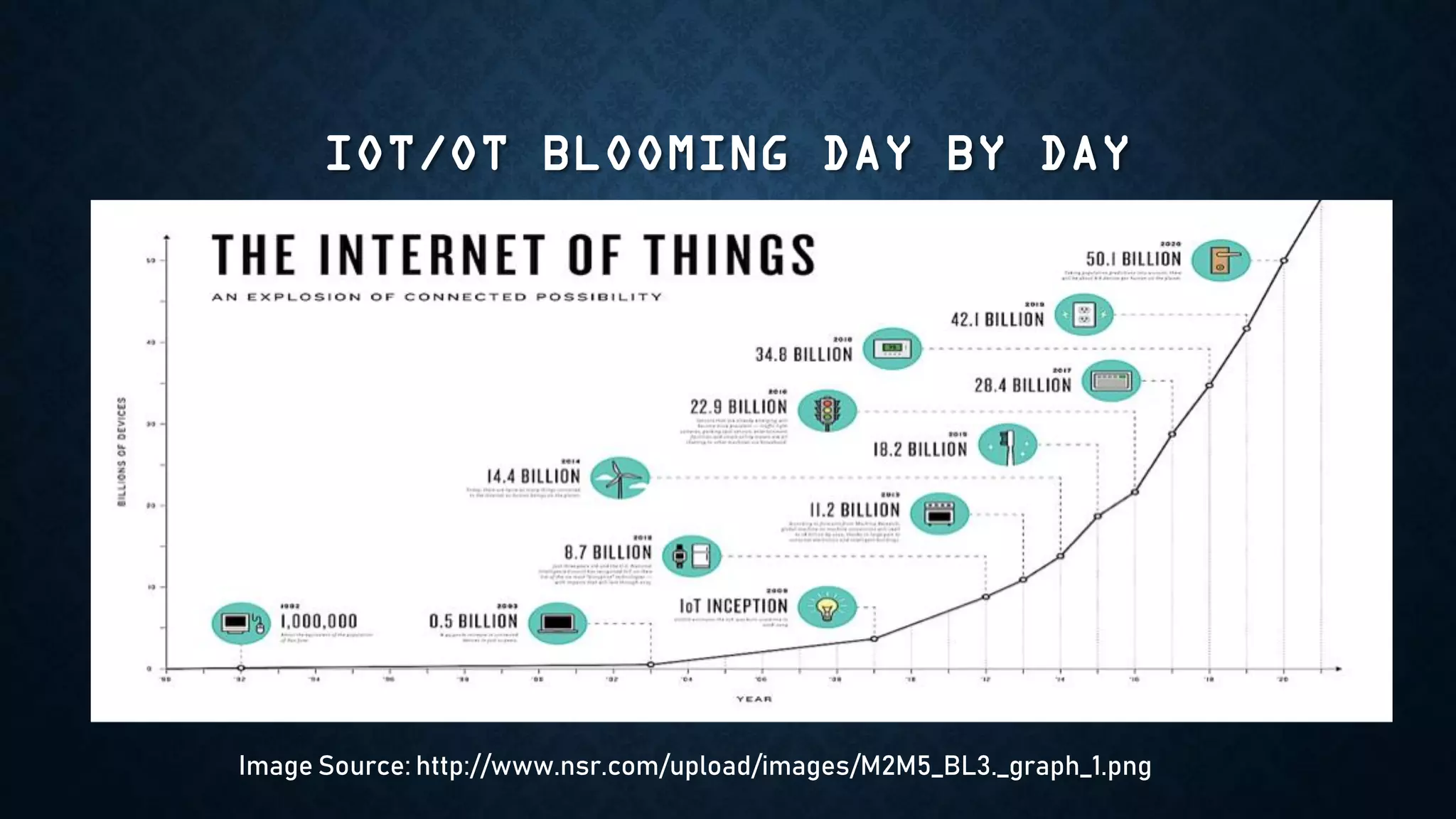
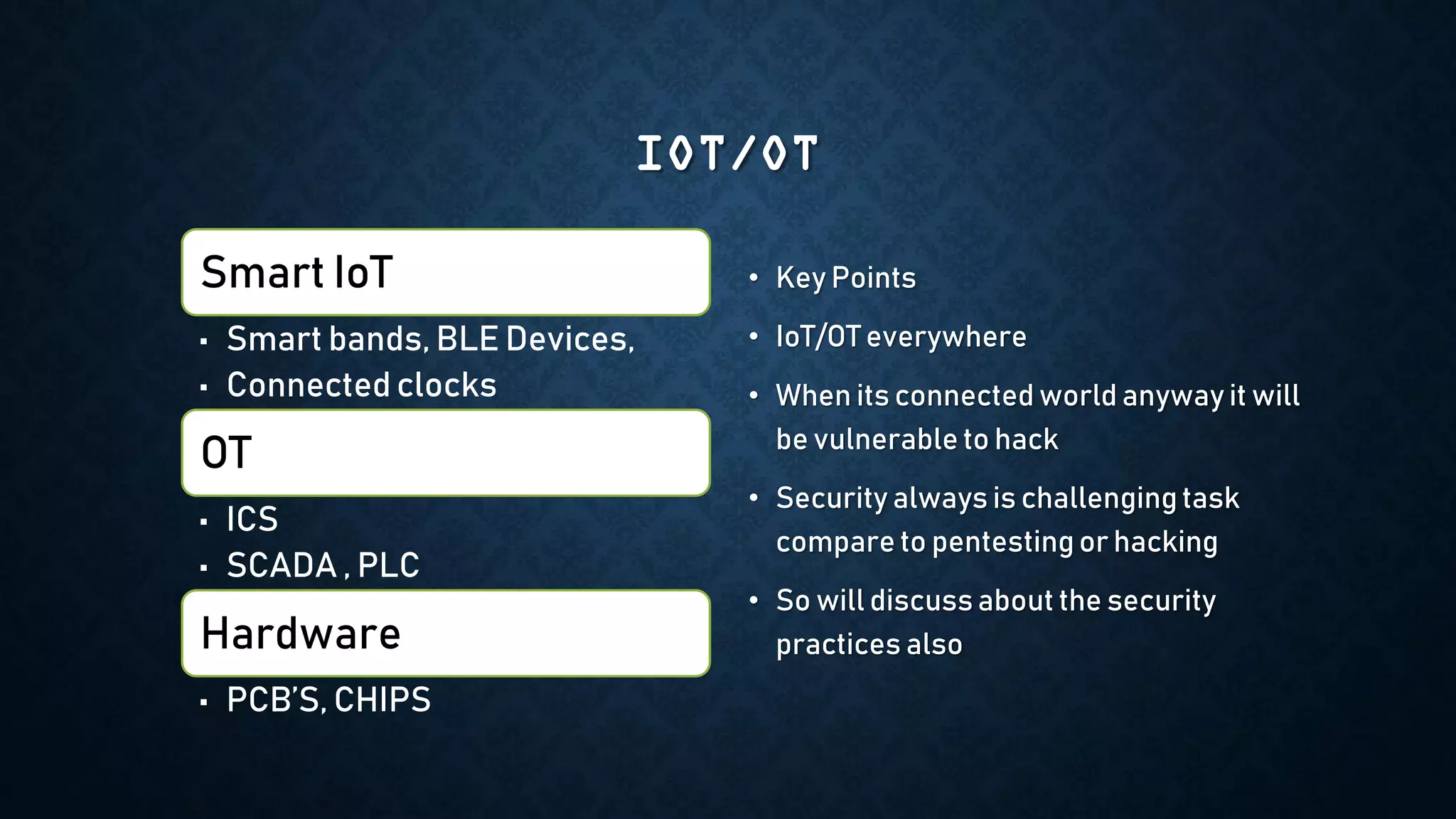
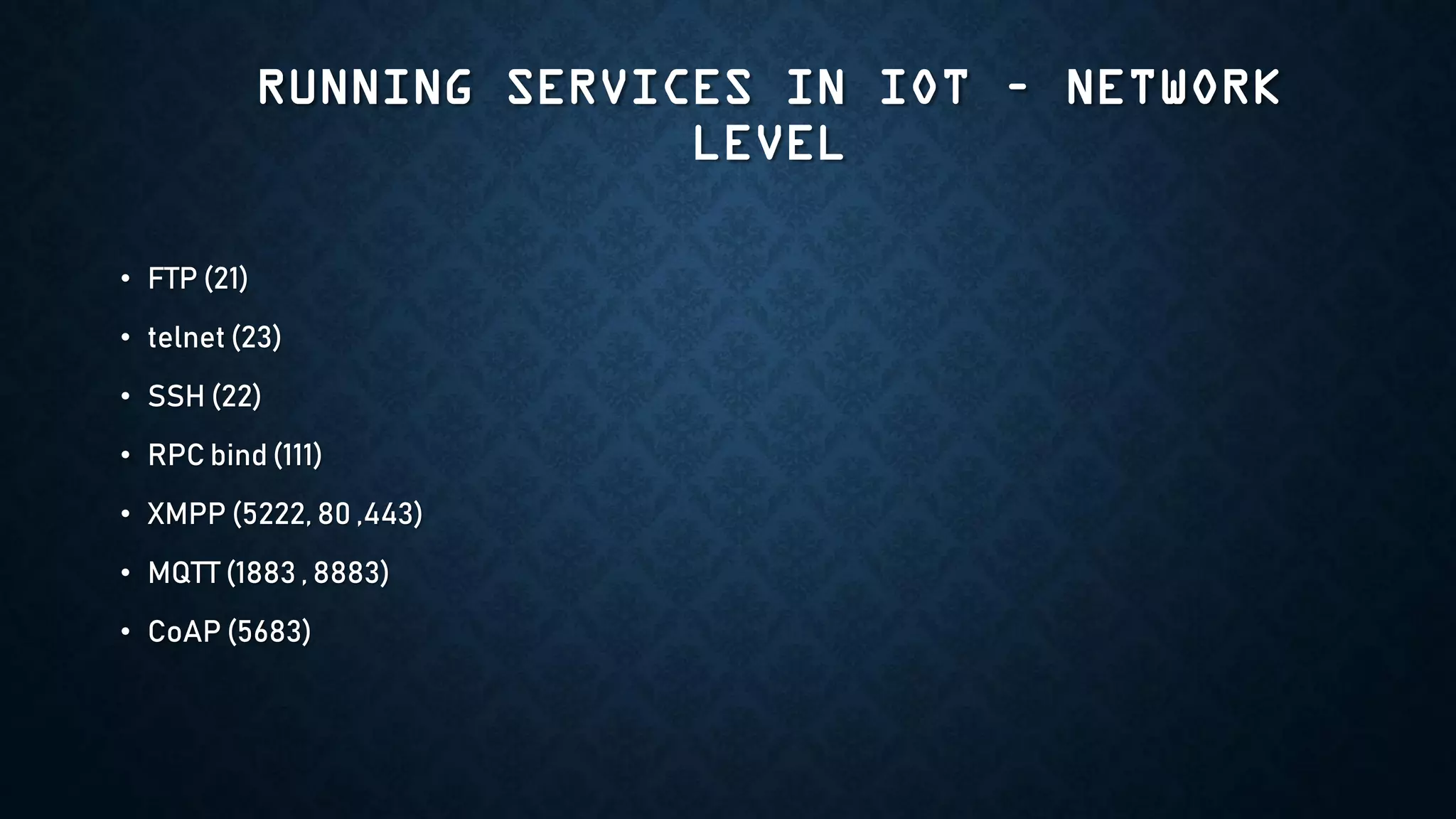
