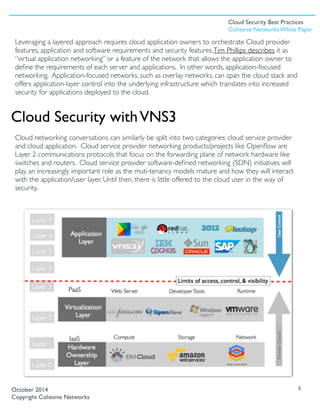
The document discusses best practices for cloud security, emphasizing the importance of layered security controls as enterprises migrate to public cloud services. It highlights that while cloud providers manage certain security aspects, end users remain responsible for securing application layers, advocating for comprehensive control over network virtualization. Cohesive Networks' VNS3 product is introduced as a solution that provides users with enhanced control, encryption, and secure connectivity in cloud environments.