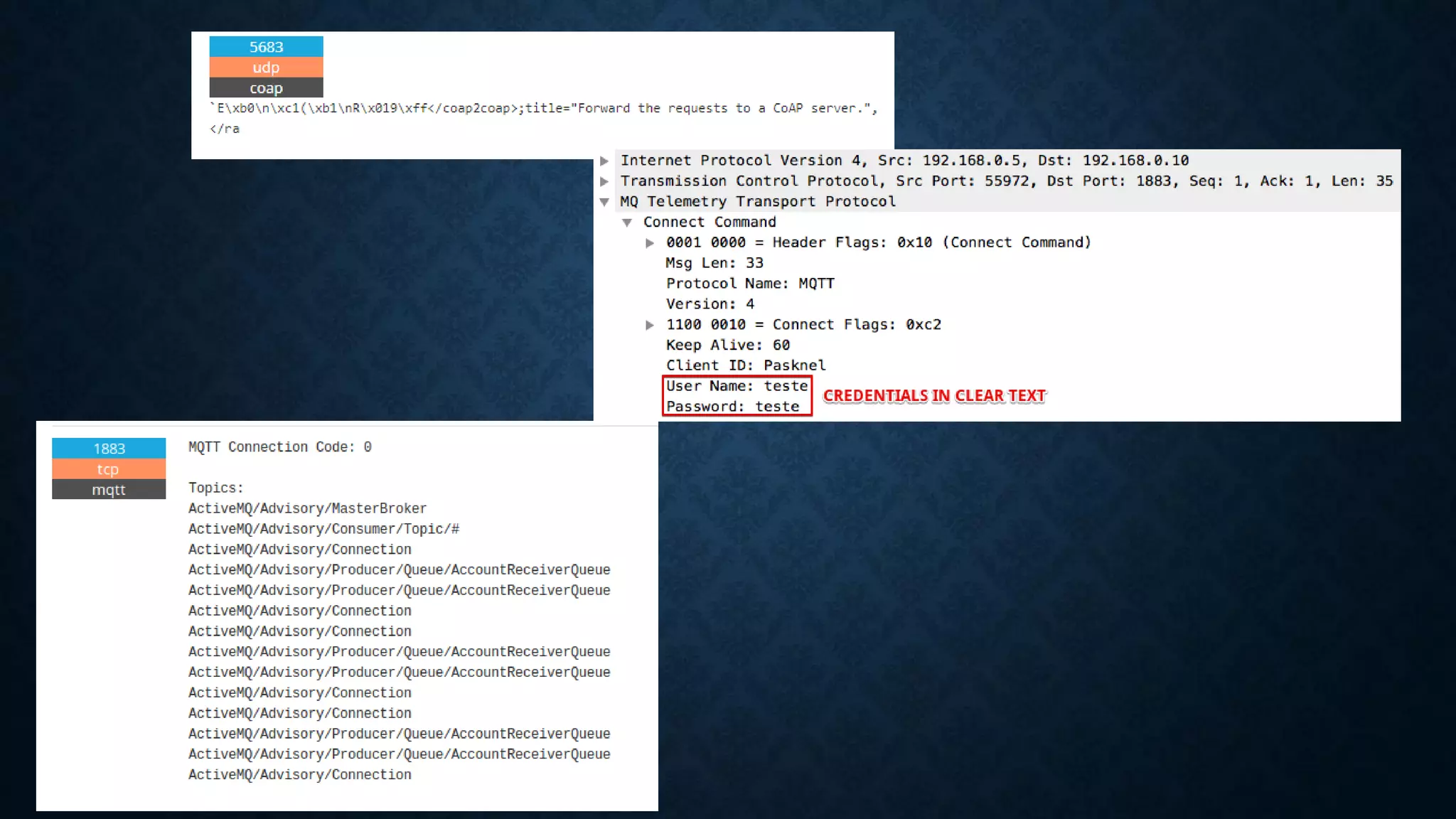
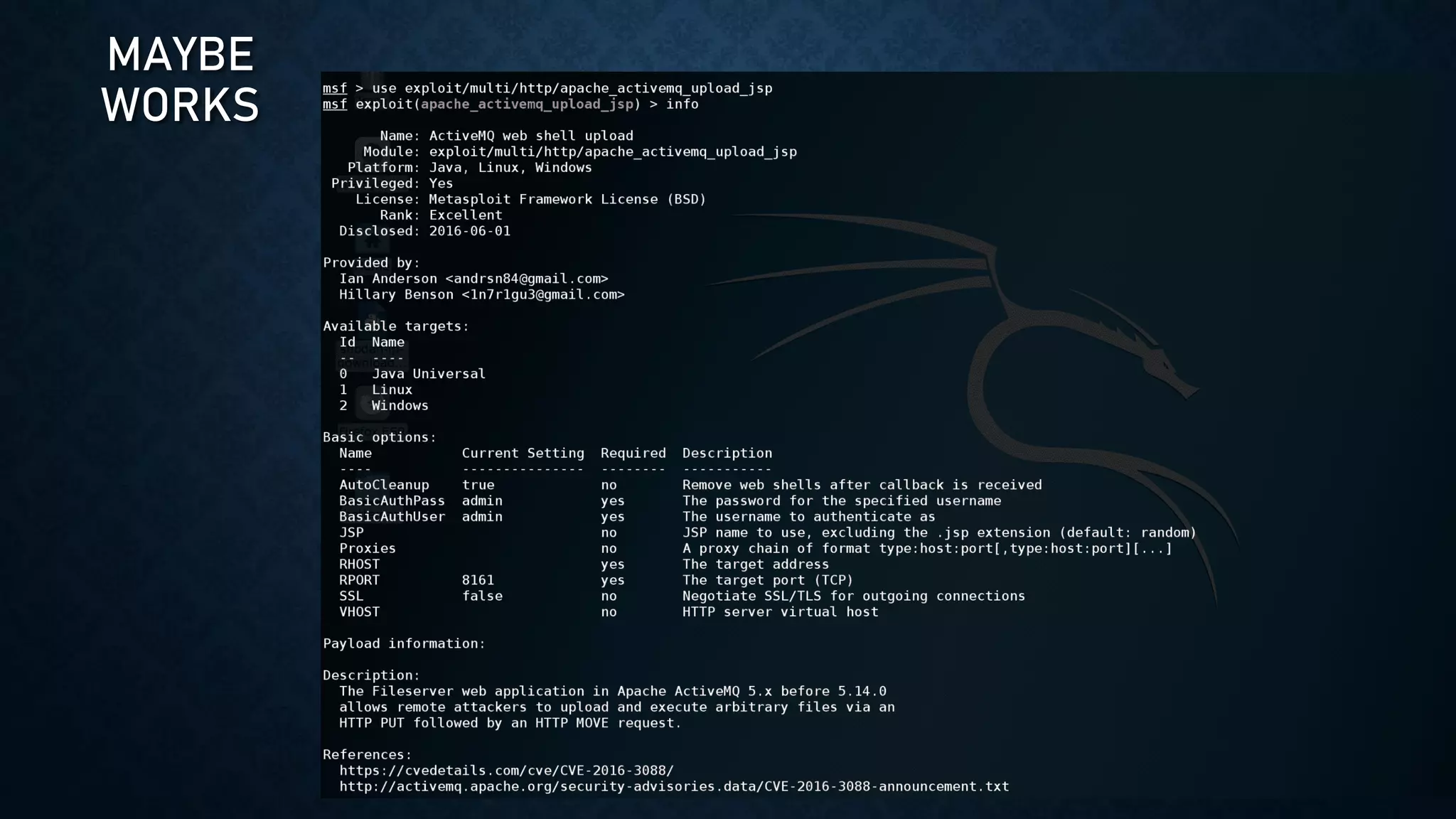
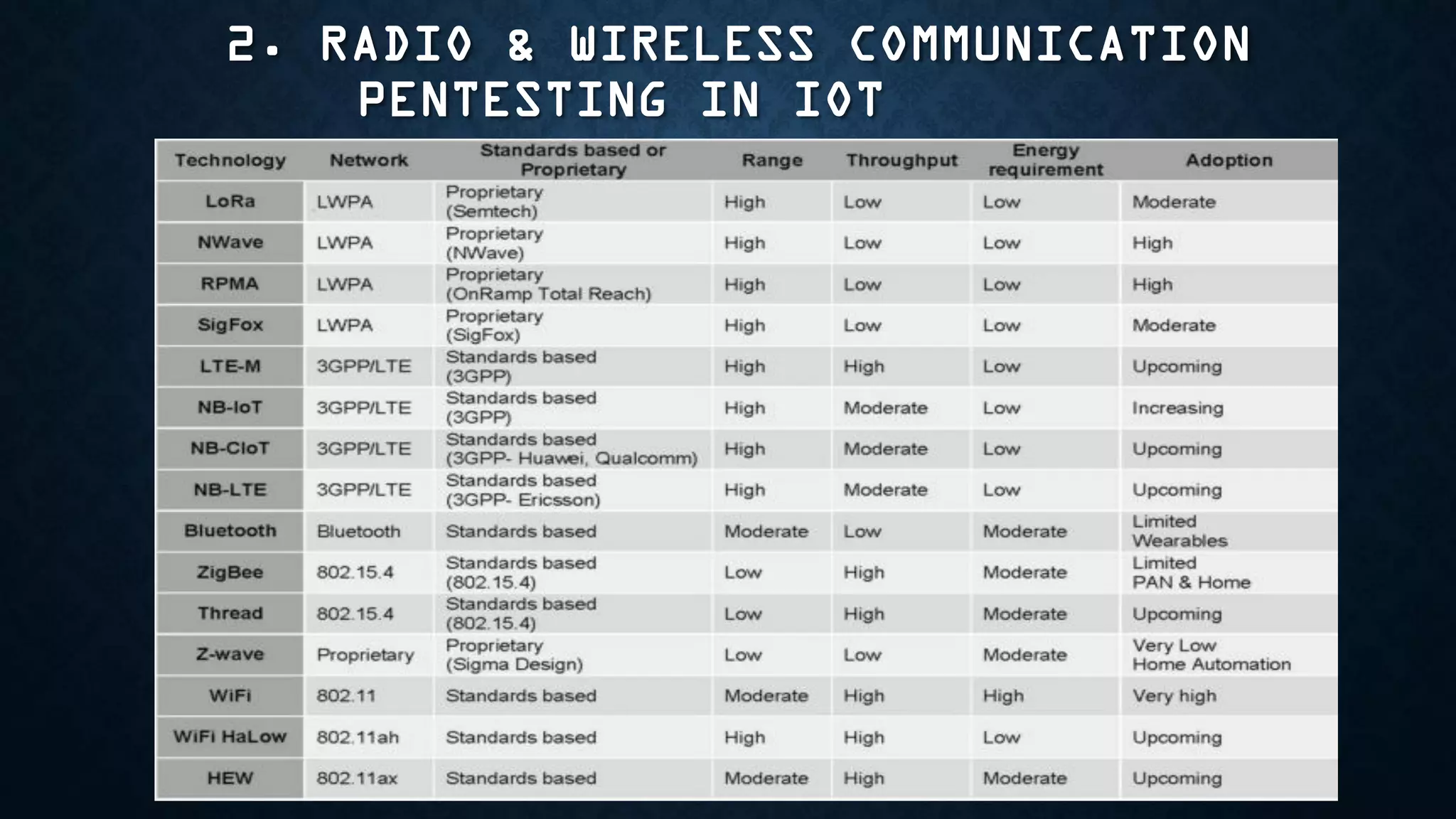
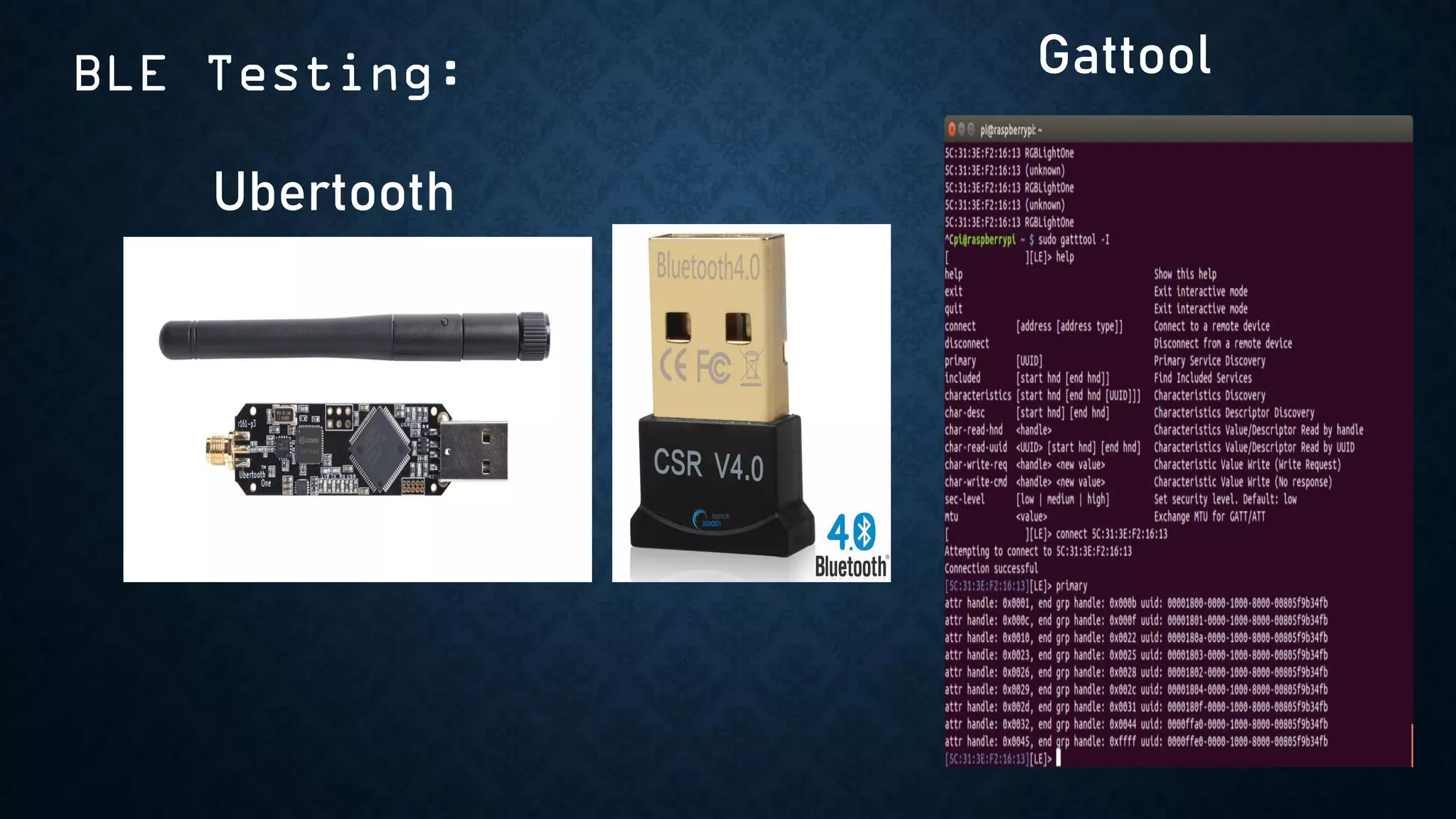
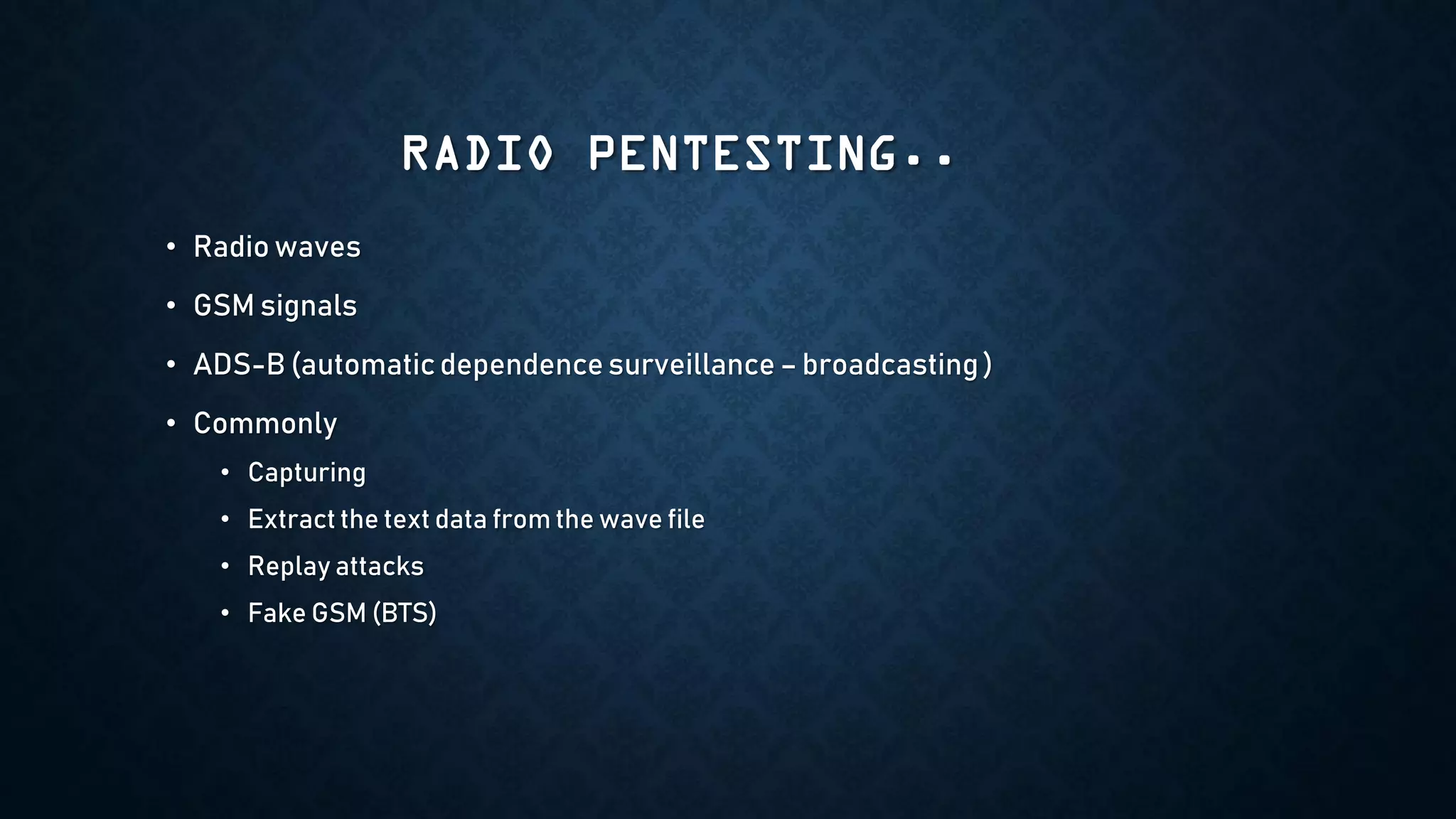
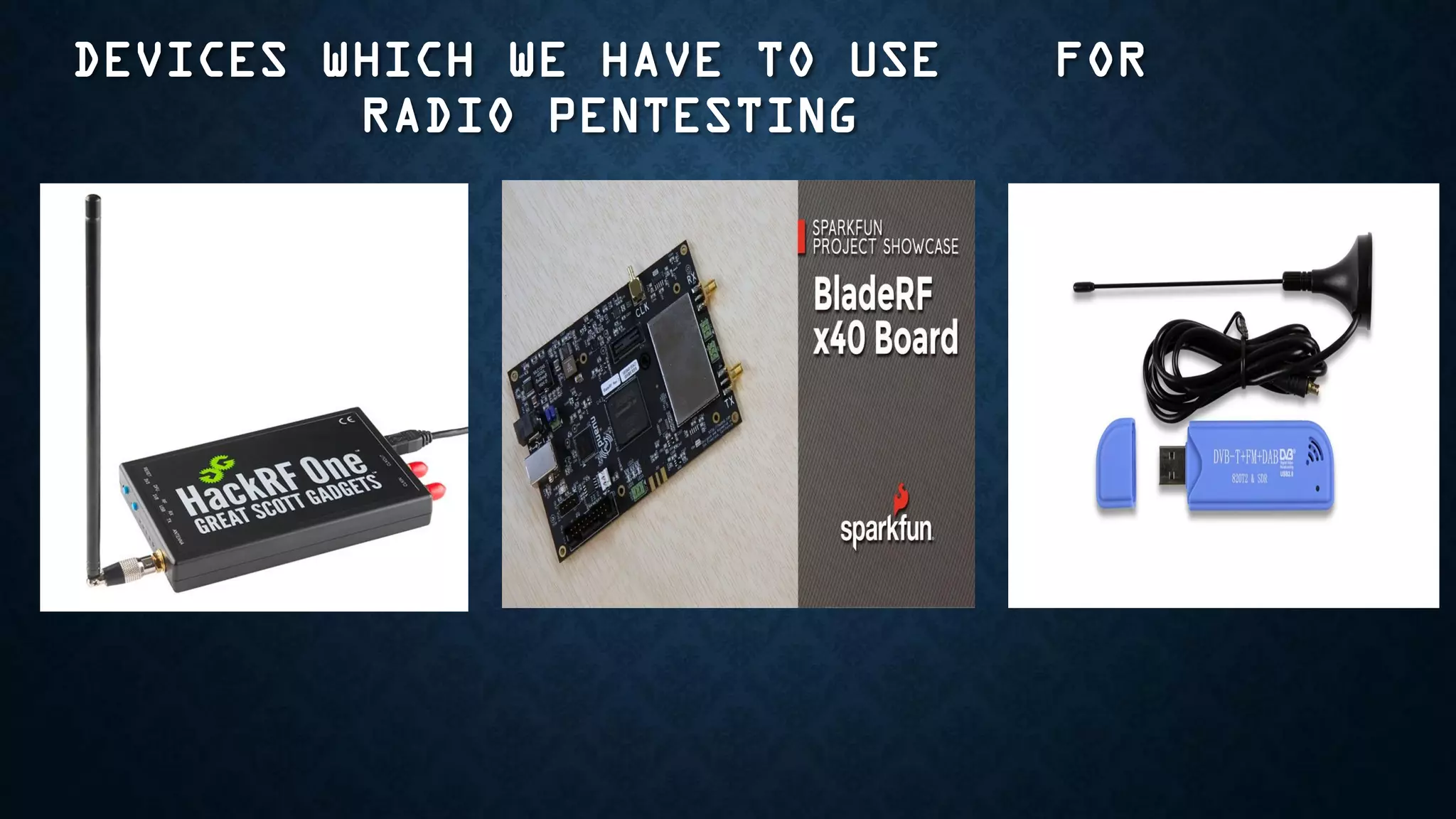
The document provides an overview of how to start exploring IoT security as a beginner. It defines IoT and OT, discusses common attack vectors like networks, wireless communication, and applications. It then provides guidance on how to perform security testing for these vectors, including tools to use for tasks like network pentesting, radio communication testing, and mobile application testing. The goal is to help beginners learn about IoT security challenges and how to start assessing vulnerabilities.